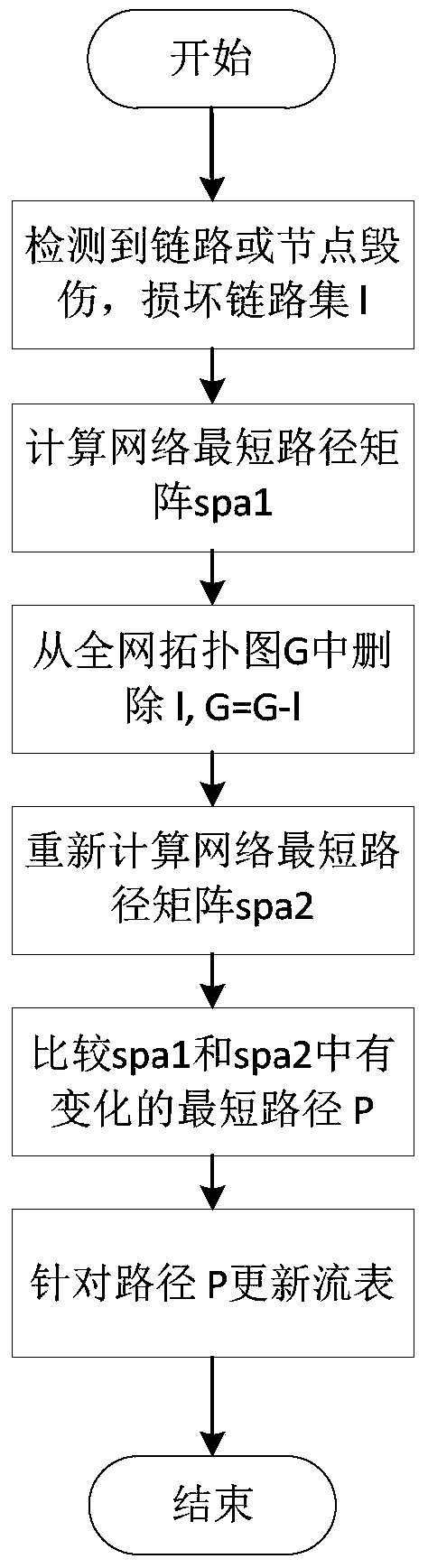
A method for building a software-defined indestructible network
A network construction and software-defined technology, applied in data exchange networks, electrical components, digital transmission systems, etc., can solve the problems that topology adjustment can only be carried out locally, the impact cannot be obtained quickly and accurately, and the operation of core important services cannot be guaranteed. Guaranteeing the transmission of important core business traffic and the effect of strong timeliness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0081] The effect of the present invention can be further illustrated by the following simulation experiments.
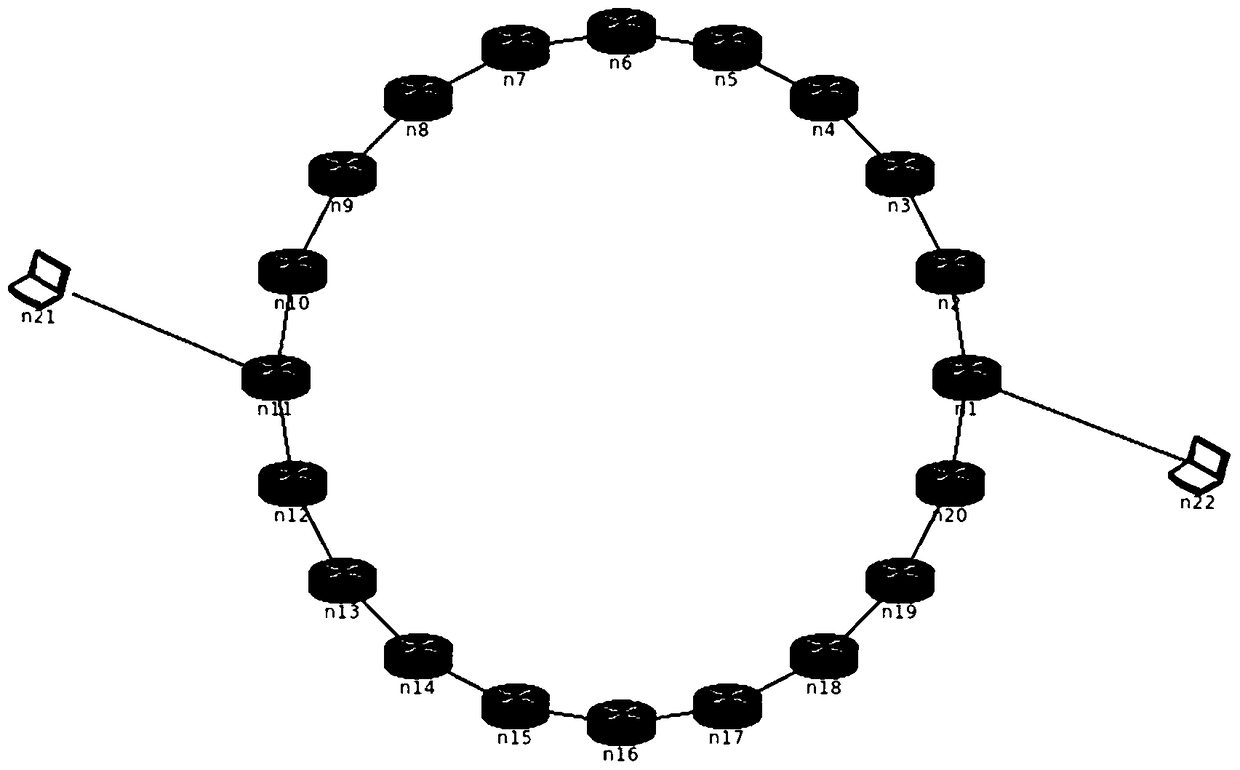
[0082] In order to verify the survivability performance of the invulnerability network, two topologies were selected, one is a ring topology and the other is a mesh topology, such as image 3 with Figure 4 Shown. The ring topology ensures that there are two paths between any two nodes, and there are more than two paths between any two points in the grid topology, and the correctness of the anti-destroy recovery algorithm can be checked.
[0083] Both topologies are configured with two network terminals, one running iperf client and the other running iperf server, you can observe the path through which the traffic flows. The UDP test uses a bandwidth of 1Mbps for testing, and checks the recovery time of the anti-destructive recovery algorithm by observing the packet loss at the UDP receiving end. During the TCP test, the client and server will negotiate the transmission...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com