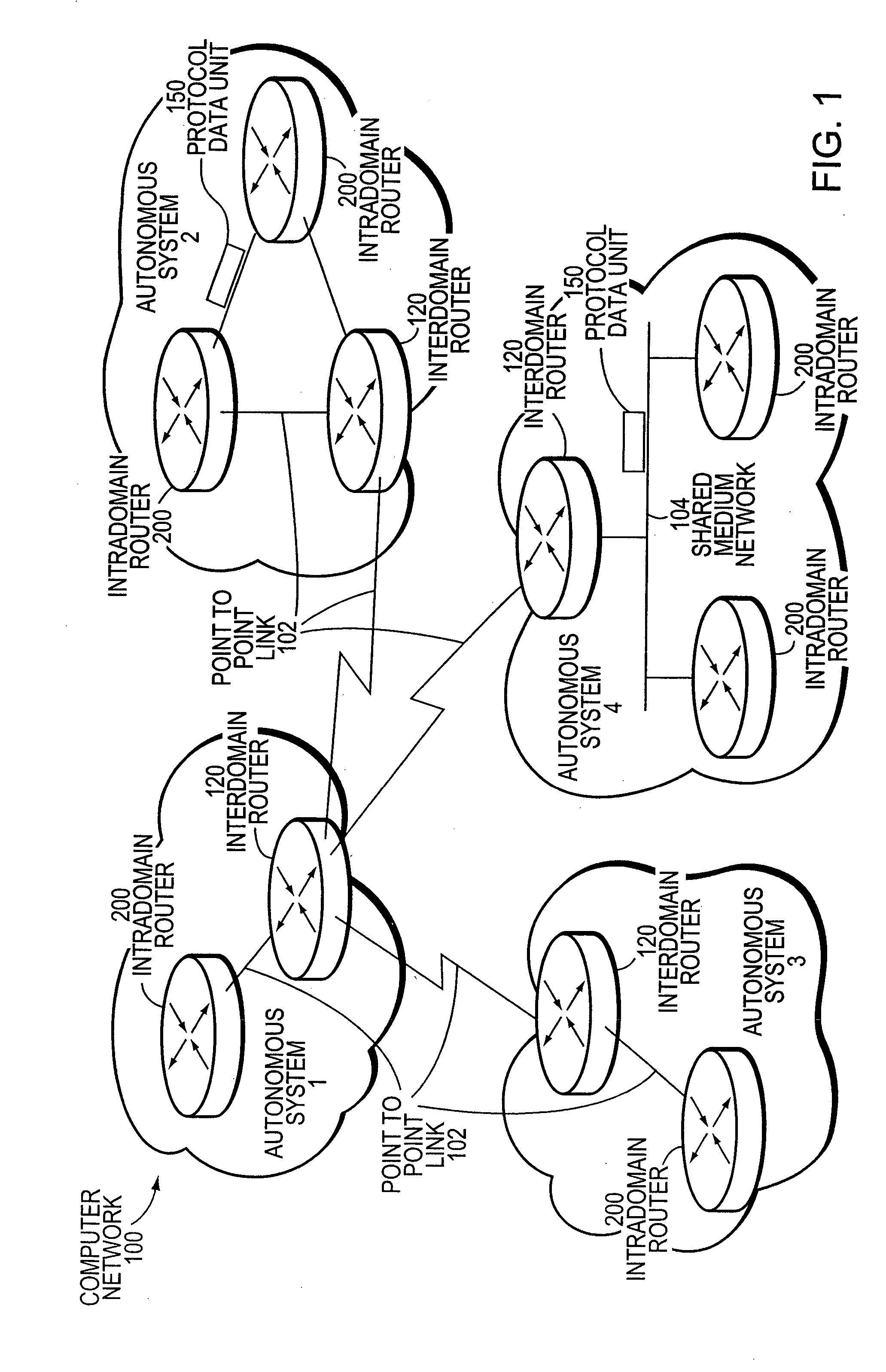
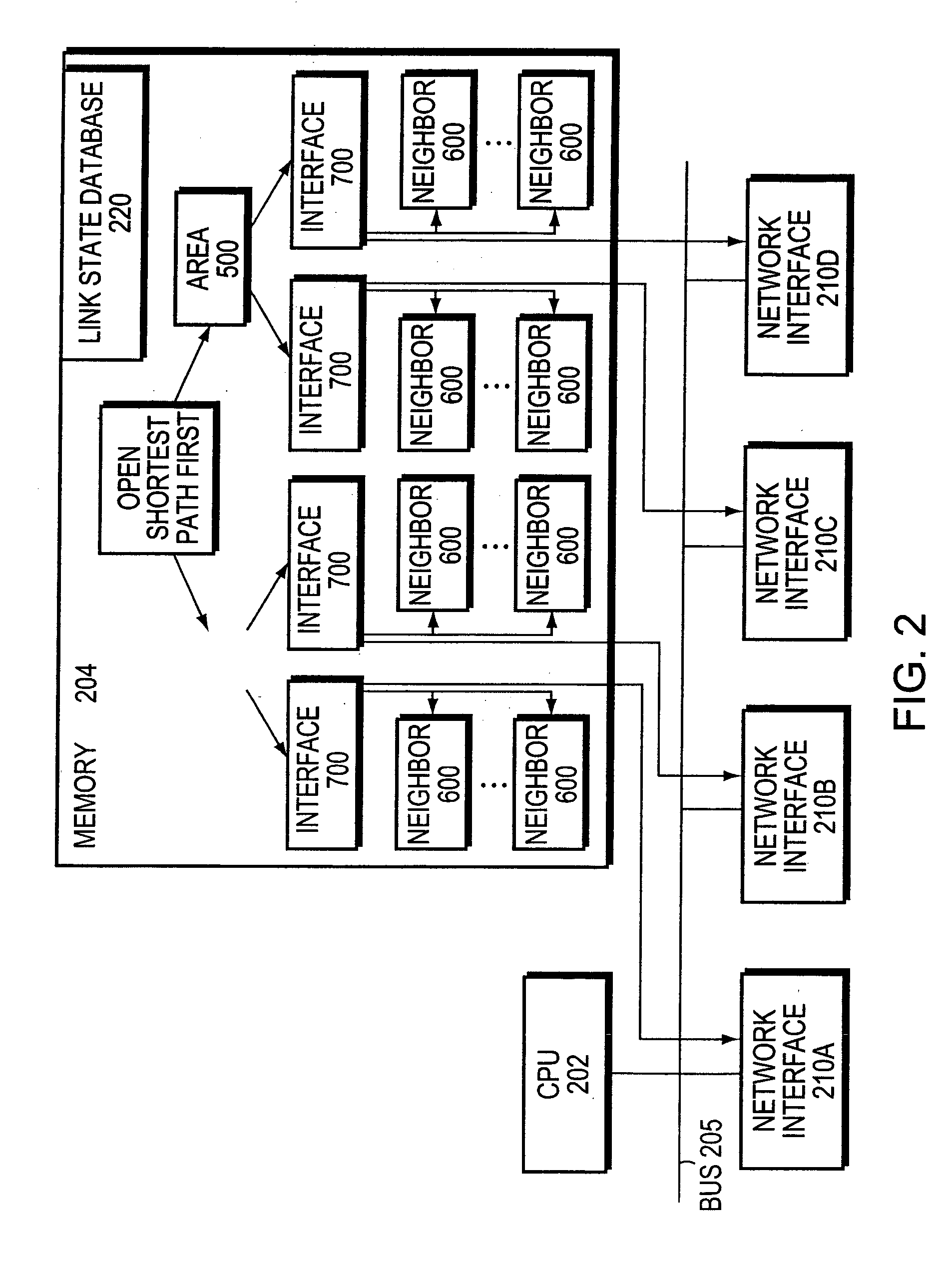
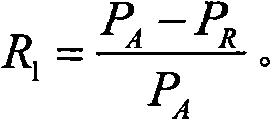Patents
Literature
33 results about "Zone Routing Protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Zone Routing Protocol, or ZRP is a hybrid Wireless Networking routing protocol that uses both proactive and reactive routing protocols when sending information over the network. ZRP was designed to speed up delivery and reduce processing overhead by selecting the most efficient type of protocol to use throughout the route.
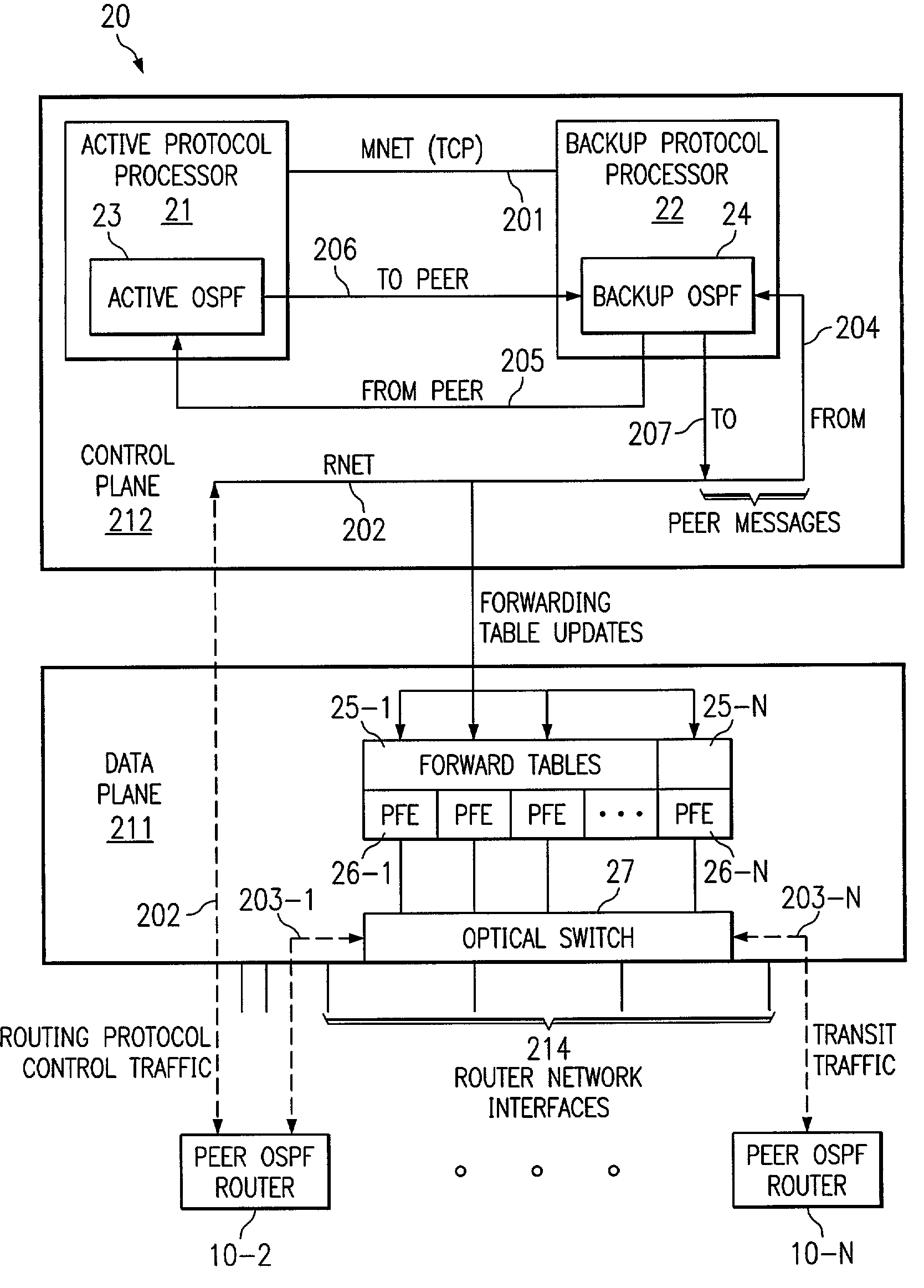
Highly-available OSPF routing protocol
InactiveUS7292535B2Error preventionFrequency-division multiplex detailsMessage flowOpen Shortest Path First
In highly-available Open Shortest Path First (OSPF) routing in a network, the dynamic state of a backup OSPF instance in a router is synchronized with the dynamic state of an active OSPF instance using explicit message transmission from the active instance to the backup instance. After this, the dynamic state synchronization of the backup OSPF instance is maintained using a combination of explicit message updates from the active OSPF instance together with a message flow-through mechanism. In the event of fail-over of the active OSPF instance, then the router recovers seamlessly without reconfiguring or interrupting traffic among peer routers in the network, by functionally substituting the synchronized backup OSPF instance for the active OSPF instance, such that the backup OSPF instance establishes itself as the new active OSPF instance.
Owner:AVAGO TECH INT SALES PTE LTD
Optimizing flooding of information in link-state routing protocol
InactiveUS20050265260A1Prevent floodingEasy to useError preventionData switching by path configurationComputer hardwareFlooding algorithm
A router executes a flooding algorithm. The router maintains a list of neighbors within an area data structure. When a new neighbor arises on an interface belonging to an area served by the router, the router updates the neighbor data structure describing that adjacency by linking it to a corresponding entry in the list of neighbors. Utilizing information contained in the list of neighbors, as well as information describing the types of interfaces used by the neighbors in the list, the router marks each interface data structure within the area as either flooding-active or flooding-passive. Marking of the interface is performed in connection with an interface election process that selects a flooding-active interface on the basis of, e.g., interface cost, giving preference to faster interfaces. Thereafter, link state protocol data units (PDUs) are sent to the neighbors over those interfaces marked as flooding-active.
Owner:CISCO TECH INC
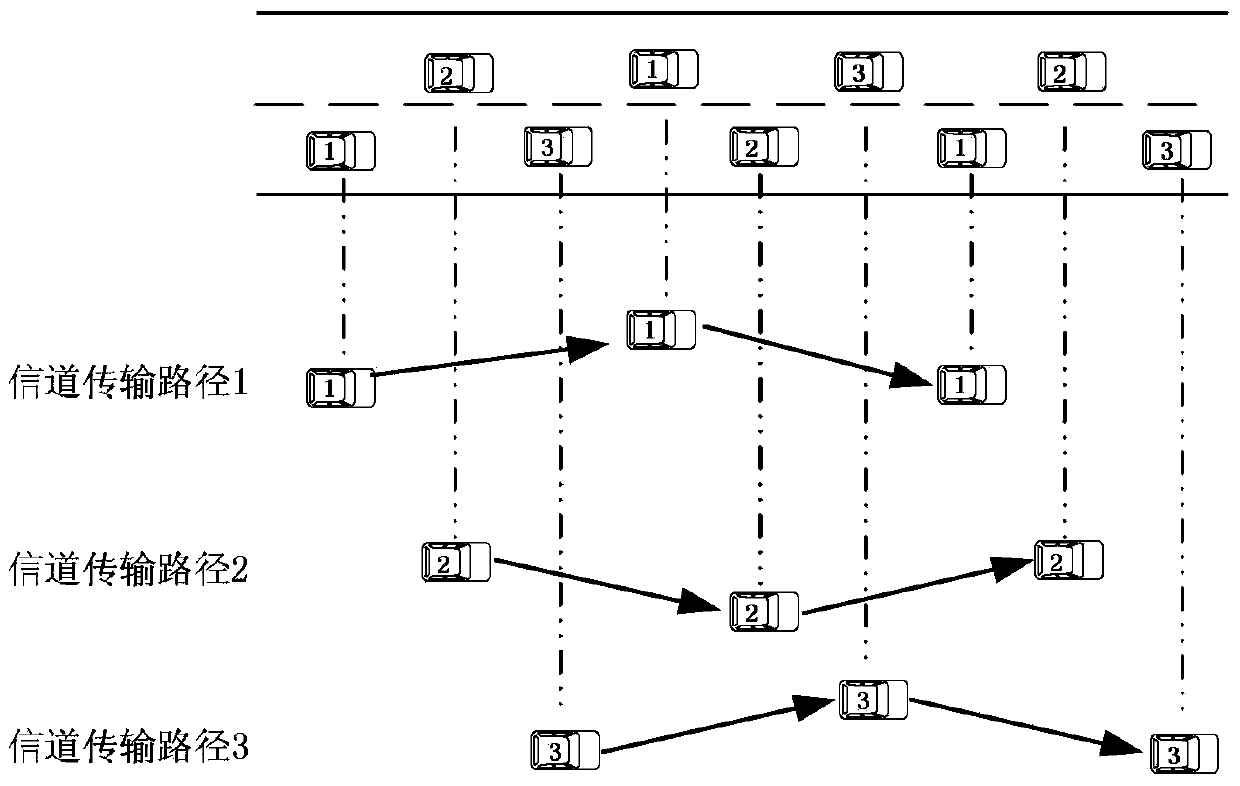
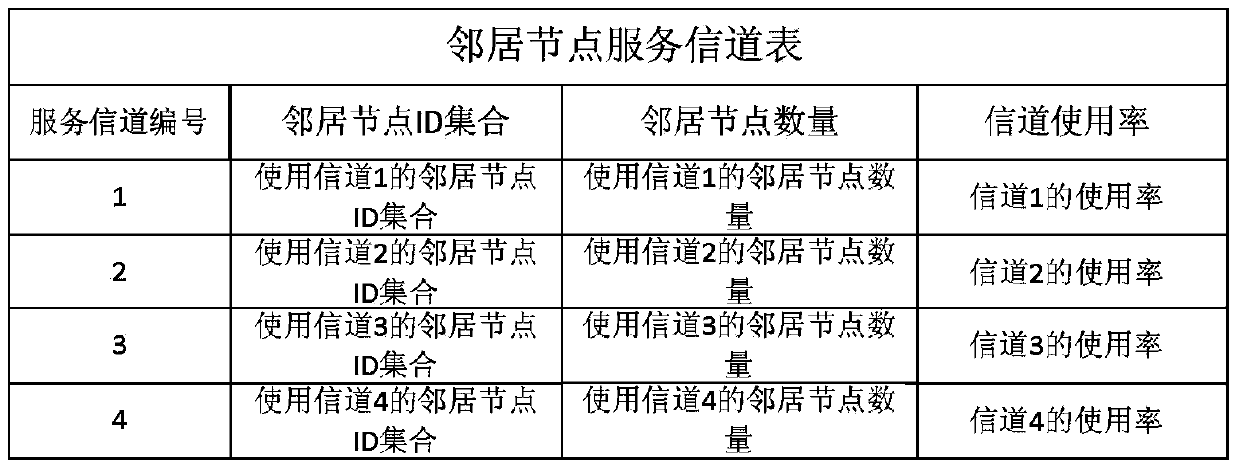
Multi-channel multi-path routing protocol for vehicle team ad-hoc networks
InactiveCN104093185AReduce competitionReduce conflictNetwork topologiesTeam communicationAlgorithm Selection
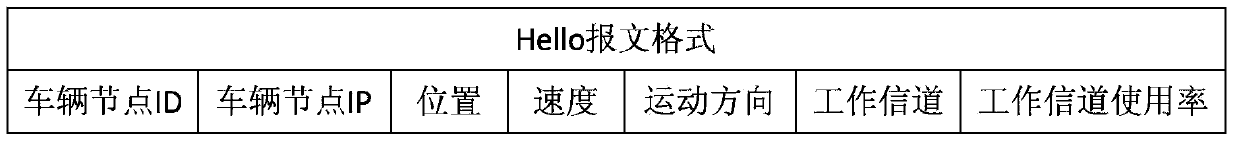
The invention discloses a multi-channel multi-path routing protocol for vehicle team ad-hoc networks. The multi-channel multi-path routing protocol mainly comprises: (1) each vehicle node is made to work on a service channel, the vehicle nodes using the same service channel form a channel transmission path in a vehicle team, and multiple transmission paths of multiple channels are formed in the vehicle team; (2) each vehicle node acquires position, speed and motion direction information of other vehicle nodes through an adaptive distributed position service; and (3) a multi-channel greedy forwarding algorithm is adopted: when the vehicle nodes send or forward a data message, a next-hop neighbor node is selected by use of the greedy forwarding algorithm according to the position of a destination node and the working channel utilization rate of a neighbor node until the data message reaches the destination node. By adopting the provided multi-channel multi-path routing protocol for vehicle team ad-hoc networks, vehicle team communication is enabled to be fully self-organized without relying on any infrastructure, adjacent vehicle nodes are allowed to communicate on different channel transmission paths at the same moment, the network throughput is improved, and the routing protocol supports multi-hop big data transmission and has practical application prospects.
Owner:SOUTH CHINA UNIV OF TECH
Clustering multi-hop routing protocol of wireless sensor network
InactiveCN105072661AExtend the life cycleEnergy averageNetwork topologiesHigh level techniquesWireless mesh networkReal-time data
The invention provides a clustering multi-hop routing protocol of a wireless sensor network. In network initialization, each node forms a cluster according to position information, A sink node acquires all clusters in the network. Data transmission is initialized by the sink node. Furthermore routing from the sink node to a target cluster between cluster heads which are dynamically selected is formed in real time. The cluster head of the target cluster acquires local data local data (such as real-time data of a certain cell in the cluster) and transmits the local data to the sink node. In the establishing process of the routing, the intermediate node of the routing utilizes estimated cost for deciding a next-hop node. The estimated cost comprises a distance between a normalized intermediate node and the residual energy of the node. The clustering multi-hop routing protocol is mainly used for the field of wireless sensing network routing control.
