A File Encryption System Based on Bridge File System
A file system and file encryption technology, which is applied in the field of information security, can solve problems such as complex technical solutions, complex technical solutions, and inability of users and programs to operate directly.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The specific implementation of the present invention will be described below in conjunction with the accompanying drawings.
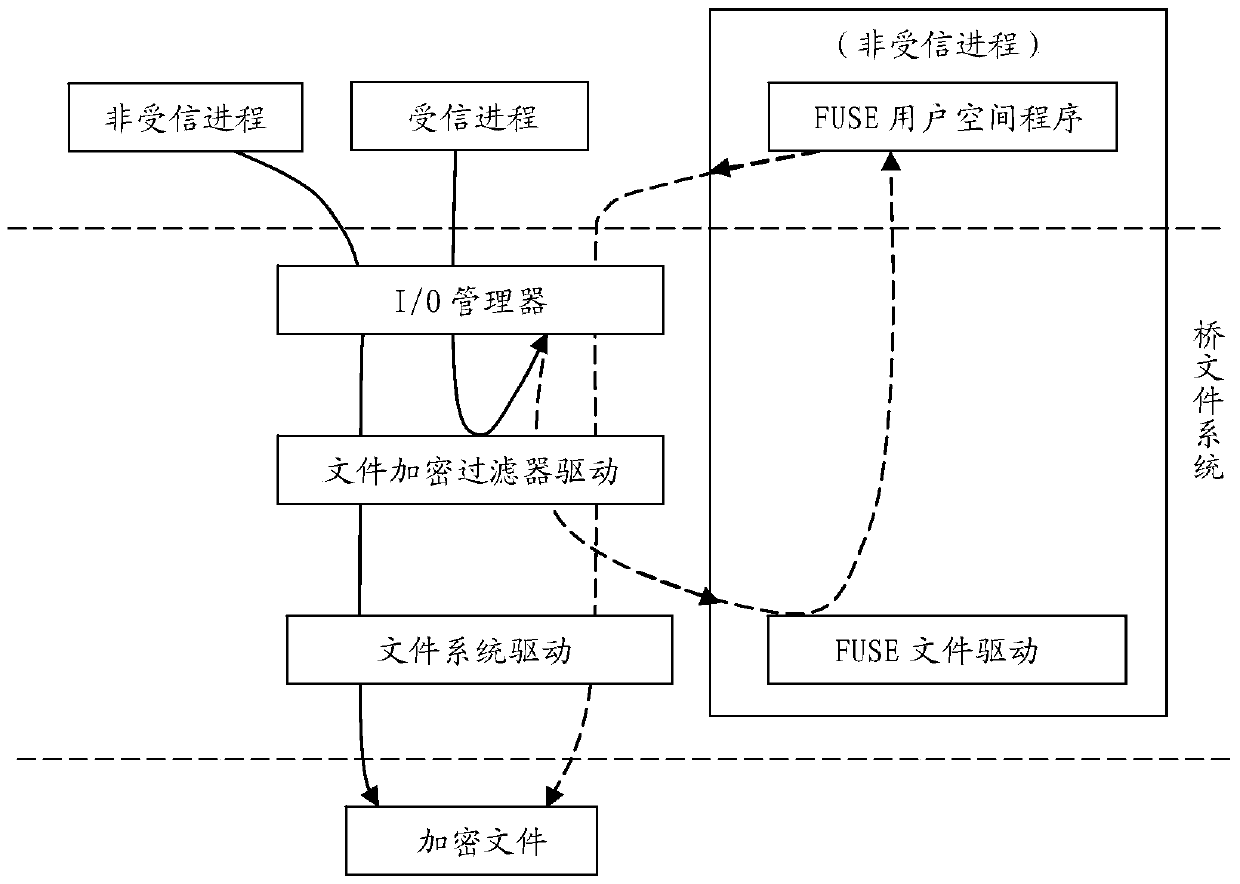
[0030] The structure and principle diagram of the system of the present invention under Windows are as figure 1 As shown, wherein, the development of the file encryption filter driver can be developed using Windows file filter driver (filter driver) or micro-filter driver (mini-filter driver) technology. Utilizing the Windows file filter driver or minifilter driver to implement the encryption function and to judge trusted processes and untrusted processes is a mature technology, which will not be described here. For file redirection, you can use the reparse point function of Windows file I / O (see simrep.c code); it should be noted that, in addition to redirecting the file path in the open or create file operation (IRP_MJ_CREATE), for The rename file path in the file rename operation (IRP_MJ_SET_INFORMATION+FileRenameInformation) also needs to be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com