A design method of etl framework for safety monitoring business analysis
A business analysis and security-oriented technology, applied in the field of data extraction-transformation-loading framework design, can solve problems such as concurrency limitation and scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] Below in conjunction with specific embodiment, further illustrate the present invention.
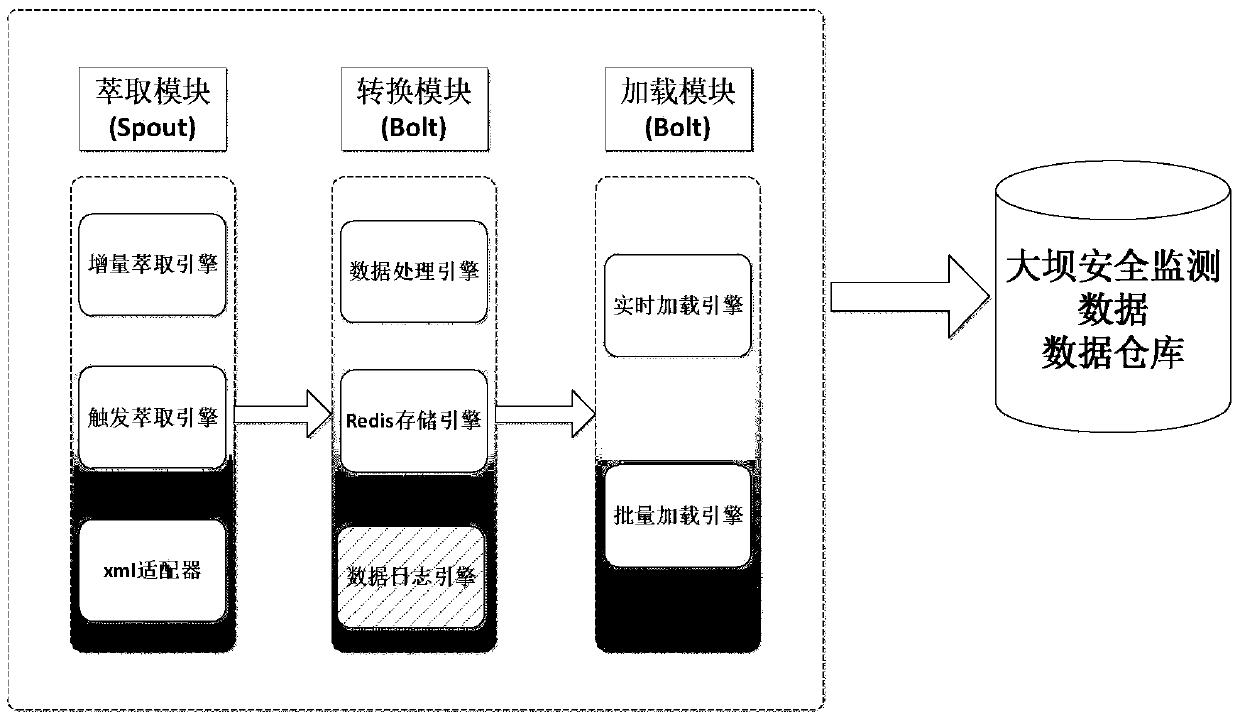
[0015] figure 1 Design a method structure diagram for the ETL framework oriented to security monitoring business analysis. The ETL framework design method for safety monitoring business analysis includes data extraction module, data conversion module and data loading module.