Owner:STATE GRID CORP OF CHINA +3
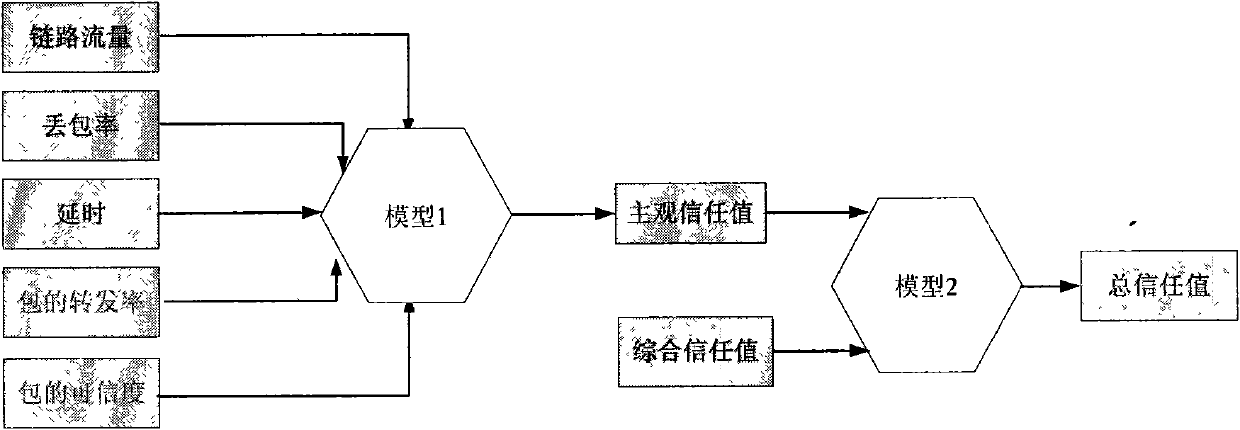
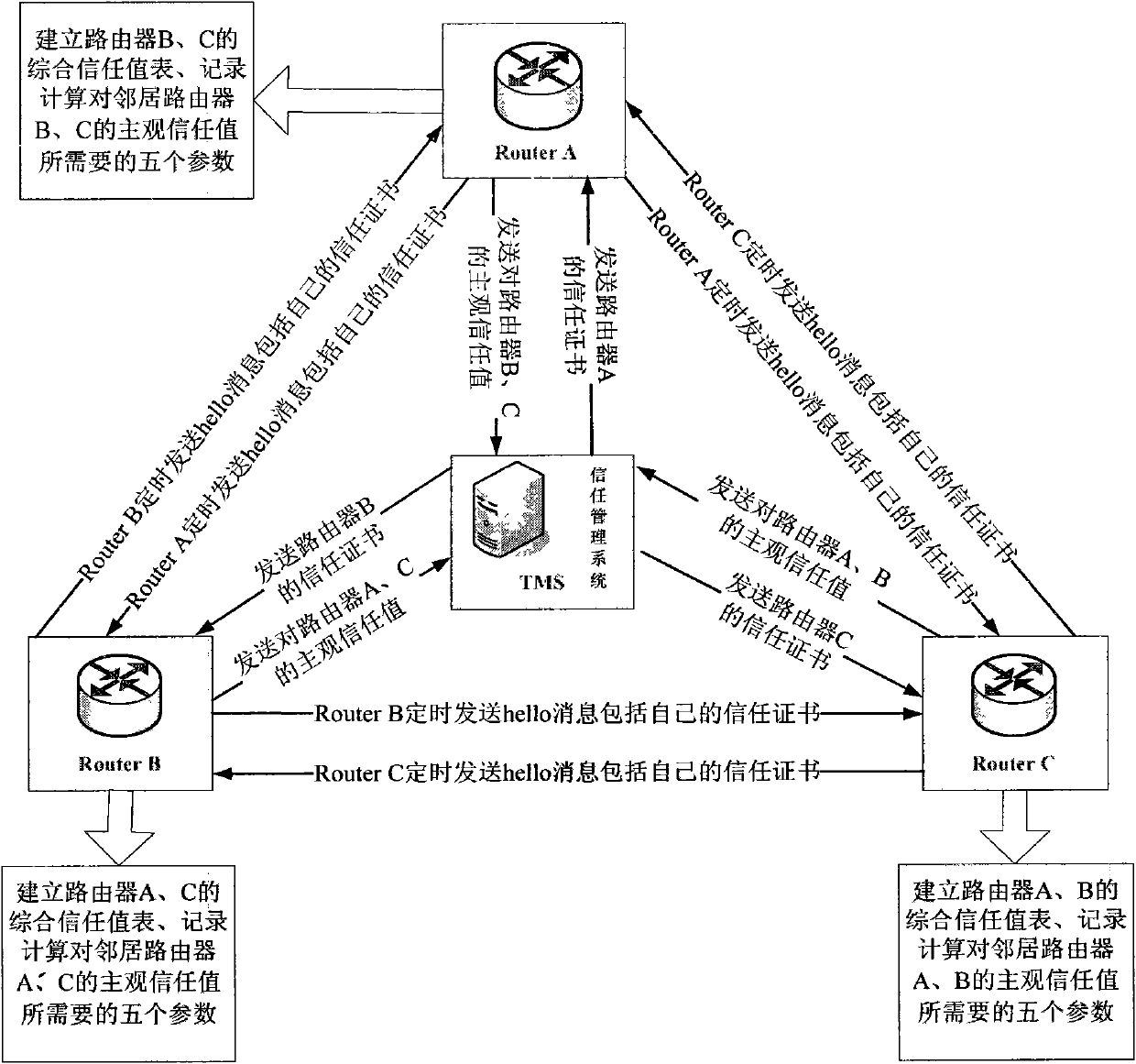
Trust management system based trusted reconstructing method of IP routing protocol
The invention discloses a trust management system based trusted reconstructing method of an Open Shortest Path First (OSPF) routing protocol, which comprises the following steps of: (1) before each router is added into a network, registering to the trust management system, and sending corresponding trust certificates to the routers by the trust management system, the trust certificates including comprehensive trust values of the routers and each being calculated according to safe parameters and configuration parameters of the routers and all the subjective trust value of the neighbor router to the routers by the trust management system; (2) transferring the trust certificates among the routers through hello information, wherein an adjacency relation is not established for the router without the trust certificate, all the routers in the network are ensured to have own trust certificates; (3) each router calculating the subjective trust value of the neighbor router based on network real time parameters including link flow, packet loss probability, retardation, transmission rate of the packet and reliability of the packet, during an interactive work with the neighbor router, calculating a total trust value of the neighbor router by using the comprehensive trust value and the subjective trust value of the neighbor router, and modifying a metric field of a link-state announcement Router_LSA packet as the total trust value and synchronizing a link-state data base;(4) modifying a Dijkstra algorithm, using a reciprocal of the total trust value between the routers as the parameter for the arithmetic computation, selecting the router with higher trust value to generate a shortest path tree, and forming a trust routing list; (5) periodically reporting the subjective trust value of the neighbor routers to the trust management system by each router, simultaneously obtaining the parameter required for computing the subjective trust value, updating the trust certificate of each router at fixed time, and eliminating the router with the overdue trust certificate out of the network to maintain the topological structure of the whole network.
Owner:BEIJING UNIV OF POSTS & TELECOMM
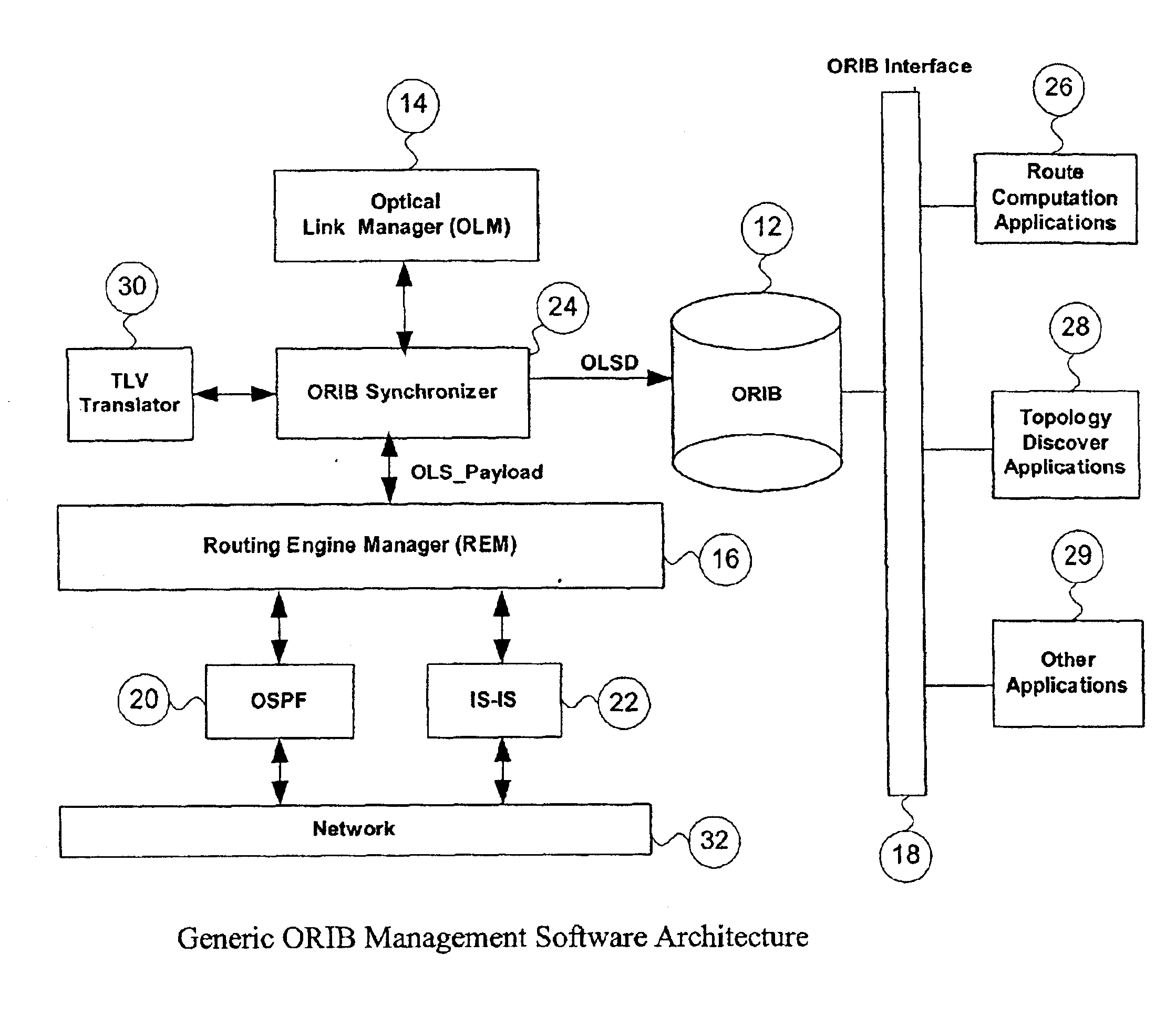
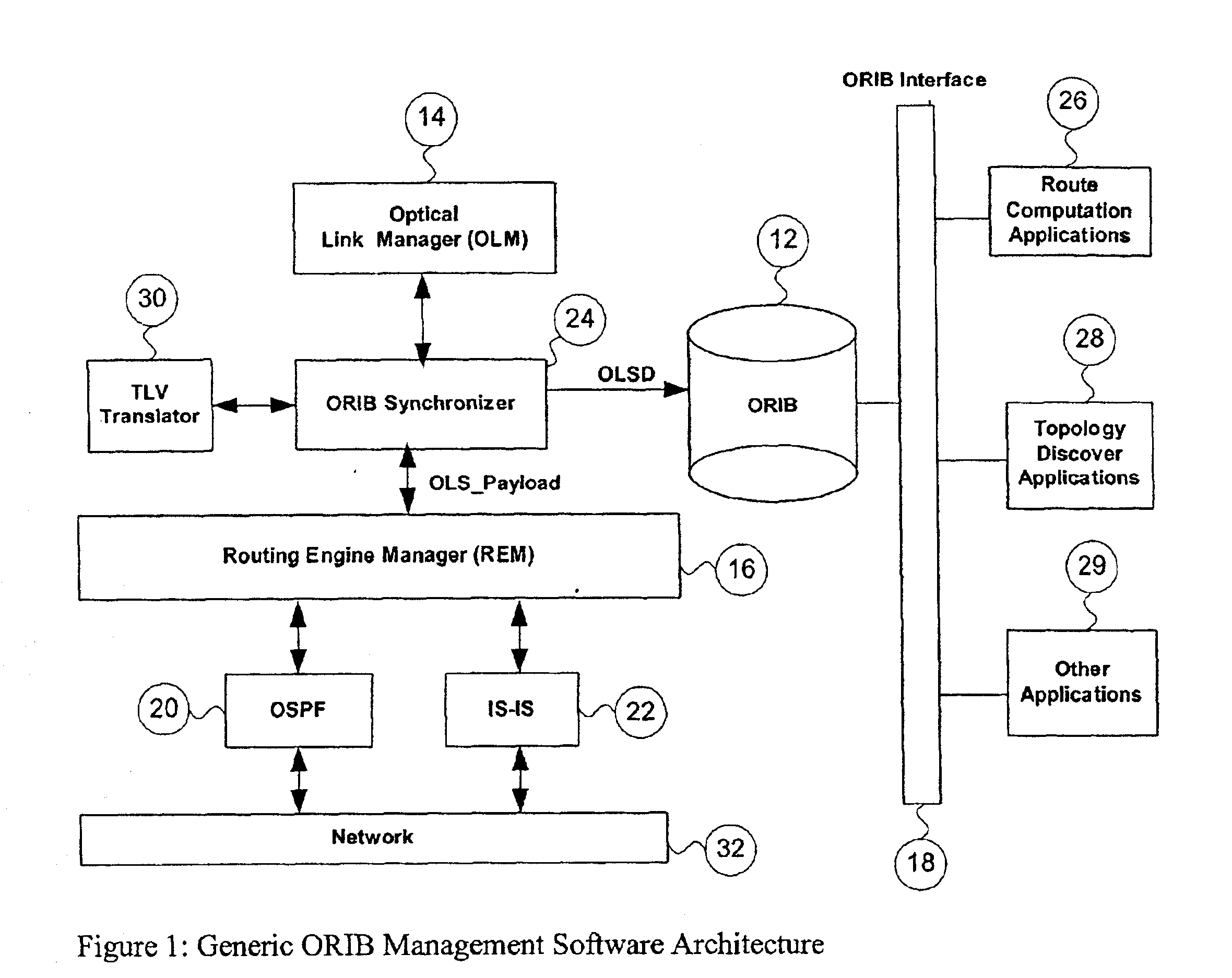
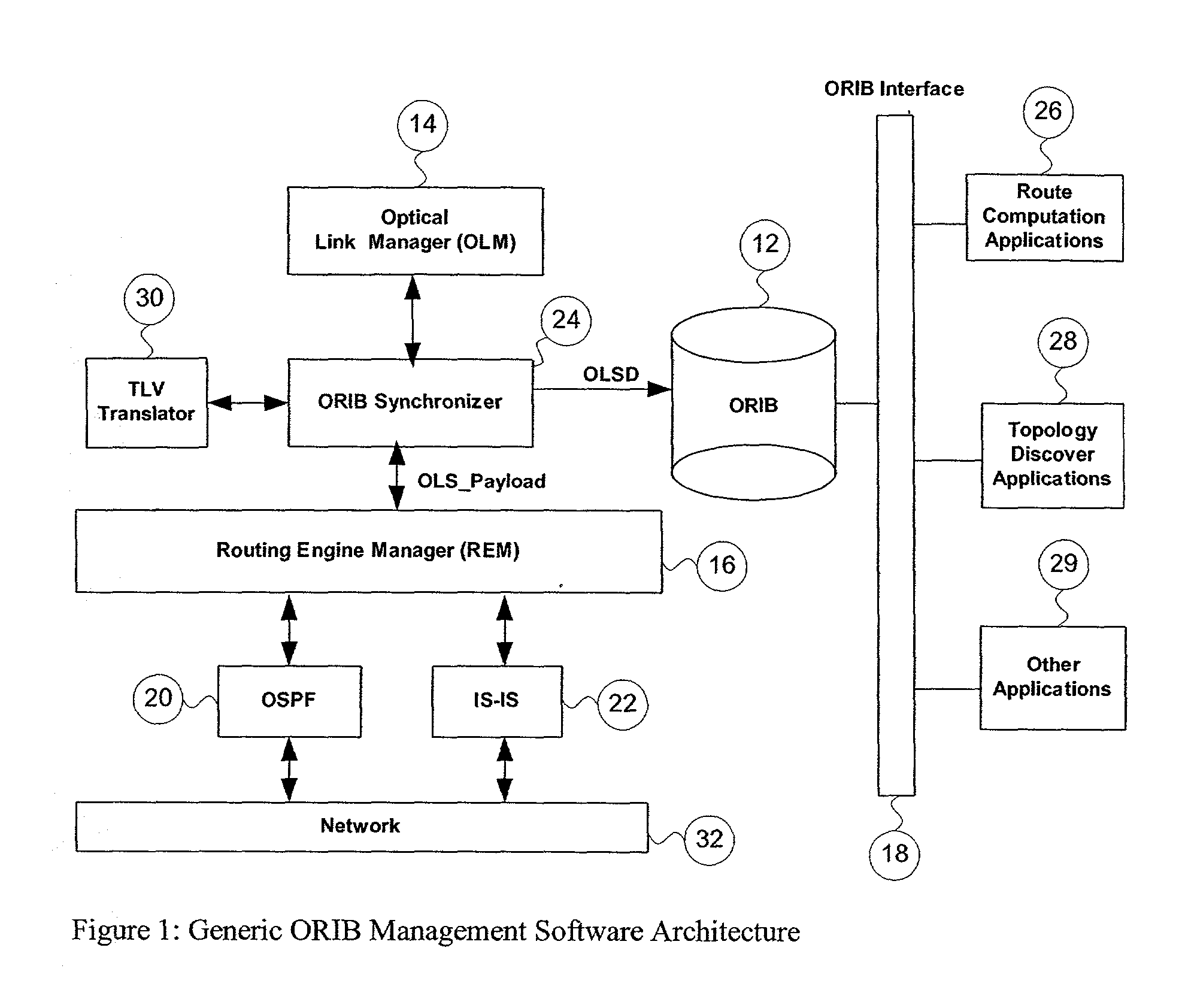
Generic optical routing information base support
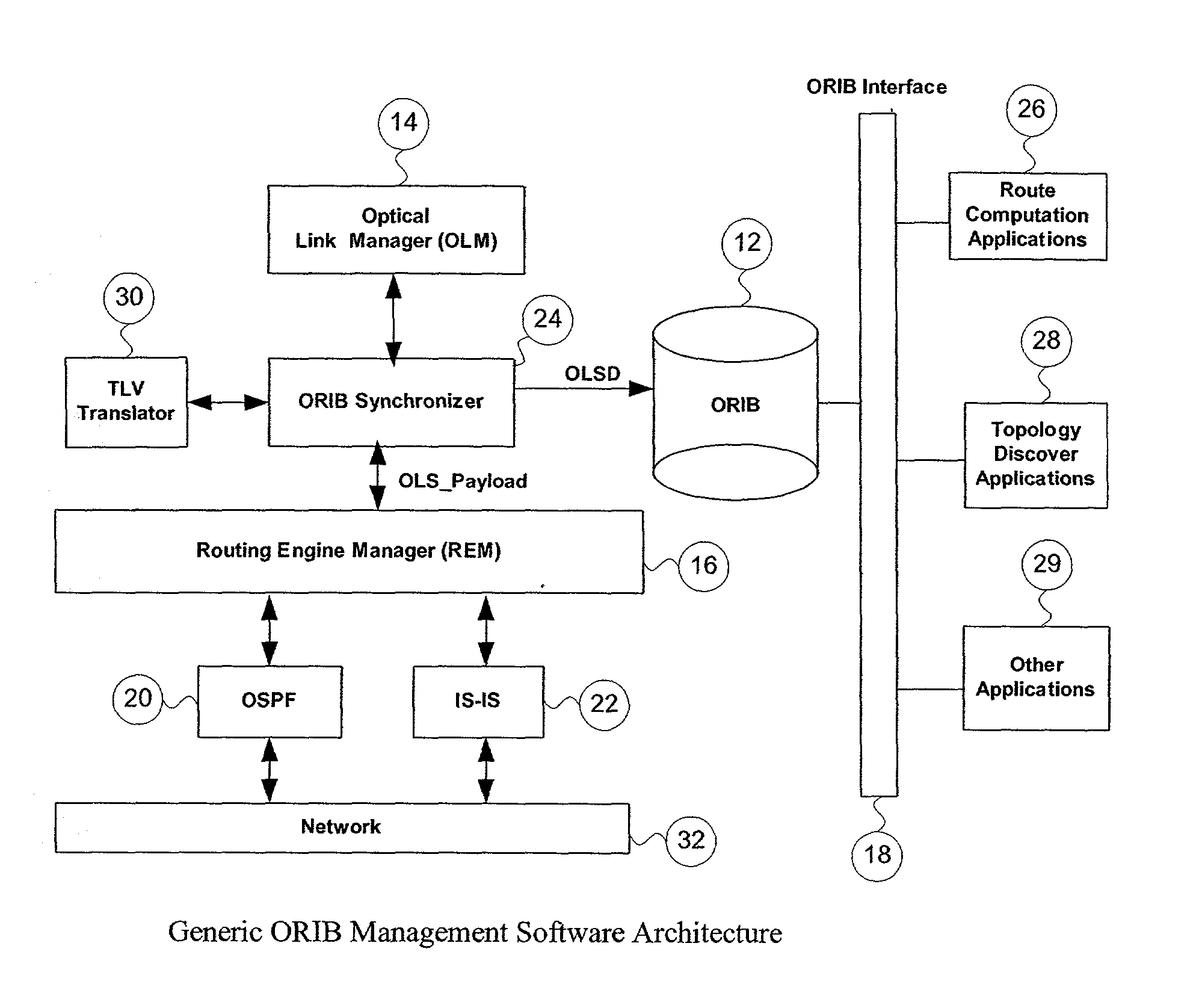
ActiveUS6947669B2Multiplex system selection arrangementsError preventionComputer hardwareInformation repository
This application proposes a solution that makes access to the Optical Link State (OLS) information more efficient for use by upper level applications. Applications are independent of underlying routing protocols. This solution applies to all Link State based IGP protocols with the extension to optical networks, including OSPF and IS-IS.
