Smart device identity authentication method and client based on touch screen operation
A smart device and identity authentication technology, applied in the field of information security, can solve problems such as failure to take confidentiality measures, high failure rate of training model identity authentication, easy password leakage, etc., to achieve reasonable data standardization process and fast and simple data connection , safety and robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0091] Please refer to Figure 2 to Figure 6 , Embodiment 1 of the present invention is:
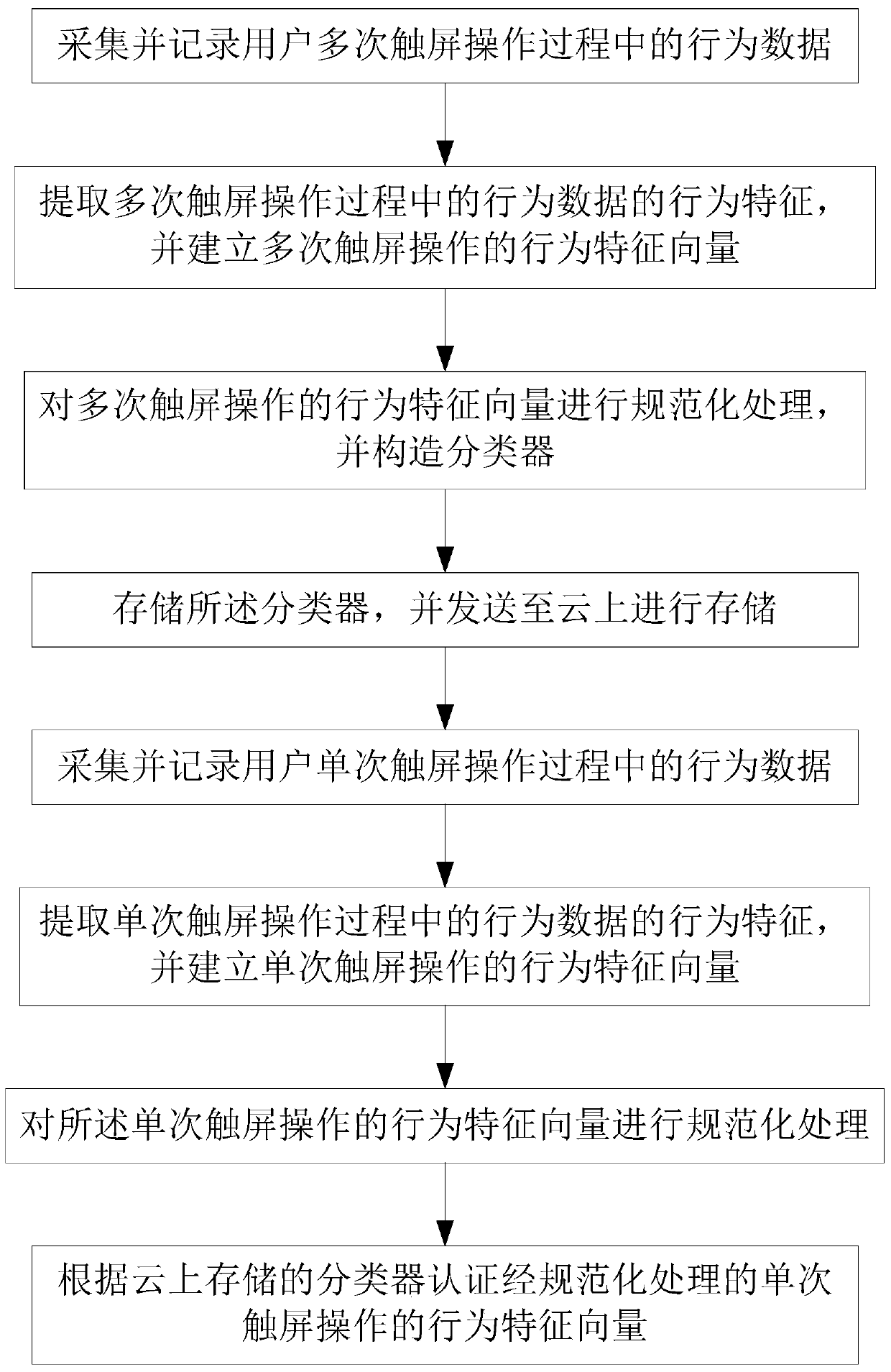
[0092] A smart device identity authentication method and client based on touch screen operation, specifically:
[0093] Install an application program on the client, and the application program authorizes the use of the built-in sensor of the client;
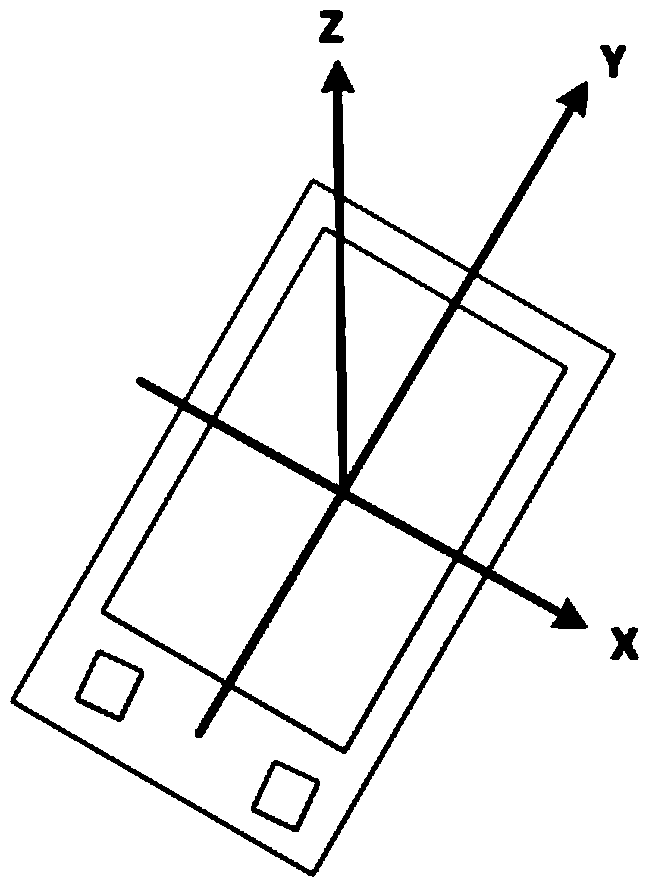
[0094] The client uses the built-in pressure sensor, gyroscope sensor, acceleration sensor, and direction sensor to collect user behavior data during multiple touch screen operations;
[0095] Decompose each touch screen operation into three stages: press down time, hold time, and lift-off time, among which
[0096] Press down time refers to the time from when the smart device receives the applied external force to when the external force reaches its peak value;
[0097] Holding time refers to the duration of receiving the peak external force from the smart device;
[0098] Lift-off time refers to the time from when the smart device re...
Embodiment 2
[0142] Please refer to Figure 7 to Figure 11 , the second embodiment of the present invention is:
[0143] The client's password is a digital password lock, Figure 7 It is the numeric keypad interface of the client screen. When establishing the touch screen area sub-feature of user touch screen operation, user touch screen gestures are divided into the following five gestures:
[0144] The first gesture: hold the device with the left hand, and touch the screen with the left thumb;
[0145] The second gesture: Hold the device with your right hand, and touch the screen with your right thumb;
[0146] The third gesture: hold the device with the left and right hands, and operate the touch screen with the left and right thumbs;
[0147] The fourth gesture: hold the device with the left hand, and touch the screen with the index finger of the right hand;
[0148] The fifth gesture: hold the device with the right hand, and touch the screen with the index finger of the left hand;...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com