Certificateless Elliptic Curve Hybrid Signcryption Method
An elliptic curve and certificate-free technology, which is applied in the field of network information security, can solve the problems of unrealizable, unreasonable resource-constrained environments, large calculation and communication costs, etc., achieve low communication costs, eliminate key escrow problems, good safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
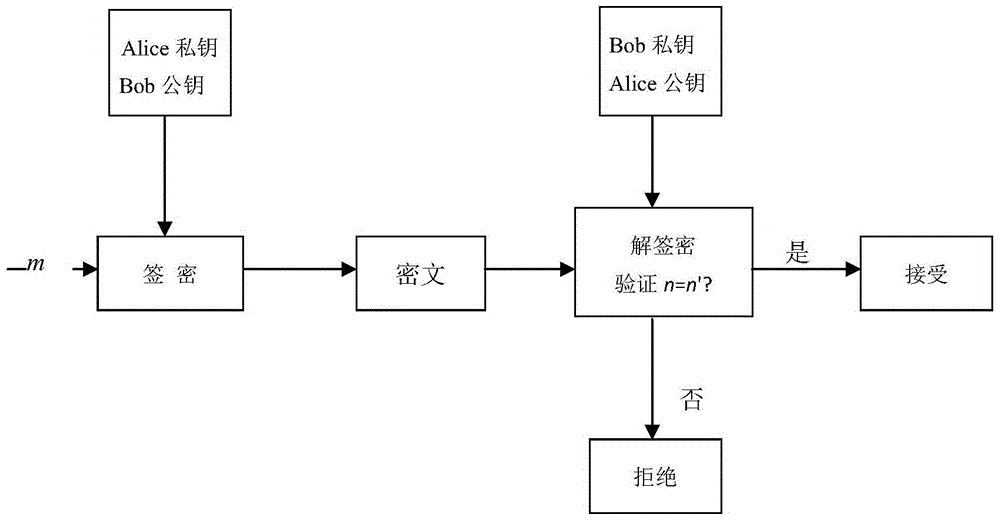
[0045] A large prime number p selected by the key generation center, p is 2 192 -2 64 ‐1 as an example, the steps of the certificate-free elliptic curve hybrid signcryption method are as follows:
[0046] A. System initialization
[0047] (A1) The key generation center chooses a large prime number p, where p is 2 192 -2 64 -1, finite field F p The congruence equation y on 2 ≡x 3 +ax+bmodp all solutions (x,y)∈F p ×F p , together with a point O at infinity constitutes F p Elliptic curve E on :y 2 ≡x 3 +ax+b, where a,b∈F p is satisfied with 4a 3 +27b 2 ≠0 constant. E(a,b) and the point O at infinity form an additive cyclic group G p , G is the group G p A generator of .
[0048] (A2) The cryptographically secure Hash function selected by the key generation center includes: H 1 :{0,1} * → Z p * , H 2 :G p ×G p →{0,1} β , H 3 :{0,1} *2 ×{0,1} n ×G p 3 → Z p * , H 4 :{0,1} * ×G p 3 →G p , where β is the symmetric key length of a Data Encapsulatio...
Embodiment 2
[0076] A large prime number p selected by the key generation center, p is 2 224 -2 96 +1 as an example, the steps of the certificate-free elliptic curve hybrid signcryption method are as follows:
[0077] In the system initialization (A1) step of this embodiment, the key generation center selects a large prime number p, and p is 2 224 -2 96 +1, finite field F p The congruence equation y on 2 ≡x 3 +ax+bmodp all solutions (x,y)∈F p ×F p , together with a point O at infinity constitutes F p Elliptic curve E on :y 2 ≡x 3 +ax+b, where a,b∈F p is satisfied with 4a 3 +27b 2 ≠0 constant. E(a,b) and the point O at infinity form an additive cyclic group G p , G is the group G p A generator of . Other steps in Step A1 are the same as in Embodiment 1.
[0078] Other steps are the same as in Example 1.
Embodiment 3
[0080] A large prime number p selected by the key generation center, p is 2 256 -2 224 +2 192 +2 96 +1 as an example, the steps of the certificate-free elliptic curve hybrid signcryption method are as follows:
[0081] In the system initialization (A1) step of this embodiment, the key generation center selects a large prime number p, and p is 2 256 -2 224 +2 192 +2 96 +1, finite field F p The congruence equation y on 2 ≡x 3 +ax+bmodp all solutions (x,y)∈F p ×F p , together with a point O at infinity constitutes F p Elliptic curve E on :y 2 ≡x 3 +ax+b, where a,b∈F p is satisfied with 4a 3 +27b 2 ≠0 constant. E(a,b) and the point O at infinity form an additive cyclic group G p , G is the group G p A generator of . Other steps in Step A1 are the same as in Embodiment 1.
[0082] Other steps are the same as in Example 1.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com