Owner:MICROSOFT TECH LICENSING LLC
Optimizing flooding of information in link-state routing protocol
InactiveUS7437476B2Prevent floodingEasy to useError preventionTransmission systemsComputer hardwareFlooding algorithm
Owner:CISCO TECH INC
Improved AODV routing protocols adaptive to different motion scenes
ActiveCN107071850ASave bandwidthReduce end-to-end latencyWireless communicationPacket lossAodv routing protocol
The invention discloses improved AODV routing protocols adaptive to different motion scenes. The invention is characterized by comprising the steps of (1), performing routing discovery; (2), performing routing selection; (3), performing routing activation; and (4), performing routing maintenance. By means of the improved AODV routing protocols disclosed by the invention, the average relative motion speed of various unmanned aerial vehicles and adjacent unmanned aerial vehicles can be obtained through GPS signals carried by the various unmanned aerial vehicles, so that the change speed of a network topological structure is judged; different routing protocols are selected by judging the change speed of the network topological structure; namely, different improved AODV routing protocols are selected according to the average relative motion speeds of the unmanned aerial vehicles; the improved AODV routing protocols can be adaptive to the converted topological structures of the unmanned aerial vehicles; therefore, the network bandwidth is reduced; the end-to-end delay is reduced; and the packet loss ratio is reduced.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Method for realizing congestion control of Ad Hoc network based on multi-path routing protocol
ActiveCN106851727AAvoid blindnessImprove efficiencyNetwork traffic/resource managementNetwork topologiesPacket lossMultipath routing protocol
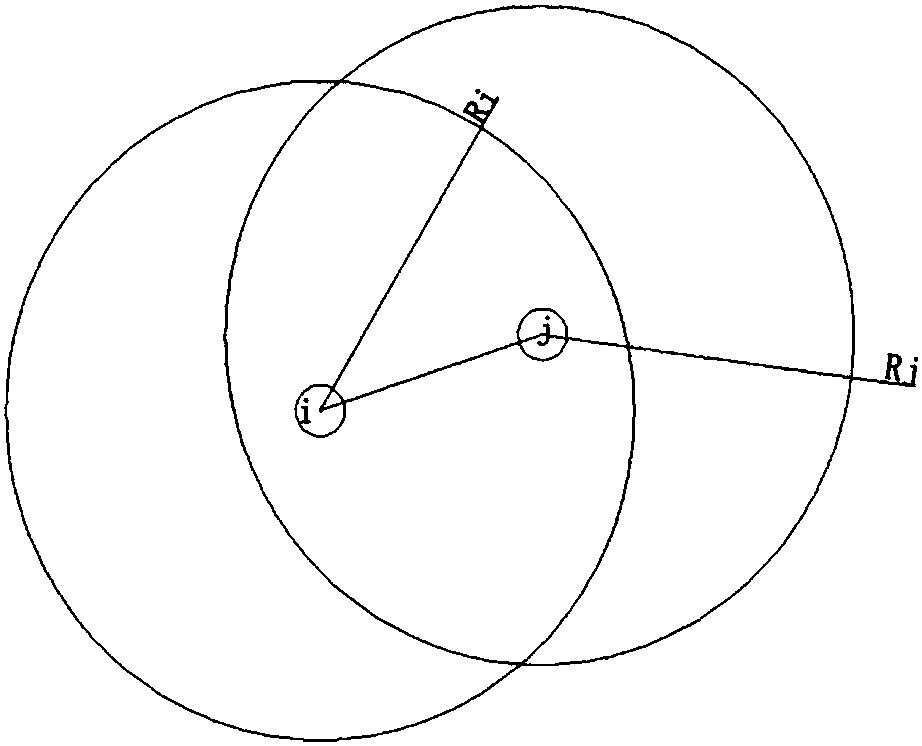
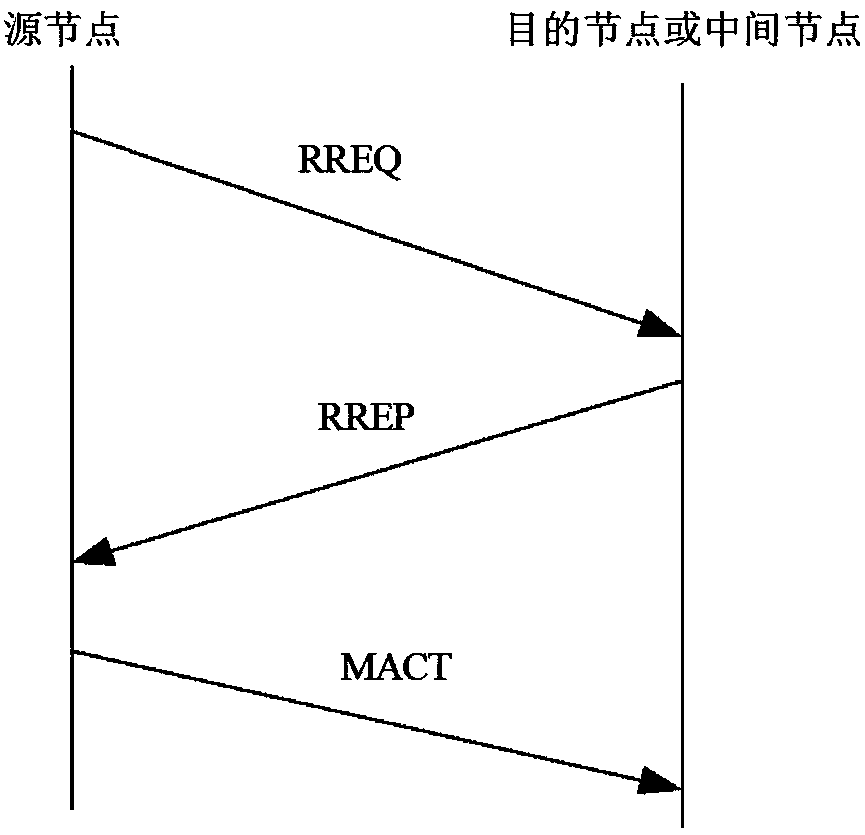
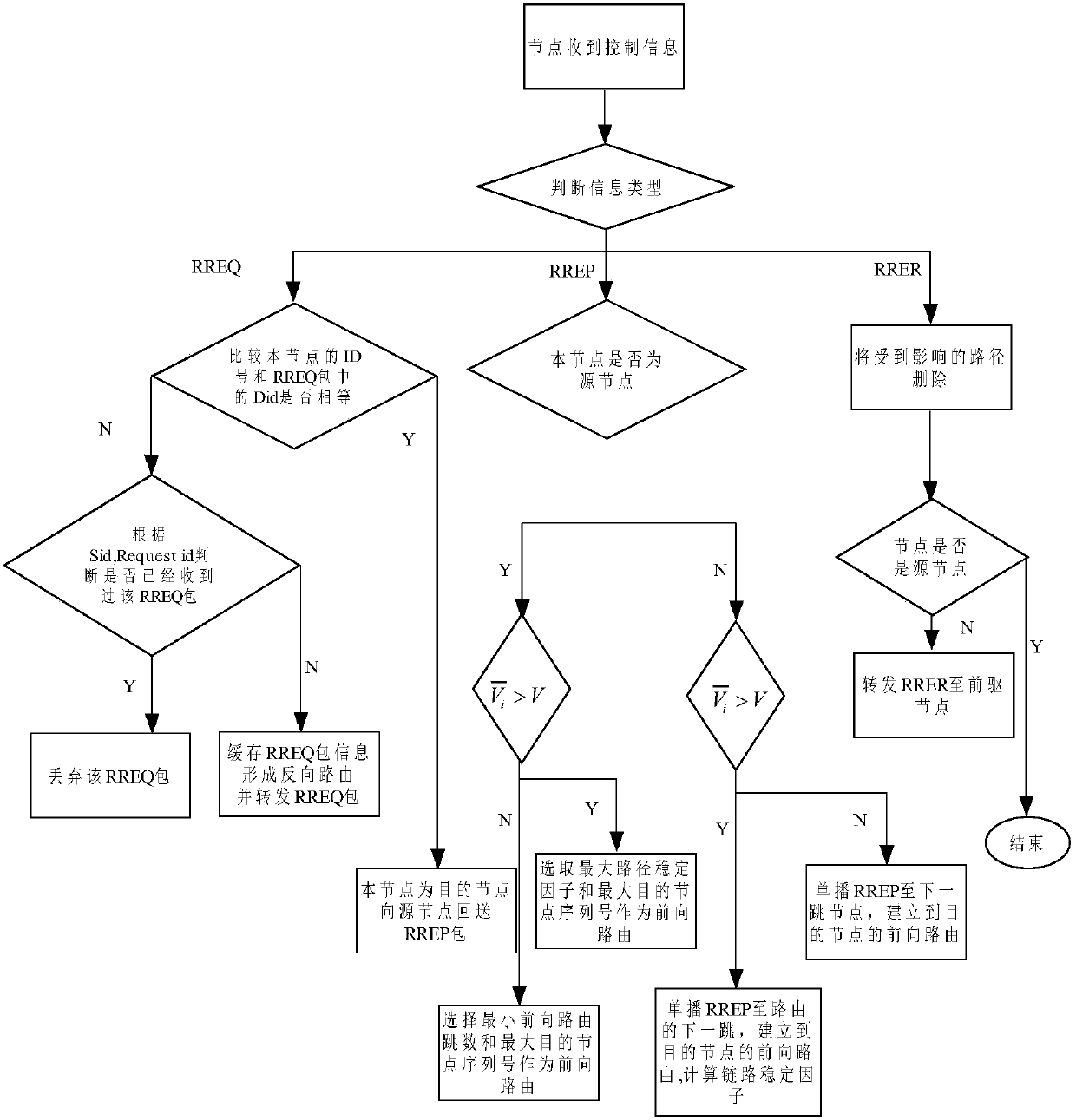
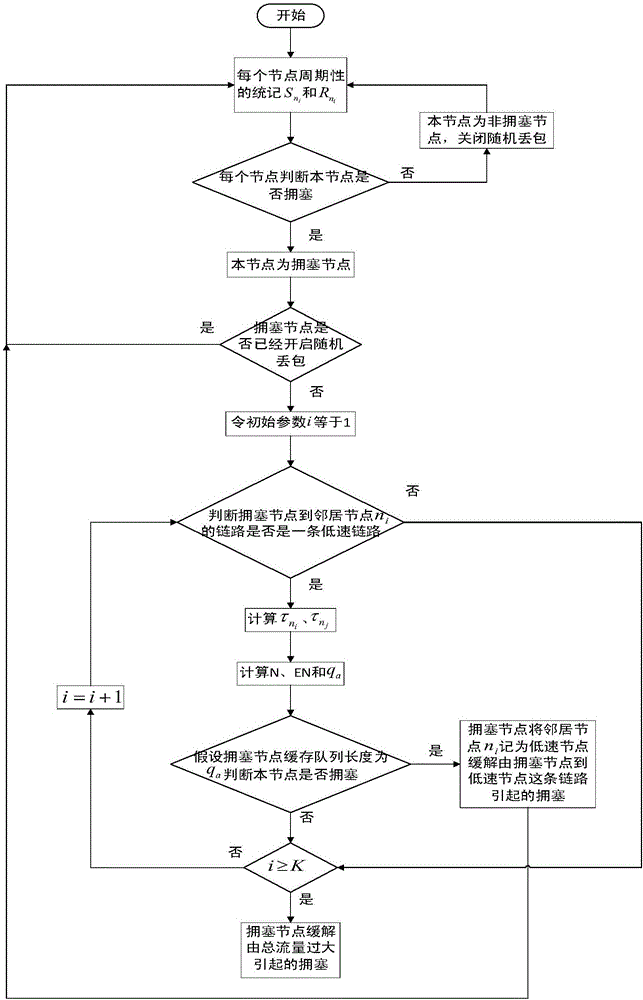
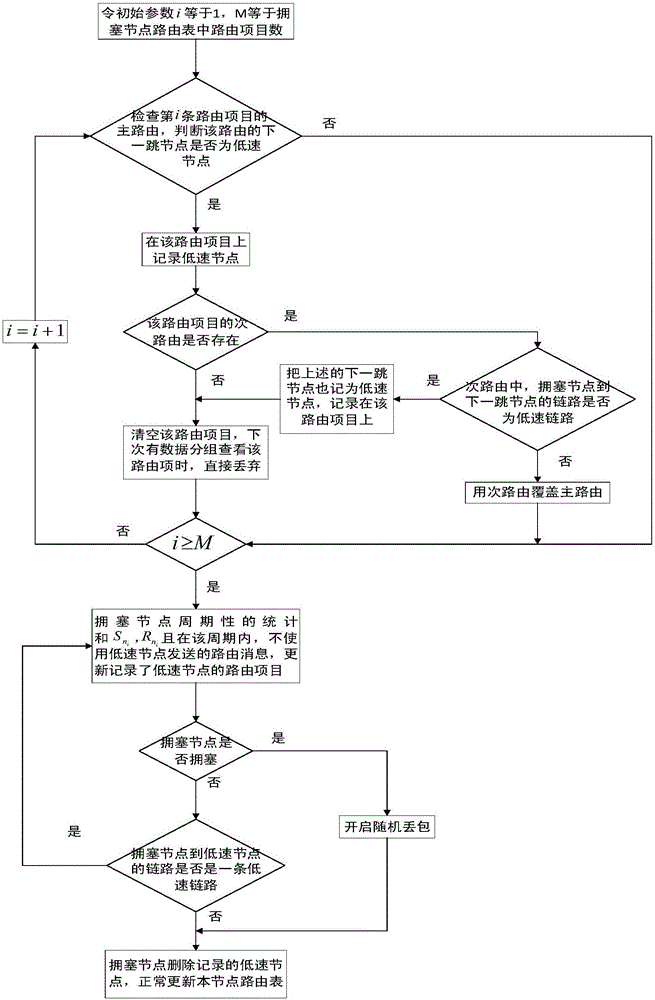
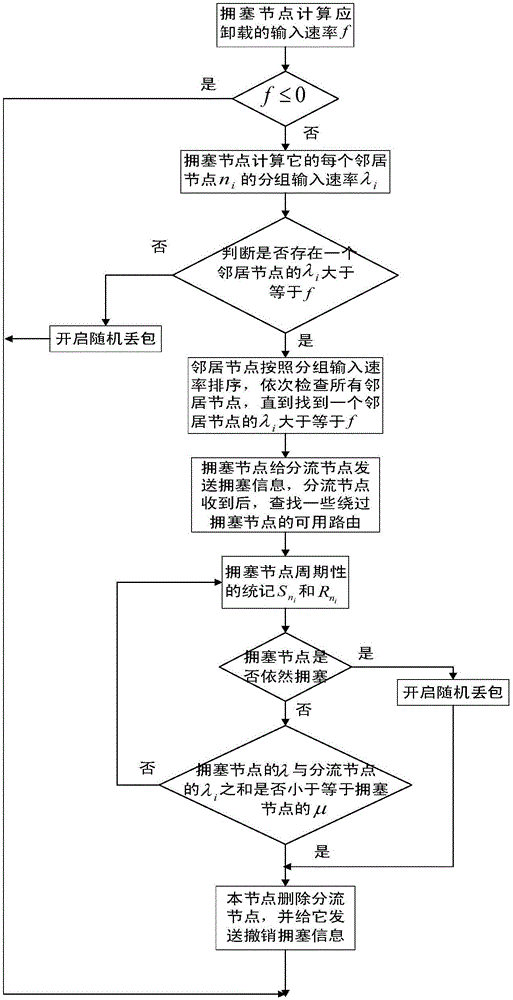
The invention discloses a method for realizing congestion control of Ad Hoc networks based on a multi-path routing protocol, which can mainly solve the problem that the prior art is lack of congestion control mechanisms, and the sharply-decreased network throughput and high node packet loss caused by congestion is further produced. The implementation scheme of the method comprises the following steps: 1, obtaining the periodic statistical data of each node in the network, and judging whether the node is congested; 2, analyzing whether the congestion reason of the congested node is caused by using the low-speed links or caused by excessive total flow of the congested node; 3, relieving the congestion of the congested node that is caused by using the low-speed links through the means of suppressing the low-speed links; and 4, relieving the congestion of the congested node that is caused by excessive total flow of the congested node through the means of flow scheduling or random packet loss. Compared with a traditional congestion control method, the method disclosed by the invention ensures that the targeted relief measures can be taken according to different congestion reasons, the network throughput can be further increased, and the method can be applied to the Ad Hoc networks.
Owner:XIDIAN UNIV
Automatically deployable virtual router establishment method
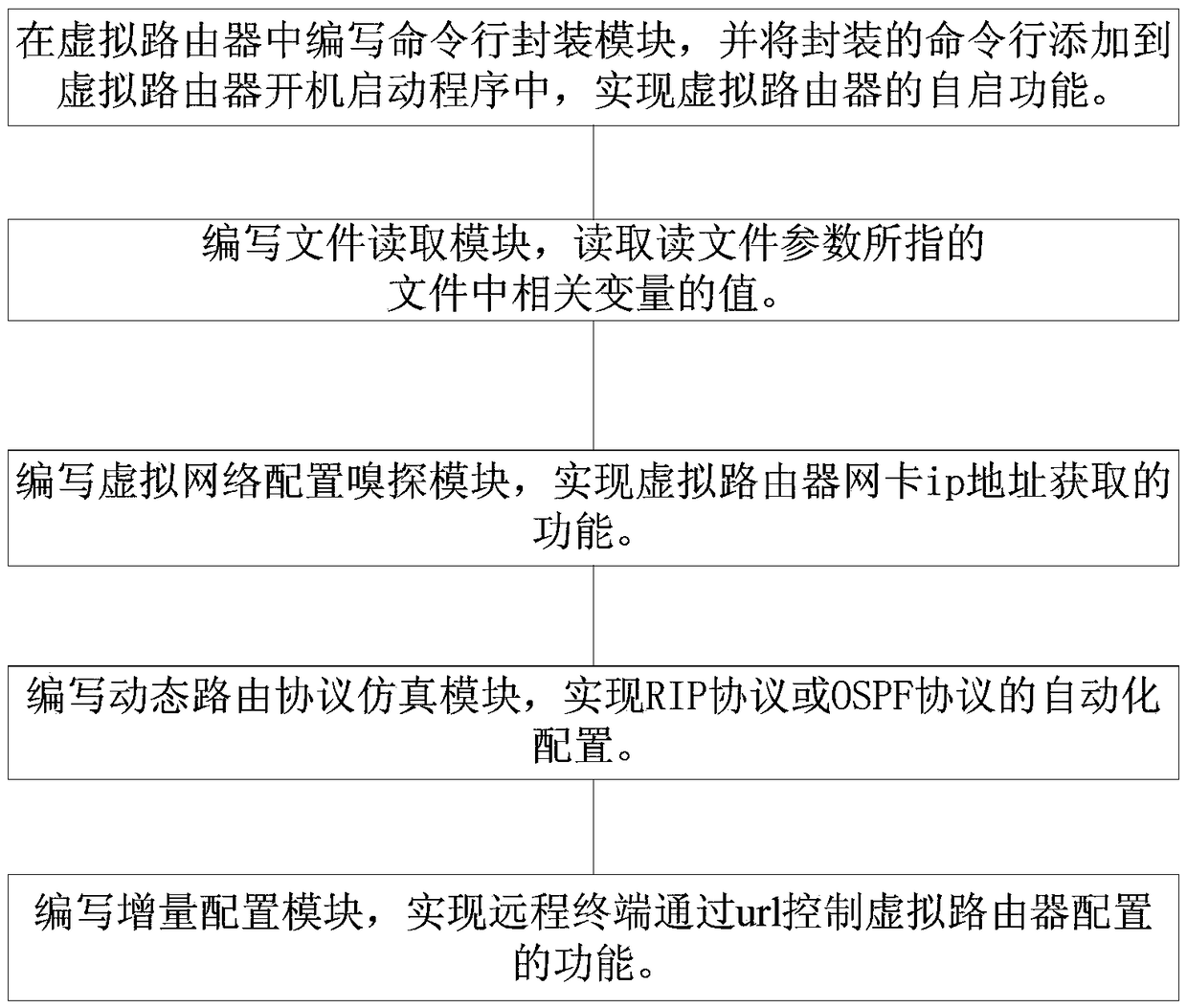
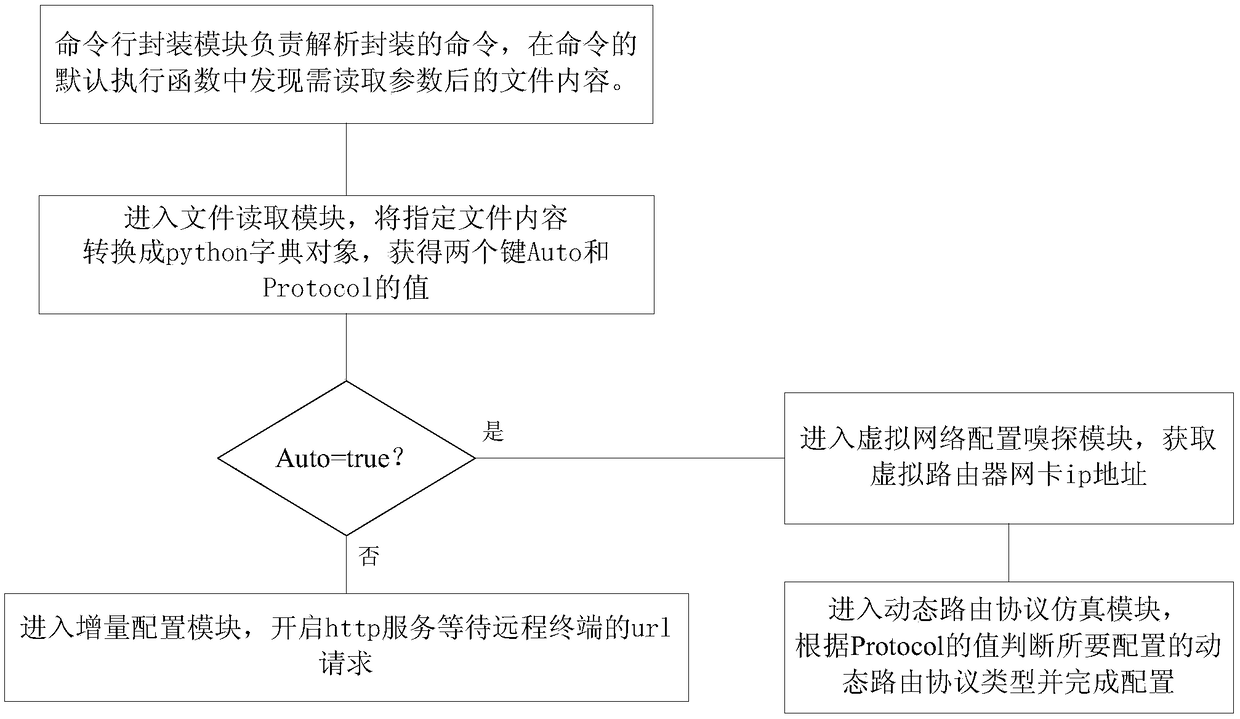
ActiveCN105827464AImplement a dynamic routing protocolAutomatic and flexible deploymentData switching networksIp addressAdaptive routing
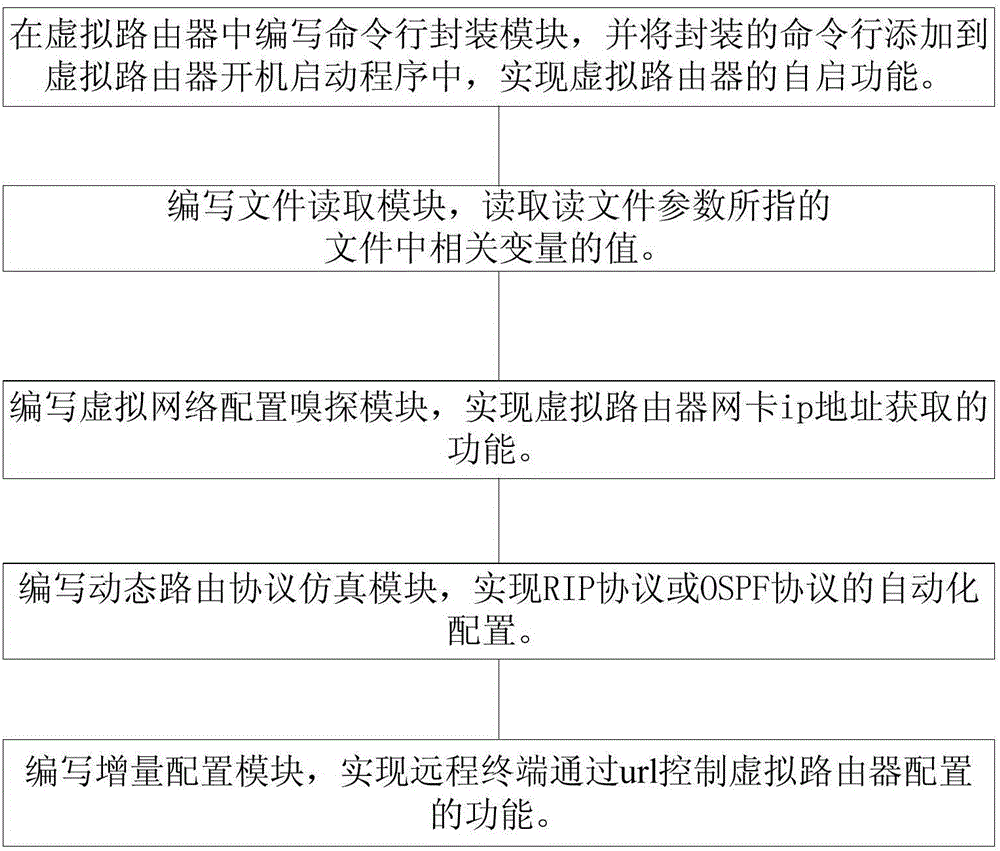
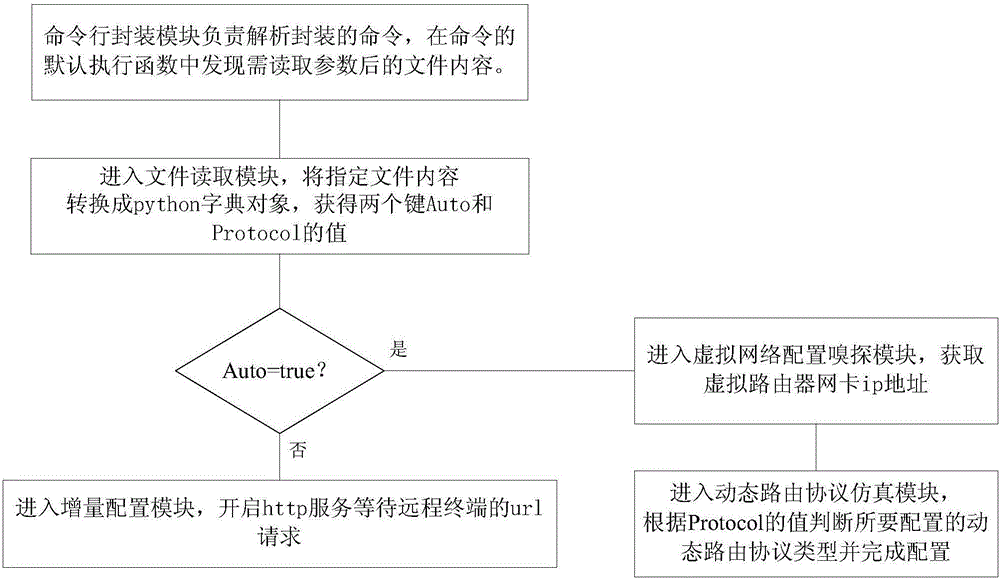
The invention provides an automatically deployable virtual router establishing method, comprising the following steps of S1, compiling a command line packaging module in a virtual router, and adding a packaged command line into applications run on start-up of the virtual router, thus achieving the self-starting function of the virtual router; S2, compiling a file reading module, and reading values of correlated variables in files to which file reading parameters point, wherein the correlated variables in the files to which the file reading parameters point comprise an automatic deployment variable of which the value is true or false, and a routing protocol variable of which the value is an appointed dynamic routing protocol; S3, compiling a virtual network configuration sniffing module, and achieving a function of acquiring the ip address of a network adapter of the virtual router; S4, compiling a dynamic routing protocol simulation module, and achieving the automatic configuration of the dynamic routing protocol based on the steps S2 and S3; and S5, compiling an increment configuration module. According to the method, the user can flexibly and conveniently perform virtual network management.
