Intrusion prevention method and apparatus based on OSPF routing protocol
A routing protocol and protection device technology, applied in the field of network communication, can solve the problems of high transmission bandwidth, impact of router efficiency, relatively high router computing requirements, etc., and achieve the effect of alleviating computing work
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0061] In order to solve the attack based on the OSPF routing protocol in the prior art, Embodiment 1 of the present application proposes a new intrusion prevention method based on the OSPF routing protocol. See Figure 5 , Figure 5 It is a flow chart of an intrusion prevention method based on OSPF routing protocol shown in Embodiment 1 of the present application, which is applied to a router, and specifically performs the following steps:
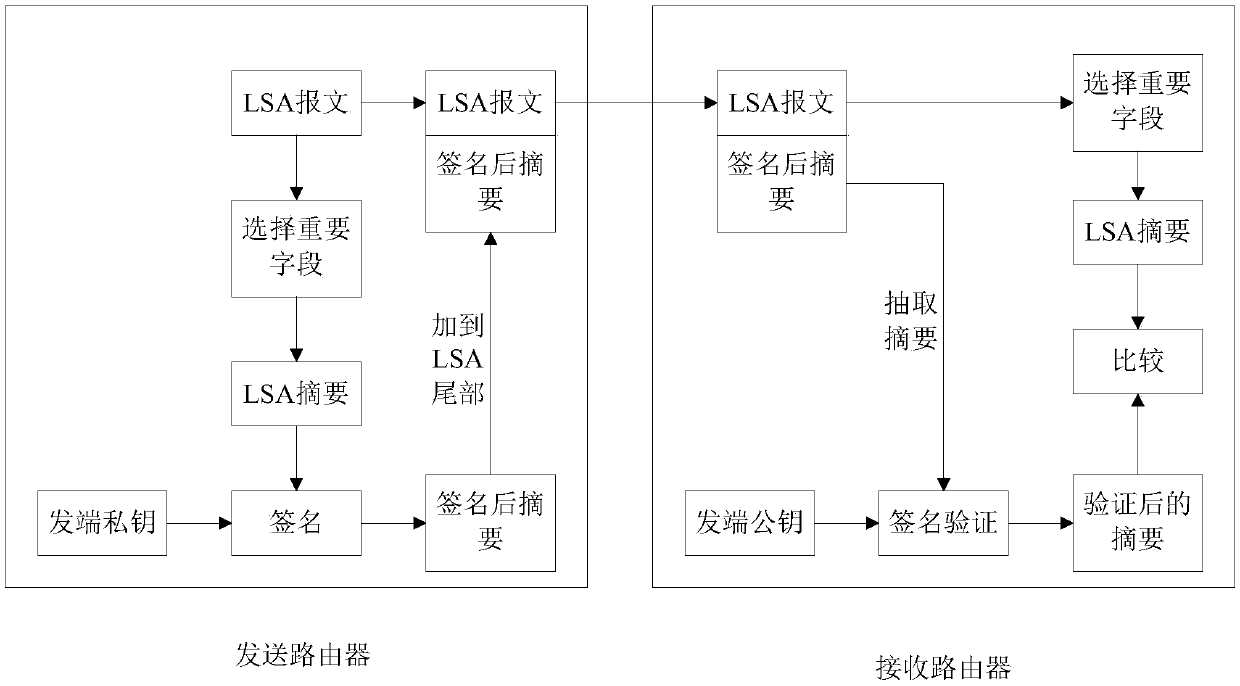
[0062] Step 501: when an LSU message is received, obtain the message information of the LSU message and obtain the PCR value of the router sending the LSU message;
[0063] Step 502: Read the signature information carried in the LSU message; wherein, the signature information is the router that sends the LSU message, and completes the hash operation on the header information of the LSU message based on its own private key The information obtained after the header hash value and the own PCR value are hashed together to obtain the signatu...
Embodiment 2
[0084] Corresponding to the first embodiment of the foregoing intrusion prevention method based on the OSPF routing protocol, the present application also provides a second embodiment of an intrusion prevention device based on the OSPF routing protocol.
[0085] An embodiment of an intrusion prevention device based on an OSPF routing protocol in this application can be applied to a router. The device embodiments can be implemented by software, or by hardware or a combination of software and hardware. Taking software implementation as an example, as a device in a logical sense, it is formed by reading the corresponding computer program instructions in the non-volatile memory into the memory for operation through the processor of the router where it is located. From a hardware perspective, such as Image 6 As shown, it is a hardware structural diagram of a router where an OSPF routing protocol-based intrusion prevention device is located in this application, except Image 6 In...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com