Method and system for centrally checking weak passwords of equipment
A weak password and weak password-level technology, applied in the transmission system, digital transmission system, electrical components, etc., can solve the problems of affecting the normal access of users, heavy manual workload, and destructive flaw detection, so as to save inspection manpower and management costs , improve work efficiency and effectiveness, and reduce direct or indirect losses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
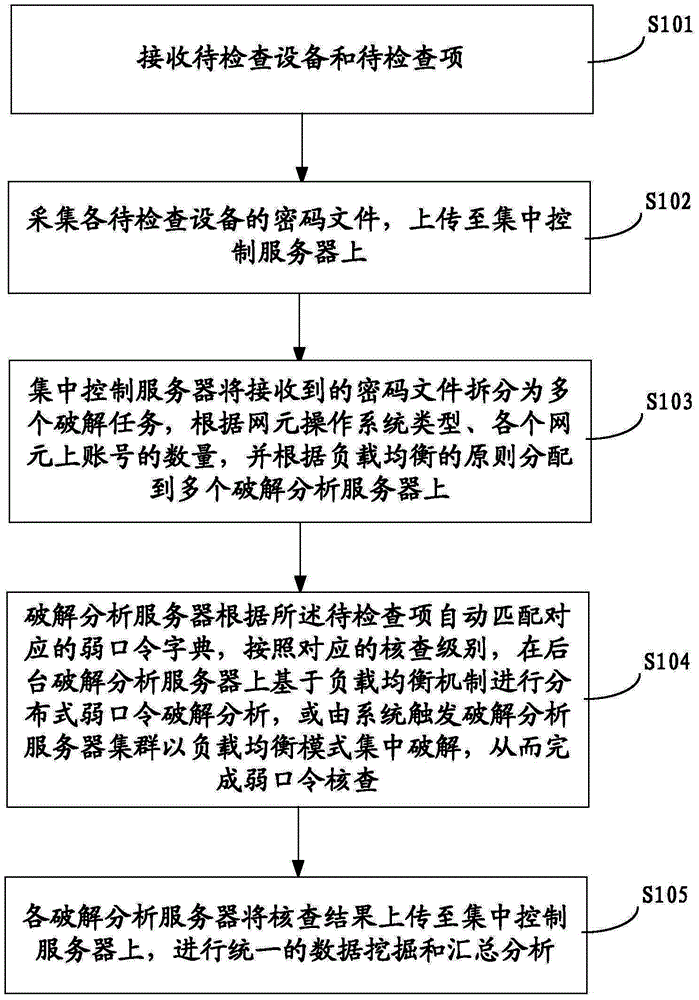
[0046] In order to make the object, technical solution and advantages of the present invention clearer, the implementation manner of the present invention will be further described in detail below in conjunction with the accompanying drawings.
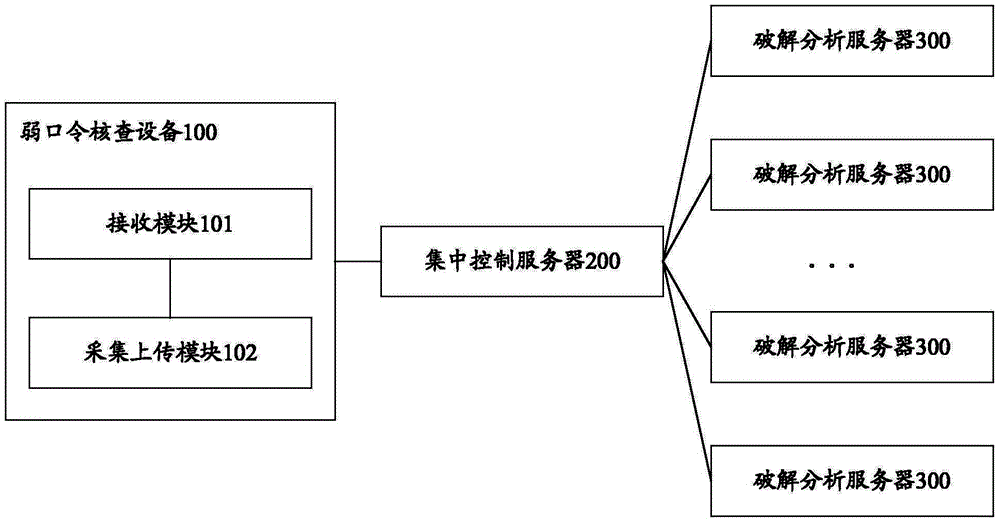
[0047]The embodiment of the present invention has the weak password verification function of the "non-destructive detection" mode that does not affect the normal operation of the business system at all, and is mainly characterized by online or offline acquisition of the password files of each network element and centralized cracking in the background. Obtain password ciphertext through technical or manual methods, realize centralized weak password dictionary management, unify the weak password standard of the whole network, and can upgrade at any time, analyze weak password status based on weak password dictionary, and achieve the purpose of comprehensively controlling the device password settings. Discover the accounts with weak passwo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com