A quantum key transmission control method and system
A quantum key and transmission control technology, applied in transmission systems, digital transmission systems, and key distribution, which can solve the problem that one-time pads have not been practically applied.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
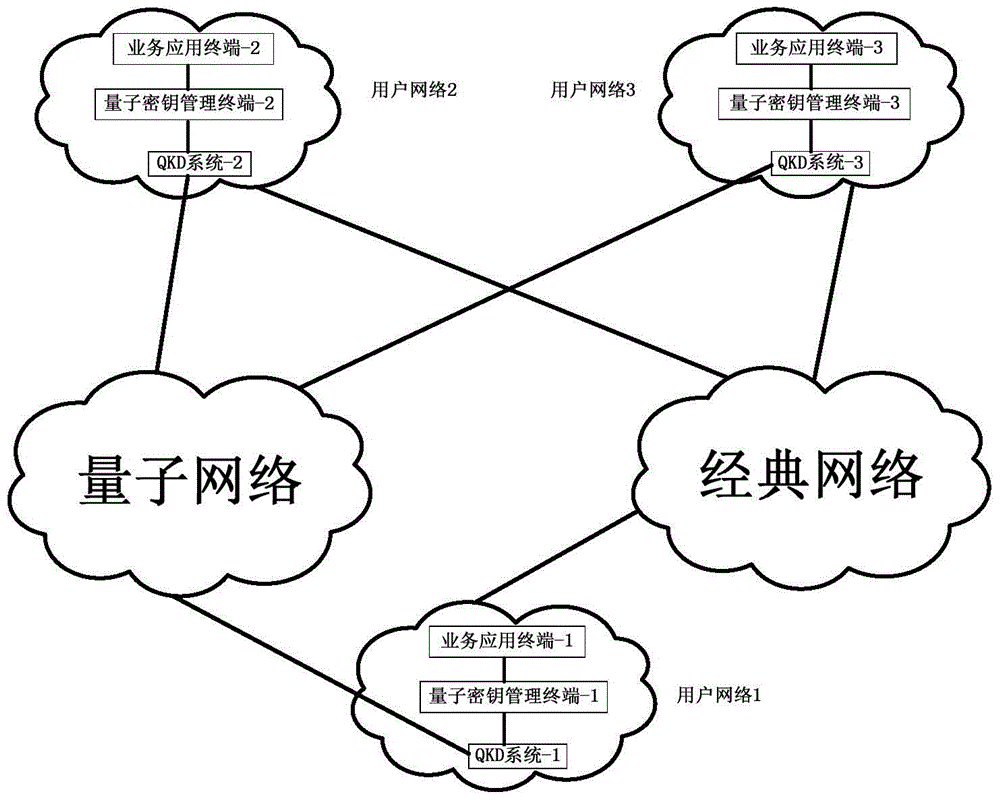
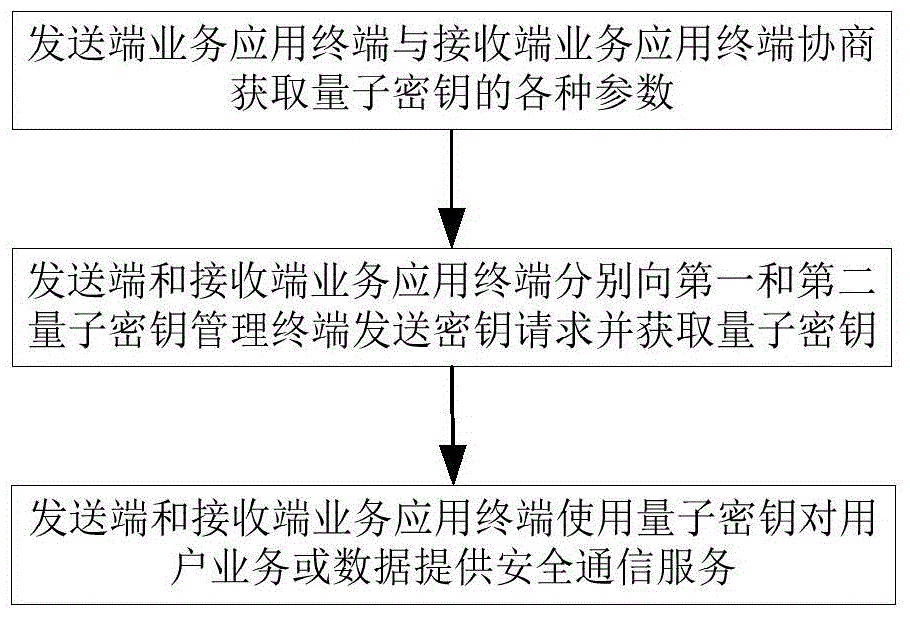
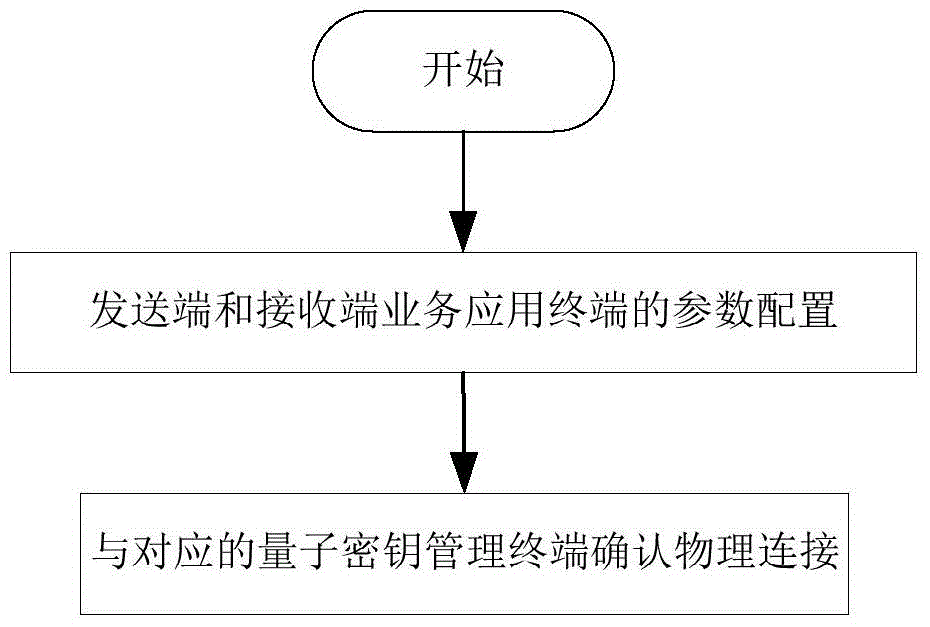
[0074] See figure 2 , The embodiment of the present invention provides a quantum key transmission control method, wherein the quantum key can be used between the sender and the receiver business application terminal to provide secure communication services for user business or data, and the sender business application terminal and the first quantum key The key management terminal is connected, and the receiving end service application terminal is connected to the second quantum key management terminal. The method includes the following steps:
[0075] Step 1. The service application terminal at the sending end and the service application terminal at the receiving end negotiate to obtain various parameters of the quantum key. The parameters include: start ID, destination ID, key usage mode, and requested key bytes; where, start ID and destination ID are the quantum key acquisition identifiers, which are used to identify the quantum key shared between the first quantum key manageme...
Embodiment 2
[0122] See Picture 12 , The embodiment of the present invention provides a quantum key transmission control system, including a sending end service application terminal and a receiving end service application terminal, a first quantum key management terminal and a second quantum key management terminal, characterized in that:
[0123] The sending end service application terminal is used to negotiate with the receiving end service application terminal to obtain various parameters of the quantum key, and send a key request to the first quantum key management terminal according to the negotiated parameters and obtain the quantum key, the parameters including : Start ID, destination ID, key usage mode, and requested key bytes; where the start ID and destination ID are the identifications for obtaining quantum keys, which are used to identify the first quantum key corresponding to the sending end service application terminal The second quantum key management terminal corresponding to ...
Embodiment 3
[0150] See Figure 12a The embodiment of the present invention provides a quantum key management terminal, which is used in the quantum key transmission control system described in the second embodiment to provide a quantum key for secure communication between multiple service application terminals. The management terminal includes:
[0151] The storage module is used to store the quantum keys sent by the quantum key distribution (QKD) system, and send a corresponding number of quantum keys to the first quantum key interaction module according to the key requirements of the corresponding business application terminal;
[0152] The first quantum key interaction module is configured to receive the key request sent by the corresponding service application terminal, and obtain the quantum key from the storage module, so as to realize the quantum key output to the service application terminal.
[0153] In the quantum key transmission control system, there are two service application termi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com