Key protection method and safety chip based on physical no-cloning function
A security chip and key protection technology, applied in key distribution to achieve the effect of protecting security and saving costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
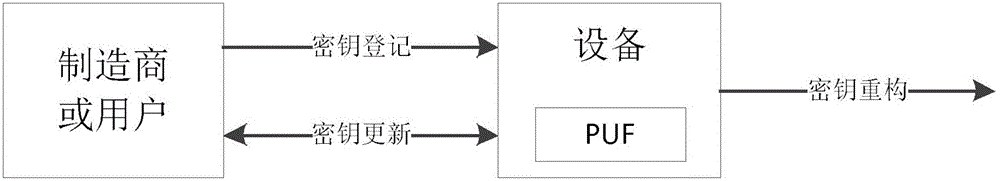
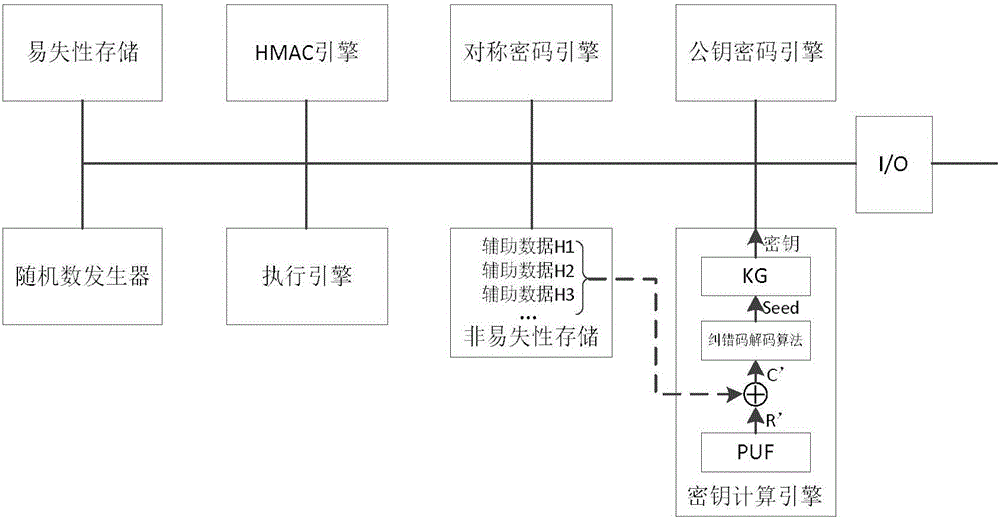
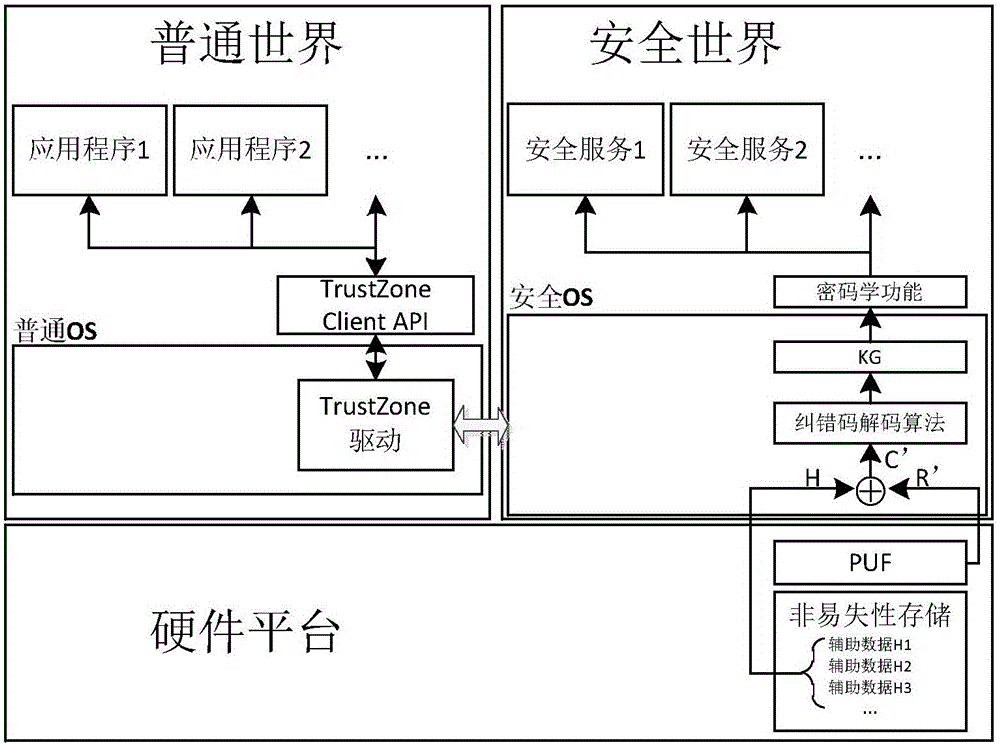
[0064] combine figure 1 ,Such as figure 2 The security chip shown includes volatile storage, HMAC engine, symmetric encryption engine, public key encryption engine, random number generator, execution engine, non-volatile storage (Non-volatile Memory, NVM), key calculation engine and other components. During the entire life cycle of the security chip, it will go through the key registration stage, the key reconstruction stage, and may also go through the key update stage.
[0065] Volatile storage is used to save temporary data when the security chip is running.
[0066] The HMAC engine is used to calculate the message authentication code, and the key used is generated by the key calculation engine.
[0067] The symmetric cipher engine is used to perform encryption and decryption operations based on symmetric cryptography, and the keys used are generated by the key calculation engine.
[0068] The public key cryptographic engine is used to perform encryption, decryption an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com