Owner:无锡新敏通网络技术有限公司
Control plane structure of virtual routing device and control method thereof
InactiveCN102231709AFlexible controlStable maintenanceData switching networksAddress Resolution ProtocolRouting table
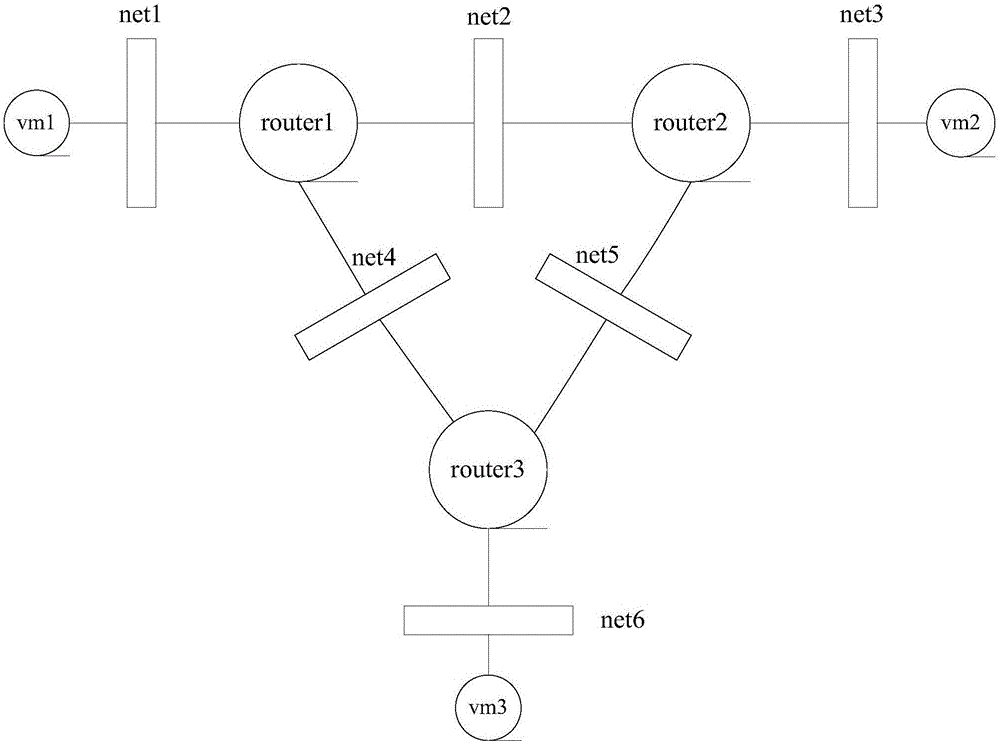
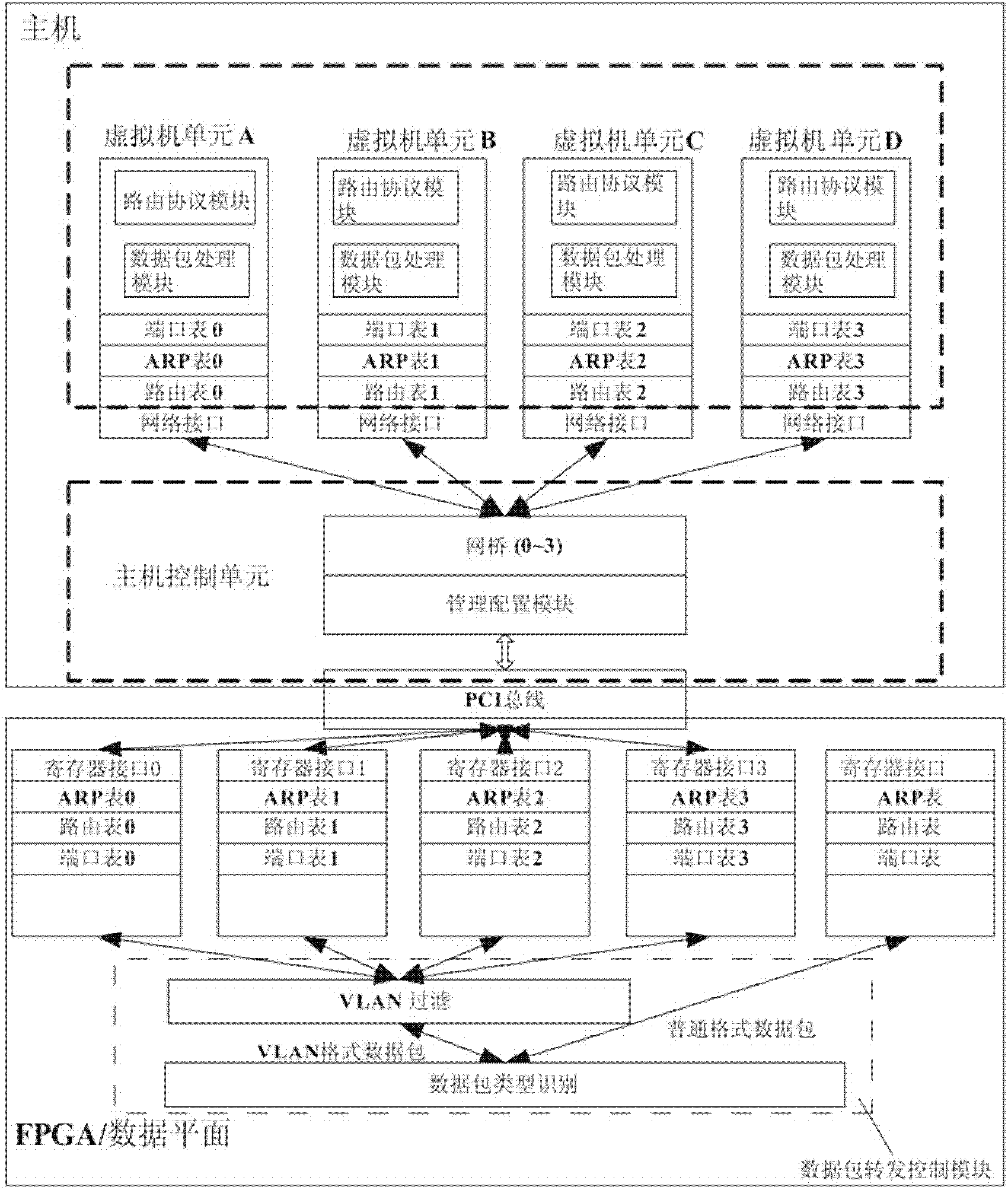
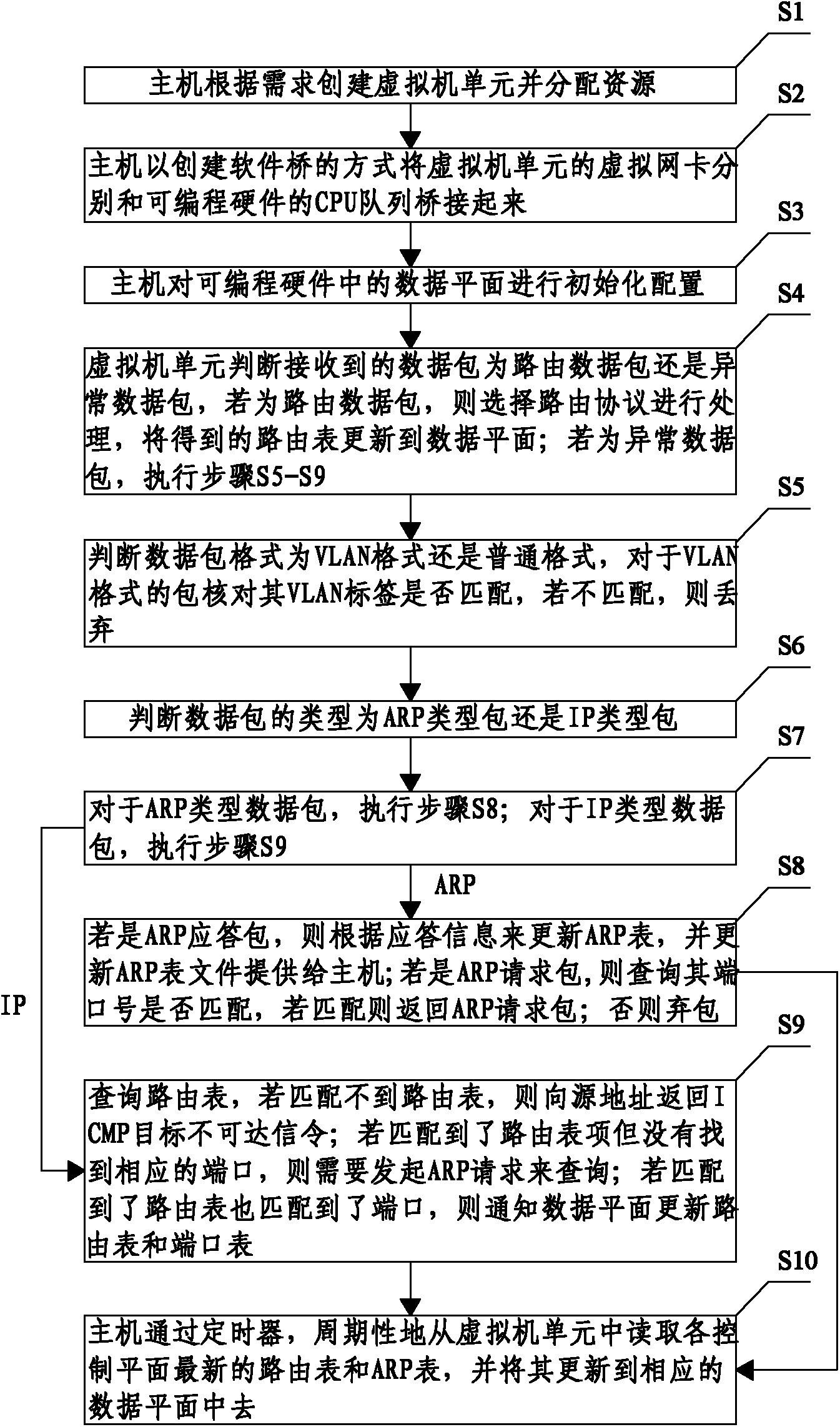
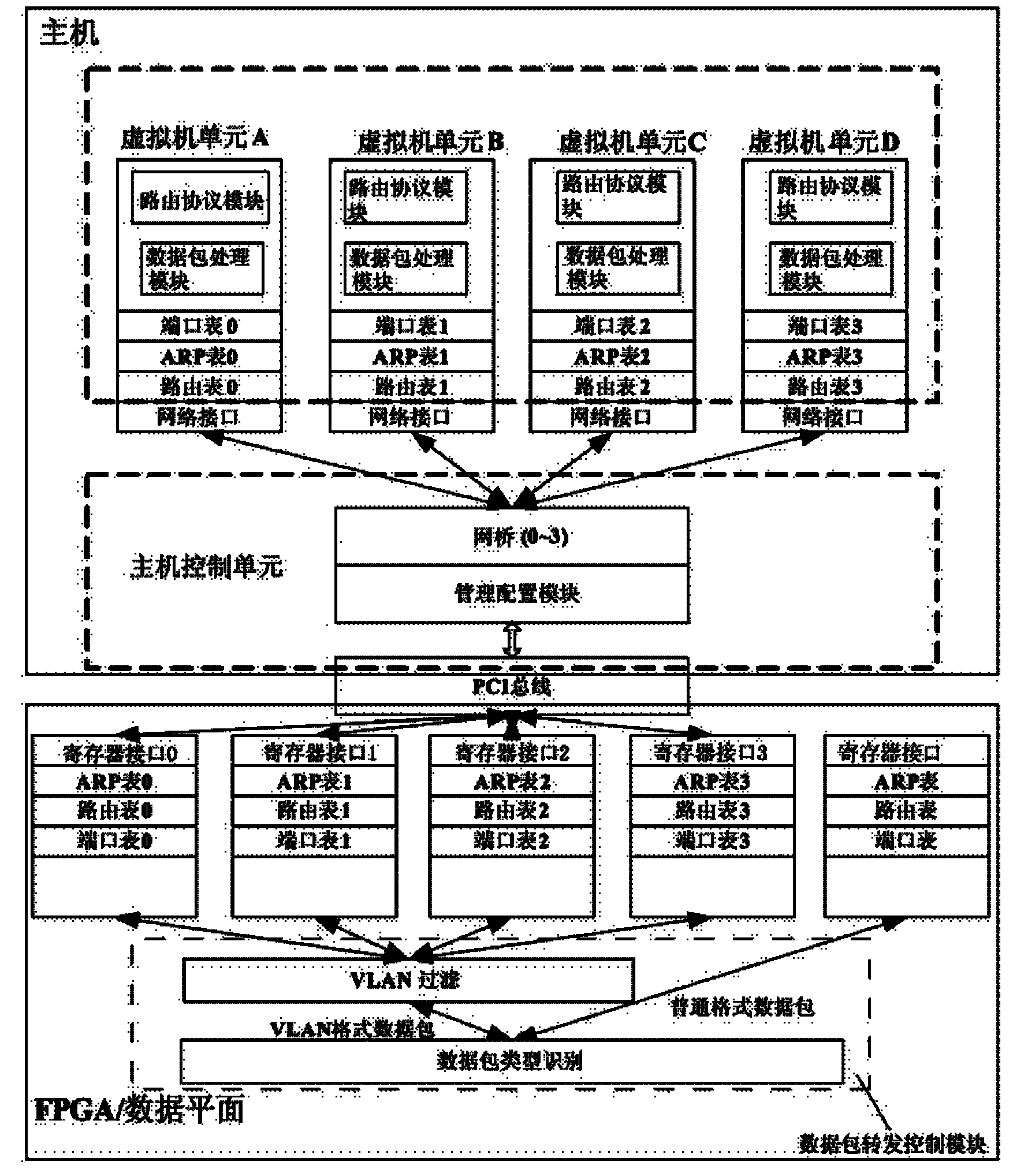
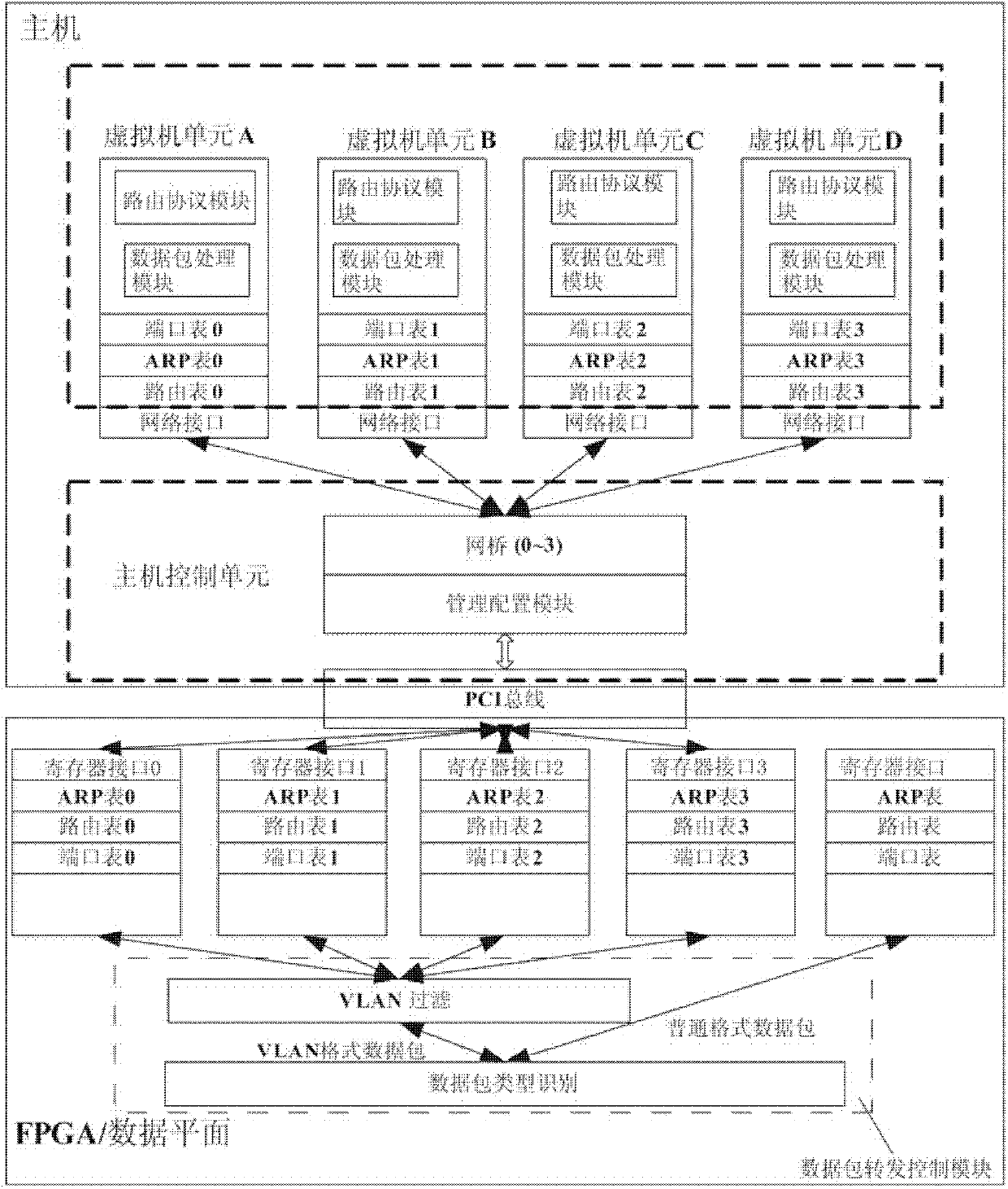
The invention discloses a control plane structure of a virtual routing device and a control method thereof, and relates to the technical field of Internet. The control plane structure comprises a host control unit and a plurality of virtual machine units, wherein the host control unit is used for realizing user interaction and management and control over a data plane and the virtual machine units, and periodically updating a routing table and an address resolution protocol (ARP) table in the data plane; and the virtual machine unit is used for realizing a routing protocol processing function and a data packet processing function, generating and updating the routing table and the ARP table in real time, and providing the routing table and the ARP table for the host control unit. The virtual routing device comprises programmable hardware and a host, wherein the programmable hardware is used for realizing a data plane function. By the structure and the method, a proper routing protocol can be flexibly selected according to an application scenario and stably maintained, table entries can be updated in real time, the flexible configuration of the data plane can be realized, and accurate responses can be given to the needs of a user in real time.
Owner:TSINGHUA UNIV
Hybrid cross-layer routing protocol for MANETs
ActiveUS8665890B2Short delayEasy to deployError preventionTransmission systemsRouting decisionProtocol design
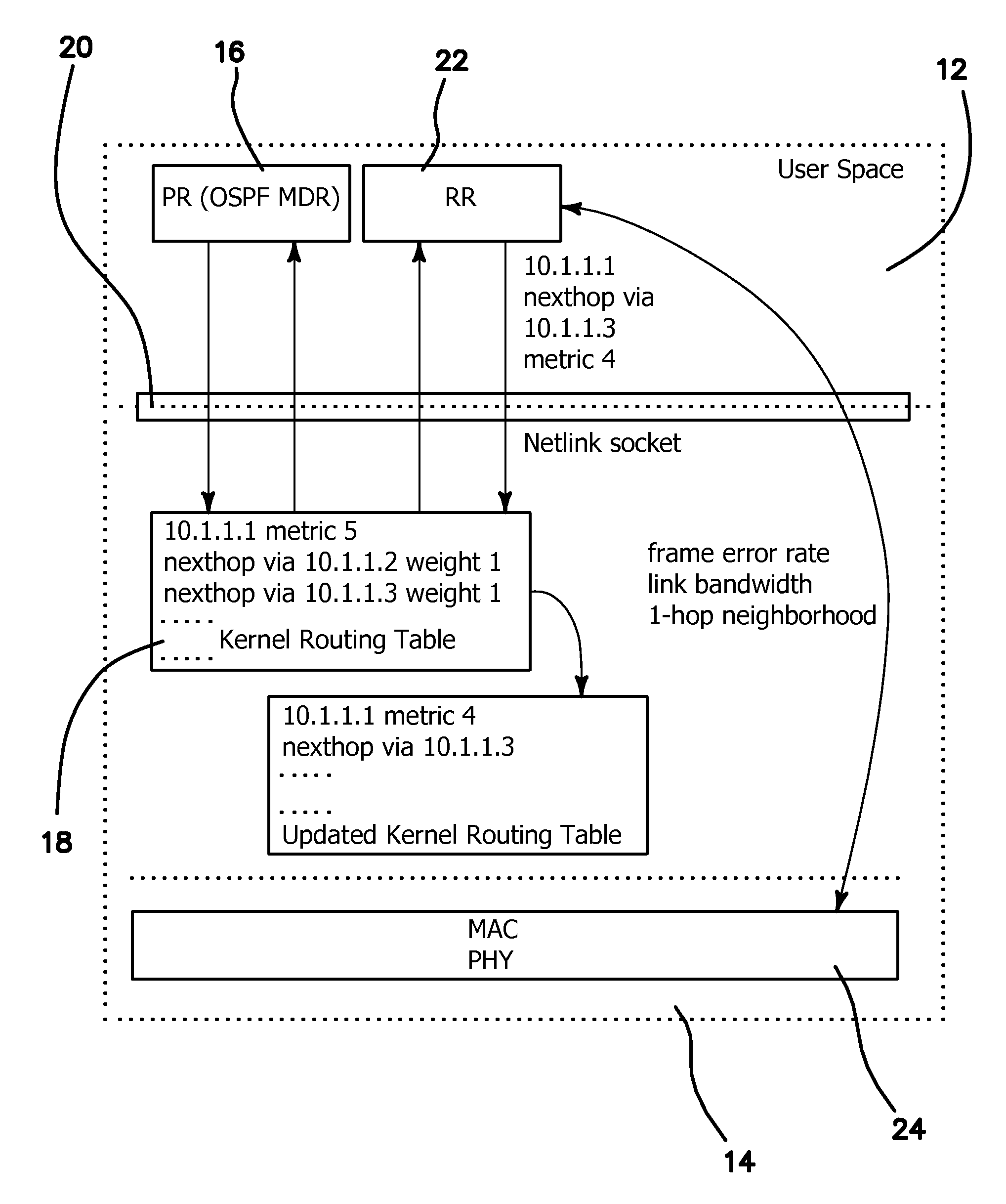
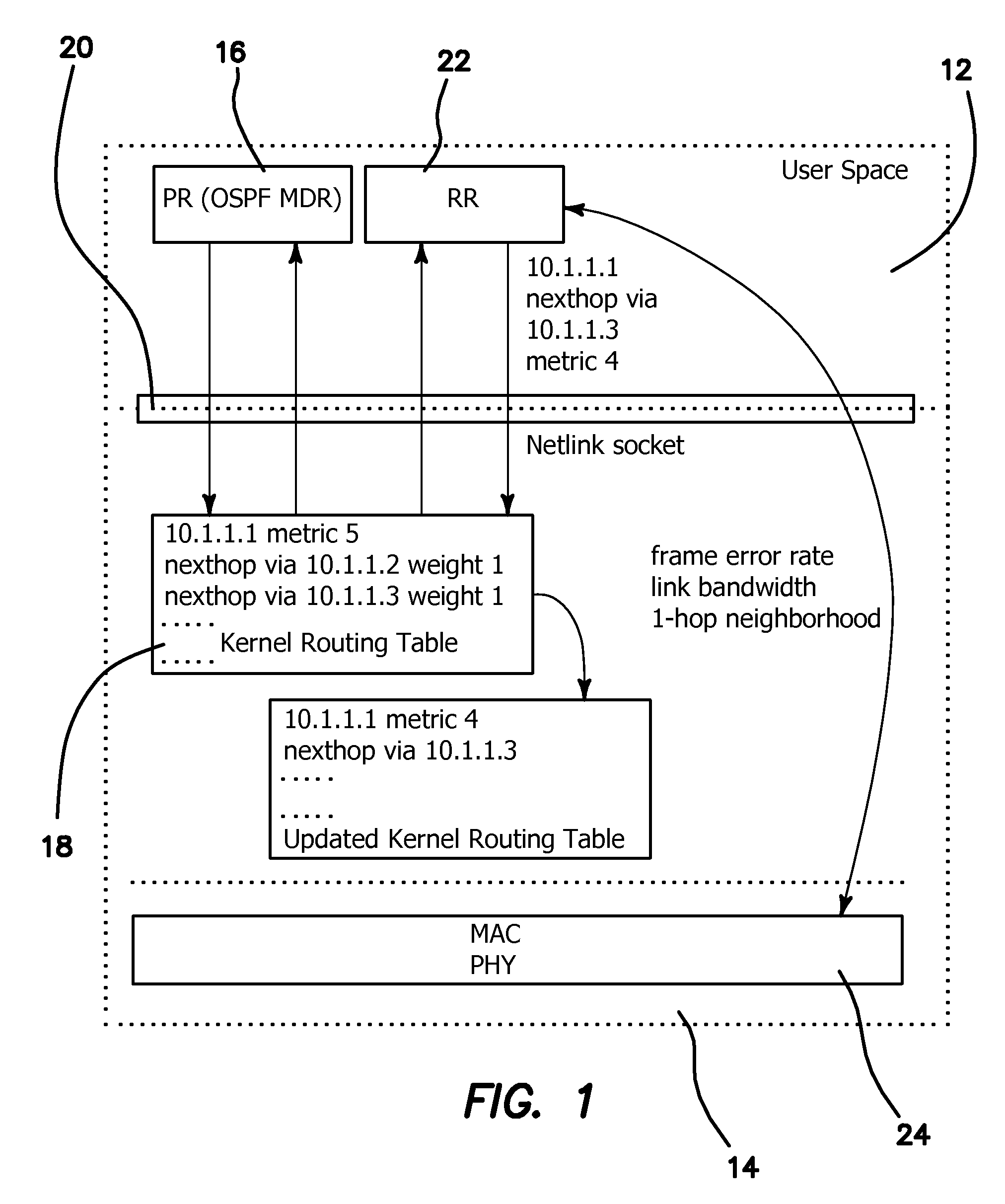
A Hybrid Cross-Layer Routing (HCLR) protocol designed and implemented based on the premise of being able to leverage a pair of proactive and reactive routing schemes in Mobile Ad Hoc Networks (MANETs) which is used to compensate against wireless link effects thereby allowing for making more intelligent routing decisions. Compared to standalone proactive or reactive routing protocols, HCLR provides a two-tier improvement logic by performing local on-demand search in an n-hop neighborhood utilizing a 2-tuple cross-layer routing metric. HCLR is implemented in a Linux Quagga suite and its performance improvements compared to OSPF MANET Designated Routing (MDR) through emulation studies is demonstrated.
