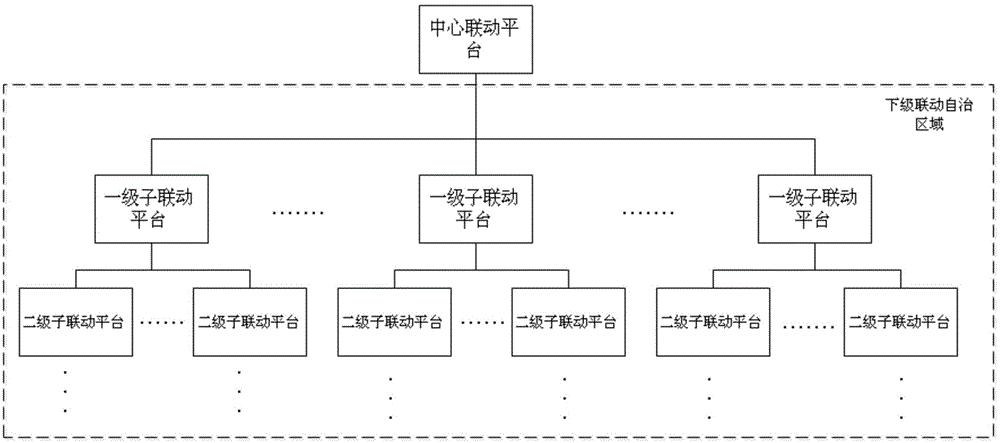
Security linkage system
A technology of security linkage and linkage, applied in the direction of program control devices, etc., can solve the problems of long time and inconvenient operation, and achieve the effect of convenient increase, accelerated processing speed, and convenient and simple use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0097] Now assume that a relationship between a smoke sensor and access control needs to be established. The specific realized function is: when the smoke sensor senses smoke, the access controller controls the door to remain closed, that is, the door cannot be opened at this time, and the door cannot be opened by swiping a card.
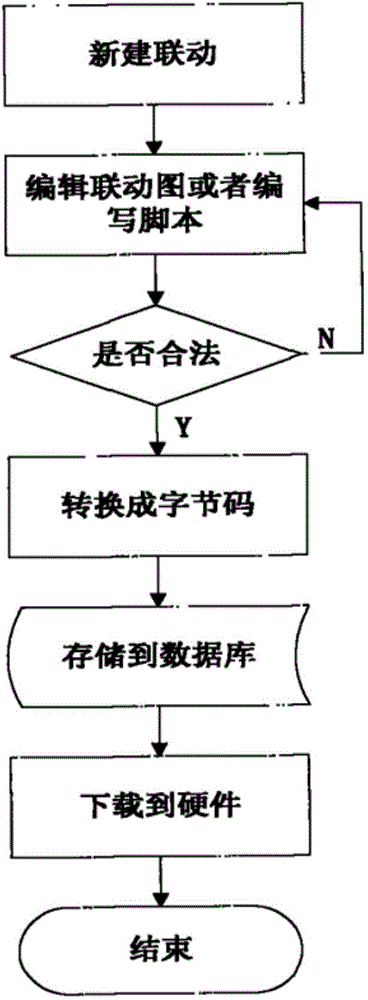
[0098] The specific operation is as follows:
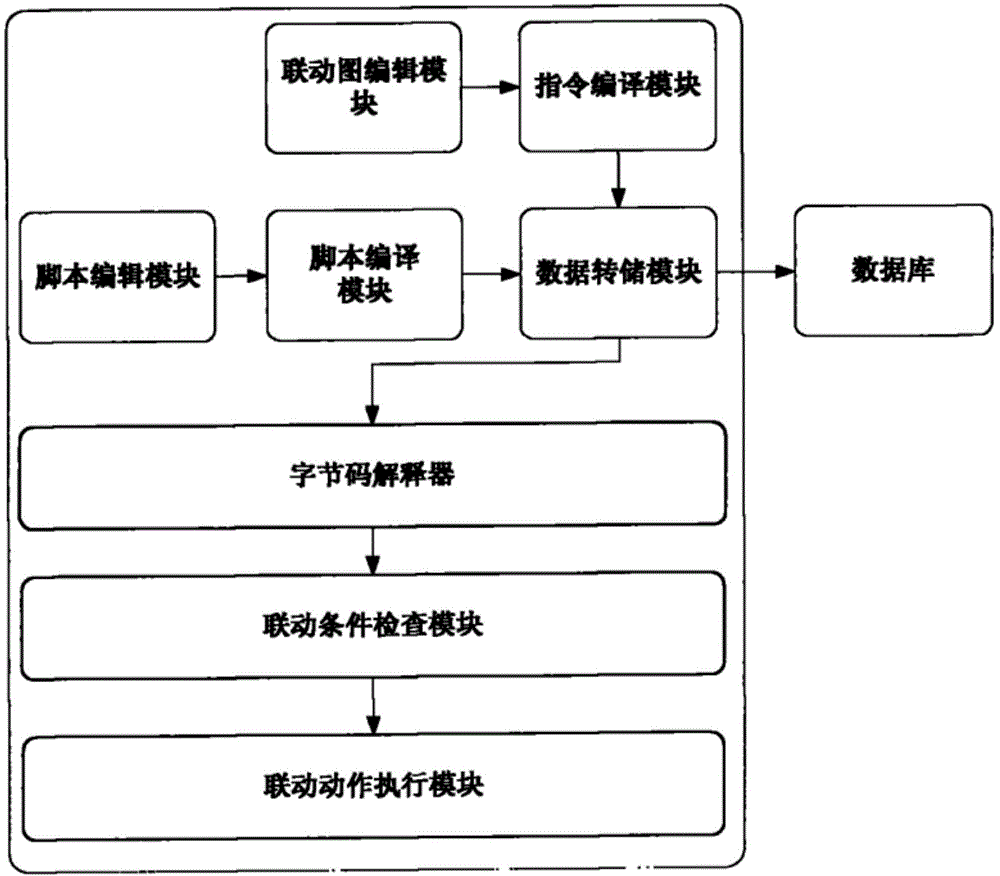
[0099] Step 1: Register the plug-in; specifically: register the plug-in of the smoke sensor and the plug-in of the access controller, that is, load the plug-in of the smoke sensor and the plug-in of the access controller, and display it on the interactive interface of the linkage platform.
[0100] Step 2: Select the category; specifically: select the smoke sensor and access controller to be controlled on the interactive interface;
[0101] Step 3: Create an instance; specifically: create a trigger instance of the smoke sensor and create an action instance of the access controller.
[0102] Step 4: Set...
Embodiment 2
[0105] This embodiment is roughly the same as Embodiment 1, and the difference is that in step 5, when establishing an association relationship, specifically:
