Safety verification method and device
A security verification and verification code technology, which is applied in the field of security verification methods and devices, can solve the problems of reducing data processing speed, user interference, and lower recognition rate, so as to achieve the effect of improving security and reducing cracking rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
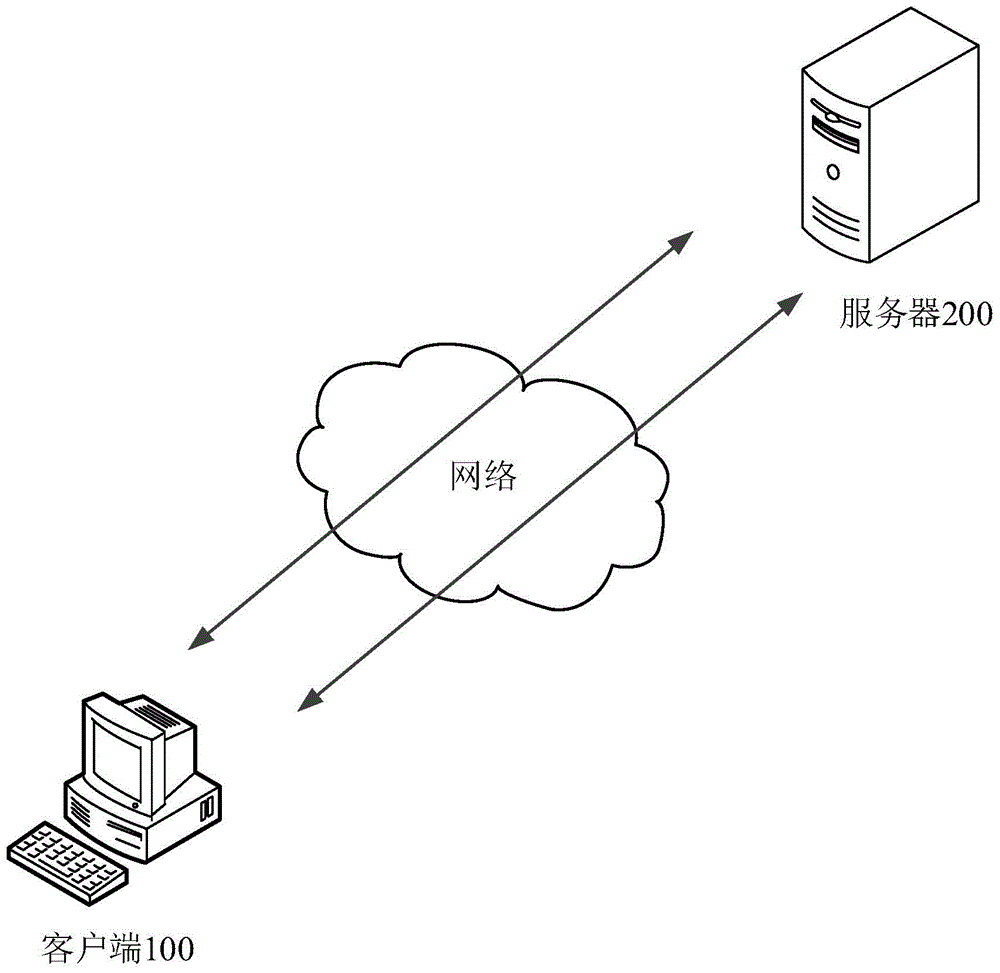
[0034] see Figure 4 , Figure 4 It is a flow chart of the security verification method provided by the first embodiment of the present invention. This example can be applied to figure 1 shown in the application environment, by figure 1 The server 200 shown implements a security verification method. like Figure 4 As shown, the security verification method provided in this embodiment includes:
[0035] Step S101, receiving the request to pull the verification code, obtaining the original picture used to generate the collage verification code, processing the color of the original picture into a first picture generated by preset colors, and a plurality of pictures cut from the original picture second picture;
[0036] The server 200 receives the request sent by the client 100 to pull the verification code, and the verification code can be used to perform security verification on the user of the client 100 .
[0037] In this embodiment, the original picture is a picture pr...
no. 2 example
[0051] see Image 6 , Image 6 It is a flow chart of the security verification method provided by the second embodiment of the present invention. This example can be applied to figure 1 shown in the application environment, by figure 1 The server 200 shown implements a security verification method. like Image 6 As shown, the security verification method provided in this embodiment includes:
[0052] Step S201, acquiring the original picture and the processing rules of the original picture;
[0053] In this embodiment, different types of original pictures may correspond to different types of processing rules. Specifically, the type of the original picture can be classified according to any one or more of several factors including, but not limited to, color block, color, hue, and the number of pixels contained in the original picture. For example: classification can be based on the color contrast of the original image. Because if the color contrast in the original pictu...
no. 3 example
[0077] see Figure 7 , Figure 7 It is a flow chart of the security verification method provided by the third embodiment of the present invention. This embodiment can be applied to figure 1 In the security verification system shown, by figure 1 The server 200 shown implements a security verification method. like Figure 7 As shown, the security verification method provided in this embodiment includes:
[0078] Step S301, acquiring the original picture and the processing rules of the original picture;
[0079] Step S302, determining the type of the original picture and the processing rule of the original picture corresponding to the type;
[0080] Step S303, according to the processing rule, process the color of the original picture into a preset color as the first picture, and cut out a plurality of small block pictures from the original picture as the second picture;
[0081] Step S304, storing the first picture, the second picture, and the position parameters of the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com