Owner:RGT UNIV OF CALIFORNIA
Generic optical routing information base support
ActiveUS20020126344A1Multiplex system selection arrangementsError preventionComputer hardwareInformation repository
This application proposes a solution that makes access to the Optical Link State (OLS) information more efficient for use by upper level applications. Applications are independent of underlying routing protocols. This solution applies to all Link State based IGP protocols with the extension to optical networks, including OSPF and IS-IS.
Owner:MICROSOFT TECH LICENSING LLC
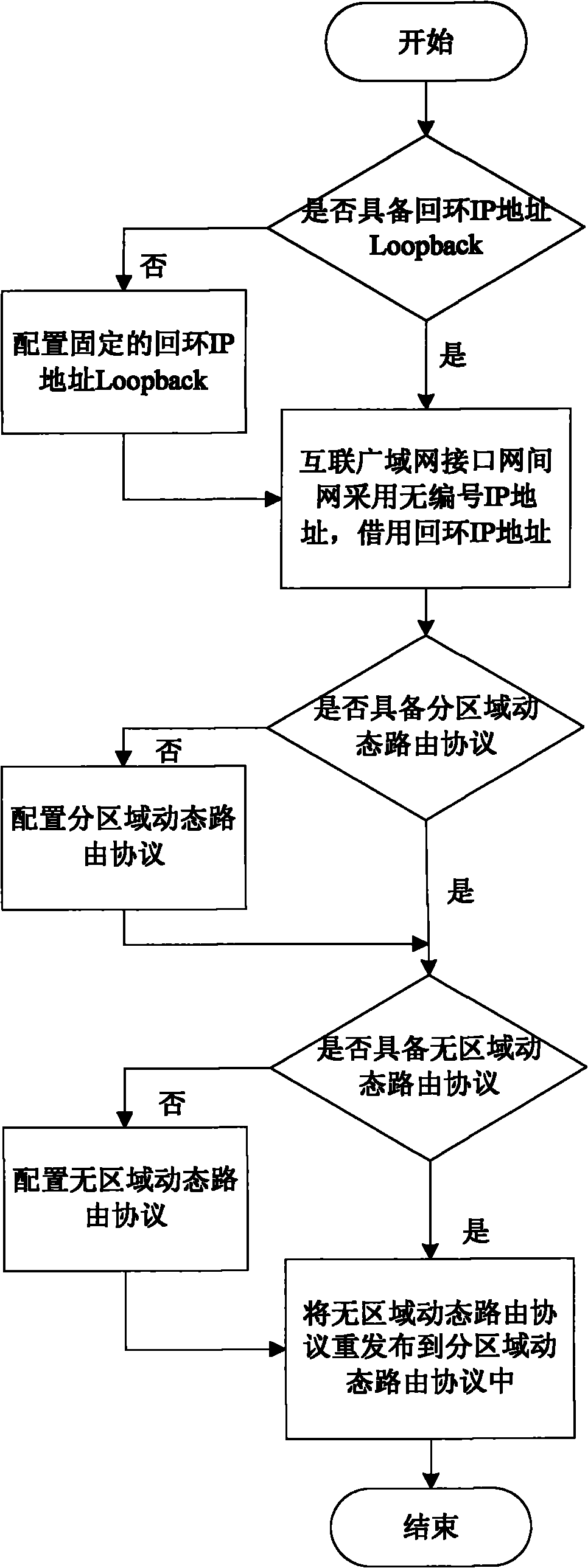
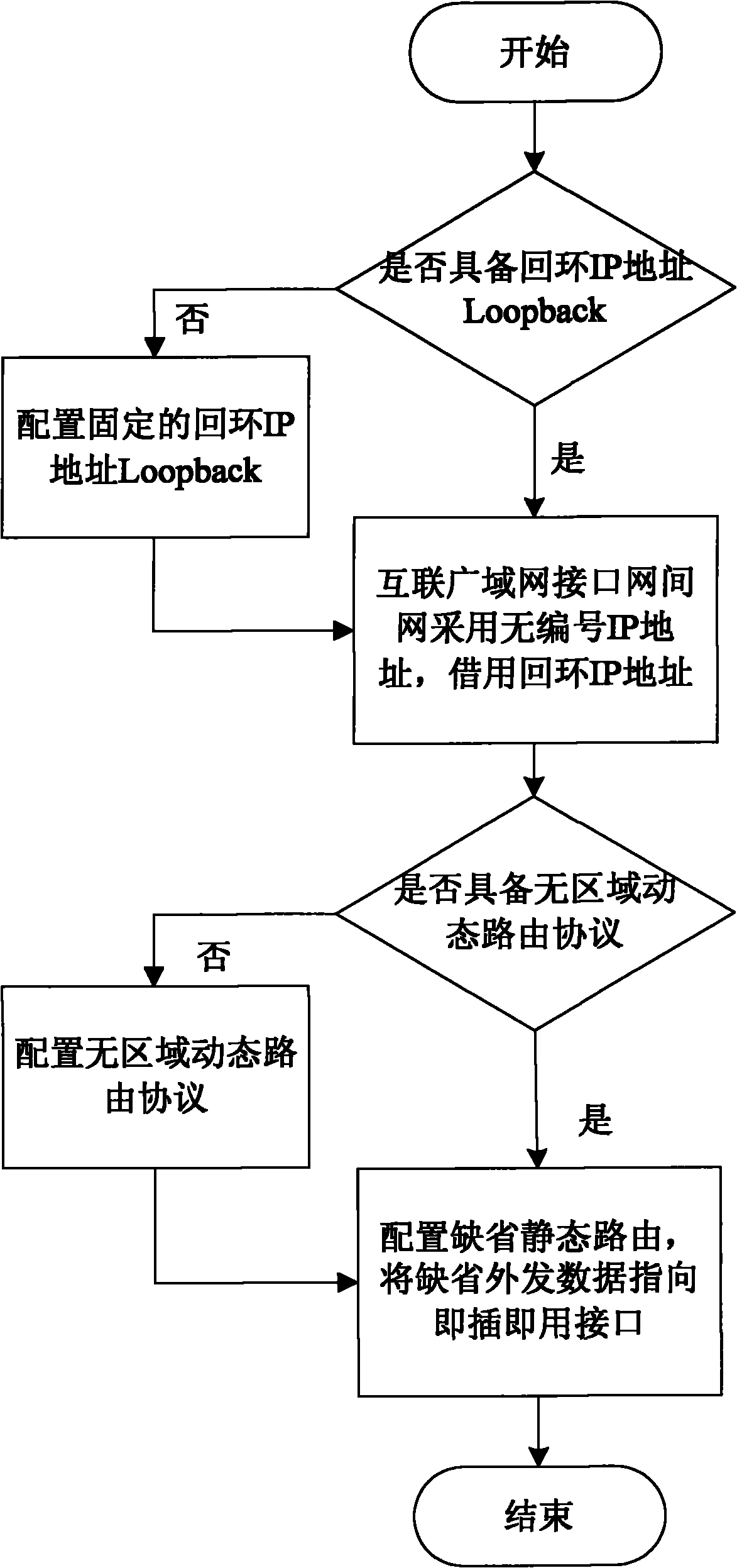
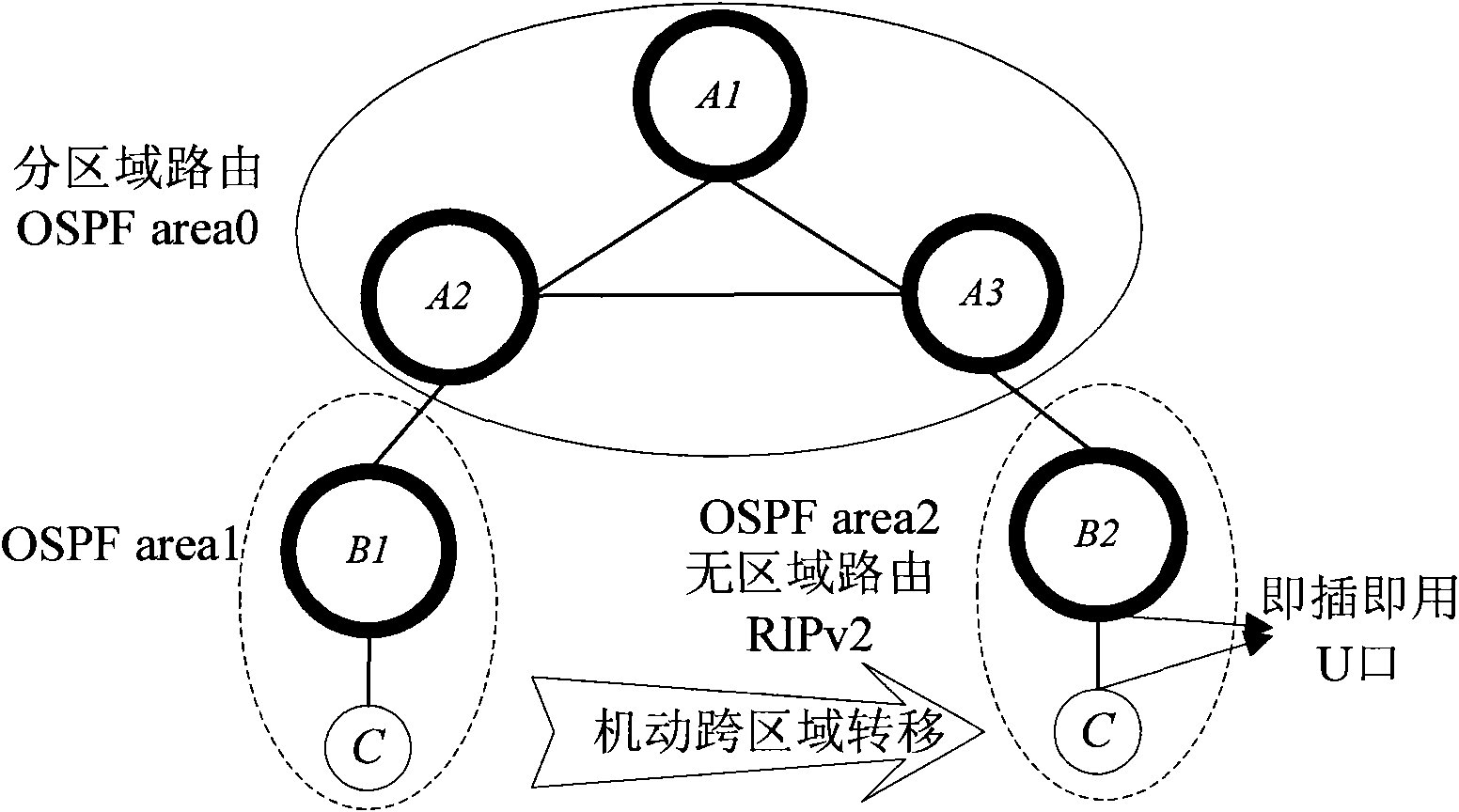
Router cross-autonomy region plug and play method
The invention discloses a router cross-autonomy region plug and play method. The method comprises the following steps of: using an IP unnumbered part: using an unnumbered address on the wide area network interfaces of routers of an access node and a maneuvering system; taking a region-free routing protocol as a transition routing protocol: adding the region-free routing protocol on a maneuvering router and the router of access node; performing routing redistribution by the access node: redistributing the region-free dynamic routing protocol to a sub-region dynamic routing protocol on the router of access node; and performing default route by the maneuvering system: adding a static default route on the maneuvering router. By the method, the maneuvering system can conveniently access any access node or the access node accesses any new maneuvering system, and the two access parts do not need to be subjected to replanning or configuration modification, and the plug and play interconnection is realized.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
Dynamic multi-path routing algorithm based on interference activity estimation
The invention provides a dynamic multi-path routing algorithm based on interference activity estimation. The algorithm mainly comprises the following steps: a node determines an interference activity (IA) value according to identification of an interfered state, and introduces the node interference activity value into a multi-path routing protocol; by utilizing the IA value combined with a multi-path discovery mechanism, route discovery from a source node to a target node is completed, and route selection and maintenance of interference avoidance are realized based on the interference activity value. The invention can provide a route with a minimal relative interfered degree for a node with a complex wireless network environment, quantity of searched paths is more than AOMDV and loop and 'cut-off' problems are not existed, protocol cost is low, an original multi-path route protocol is improved, and the algorithm in the invention can be adapted to a more complex wireless network environment.
Owner:NO 63 RES INST HEADQUARTERS OF THE GENERAL STAFF PLA
Method for adapting the OSPF routing protocol to radio networks
InactiveUS20040017801A1Provide compatibilityData switching by path configurationNetwork connectionsTelecommunicationsRadio networks
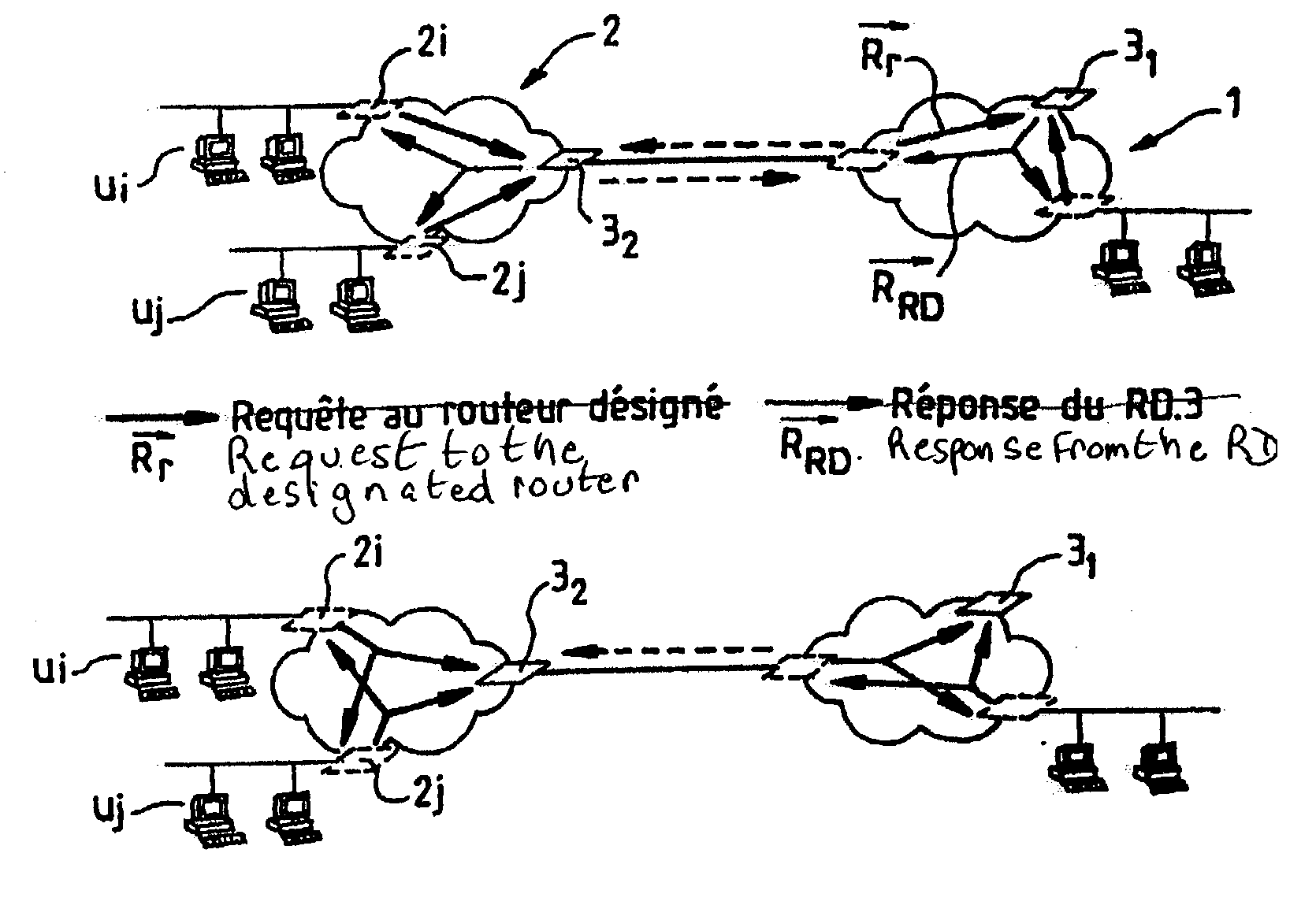
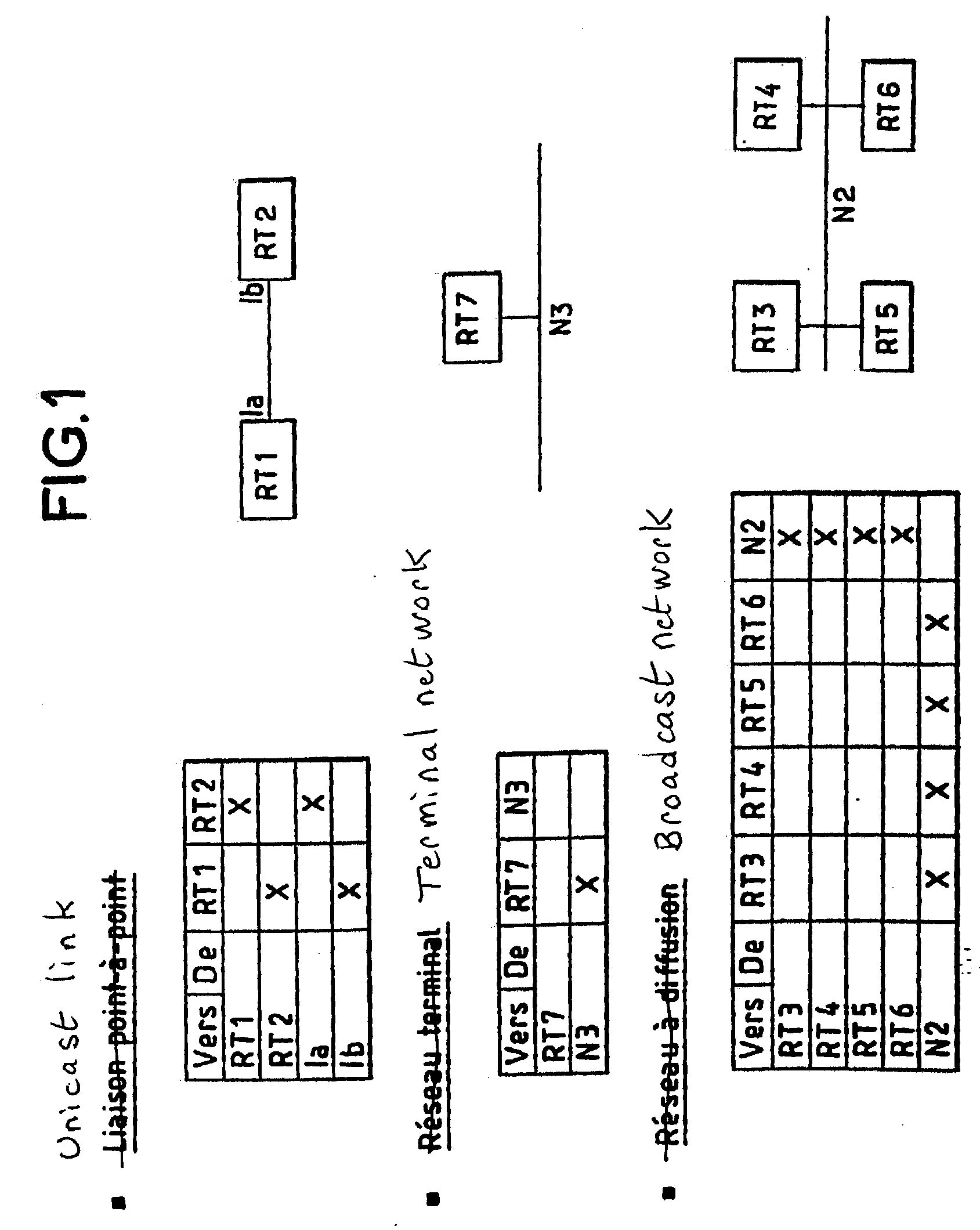
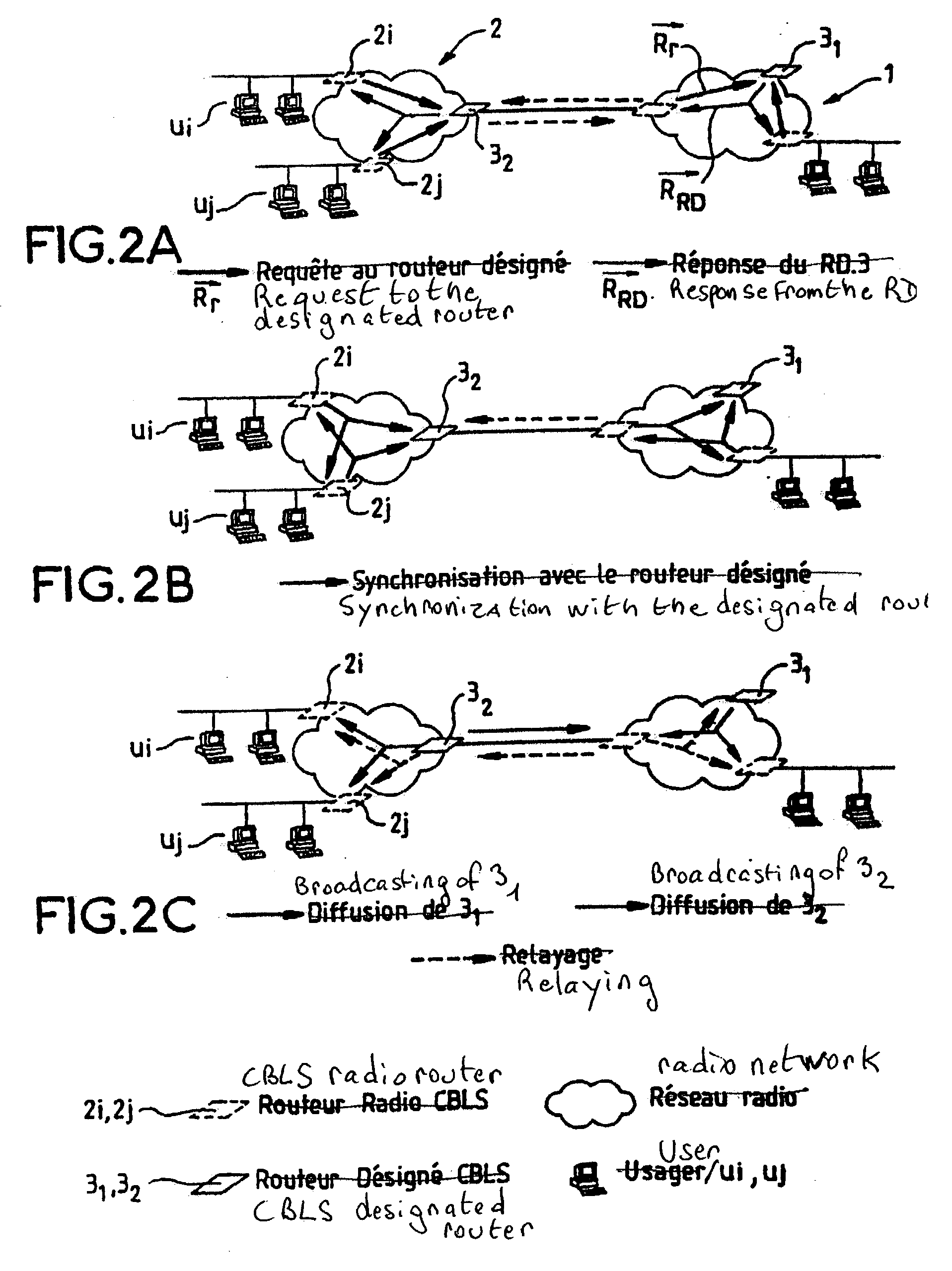
Method for adapting the OSPF routing protocol to radio networks A method for routing messages among several radio networks, a radio network comprising at least one or more routers and one designated router (RD), each router comprising a database. The method comprises at least the following steps: at the level of the majority of radio networks, each router sends a request Rr to the designated router (RD) of the radio network; the designated router (RD) responds by sending the contents of its database to all or to the majority of the routers; a router of the radio networks, having received the contents of the database, sends a Hello message in order to search for its different neighbors, each router, knowing its neighbors, sends all the other routers of the network the contents of its database in order to synchronize all its neighbors.
