XSS vulnerability detection method based on simulating browser behavior
A vulnerability detection and browser technology, applied in the field of XSS vulnerability detection system, can solve complex problems, cannot dynamically analyze the response information of the target site, and may not be able to judge the existence of XSS vulnerabilities, etc., and achieve the effect of high accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
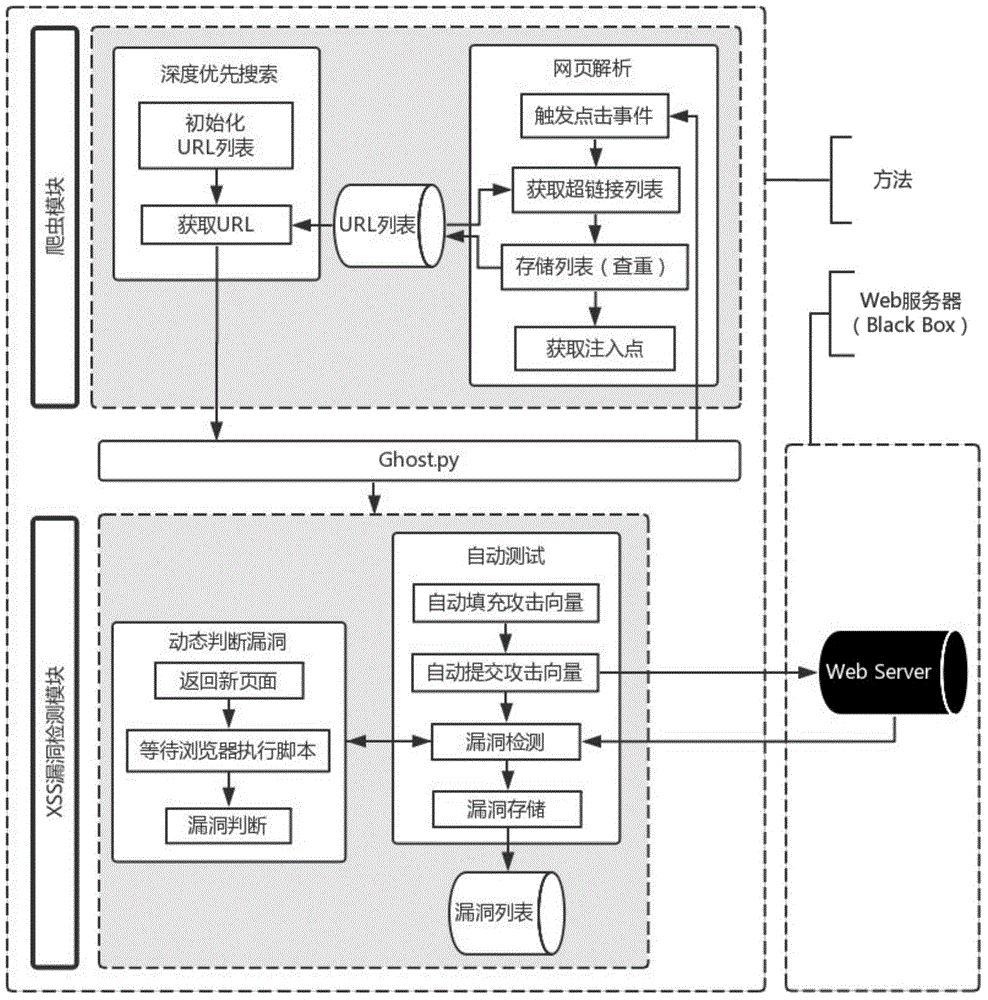
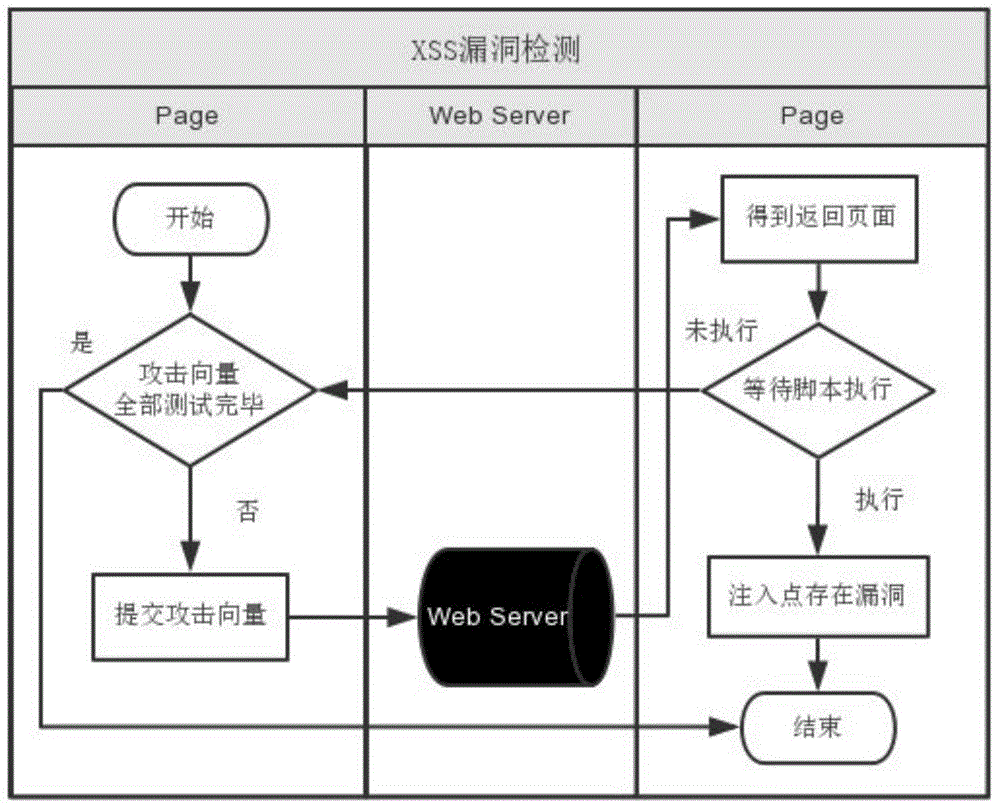
[0023] The principle of this system is based on Ghost.py's black-box test of the server, which consists of two parts: a crawler module and a vulnerability detection module. System architecture such as figure 1 shown.
[0024] 1.1 Crawler module
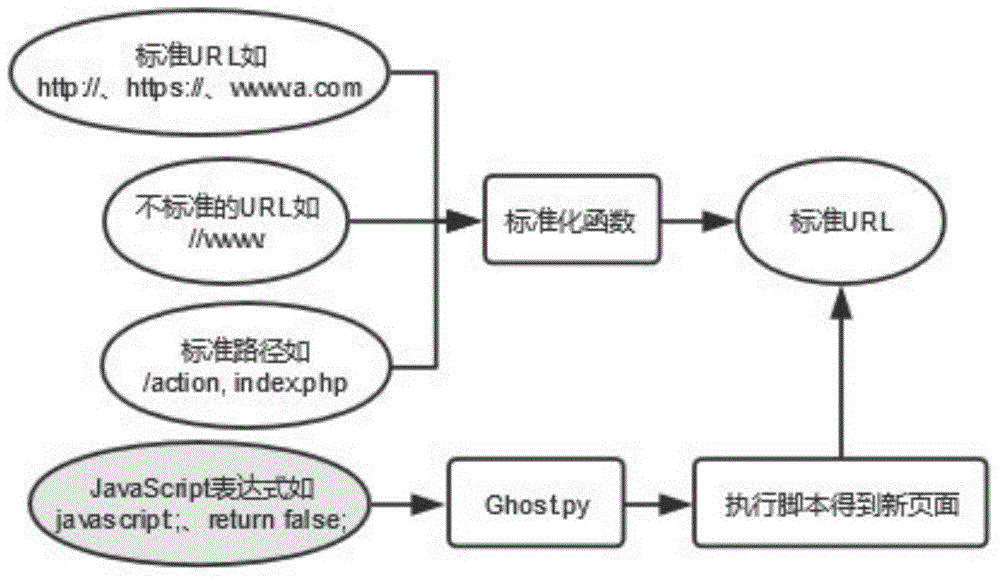
[0025] The crawler module implements the functions of exploring pages and analyzing web pages. The crawler that explores pages uses the recursive depth-first algorithm proposed in this paper to mine only pages under the same domain name. The algorithm description is shown in Algorithm 1.
[0026] Algorithm 1. Depth-first recursive algorithm for page exploration
[0027] Input: Start Website URL
[0028] Output: URLs of all pages with the same domain name crawled starting from the input URL
[0029] 1. Set the maximum depth MAX_DEPTH;
[0030] 2. Set the current depth depth=0;
[0031] 3. If the current depth is greater than the maximum depth, end; otherwise, go to step 4;
[0032] 4. Access the current URL;
[0033] 5. Obtai...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com