Access control method based on attribute-based access control policy
An access control strategy and access control technology, applied in the network field, can solve problems such as inconsistency between old and new permissions, time-consuming efficiency, etc., and achieve the effect of high error rate and improved efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The principles and features of the present invention are described below in conjunction with the accompanying drawings, and the examples given are only used to explain the present invention, and are not intended to limit the scope of the present invention.
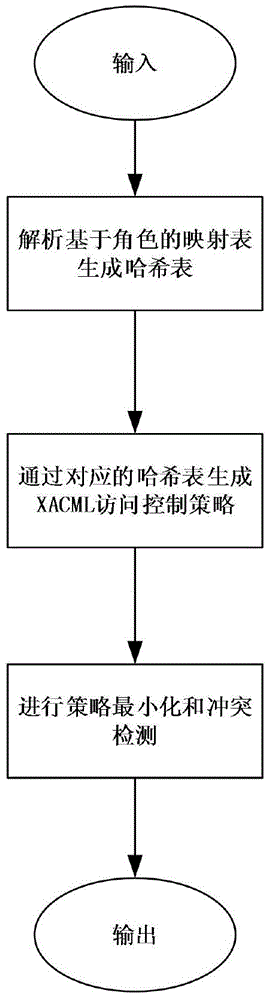
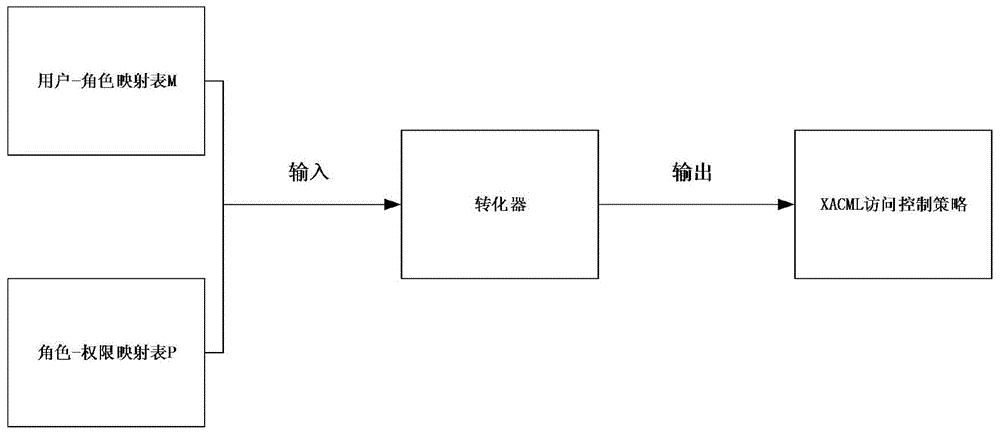
[0029] This solution intends to implement an access control conversion mechanism between the Internet of Things search engine and the third party, and transform the third party's role-based access control into the attribute-based XACML access control commonly used in the Internet of Things. In this way, the Internet of Things search engine can quickly respond to the search request according to the XACML access control and the database data submitted by the third party.
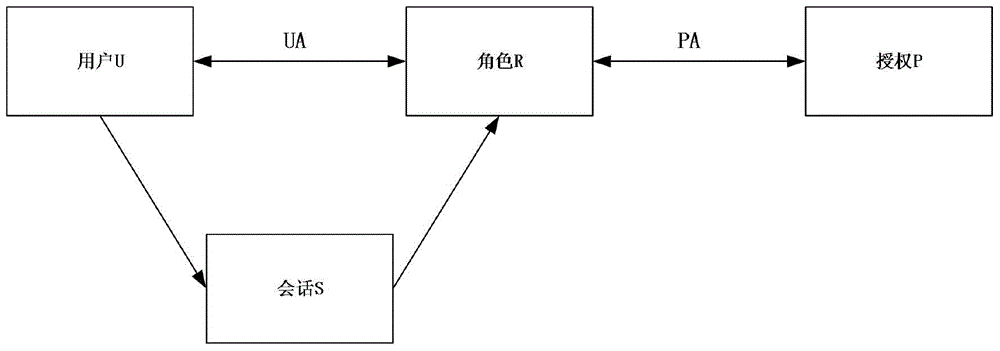
[0030] A complete role-based access control model such as figure 1 As shown, UA represents the mapping relationship between users and roles, PA represents the mapping relationship between roles and permissions, and session S is generated when users ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com