Owner:THALES SA
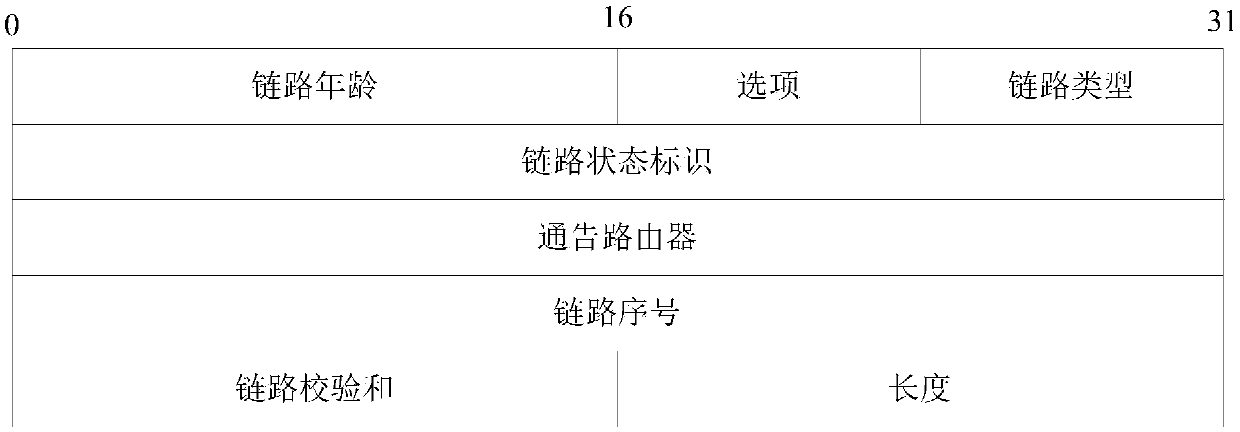
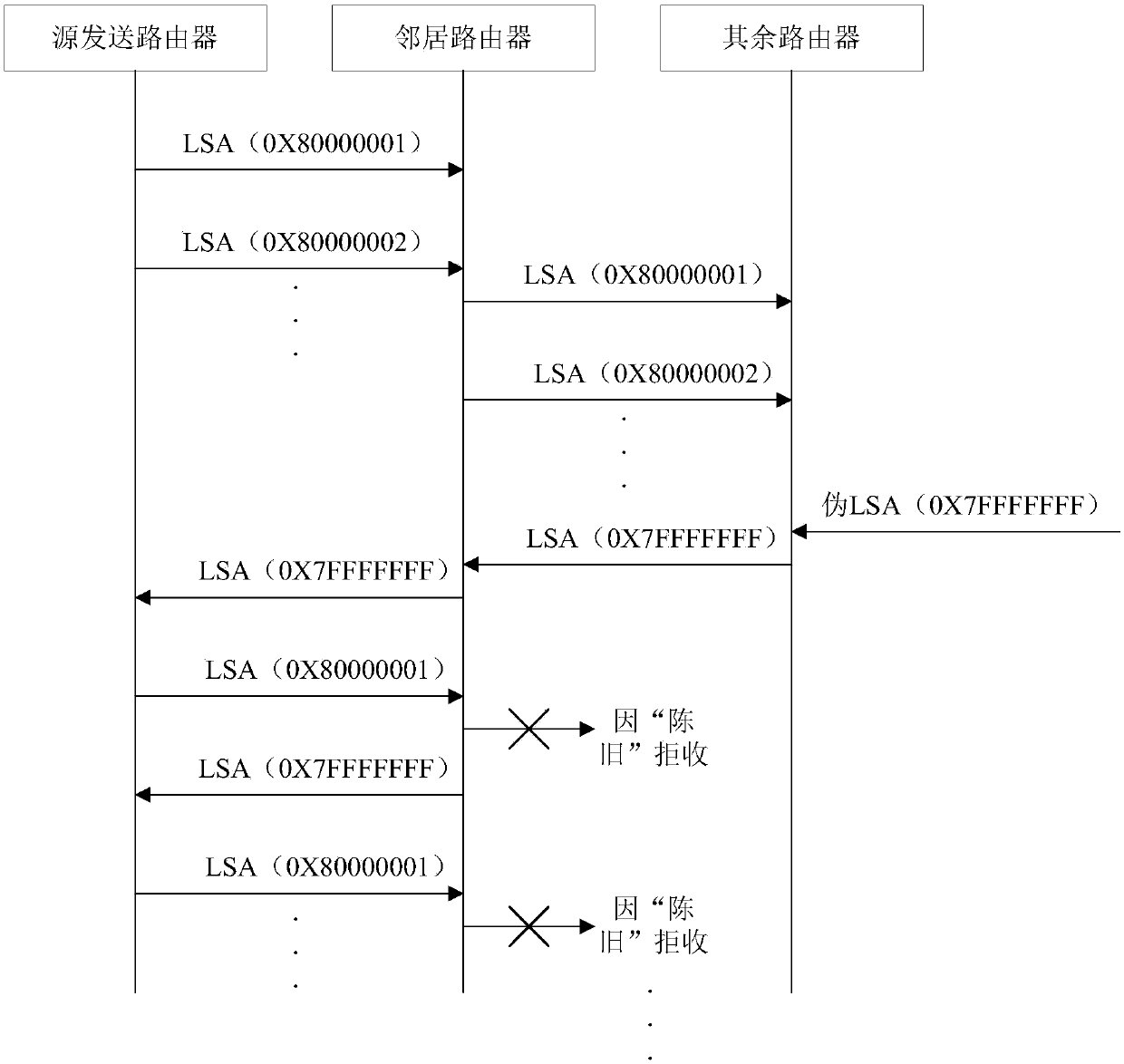
Anomaly detection for link-state routing protocols
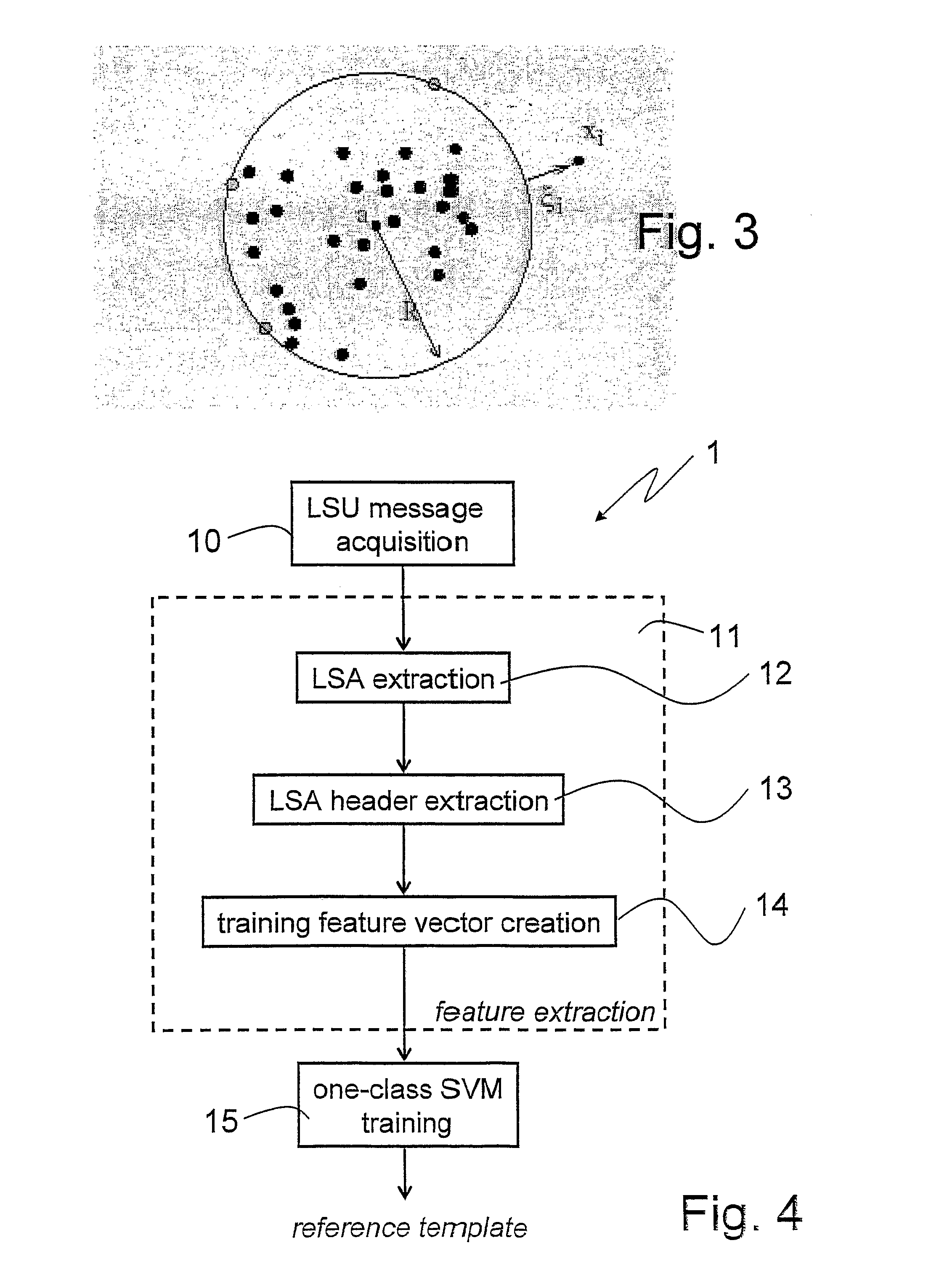
ActiveUS8626678B2Efficient and reliable detectionLarge spectrumError preventionFrequency-division multiplex detailsFeature vectorOne-class classification
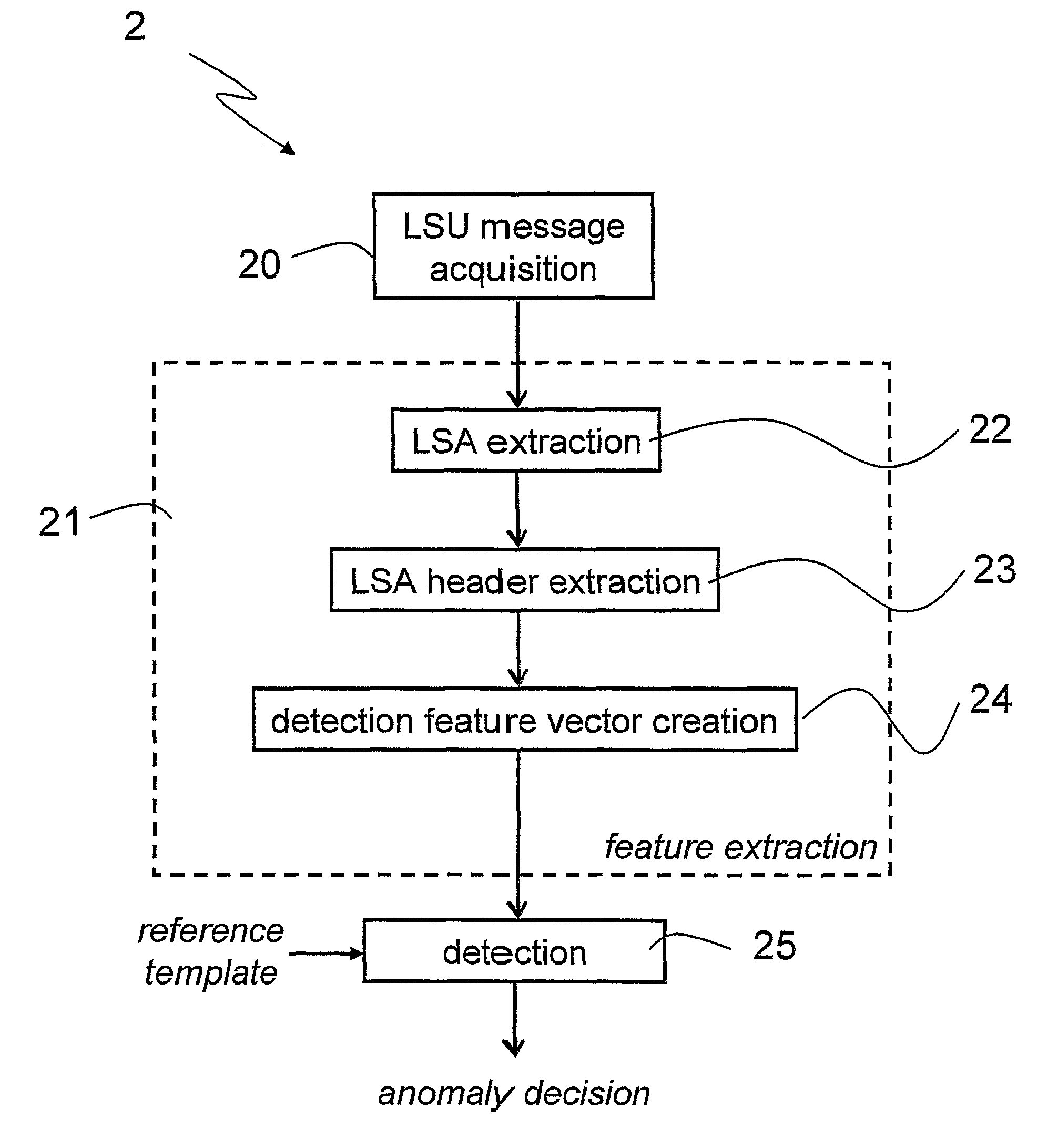
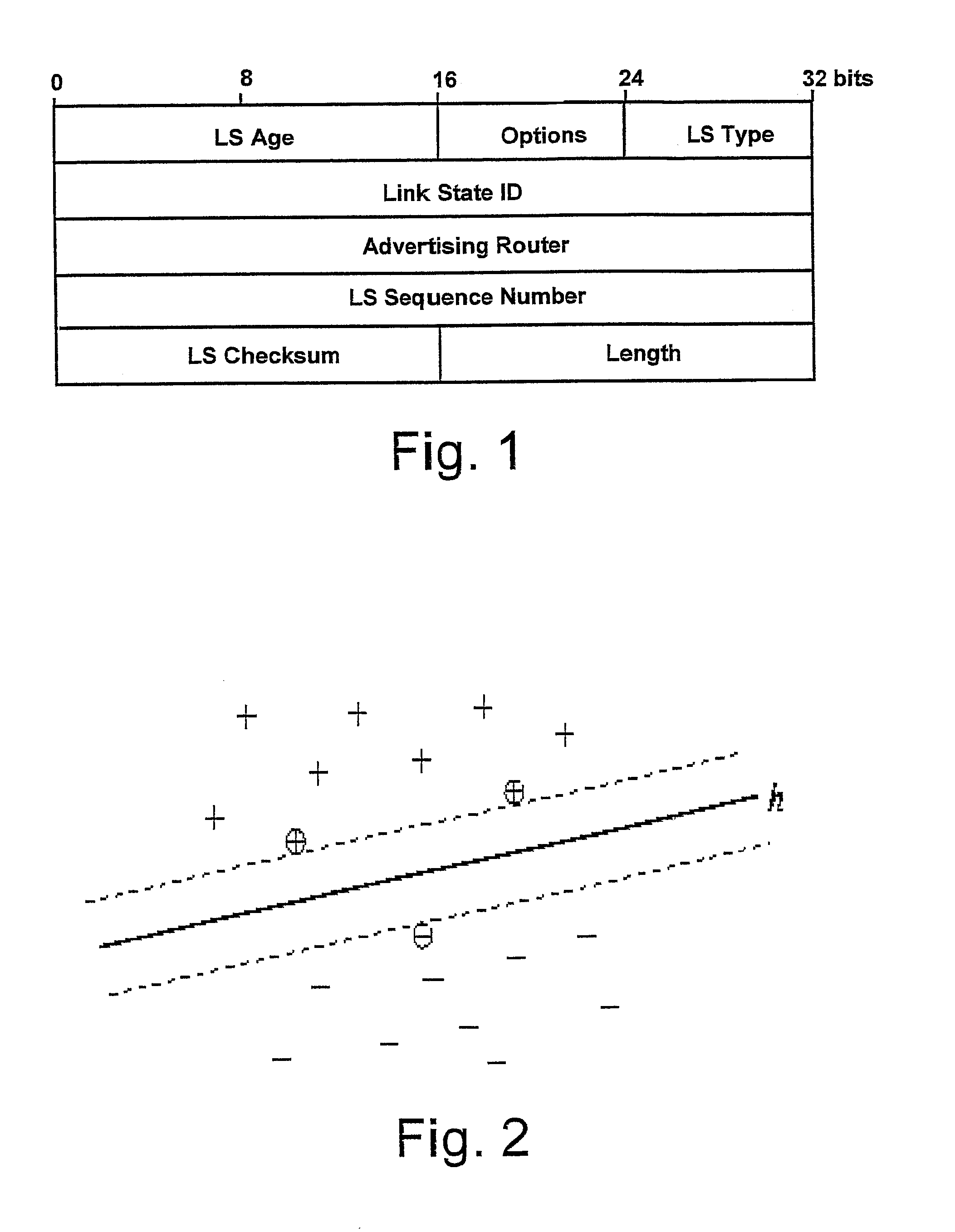
Disclosed herein is an anomaly detection method for link-state routing protocols, a link-state routing protocol providing for link-state update (LSU) messages to be exchanged between nodes in a packet-based network, wherein each link-state update message includes link-state advertisement (LSA) message(s) each having a respective header. The method comprises monitoring the link-state advertisement messages exchanged in the network, extracting and forming respective feature vectors with the values in the fields of the headers of the monitored link-state advertisement messages, and detecting an anomaly related to routing based on the feature vectors. In particular, detecting an anomaly related to routing includes feeding the feature vectors to a machine learning system, conveniently a one-class classifier, preferably a one-class support vector machine (OC-SVM).
Owner:TELECOM ITALIA SPA
Wireless sensor network node autonomous decision-making routing protocol
ActiveCN108650137AIncrease powerExtend the life cycleNetwork topologiesConnection managementTree rootWireless sensor networking
The invention relates to a wireless sensor network node autonomous decision-making routing protocol, comprising: for the problem of unbalanced energy consumption of a wireless sensor network node, dividing the neighborhood space of the node; selecting the next hop according to the virtual coordinate parameter of the adjacent node by adopting the proposed virtual coordinate model to accelerate theconvergence speed of the path to the Sink node; constructing a path tree rooted at the Sink node by using the distributed computing and self-organizing communication; and optimizing the path tree according to the remaining energy information of the node by using the proposed local energy equalization strategy. By performing the simulation under the OMNeT++ platform, compared with the DEBUC protocol and the UAUC protocol, the NAD protocol is extended by 71.8 percent and 66.5 percent respectively in the time of the first node death, the average residual energy of the node is increased by 45.8 percent and 27.9 percent respectively, and the remaining energy standard deviation of the node is increased by 51.2 percent and 34.2 percent respectively. The simulation results show that the NAD protocol is capable of effectively extending the network life cycle and balancing the node energy consumption.
