IP voice communication system
A technology of voice communication and IP data, applied in the direction of transmission system, electrical components, etc., can solve the problems of complex implementation process and delay of IP voice calls, and achieve the effect of overcoming large power consumption and enhancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
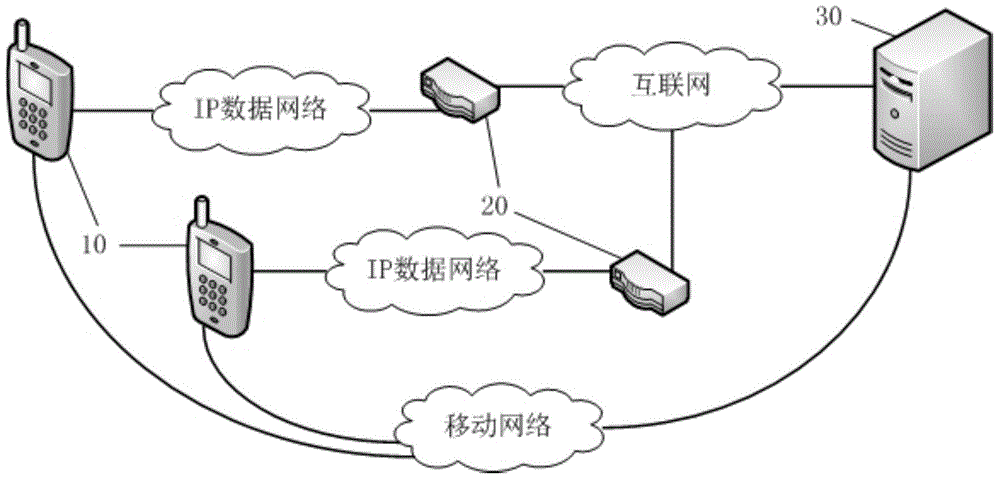
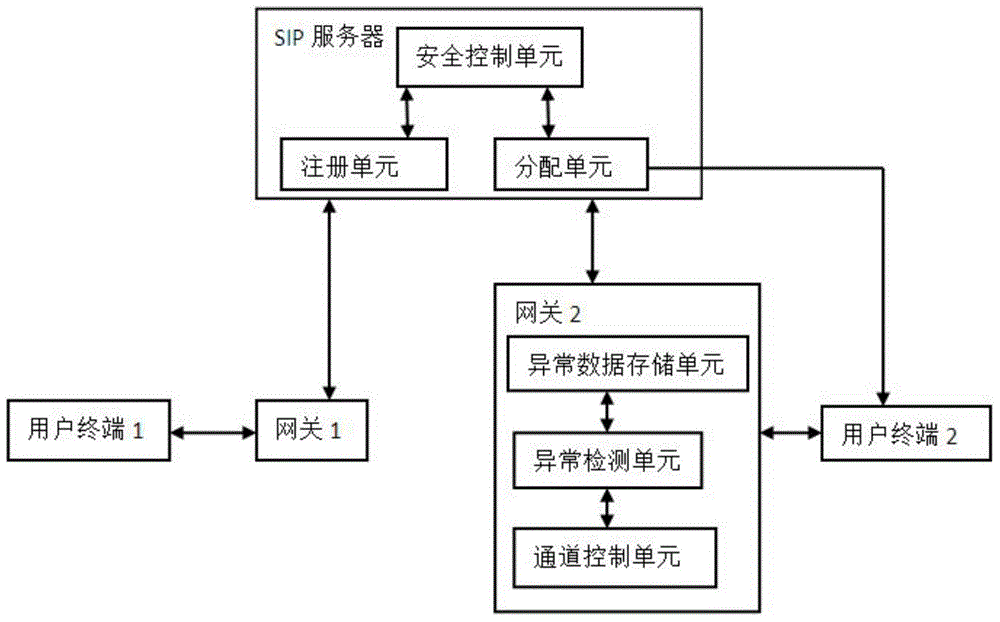
[0045] Such as figure 2 As shown, user terminals 1 and 2 are the calling user terminal and the called user terminal respectively, and the gateway 1 may be the structure of the gateway 2, which is simplified in the figure. The database on the SIP server 30 stores user-side application registration data. The registration data includes but is not limited to user name, password, device information, network port data, and historical data.
[0046] The IP voice call request initiated by the calling user terminal is transmitted to the SIP server via the gateway 1. After the SIP server receives the IP voice call request, the security control unit analyzes and outputs the first security data to the distribution unit based on the preset security policy and / or the stored security analysis data. The distribution unit determines whether to send the INVITE message and / or push message related to the IP voice call request to the called user terminal according to the first security data.
[0047...
Embodiment 2
[0050] On the basis of Embodiment 1, the user terminal 10 in this embodiment does not have to maintain WiFi and LAN connections all the time. When an IP voice call request is directed to the user terminal 10, the distribution unit of the SIP server 30 sends a push message to the user terminal 10 via the mobile communication network (2G, 3G, or 4G) after performing security verification.
[0051] After detecting the network connection status of the device, the application program of the user terminal 10 reminds the user of a new IP voice call by means of sound, flash, vibration, prompt message, and / or interface display. Specifically, after the application detects that the device does not have WiFi or LAN connection, it caches the received push message and performs a reminder action based on the push message. The user can set the aforementioned reminder actions as needed. The user chooses to open the WiFi connection so that the registration message reaches the gateway 20 via the I...
Embodiment 3
[0054] As an improvement and supplement of Examples 1 and 2. In this embodiment, the user can set the security level of the IP voice call in the application. In the state of high security level, when the channel control unit analyzes that there is an abnormality, it prompts the user through the application program interface and sends the abnormal information to the abnormal data storage unit for storage. When the user wants to avoid false interception that may occur in the high security level state, the security level can be set to the normal state. When the channel control unit analyzes that there is an abnormality, it sends a verification instruction to the user terminal 10 so that the application on the terminal invokes hardware devices (such as sensors, earpieces, cameras, etc.) on the terminal to collect user verification data. User authentication data includes images, sounds, and geographic location. Further, the user verification data may also include a verification pa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com