[0106] Use the form of advance parameters to establish an association between the smoke sensor and the access controller. see Figure 12 , which is a schematic diagram of establishing an association between the smoke sensor and the access controller in this embodiment. First extract the trigger parameters of the smoke sensor and the action parameters of the access control controller, and then establish the corresponding relationship between the parameters. For example, in this embodiment, in this embodiment, the parameter that the smoke sensor detects smoke is associated with the action parameter that the access controller controls the door to keep closed; the parameter that the smoke sensor does not detect smoke is associated with the action parameter that the access controller controls the door to open Make an asso...
Embodiment 3
[0108] The difference between this embodiment and Embodiment 1 is that this embodiment adds a judgment on temperature when judging whether to trigger. That is, when judging whether there is smoke, judge whether the temperature reaches the threshold at the same time, if so, then control the door to close; if not, control the door to open. The specific steps are as follows:
[0109] Step 1: Register the plug-in; specifically: register the plug-in of the smoke sensor, the temperature sensor and the plug-in of the access controller, that is, load the plug-in of the smoke sensor, the plug-in of the temperature sensor and the plug-in of the access controller, and displayed on the interactive interface of the platform.
[0110] Step 2: Select the category; specifically: select the smoke sensor, temperature sensor and access controller to be controlled on the interactive interface;
[0111] Step 3: Create an instance; specifically: first create a trigger instance of the smoke sensor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com