Owner:LIAONING UNIVERSITY
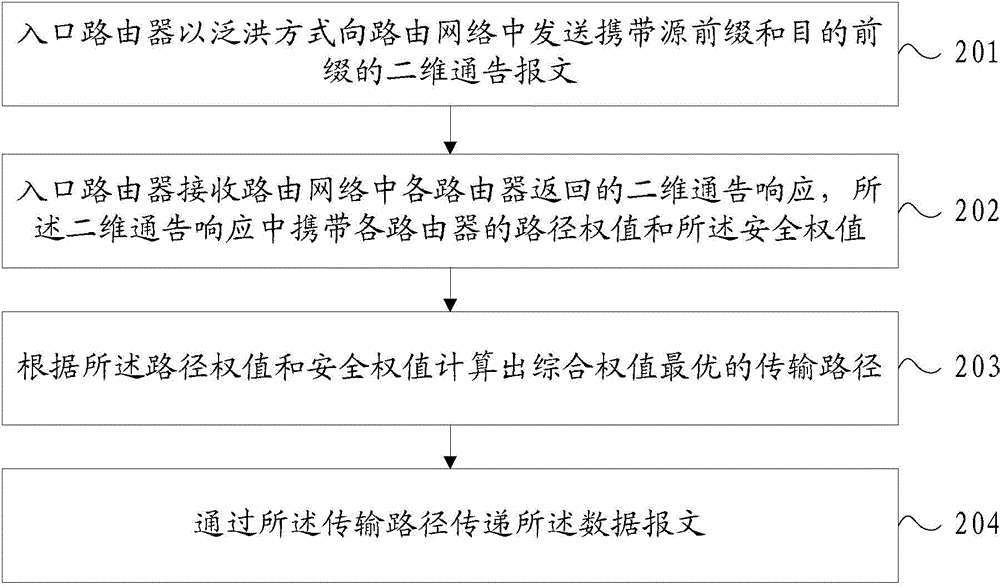
Implementation method of two-dimension routing protocol and device using protocol
The invention relates to the technical field of router transmission, and provides an implementation method of a two-dimension routing protocol. Respective safety weight is set for each router in a routing network according to the safety level. When an ingress router receives a data message required to be sent to an egress router and establishes a transmission path for the data message, the method comprises steps as follows: the ingress router sends a two-dimension announcement report carrying a source prefix and a target prefix to the routing network in a flooding manner; the ingress router receives a two-dimension announcement response returned by each router in the routing network, and the two-dimension announcement response carriers path weight and safety weight of each router; the transmission path with the optimal comprehensive weight is calculated according to the path weight and the safety weight; the data message is transmitted through the transmission path. Double indexes of the shortest transmission path and the transmission path safety are balanced, and the transmission safety of a data pack in the conventional routing network is improved.
Owner:SHENZHEN OUDMON TECH
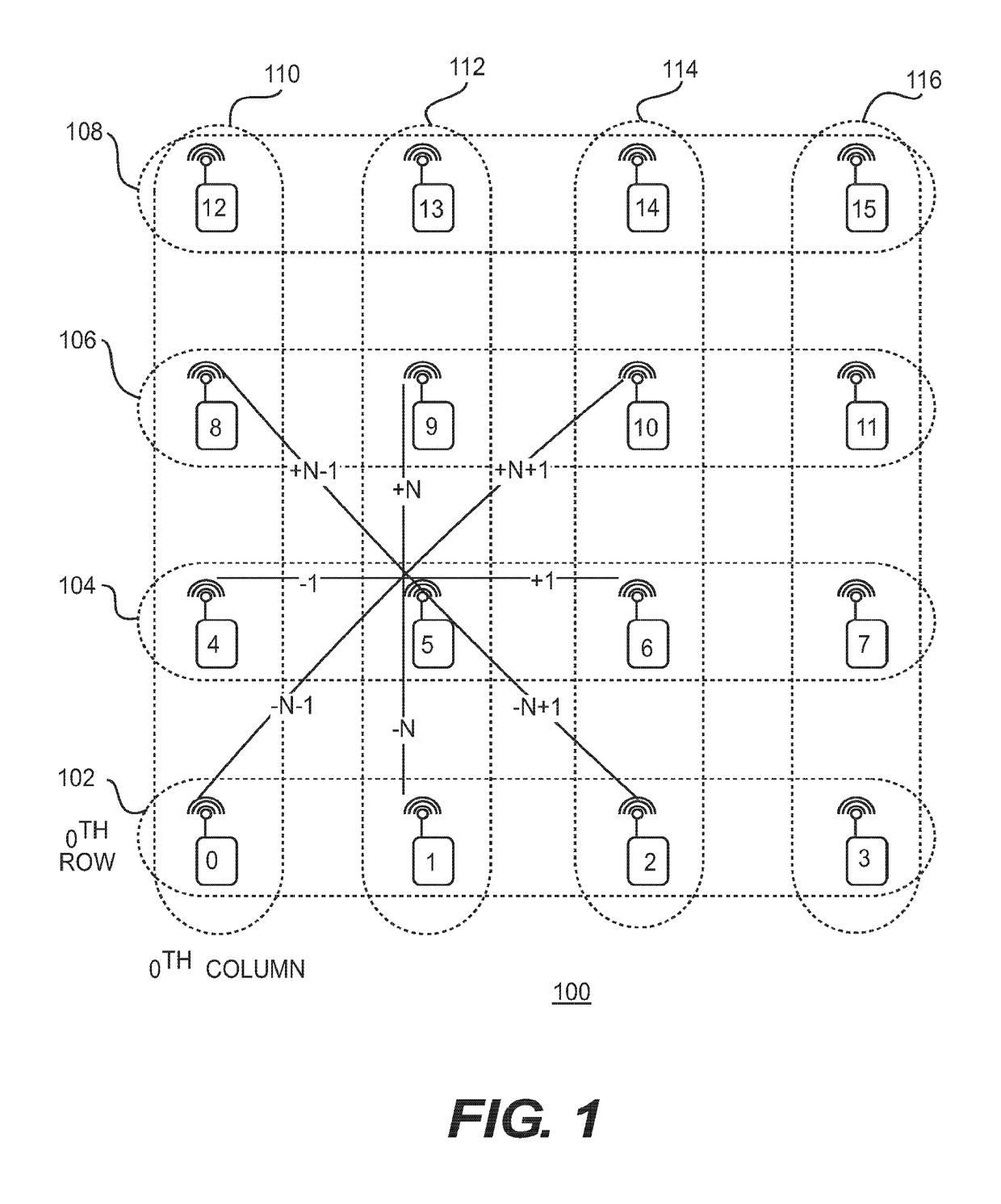
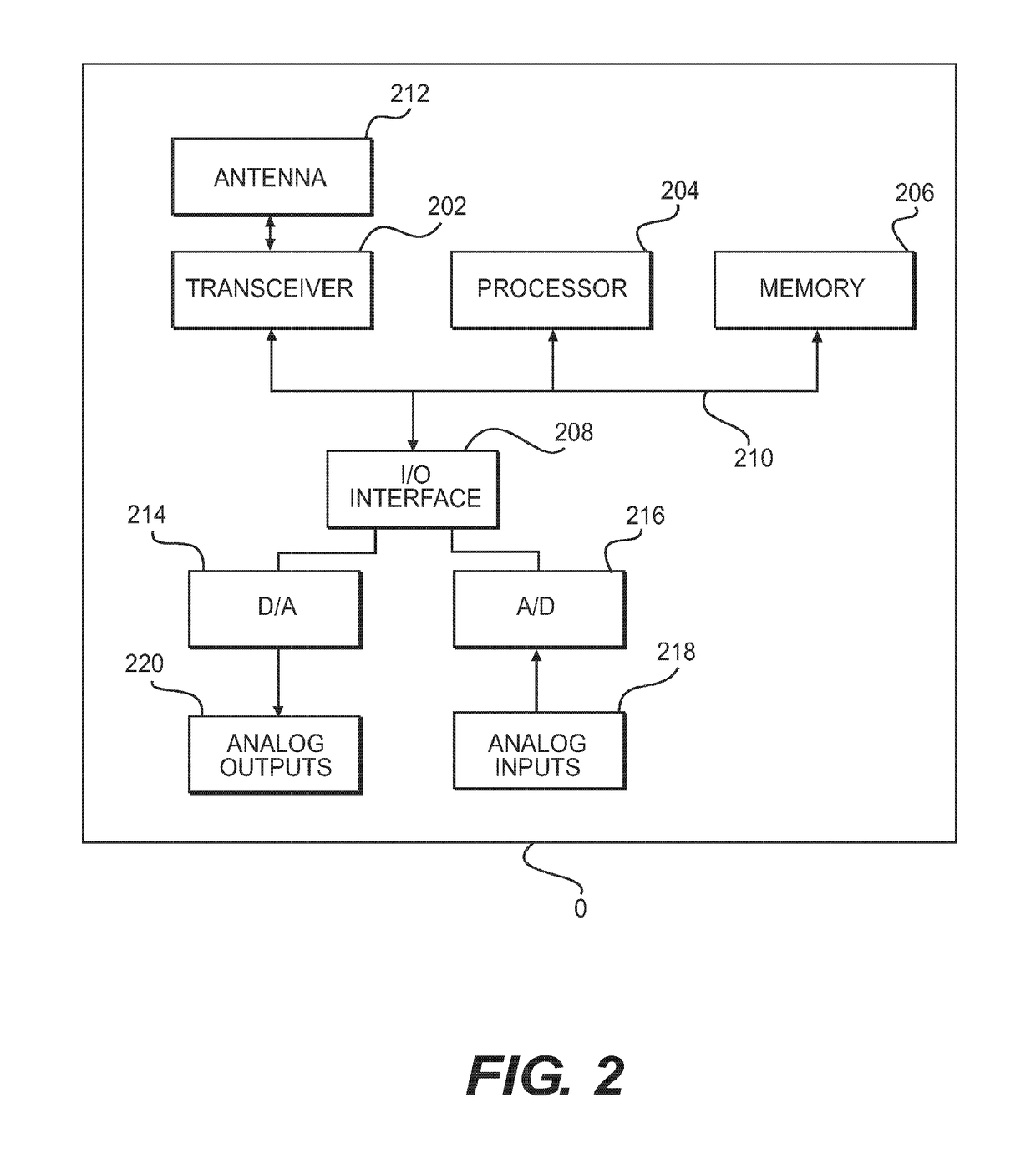
ID-based routing protocol for wireless network with a grid topology
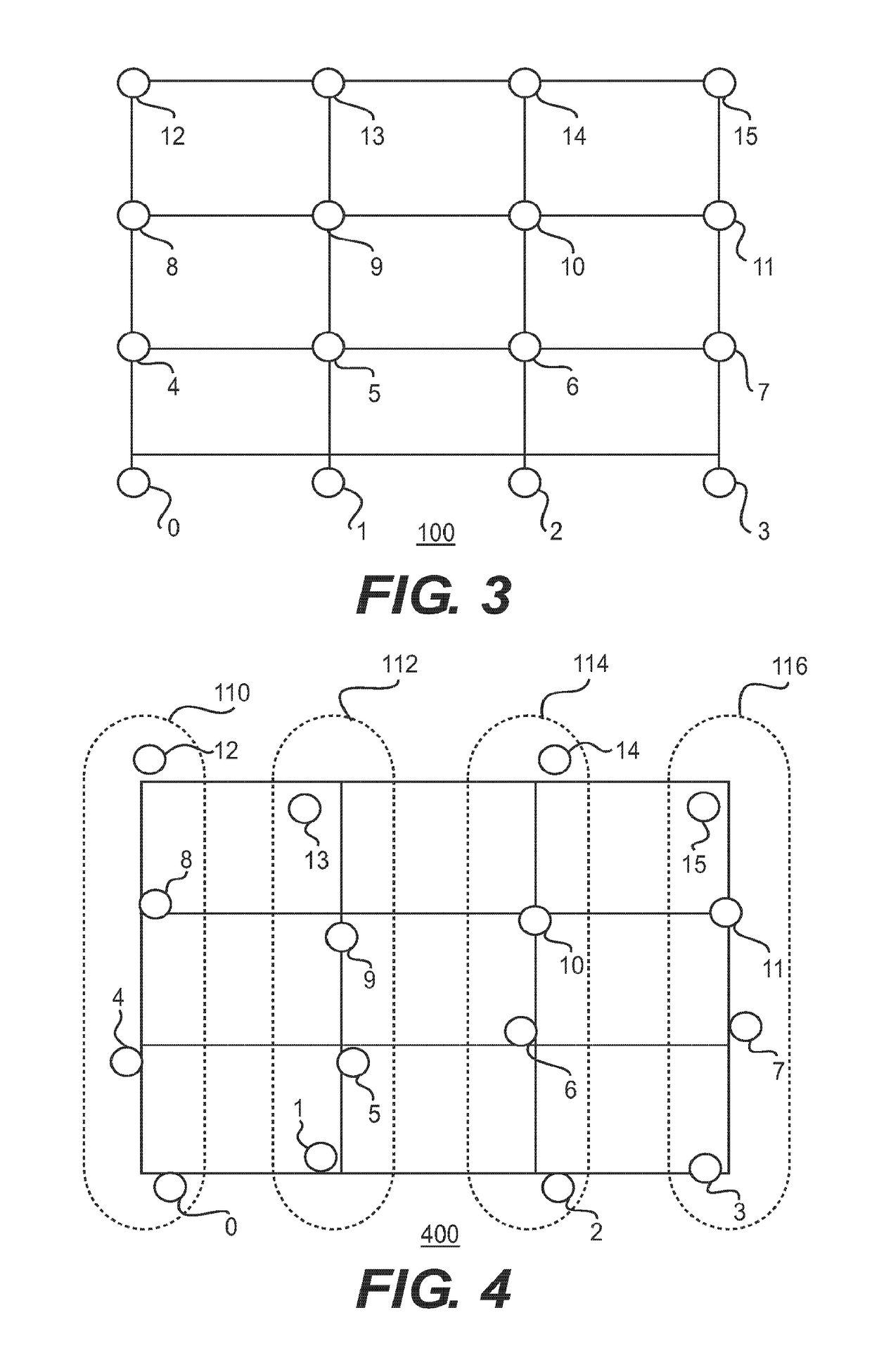
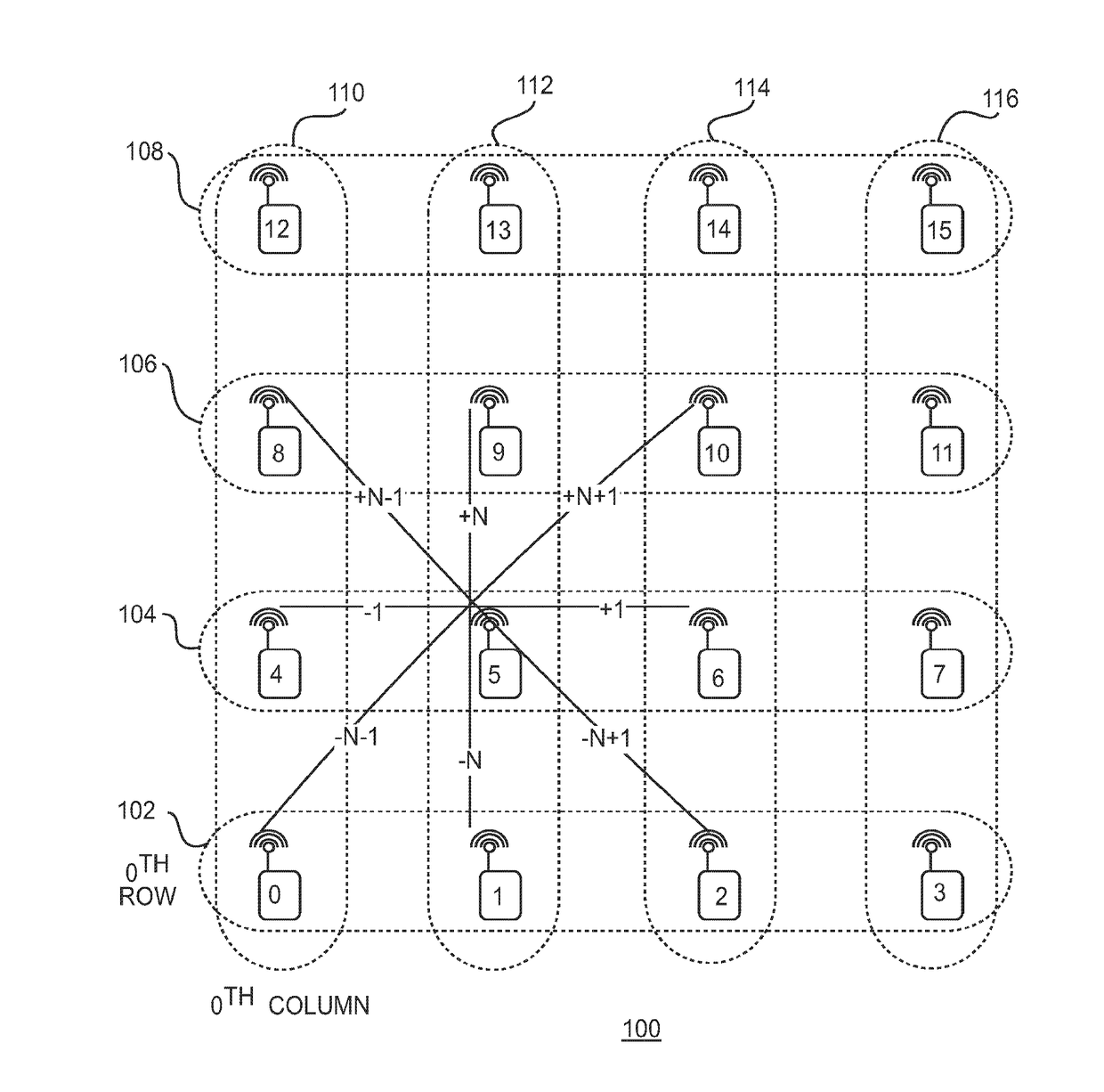
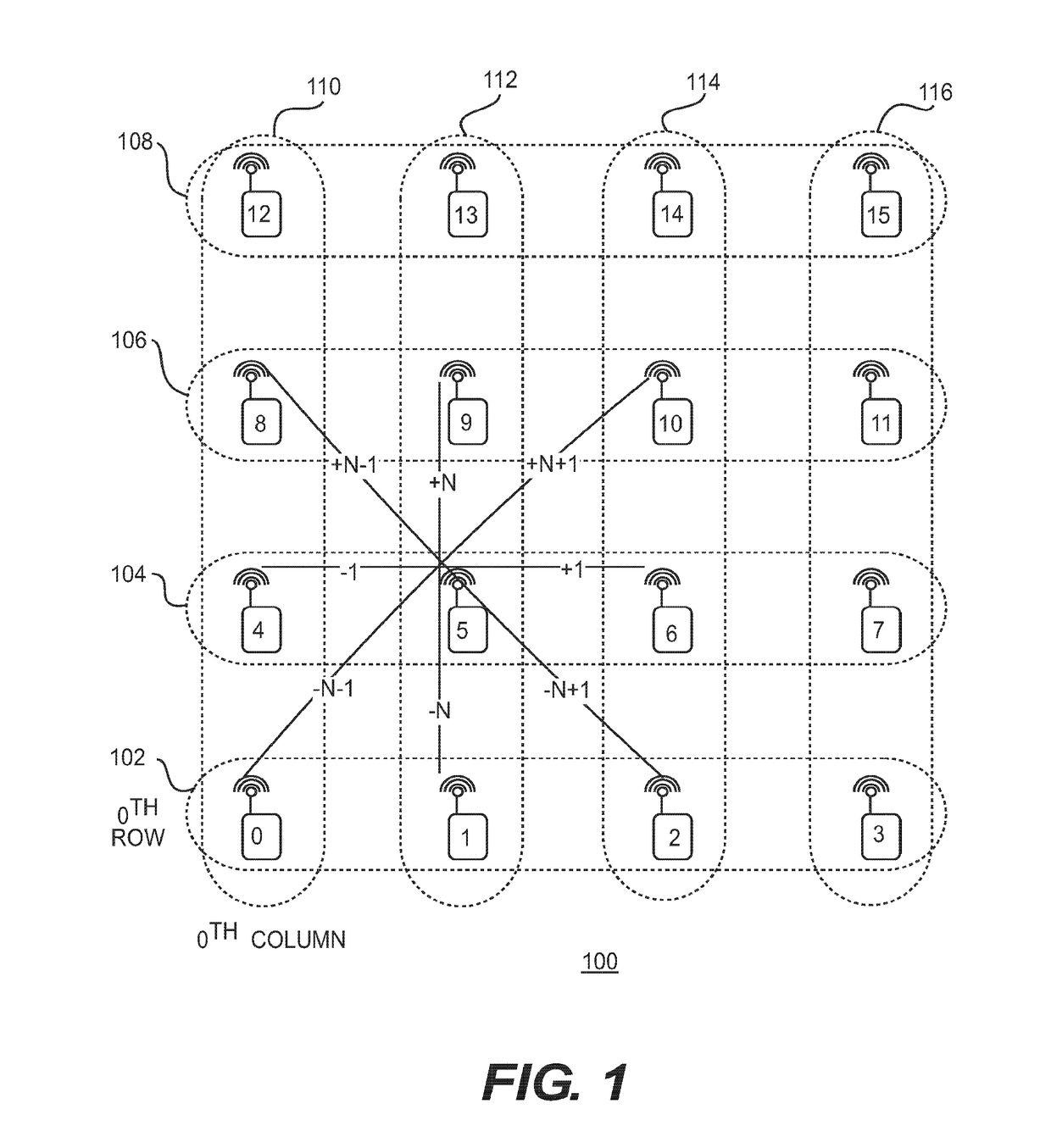
InactiveUS10149226B2Circuit switching systemsHigh level techniquesTelecommunicationsWireless mesh network
Aspects of the disclosure provide a wireless node in a wireless network with a grid topology for routing a message. The wireless node includes circuitry configured to receive a message including a destination node identification number, calculate a destination column and a destination row based on the destination node identification number, determine a next hop address based on the destination column and the destination row, and transmit the message including the next hop address to a next hop node.
Owner:KING FAHD UNIVERSITY OF PETROLEUM AND MINERALS
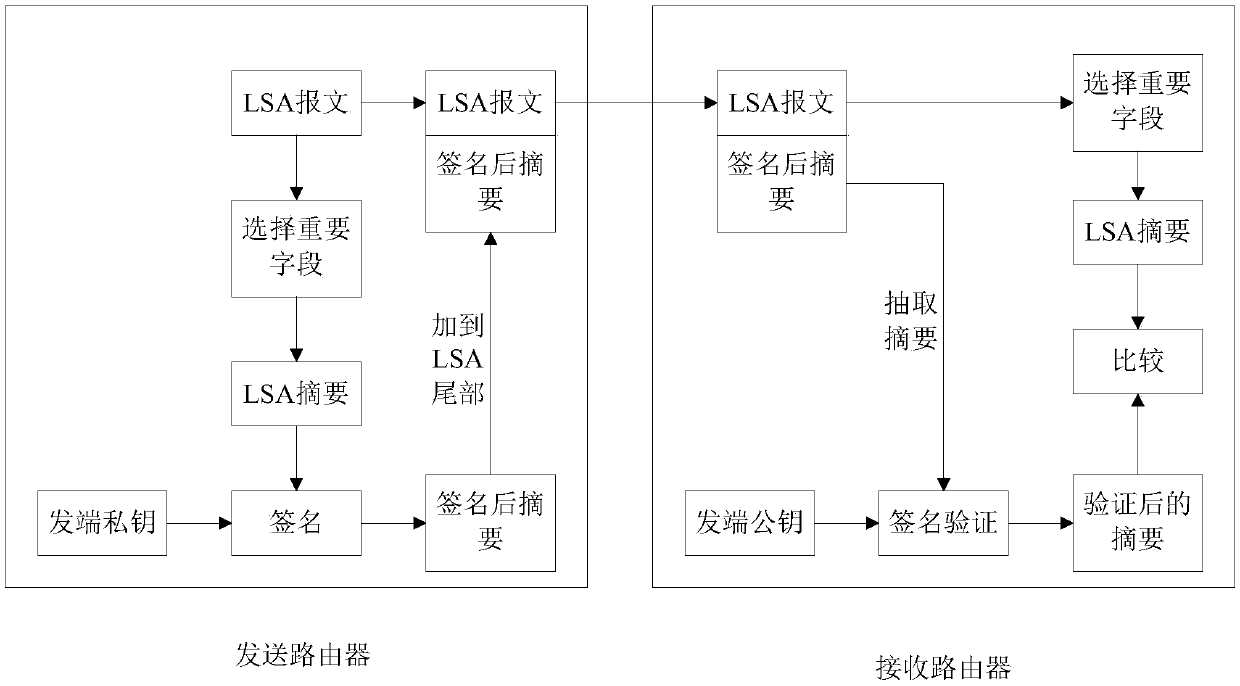
Intrusion prevention method and apparatus based on OSPF routing protocol
ActiveCN108055285AAvoid accessEase computing workUser identity/authority verificationData switching networksIntrusion prevention systemTransmission bandwidth
The invention provides an intrusion prevention method and apparatus based on an OSPF routing protocol, applied to a router. The method comprises the following steps: when an LSU message is received, obtaining message information of the LSU message, and obtaining a PCR value of the LSU message; reading signature information carried in the LSU message; comparing whether a verification hash value obtained by performing hash operation on a message header hash value obtained by the hash operation of the message header information of the LSU message and the PCR value of the router sending LSU message is the same as a signature hash value obtained by decrypting the signature information based on a public key of the router sending the LSU message; and if not, discarding the LSU message. By adoption of the technical method provided by the invention, the operation work of the router can be relieved, the transmission bandwidth is reduced, and the efficiency of the router is improved.