[0016] The data extraction module refers to the process of obtaining source data from multiple heterogeneous data sources, by using the XML adapter to confirm the data source and using the incremental extraction technology engine for data extraction.
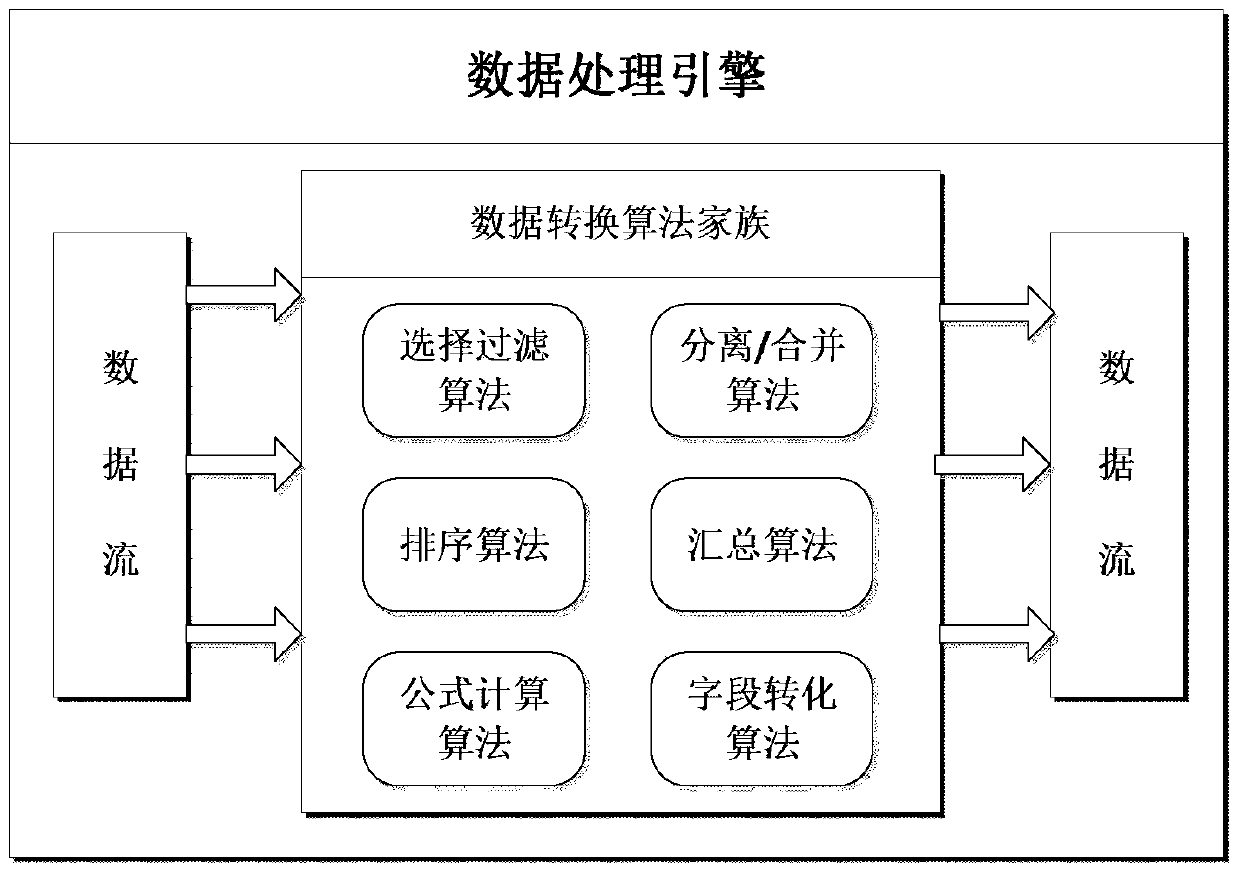
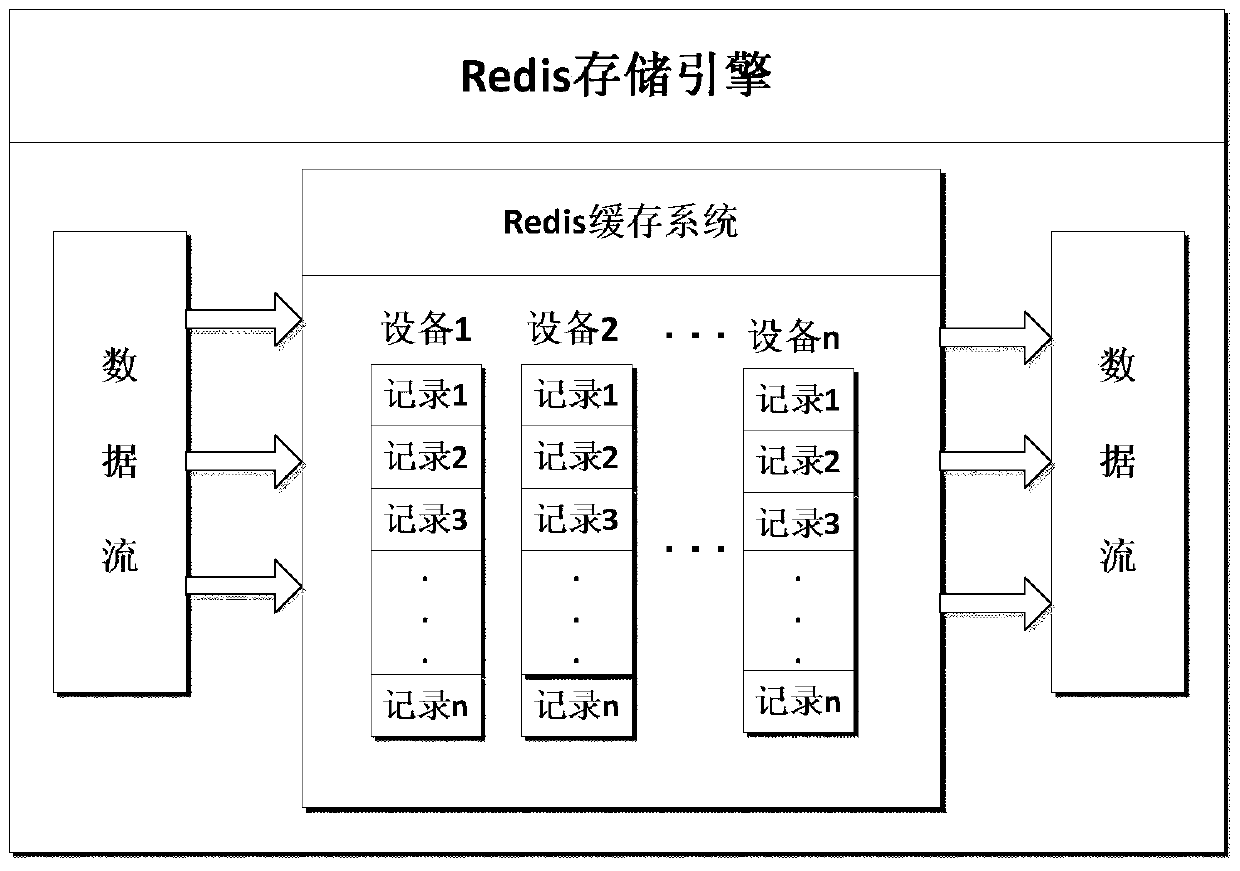
[0017] The data conversion module is the link connecting the data extraction process and the data loading process. In this process, the two components of "data processing engine" and "Redis storage engine" are used for data conversion.
[0018] Data loading module, the loading of data mainly includes two loading types: initial loading and incremental loading...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com