A highly efficient symmetrical secret key apparatus which allows pairing and a pairing method
A technology of symmetric keys and paired keys, which is applied to encryption devices with shift registers/memory, etc., can solve problems such as single encryption mode, reduced security, and increased keys, and achieve good scalability, reduced area, Overall compact effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings.
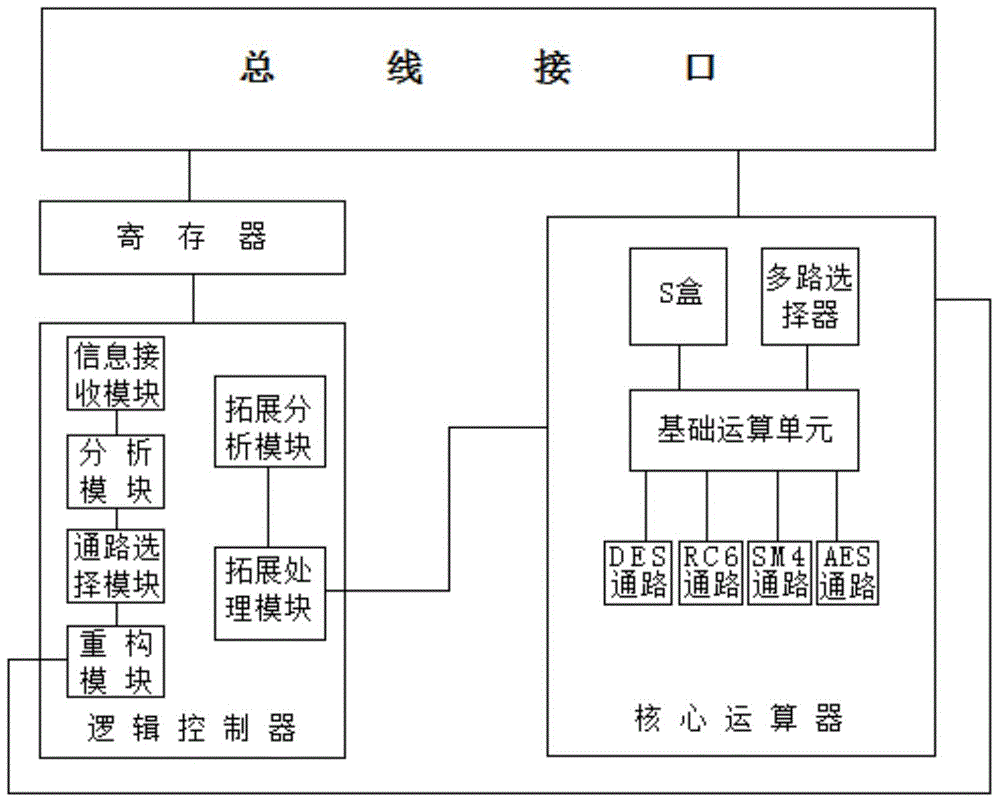
[0037] The present invention selects SM4, AES, DES, RC6 as the design object: SM4 and AES are based on the operation on the integer field, we call it homogeneous type algorithm; DES, RC6 are different, are called heterogeneous type algorithm. The multiple algorithms selected in this way illustrate the universality and good scalability of the architecture design of the present invention.
[0038] Such as figure 1 As shown, the top-level architecture design of the cryptographic algorithm is carried out according to the design requirements of high-efficiency and configurable and the design method of the general function IP core. encrypted / plaintext. The register module is used to store user configuration information and module status information. The control logic flexibly generates control information according to the u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com