Router with hardware encryption and decryption function and encryption and decryption method of router
An encryption method and router technology, applied in the field of network security, can solve problems such as slow software implementation speed, taking up more host resources, and program running is easy to be tracked
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
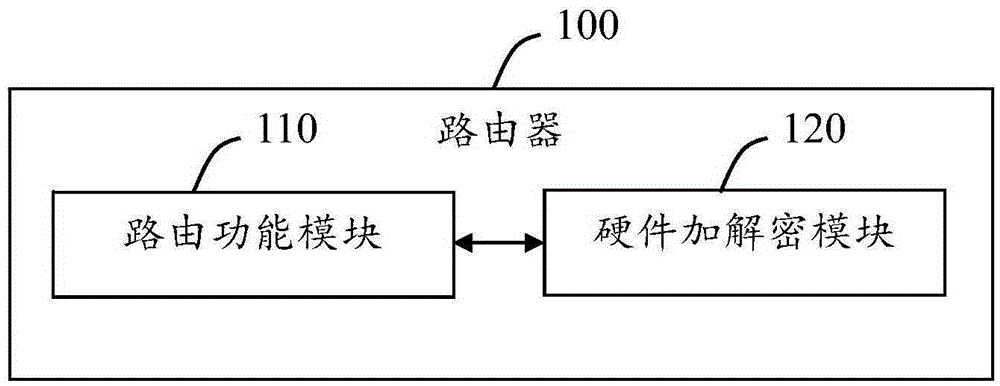
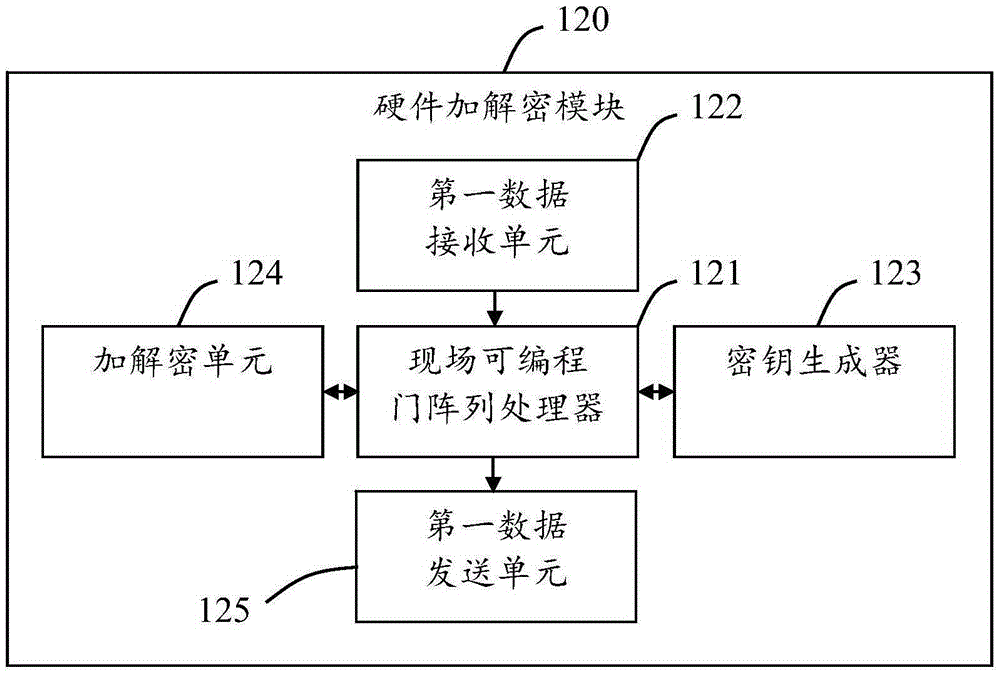
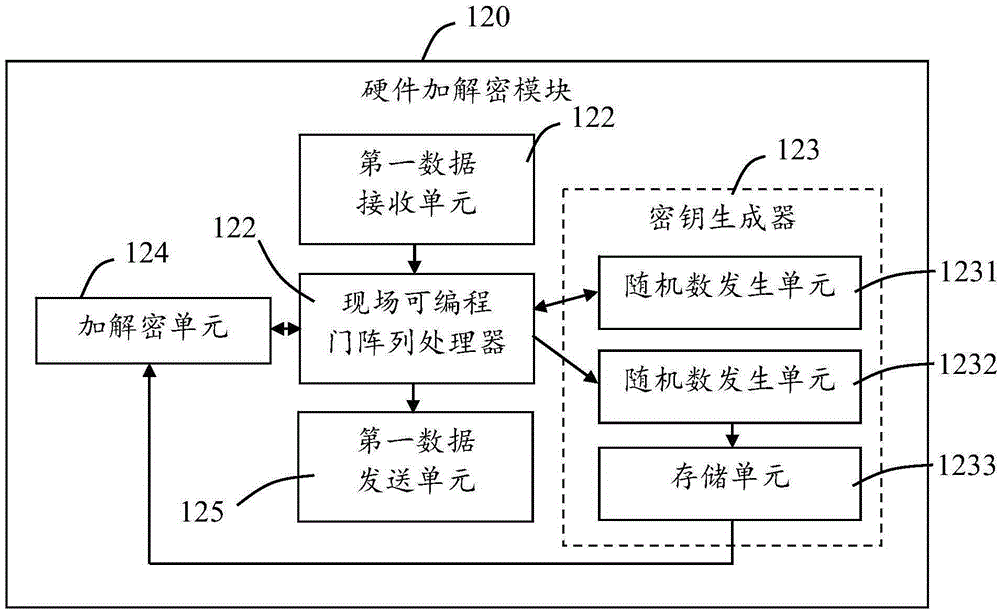
[0109] Such as figure 1 Shown is a schematic structural diagram of the first embodiment of the router 100 with hardware encryption and decryption functions provided by the present invention. It can be seen from the figure that the router 100 includes interconnected routing function modules 110 and FPGA-based hardware Encryption and decryption module 120. In the course of work, first, the routing function module 110 receives from the outside the plaintext that needs to be encrypted or receives the ciphertext that needs to be decrypted; then, the routing function module 110 sends the received plaintext or ciphertext to the hardware encryption and decryption module 120; When the hardware encryption and decryption module 120 receives the plaintext or ciphertext sent by the routing function module 110, it is encrypted or decrypted immediately, and the encrypted data or decrypted data produced are sent to the routing function module 110; finally, the routing function module 110 sen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com