One based on gf(2 3 )'s (k,n) meaningful non-expansion image sharing and reconstruction method
An image and secret image technology, applied in image data processing, image data processing, instruments, etc., can solve the problem of not introducing forward authentication strategy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
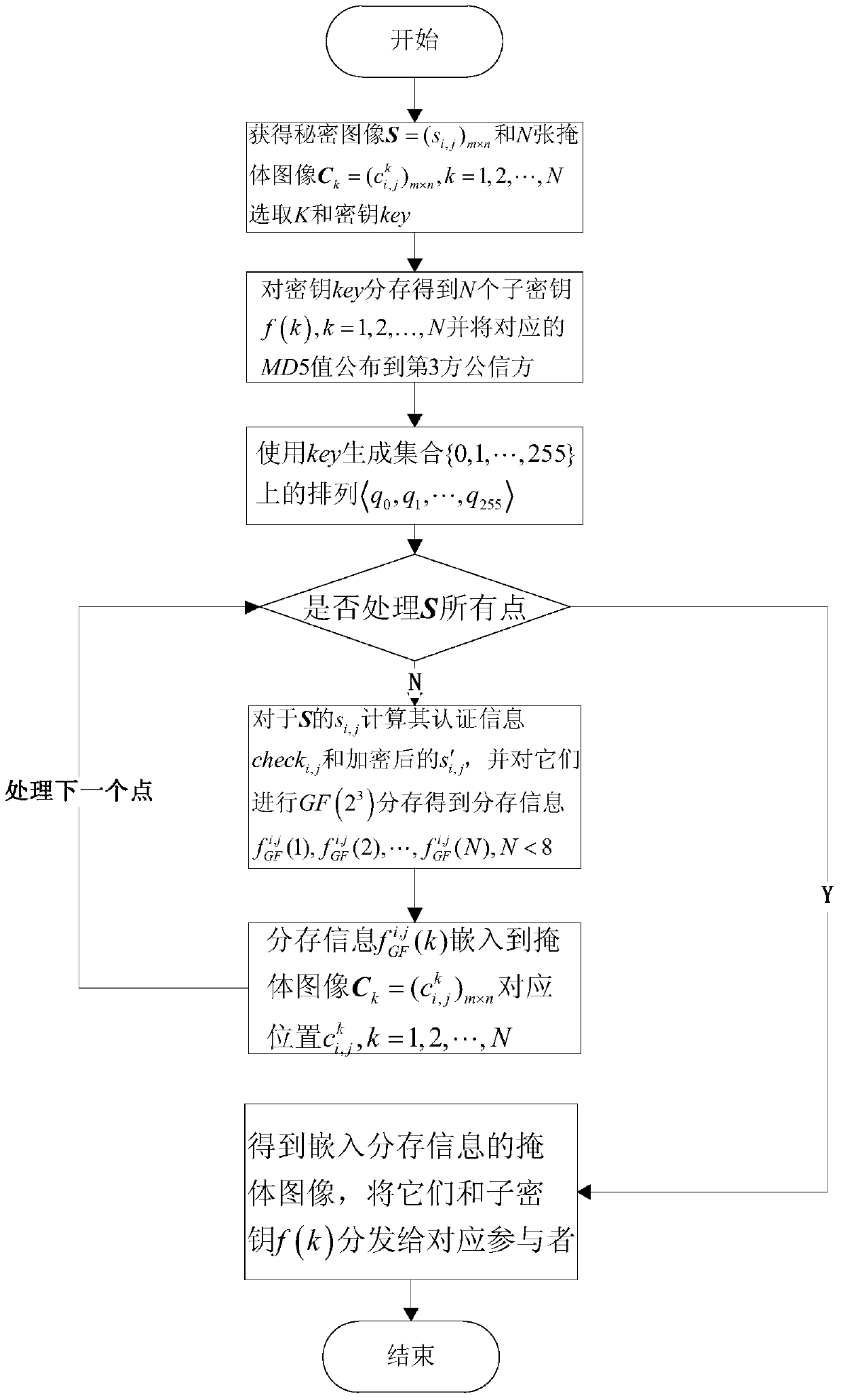
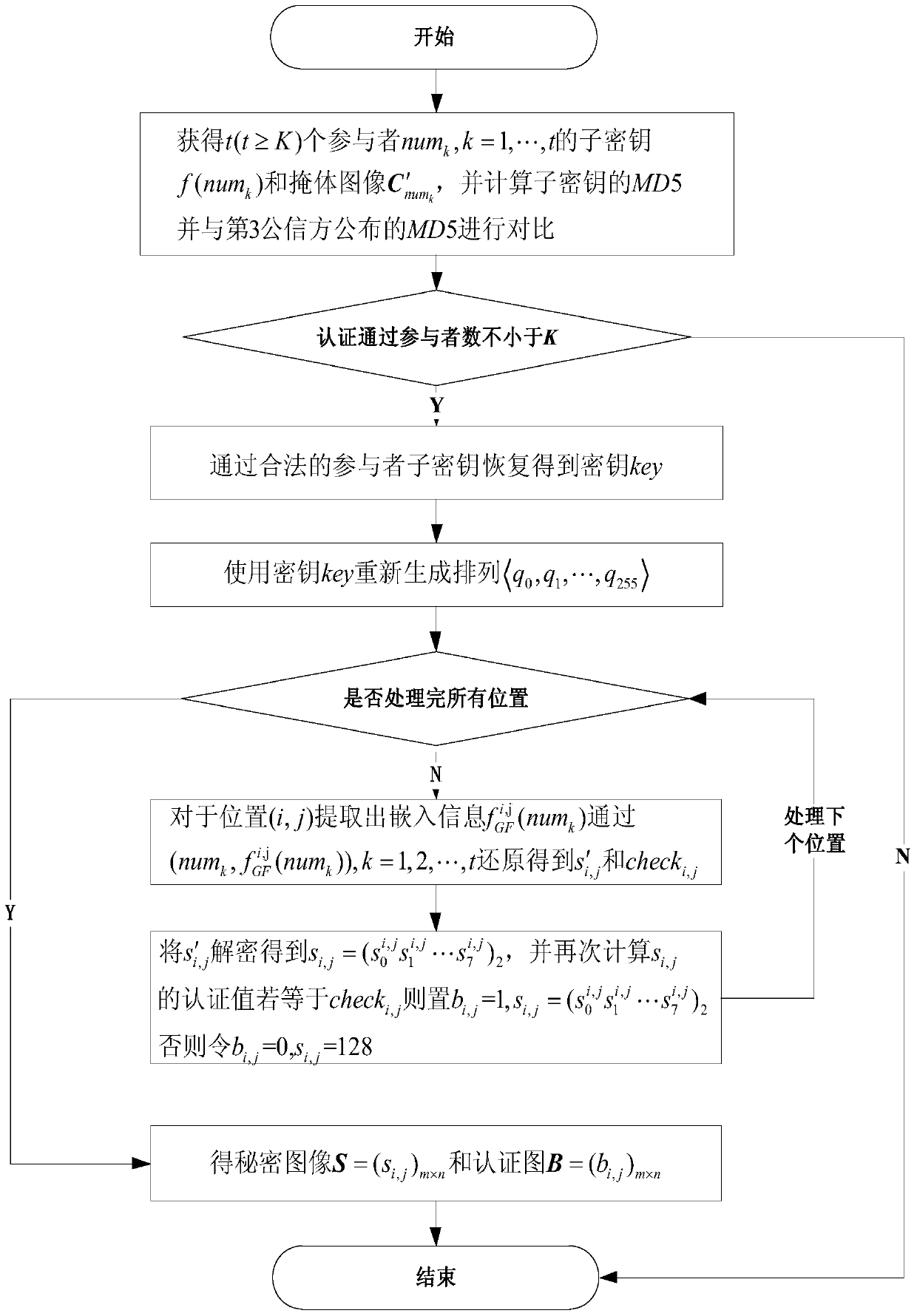
[0087] The method of the present invention is described in detail below in conjunction with the specific embodiments of the accompanying drawings:
[0088] Principle of the present invention:
[0089] The traditional sharing method is usually based on the Shamir-(K,N) threshold scheme, and its main idea is to construct the Lagrange polynomial shown in formula (1):
[0090] f(k)=(s+r 1 k+r 2 k 2 +…+r K-1 k K-1 ) mod p (1)
[0091] In formula (1), s is the secret, r 1 ,r 2 ,...,r K-1 Is a random integer, p is a prime number and satisfies s, r 1 ,r 2 ,...,r K-1 ∈[0,p), N is an integer in the range of [K,p). Substituting x=1,2,...,N into formula (1) in order to form N distribution information (1,f(1)),(2,f(2)),...,(N,f(N) ).
[0092] If t (t≥K) different distribution information (num k ,f(num k )), k=1, 2, ..., t, then f(x) can be restored first according to the Lagrange interpolation formula of formula (2), and then the distributed secret s=f(0) can be reconstruct...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com