Owner:HANGZHOU DPTECH TECH
Big data identification and intelligent analysis method and system for wireless sensor network based on energy-aware routing protocol
InactiveCN108848504AReduce energy consumptionHigh security mechanismUser identity/authority verificationNetwork topologiesLine sensorWireless mesh network
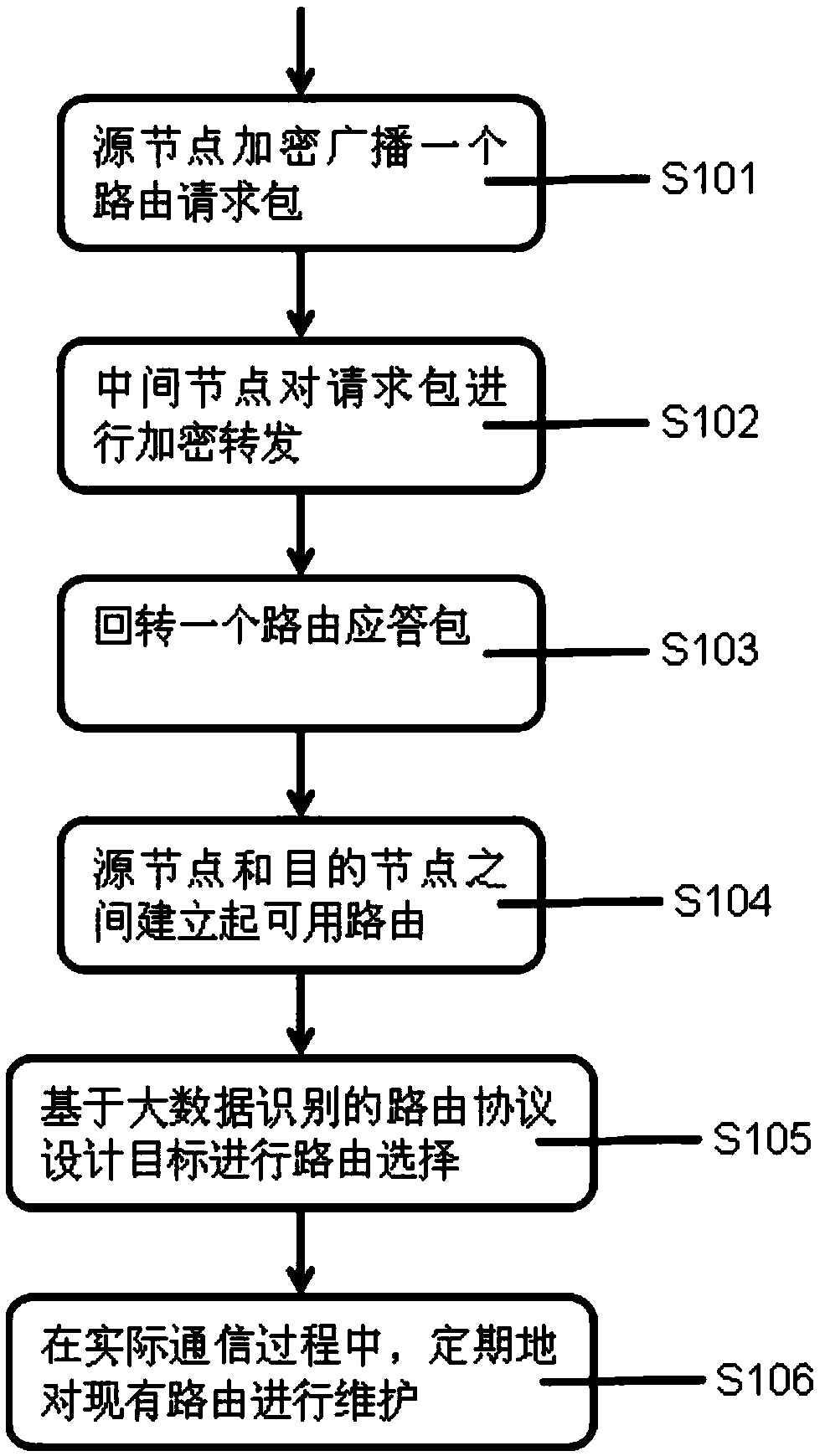
The invention belongs to the technical field of wireless sensor security mechanisms, and particularly relates to a big data identification and intelligent analysis method for a wireless sensor networkbased on an energy-aware routing protocol. The invention also provides a big data identification and intelligent analysis system for the wireless sensor network based on the energy-aware routing protocol at the same time. The method includes the followings steps that: a source node encrypts and broadcasts a route request packet, and an intermediate node encrypts and forwards the request packet and simultaneously revokes a route response packet until an available route is established between the source node and a destination node. The scheme of the invention solves the problem that the security is poor because some existing routing protocols in the wireless sensor network do not highly consider the security requirements in the prior art, and has the beneficial technical effects of high security performance, good security, high reliability, wide application range and low energy consumption.
Owner:SHENYANG NORMAL UNIV
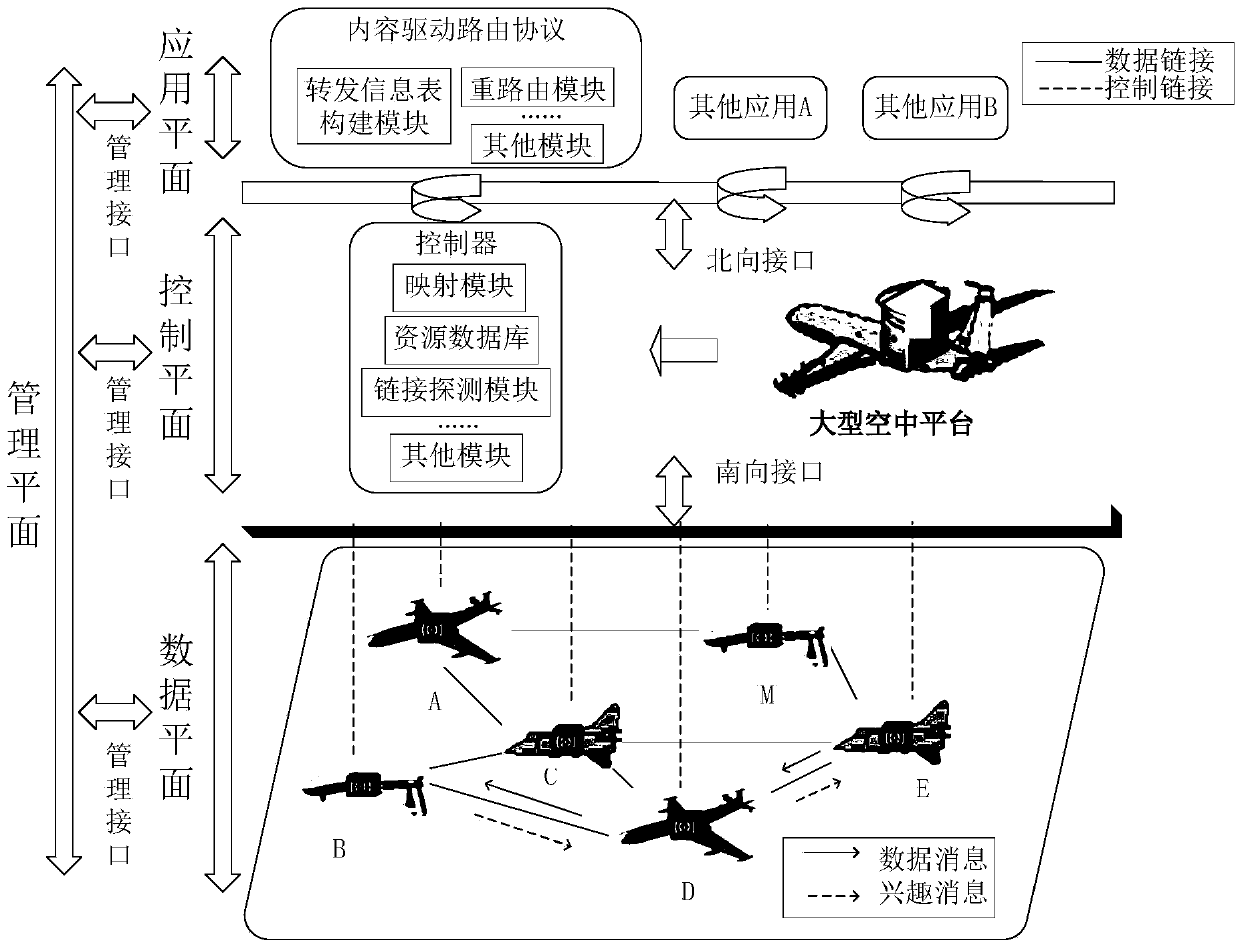
Software defined information centric-airborne networking architecture and content-driven routing protocol
ActiveCN109547345AIncrease flexibilityImprove efficiencyNetwork topologiesData switching networksDifferentiated serviceInformation-centric networking
The invention discloses a software defined information centric-airborne networking architecture and a content-driven routing protocol. A data plane is connected with a control plane through a southbound interface, the control plane is connected with an application plane through a northbound interface, and a management plane is connected with the application plane, the control plane and a data plane through management interfaces respectively; and by taking the software defined airborne networking architecture as a basis and starting with network performance parameters such as the end-to-end access delay and the throughput, the content-driven routing protocol is further designed. According to the software defined information centric-airborne networking architecture, software defined networking, information centric networking and airborne tactical networking are integrated, the flexibility and efficiency of networking control are improved, and differential networking services and efficient transmission of high-value information are provided for networking; and in addition, the routing protocol provides different levels of differential routing forwarding capacities for different information content, and then the purpose of providing the high-efficiency differential services for networking is achieved.
Owner:陈柯帆 +1
Improved CARP routing protocol
InactiveCN105246123AReduce redundancyReduce in quantityPower managementHigh level techniquesNetwork packetCarp
The invention discloses an improved CARP routing protocol. The protocol of selecting an optimal data transmission relay node comprises the following steps that step1, when a sensor node nvsn broadcasts one PING control information packet, a channel quality parameter g(nvsn) value of a sensor node which is adjacent to the node nvsn is calculated; step2, the adjacent nodes of a previous data transmission relay node and all the g(nvsn) values in a range (beta*g(omega), infinite) reply a PONG packet, wherein the threshold value beta is a floating number in a range of 0-1; step3, in the adjacent nodes of all the g(nvsn) values in the range (beta*g(omega), infinite), an upper layer of node uvz of a maximum g(nvsn) value is selected, and the uvz is selected as the relay node of current data transmission if a condition which is defined in the description is satisfied; otherwise, a last-time relay node is continuously used. When the optimal data transmission relay node is selected, a PING-PONG redundancy control information packet is reduced. Further, a data packet uploading algorithm is provided so that data collected by the sensor is used in high-efficiency and energy-saving mode.
Owner:GUANGDONG UNIV OF PETROCHEMICAL TECH
Novel routing protocol for solving congestion problem of wireless routers
A novel routing protocol for solving the congestion problem of wireless routers can be used for information detection and transmission. The novel routing protocol is mainly composed of a link breakage strategy and a node congestion strategy. When a router in a node fails due to link breakage, the routing protocol can limit the broadcast of the invalid router in a limited range and create a new loop-free router reaching a target node based on the existing information. Thus, packet loss because of link breakage can be reduced, and the packet delivery success rate of the network can be improved. When congestion occurs to a node, the routing protocol can notify an upstream node to recreate a loop-free router reaching the target node in the same processing approach as link breakage processing. Thus, packet loss because of node congestion can be reduced, and the packet delivery success rate of the network can be improved.
Owner:JIANGNAN UNIV
Control plane structure of virtual routing device and control method thereof
InactiveCN102231709BFlexible controlStable maintenanceData switching networksAddress Resolution ProtocolRouting table
The invention discloses a control plane structure of a virtual routing device and a control method thereof, and relates to the technical field of Internet. The control plane structure comprises a host control unit and a plurality of virtual machine units, wherein the host control unit is used for realizing user interaction and management and control over a data plane and the virtual machine units, and periodically updating a routing table and an address resolution protocol (ARP) table in the data plane; and the virtual machine unit is used for realizing a routing protocol processing function and a data packet processing function, generating and updating the routing table and the ARP table in real time, and providing the routing table and the ARP table for the host control unit. The virtual routing device comprises programmable hardware and a host, wherein the programmable hardware is used for realizing a data plane function. By the structure and the method, a proper routing protocol can be flexibly selected according to an application scenario and stably maintained, table entries can be updated in real time, the flexible configuration of the data plane can be realized, and accurate responses can be given to the needs of a user in real time.
Owner:TSINGHUA UNIV
Id-based routing protocol for wireless network with a grid topology
InactiveUS20170273000A1Data switching networksHigh level techniquesWireless mesh networkProtocol for Carrying Authentication for Network Access
Aspects of the disclosure provide a wireless node in a wireless network with a grid topology for routing a message. The wireless node includes circuitry configured to receive a message including a destination node identification number, calculate a destination column and a destination row based on the destination node identification number, determine a next hop address based on the destination column and the destination row, and transmit the message including the next hop address to a next hop node.
Owner:KING FAHD UNIVERSITY OF PETROLEUM AND MINERALS
Design method of joint routing protocol for UAV communication network
ActiveCN107517158BLower latencyImprove throughputRadio transmissionData switching networksMonitor modeRouting decision
The invention provides a method for designing a joint routing protocol of an unmanned aerial vehicle communication network, and belongs to the technical field of designing the routing protocol of the unmanned aerial vehicle communication network. The method comprises the following steps: firstly constructing a lightweight unmanned aerial vehicle forward queue model that is low in maintenance cost and is easy to achieve; then based on the model, separately extracting an instant queue power concept and an instant transmission power concept, and designing a joint routing decision in a sum form; designing a new data packet header, adding unmanned aerial vehicle information to the data packet header, opening the monitoring mode of the unmanned aerial vehicle, and passively discovering a neighbor unmanned aerial vehicle; and finally selecting a proper unmanned aerial vehicle to serve as the next hop according to the maximum routing decision variable, and transmitting data packets to the next hop unmanned aerial vehicle. The joint routing protocol of the unmanned aerial vehicle communication network has a smaller node queue maintenance cost and a lower neighbor unmanned aerial vehicle discovery cost, and efficient communication access services can be provided for short time bursty traffic on the ground.
Owner:BEIJING TASSON SCI & TECH CO LTD
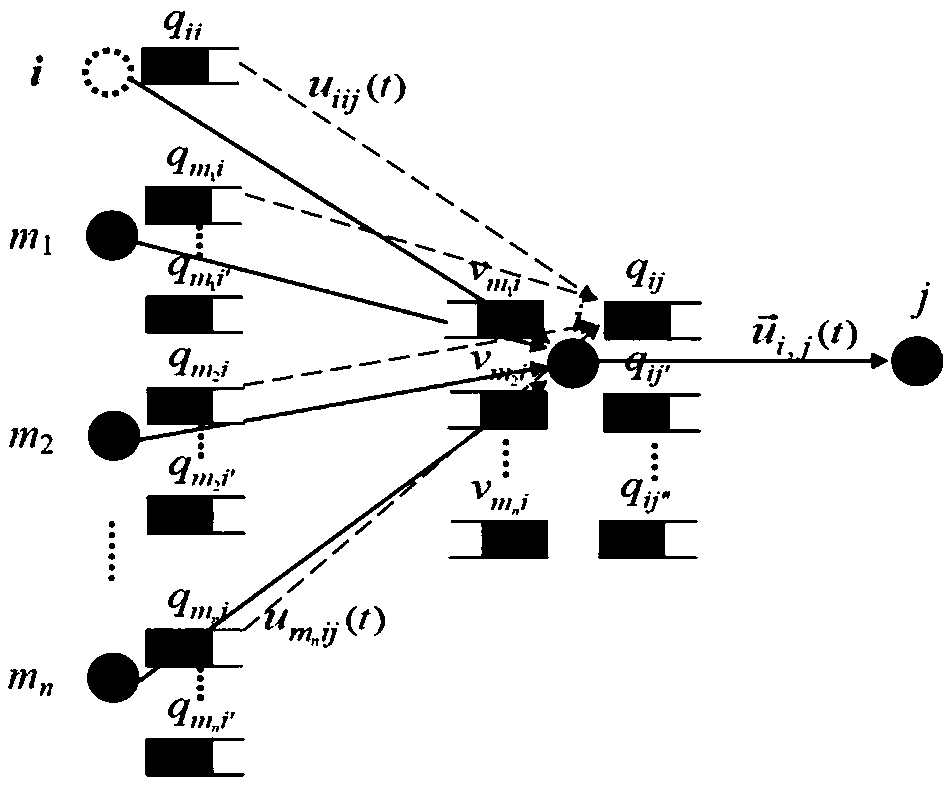
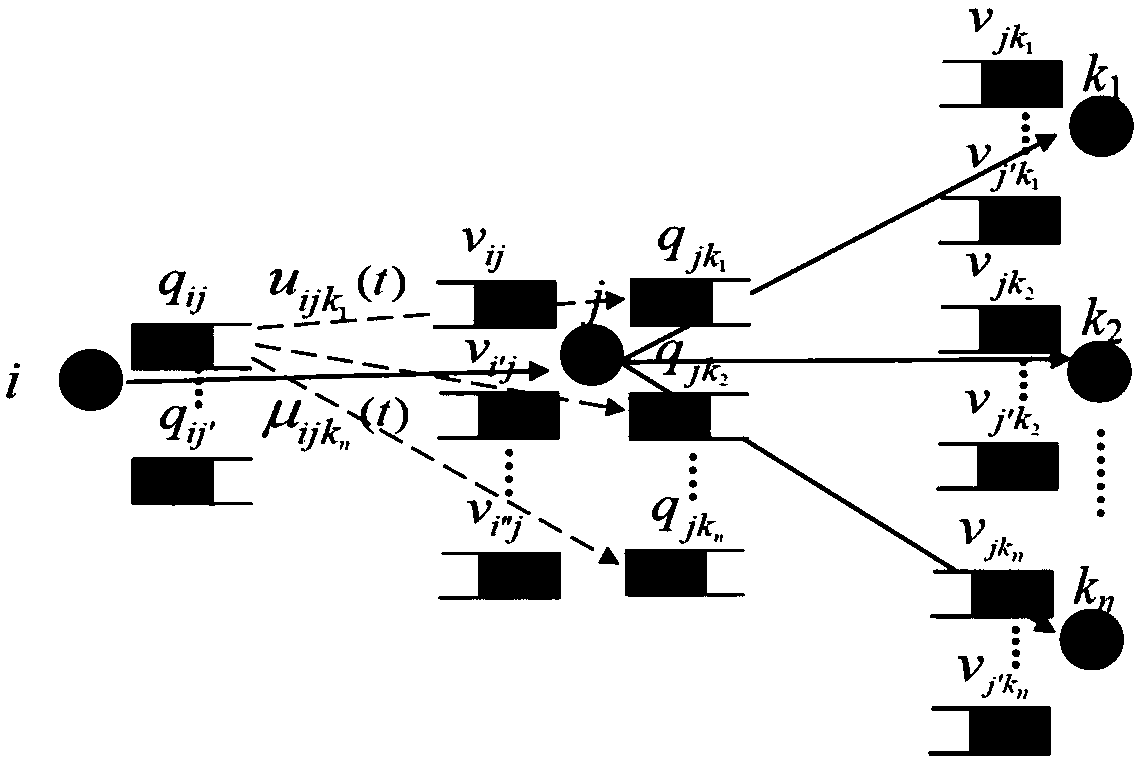
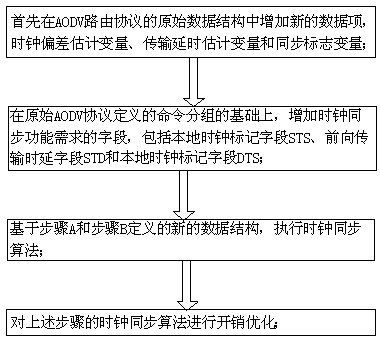
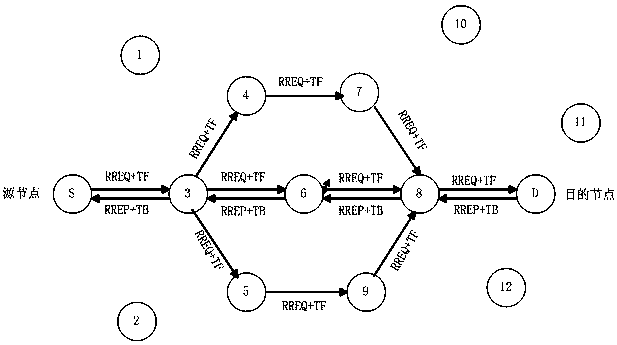
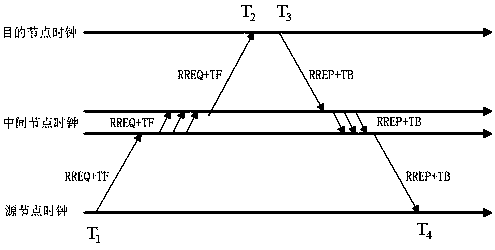
On-demand Clock Synchronization Method for Wireless Sensor Networks Based on AODV Routing Protocol
ActiveCN104540212BHop-by-Hop AccumulationHigh precisionSynchronisation arrangementData synchronizationMobile wireless sensor network
The invention discloses a wireless sensor network on-demand clock synchronization method based on an AODV (Ad Hoc On-Demand Distance Vector) routing protocol. A clock synchronization algorithm is integrated with a path finding algorithm of an AODV protocol, so that clock synchronization with a target node can be implemented according to the demand of the node, and the implementation of the clock synchronization is not limited to a whole-network synchronization way. The clock synchronization algorithm is implemented on the basis of direct interaction of a source node with a target node, and an intermediate node does not participate into clock synchronization computation anymore, so that hop-by-hop accumulation of clock synchronization deviations can be avoided, and the accuracy of multi-hop clock synchronization is increased. Through use of existing clock synchronization information of the intermediate node, further optimization of the communication overhead of the clock synchronization algorithm can be realized; the computation speed of the clock synchronization algorithm can be increased in a network in which a topological structure changes rapidly; and rapid synchronization of the node with the target node is implemented. Therefore, the technology can well adapt to the network in which the topological structure changes rapidly.
Owner:STATE GRID HENAN ELECTRIC POWER ELECTRIC POWER SCI RES INST +1
A method for constructing a virtual router that can be deployed automatically
ActiveCN105827464BImplement a dynamic routing protocolAutomatic and flexible deploymentData switching networksIp addressAdaptive routing
The invention provides an automatically deployable virtual router establishing method, comprising the following steps of S1, compiling a command line packaging module in a virtual router, and adding a packaged command line into applications run on start-up of the virtual router, thus achieving the self-starting function of the virtual router; S2, compiling a file reading module, and reading values of correlated variables in files to which file reading parameters point, wherein the correlated variables in the files to which the file reading parameters point comprise an automatic deployment variable of which the value is true or false, and a routing protocol variable of which the value is an appointed dynamic routing protocol; S3, compiling a virtual network configuration sniffing module, and achieving a function of acquiring the ip address of a network adapter of the virtual router; S4, compiling a dynamic routing protocol simulation module, and achieving the automatic configuration of the dynamic routing protocol based on the steps S2 and S3; and S5, compiling an increment configuration module. According to the method, the user can flexibly and conveniently perform virtual network management.
Owner:无锡新敏通网络技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com