Privacy protection method of lbs trajectory based on location label
A privacy protection and labeling technology, applied in the field of information security, can solve problems such as time-consuming, increased difficulty for K users, and slow LBS request speed, and achieve the effect of protecting location privacy and trajectory privacy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
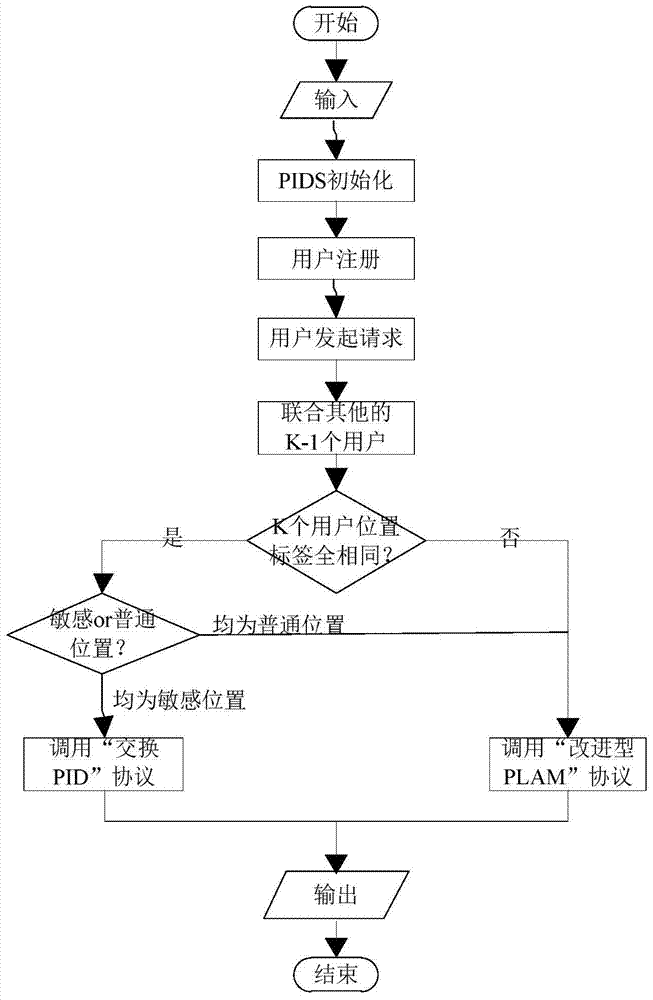
Embodiment 1
[0045] In this embodiment, it is assumed that 100 users are evenly distributed in area A (area A includes common locations and sensitive locations). For the convenience of simulation, these 100 users are within the communication range. user u 1 In a common location and initiate an LBS request, other users may have initiated aggregation request messages, but the number of aggregations does not exceed K (random). The probability p = 0.5 of exchanging PID protocols. In order to facilitate message transmission, this embodiment assumes that the LP server (LBS provider) provides 32 service types, so Serve has 32 bits. In order to satisfy L diversification, this embodiment assumes that L=K / 2.
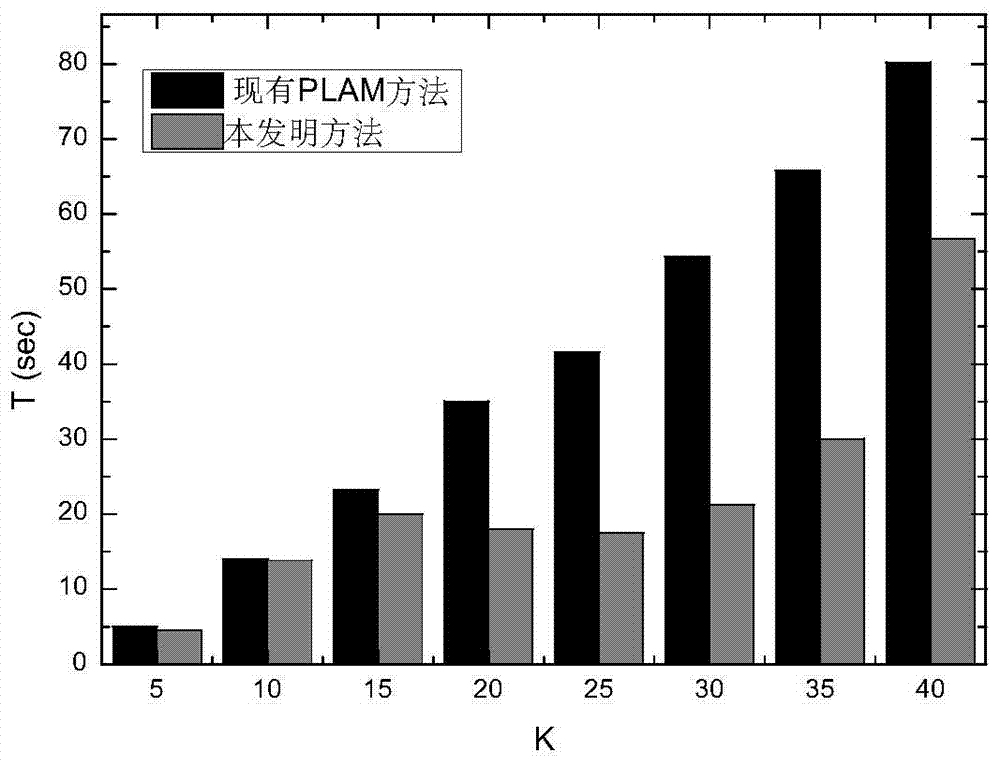
[0046] figure 2 It is the comparison of the request delay of the existing PLAM algorithm and the algorithm provided by the present invention under different K values. It can be observed from the figure that the request delay of the existing PLAM algorithm increases with the increase of th...
