Implementation method of two-dimension routing protocol and device using protocol
A technology of routing protocol and implementation method, applied in the direction of digital transmission system, electrical components, transmission system, etc., can solve problems such as network security problems that cannot be solved, and achieve the effect of improving transmission security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
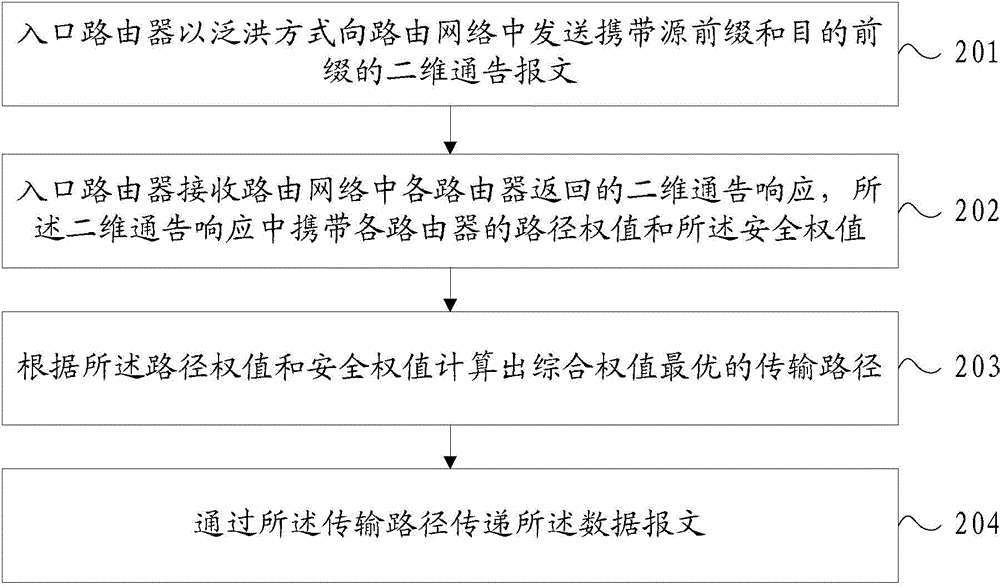
[0031] Embodiment 1 of the present invention provides a method for implementing a two-dimensional routing protocol, wherein each router in the routing network is provided with its own security weight according to the security level, and the ingress router receives the data message that needs to be sent to the egress router , and when establishing a transmission path for sending this datagram, such as figure 1 As shown, the method includes:
[0032] In step 201, the ingress router sends a two-dimensional advertisement report carrying a source prefix and a destination prefix to the routing network in a flooding manner.
[0033] Wherein, the source prefix and the destination prefix are the network addresses of the ingress router and the egress router respectively. The ingress router is a router sending data packets in the routing network; the egress router is a router on the destination terminal side in the routing network, for example: the egress router is a router directly con...
Embodiment 2
[0073] In Embodiment 1 of the present invention, a method for implementing a two-dimensional routing protocol is proposed. Steps 201-204 of the main solution are how to obtain a safe and efficient transmission path. The scheme of performing security verification on the routers on the transmission path in the network (steps 401-404), however, in the actual implementation process, the authority owned by the operator may only exist on the exit router, while for other routers on the transmission path There is no function of setting a blacklist (it is common when the egress router is used as a router for individual users). Therefore, this embodiment 2 proposes a method for how to solve the router security problem for the egress router, wherein each router in the routing network is provided with its own security weight according to the security level, such as Figure 5 Said, the method includes the following steps:
[0074] In step 601, the egress router receives the data packet de...
Embodiment 3
[0085] The embodiment of the present invention also provides a device suitable for two-dimensional routing protocols, such as Figure 6 As shown, it includes a storage device 1, an input and output device 2, and a processing device 3. The storage device is connected to the processing device, and the input and output device is connected to the processing device. Specifically:
[0086] The storage device 1 is used for storing a blacklist, and the blacklist includes network addresses of routers with security problems.
[0087] The input and output device 2 is used to receive the data message sent by the router on the transmission path.
[0088] The processing device 3 is configured to obtain the source prefix and the destination prefix carried in the data message; verify the security of the router corresponding to the source prefix; and use the input and output device 2 to forward the The data message is sent to the destination terminal.
[0089] It is worth noting that the inf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com