Method for repairing P table of Seagate hard disk
A technology of hard disk and table data, applied in the field of information security, can solve the problems of hard disk identification, compiler abnormality, and unsuccessful compiler recovery, etc., to shorten the time, reduce the probability of errors, and improve the success rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] In order to make the object, technical solution and advantages of the present invention clearer, the following examples are given to further describe the present invention in detail.
[0021] S101: read the system file corresponding to the P table through the serial port, and the P table is in the position corresponding to the head 0 of the hard disk, the volume 3, and the file descriptor;
[0022] S102: Analyzing the effective data body of the P list, and distinguishing abnormal entries;
[0023] S103: Clear all abnormal entries;
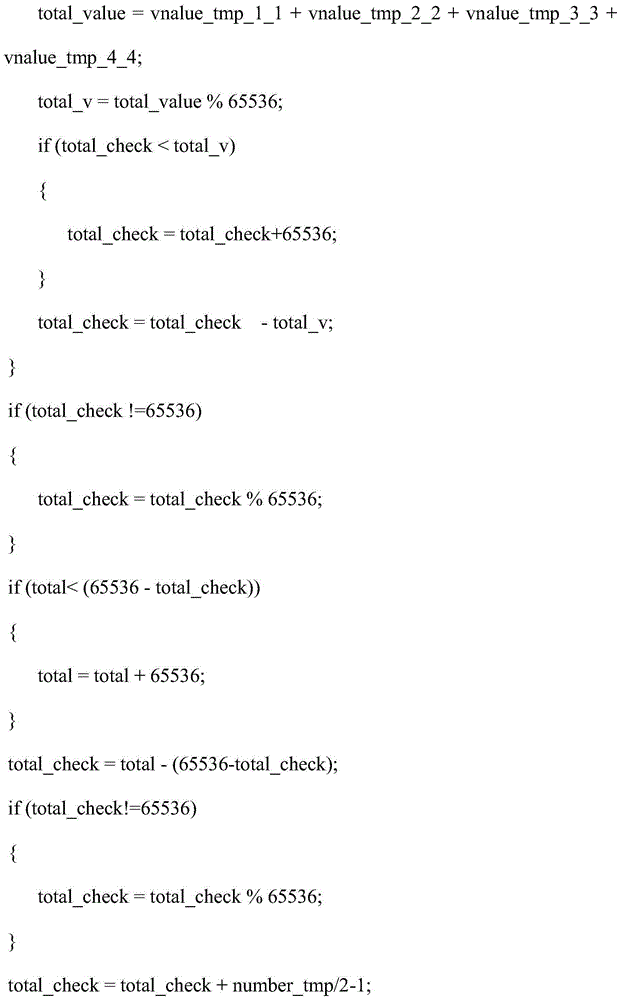
[0024] S104: Starting from the offset position of the effective data body in the P table, take 14 bytes as a group, first sum the two groups of bytes, and then calculate the modulus; loop until the end of the effective data body in the P table, and calculate the The result is written to the last 2 bytes of the P list to overwrite;
[0025] The specific algorithm is as follows:
[0026]
[0027]
[0028] S105: rebuilding the compiler...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com