Method, system and apparatus for carrying out safety authentication on application programs
An application program and security authentication technology, applied in the field of security authentication, can solve the problem of illegal theft and loss of key algorithms and sensitive information by hackers, and achieve the effect of enhancing integrity, improving security, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example
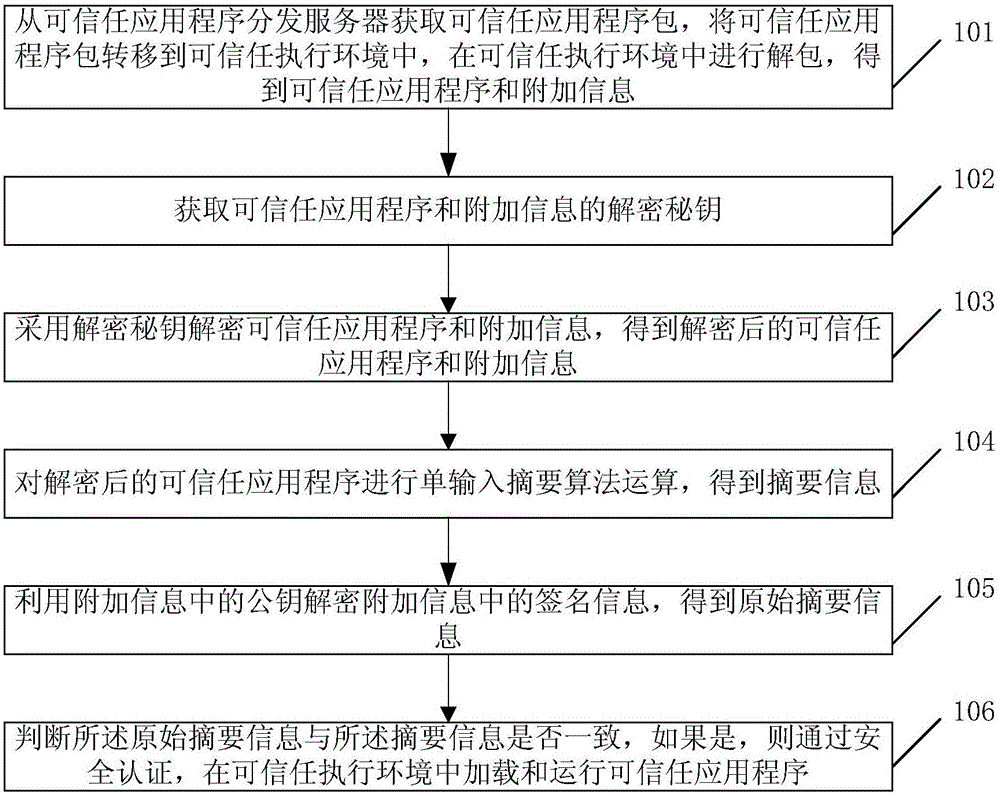
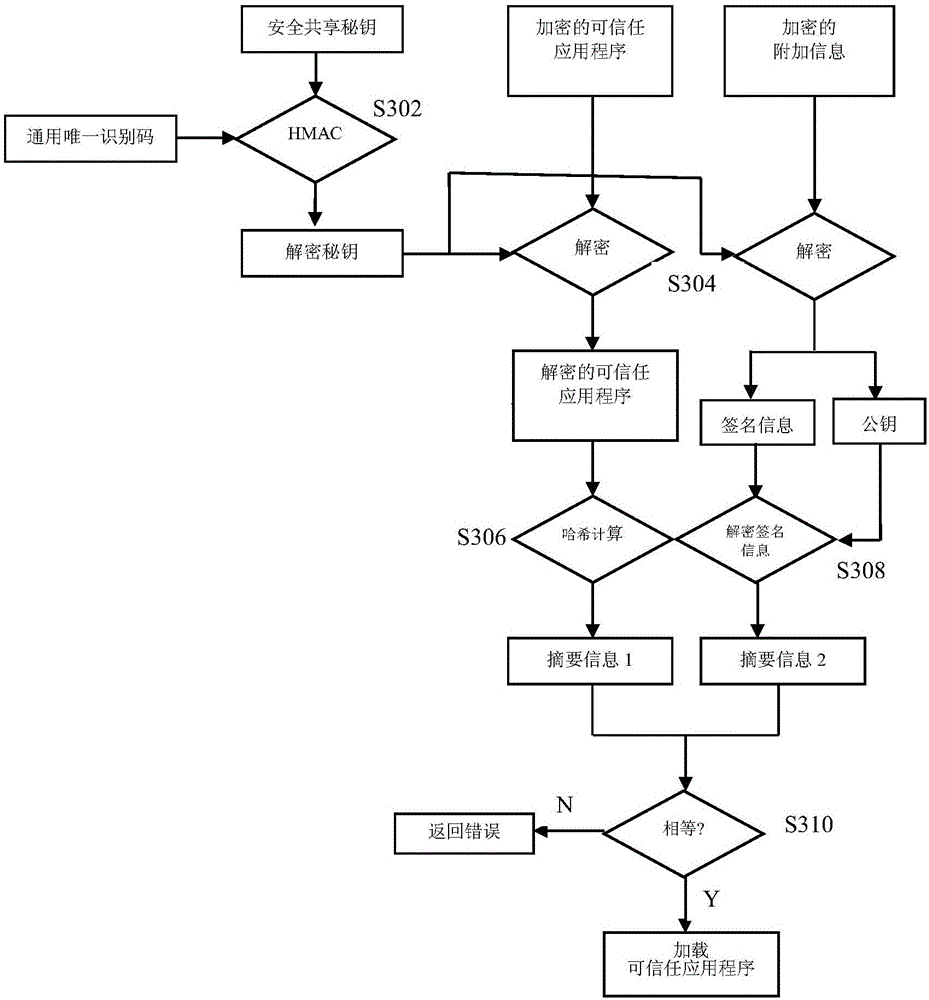
[0091] see image 3 , which is an example of a flow chart of the security authentication of a trusted application by a smart device in the present invention, which includes the following steps:
[0092] Step S302: Use the UUID corresponding to the trusted application and the secure shared key in the trusted execution environment to perform HMAC calculation to obtain a decryption key for decrypting the trusted application and additional information.
[0093] Step S304: Use the decryption key obtained in step S302 to decrypt the trusted application and the corresponding additional information to obtain the decrypted trusted application and the corresponding additional information.
[0094] Step S306: Perform a hash operation on the decrypted trusted application program to obtain summary information 1.
[0095] Step S308: Use the public key in the additional information to decrypt the signature information in the additional information to obtain the digest information 2.
[0096]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com