Virtualization supporting guest operating systems using memory protection units
A memory protection and memory technology, applied in memory systems, preventing unauthorized use of memory, instruments, etc., can solve problems such as reducing the cost of data processing systems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
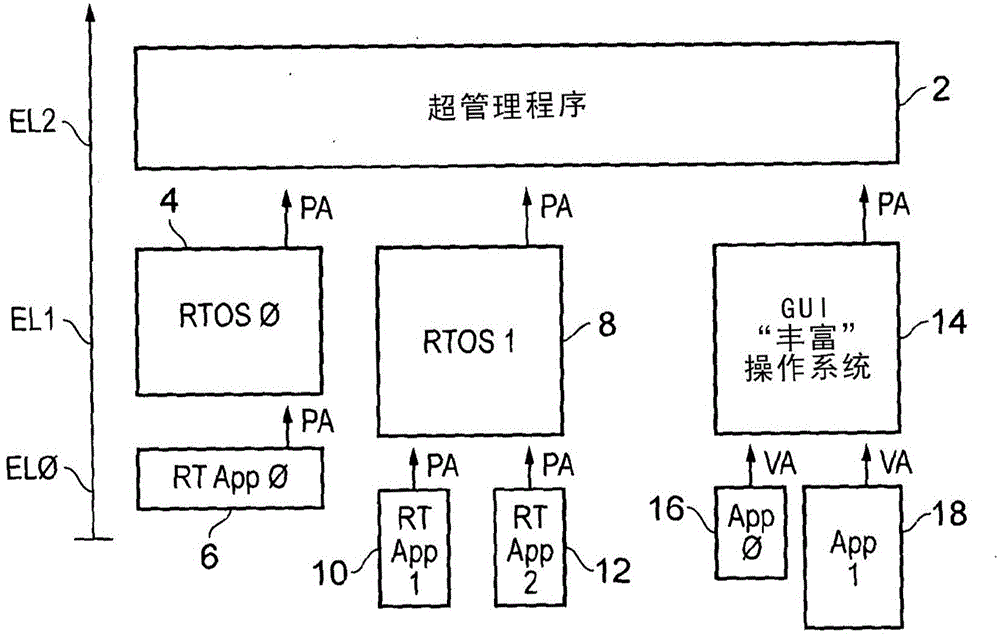
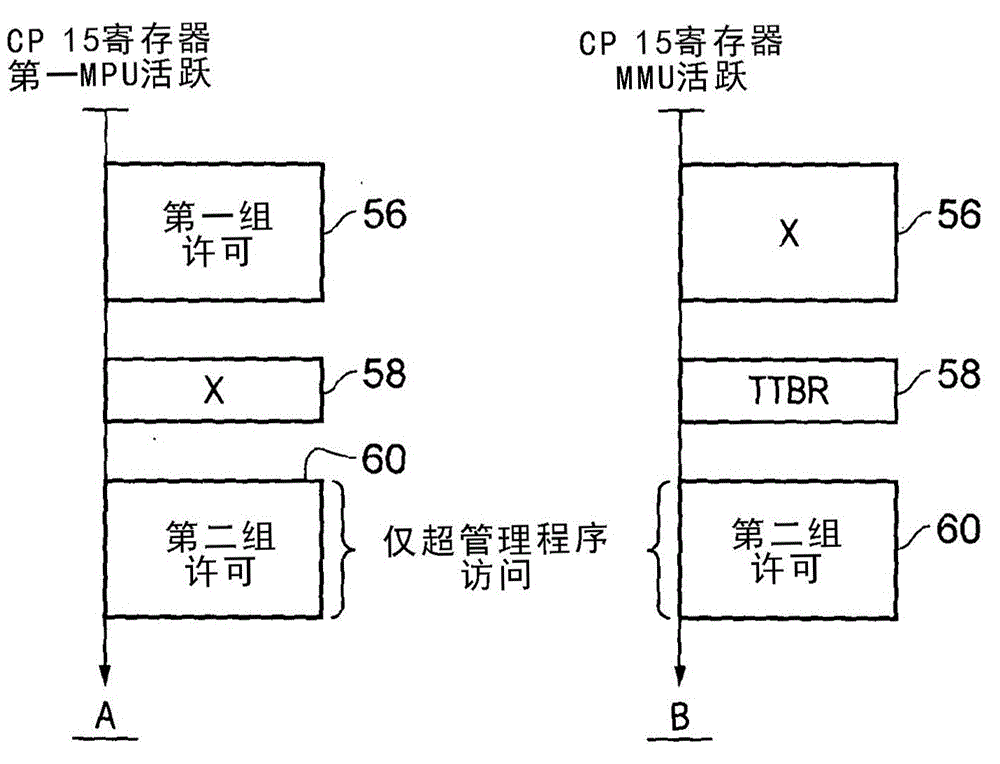
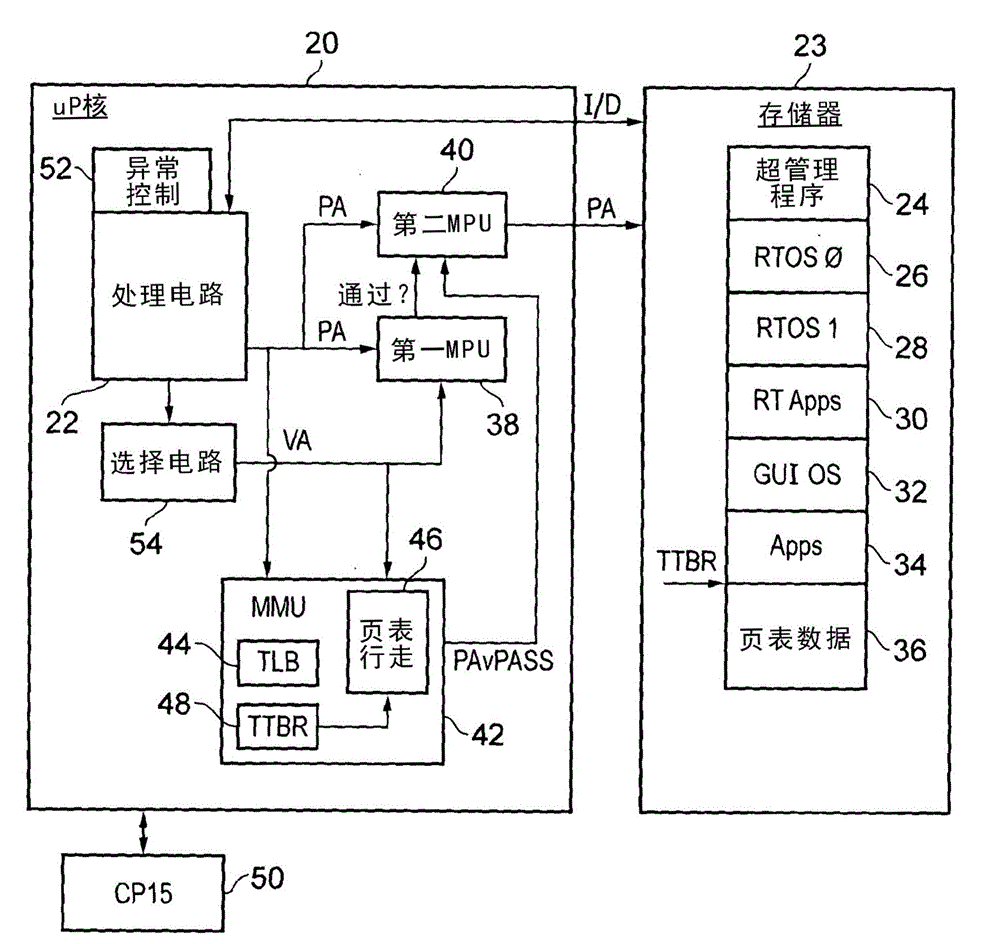
[0053] figure 1 A system supporting multiple virtual real-time processors and a virtual processor using virtual memory is schematically shown. The hypervisor 2 works at the second exception level EL2 and is used to control switching between virtual processors and to protect / isolate these virtual processors from each other. The first virtual real-time processor uses the first real-time operating system 4 to support the running of real-time applications 6 . When the real-time application 6 and the real-time operating system 4 specify a memory access operation, they both generate a physical address PA. The physical address PA generated by the real-time application 6 is subject to a first level of memory protection (on behalf of the guest real-time operating system 4 ) performed by a first memory protection unit, which is controlled by the real-time operating system 4 . If the memory access request is permitted by this first set of permissions, the memory access operation is als...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com