A method for real-time detection of cyberspace security situation
A security situation, real-time detection technology, applied in the field of information security, can solve the problems of reduced sequence randomness, inaccurate network behavior analysis, etc., to achieve the effect of high integration level, accurate situation assessment results, and comprehensive time scale.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] Below in conjunction with accompanying drawing, the present invention is described in further detail:
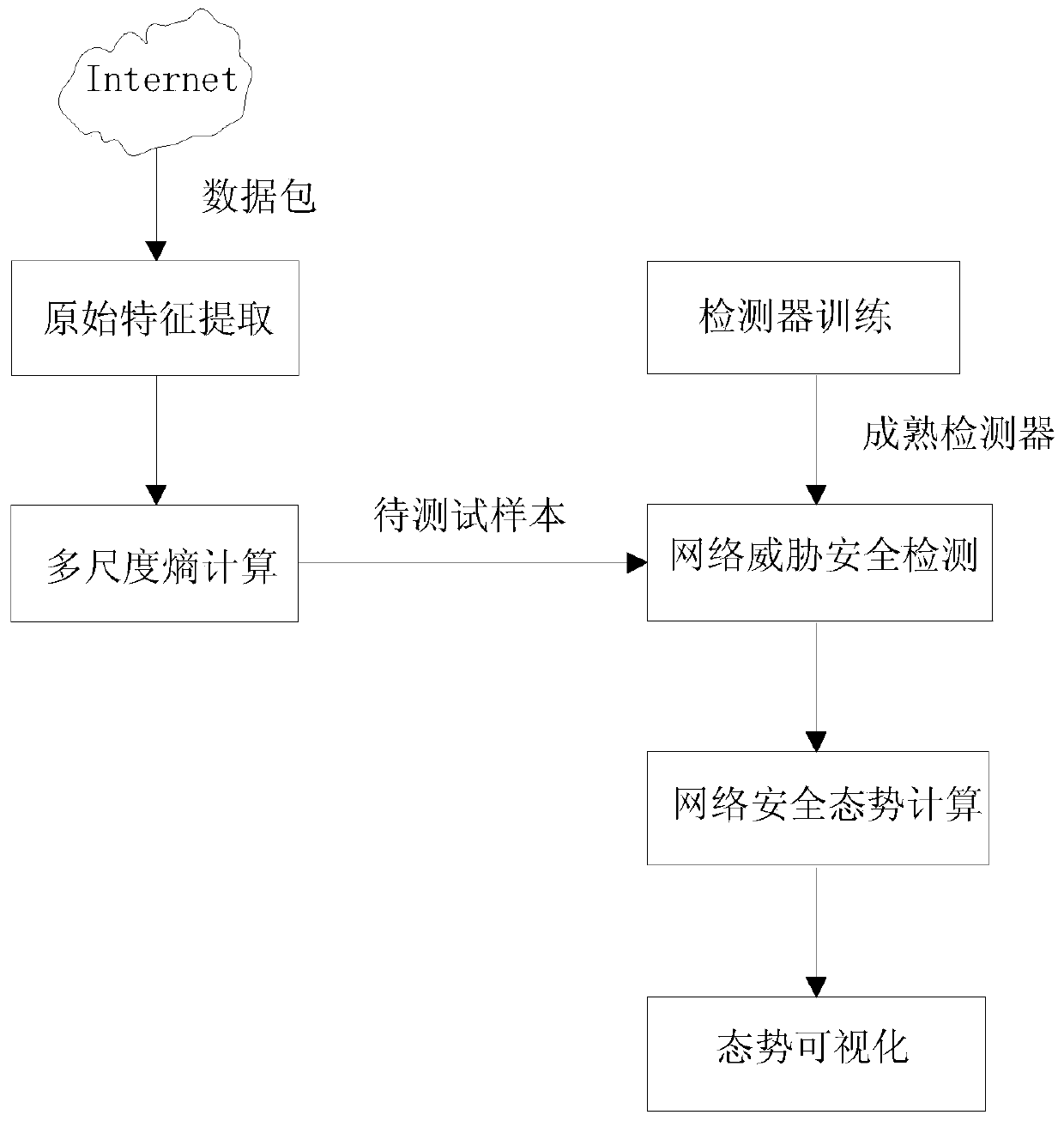
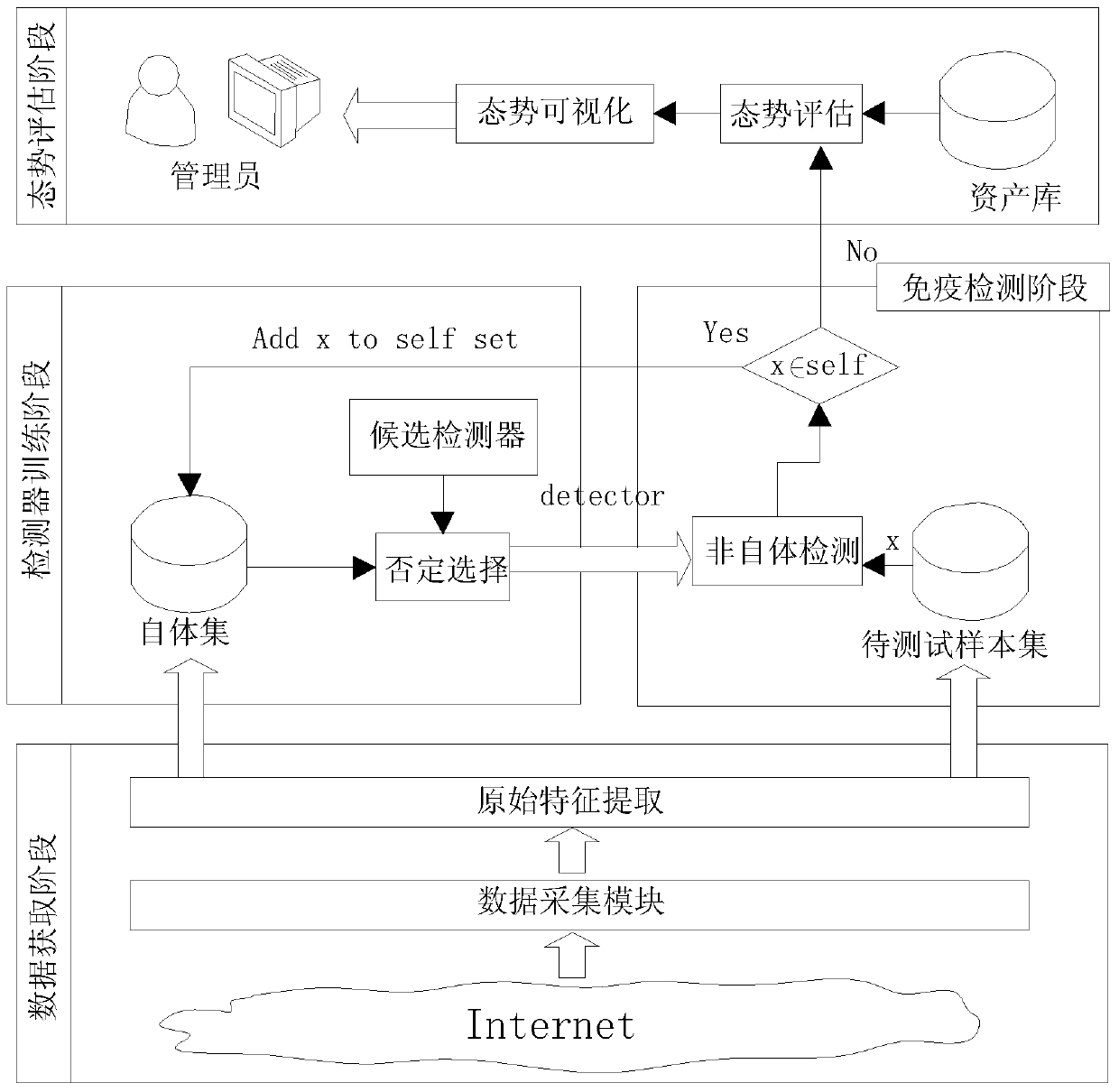
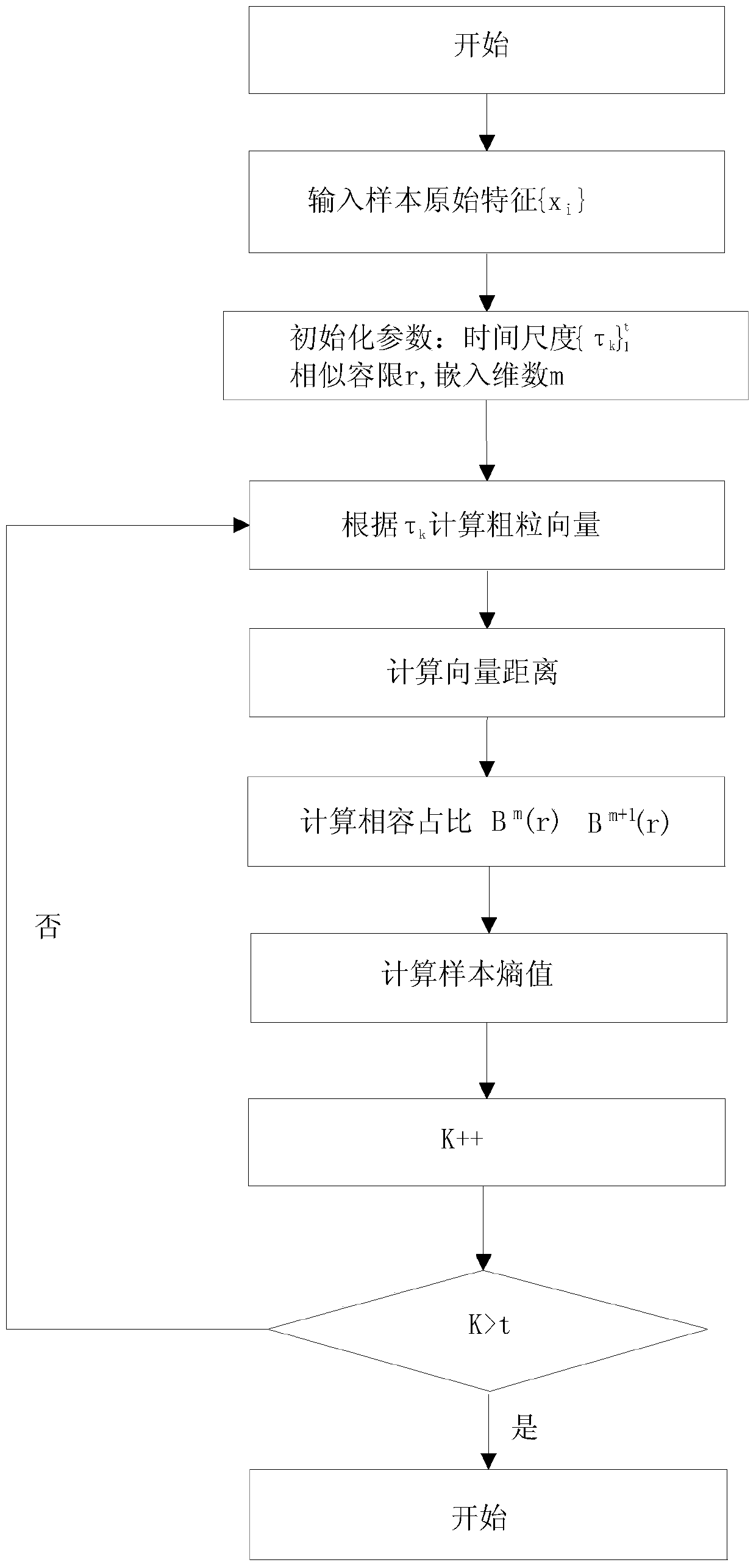
[0044] Such as figure 1 As shown, the present invention proposes a network security situation assessment method based on artificial immunity and multi-scale entropy, which includes six parts: original feature extraction, multi-scale entropy calculation, detector training, network threat security detection, network security Situational computing and situational visualization. Among them, the original feature extraction is to obtain the original network packet features from the network through the data collection module, which is used for the subsequent multi-scale entropy calculation and network anomaly detection process; the multi-scale entropy calculation is to perform multi-scale entropy on the extracted network features. Calculation, calculate the sample entropy of the original data packet feature sequence at different time scales, and obtain the entropy feature v...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com