Identity verification method and identity verification device
An identity verification method and verification code technology, applied in the field of identity verification methods and devices, can solve problems such as low security, cracking, and high cost, and achieve the effects of increasing difficulty, improving security, and improving cracking resistance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0058] see Image 6 , shows a flow chart of an identity verification method provided by the first embodiment of the present invention. combine figure 2 , this embodiment describes the processing flow of the server, and the identity verification method provided by this embodiment includes the following steps:
[0059] In step S11, the server receives the verification code pull request sent by the user terminal.
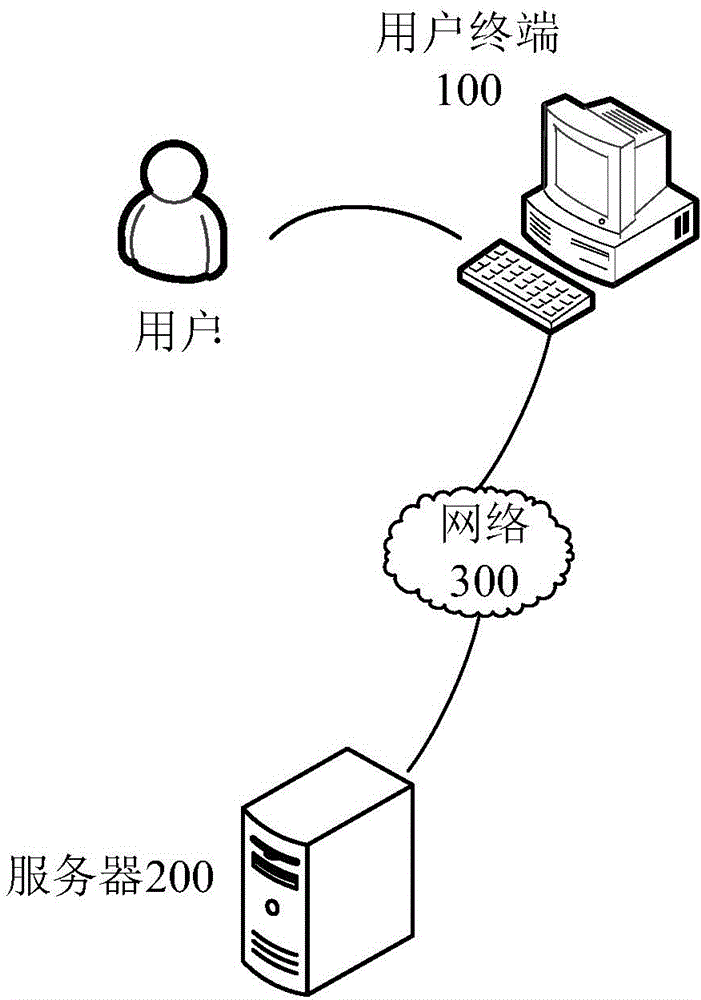
[0060] When the browser in the user terminal 100 or the clients of various applications detects that the user performs sensitive operations that require identity verification, such as initiating transactions, or logs in to an application too many times within a certain period of time, or logs in to an application in a different place, or logs in When an application password is entered incorrectly for too many times, it may be determined that the identity verification request is triggered, and the user terminal 100 may send a verification code pull request to the ser...
no. 2 example
[0098] see Figure 13 , shows a flow chart of an identity verification method provided by the second embodiment of the present invention. combine figure 2 , this embodiment describes the processing flow of the user terminal, and the identity verification method in this embodiment may include the following steps:
[0099] In step S21, the user terminal sends a verification code pull request to the server.
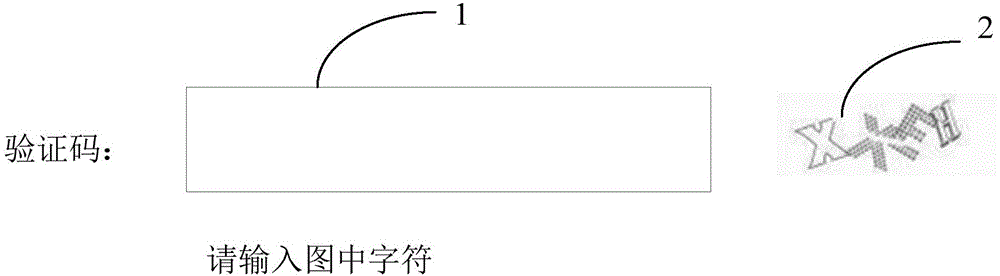
[0100] Step S22, receiving and displaying the verification code background picture sent by the server and spliced with multiple sub-pictures, wherein the multiple sub-pictures are respectively spliced into multiple vacant areas in the verification code background picture.
[0101] The background image of the verification code spliced with multiple sub-images displayed on the user terminal can be as follows: Figure 14 As shown in FIG. 2 , the verification code background picture spliced with multiple sub-pictures can be displayed in the user interaction interface...
no. 3 example
[0112] see Figure 15 , Figure 15 Shown is a flow chart of an identity verification method provided by the third embodiment of the present invention. combine figure 2 , this embodiment describes an interactive processing flow between a user terminal and a server. The authentication methods in this embodiment may include:
[0113] In step S301, the user terminal sends a verification code pull request to the server.
[0114] Step S302, randomly select a verification code background picture, obtain a plurality of sub-pictures corresponding to the verification code background picture, a first mosaic rule, and a second mosaic rule, the verification code background picture includes the sub-pictures respectively Corresponding to a plurality of vacant areas, the first mosaic rule includes: the plurality of sub-pictures, a plurality of randomly generated rotation angles and a configuration relationship between the plurality of vacant areas, and the second mosaic rule includes : a ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com