Embodiment 2
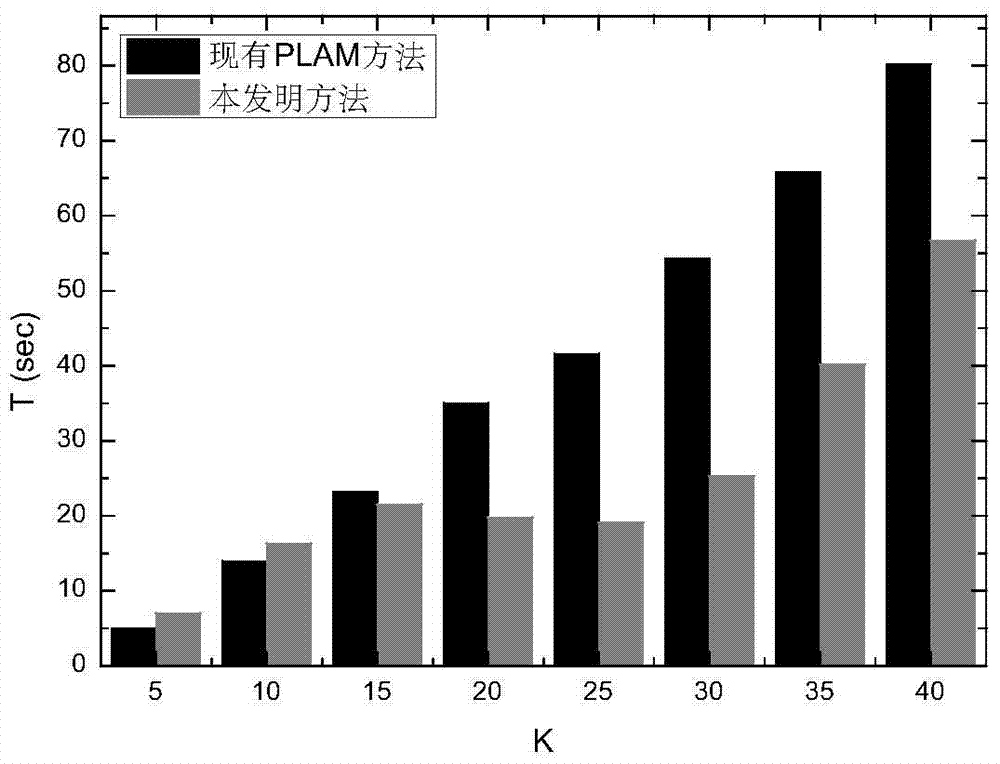
[0048] In this embodiment, it is assumed that 100 users are still in area A, but most of them are densely distributed in sensitive locations, and a few of them are scattered in common locations. user u 1 Be in a sensitive location and initiate an LBS request. image 3 The variation of the request delay with the value of the security parameter K of the LBS system in this embodiment is described. From image 3 It can be seen that when the K value is less than 20, the request delay of the PLAM algorithm is lower than that of the trajectory privacy protection algorithm based on location tags. Because when the user is in a sensitive location, the user density in the sensitive location is high, and it is very likely that more than half of the combined K users are in the same location. Therefore, it is necessary to execute the PID exchange protocol, and the process of exchanging PIDs needs to consume a small amount of time, thus lengthening the request delay. When the value of K ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com