Enterprise mobile safety gateway method of application flow management, application acceleration and safety
A technology of application traffic and security gateway, applied in the field of data security and interaction, can solve problems such as hidden dangers of enterprise information security, illegal uploading of enterprise data, and performance degradation of mobile terminals, so as to improve performance and battery life, solve slow access speed, Effect of increasing data exchange speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
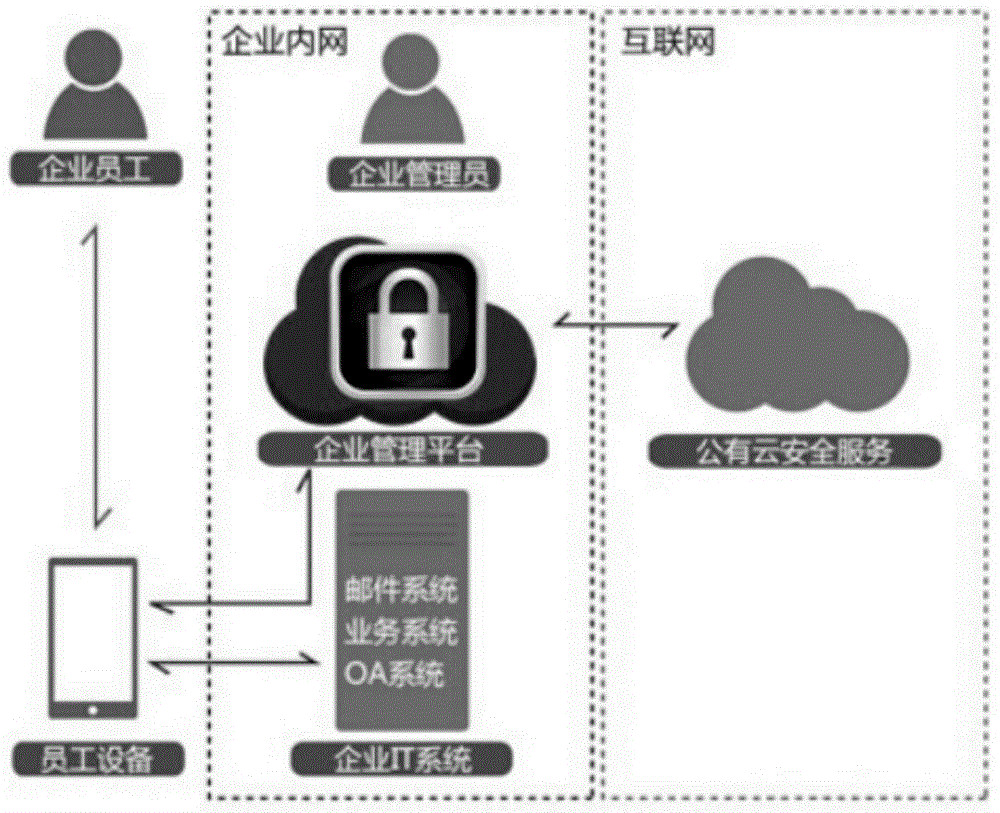
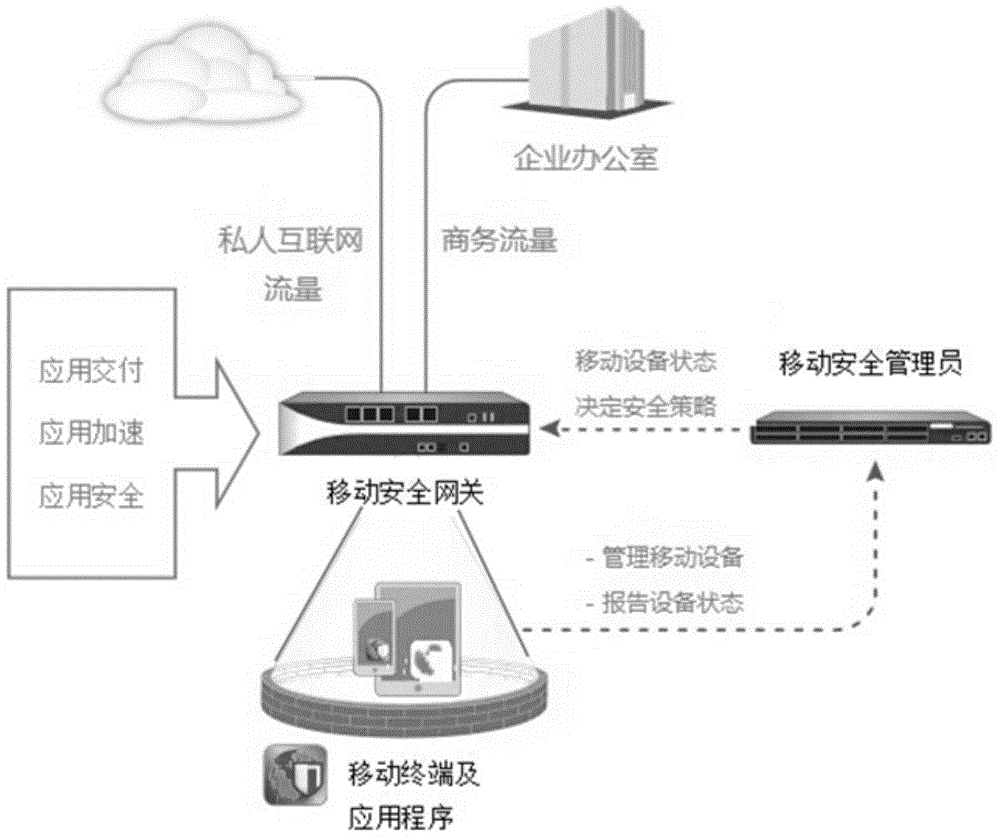
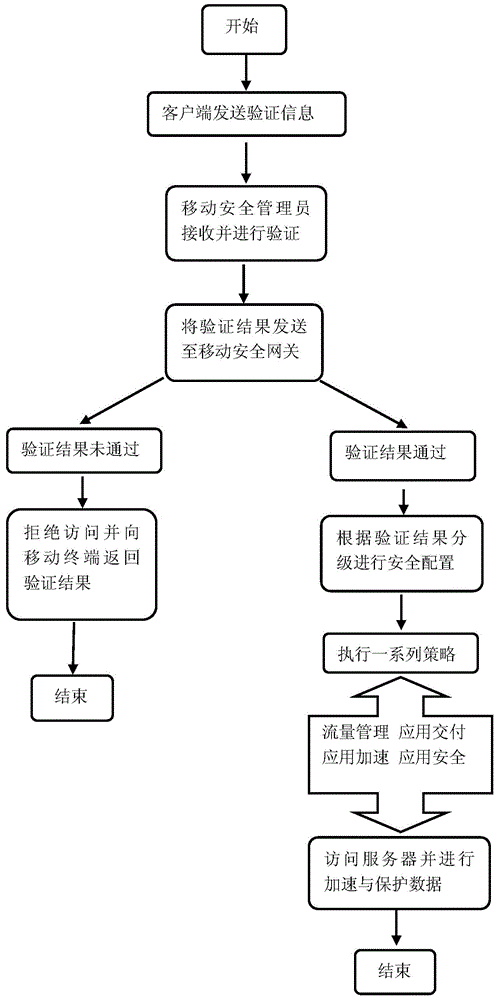
[0036] When an enterprise mobile user needs to access sensitive data on an enterprise server, the software module running on the mobile terminal is designed to establish a VPN security channel with the gateway, and the gateway provides the mobile security administrator with information such as user identity, access content, used equipment, and equipment status. The software module running on the gateway implements corresponding security policies to control the mobile terminal's access to data based on the information provided by the user identity, access content, device use, and device status, and the mobile terminal interacts with the enterprise server for applications. At the same time, functions such as application delivery, application acceleration, and application security are implemented through the software modules running on the gateway.
[0037] Among the above software modules installed on the gateway, the following functional modules are included:
[0038] A. Applic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com