Protective method for solid-state disk encryption key
A solid-state hard disk and encryption key technology, applied in the field of information security, can solve the problems of easy cracking and low complexity of encryption key security protection, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
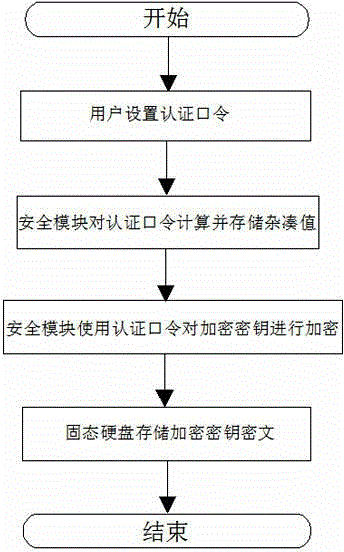
[0021] Such as figure 1 Shown, a kind of protection method of solid-state disk encryption key, described method comprises steps as follows:
[0022] The user authenticates the password through the management program;
[0023] The solid-state disk security module calculates a hash value for the authentication password and stores the hash value in the solid-state disk, which is used to verify the user password during daily use;
[0024] The security module encrypts the encryption key with the authentication password;
[0025] The solid-state drive stores the encryption key ciphertext.
[0026] Only the hash value of the authentication password is stored inside the solid state disk, and the authentication password is not stored. The user authentication password and the encryption key ciphertext are stored separately, realizing the physical separation of the key and the protected data.
[0027] The encryption key is encrypted by using the user authentication password, so to pa...
Embodiment 2
[0029] On the basis of Embodiment 1, the management program described in this embodiment is a setting program built into the solid-state hard disk, and when powered on, the program is loaded into the internal memory as a user management setting terminal.
Embodiment 3
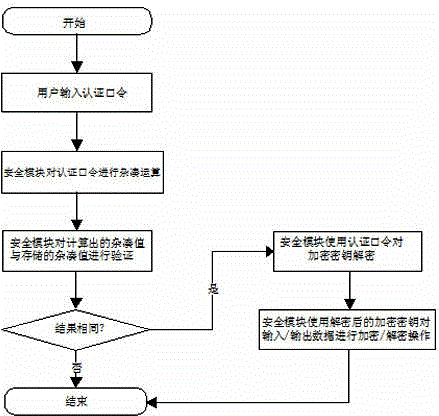
[0031] On the basis of Embodiment 1 or 2, the security module described in this embodiment is a security function processing module built in a solid-state hard disk, which realizes functions such as encryption key protection / storage, authentication password verification, and data encryption / decryption.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com