A method for securely storing the root key required for encryption and authentication in flash
An encryption authentication and secure storage technology, which is applied in the field of root keys required for FLASH secure storage encryption authentication, and can solve problems such as inability to calculate and process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
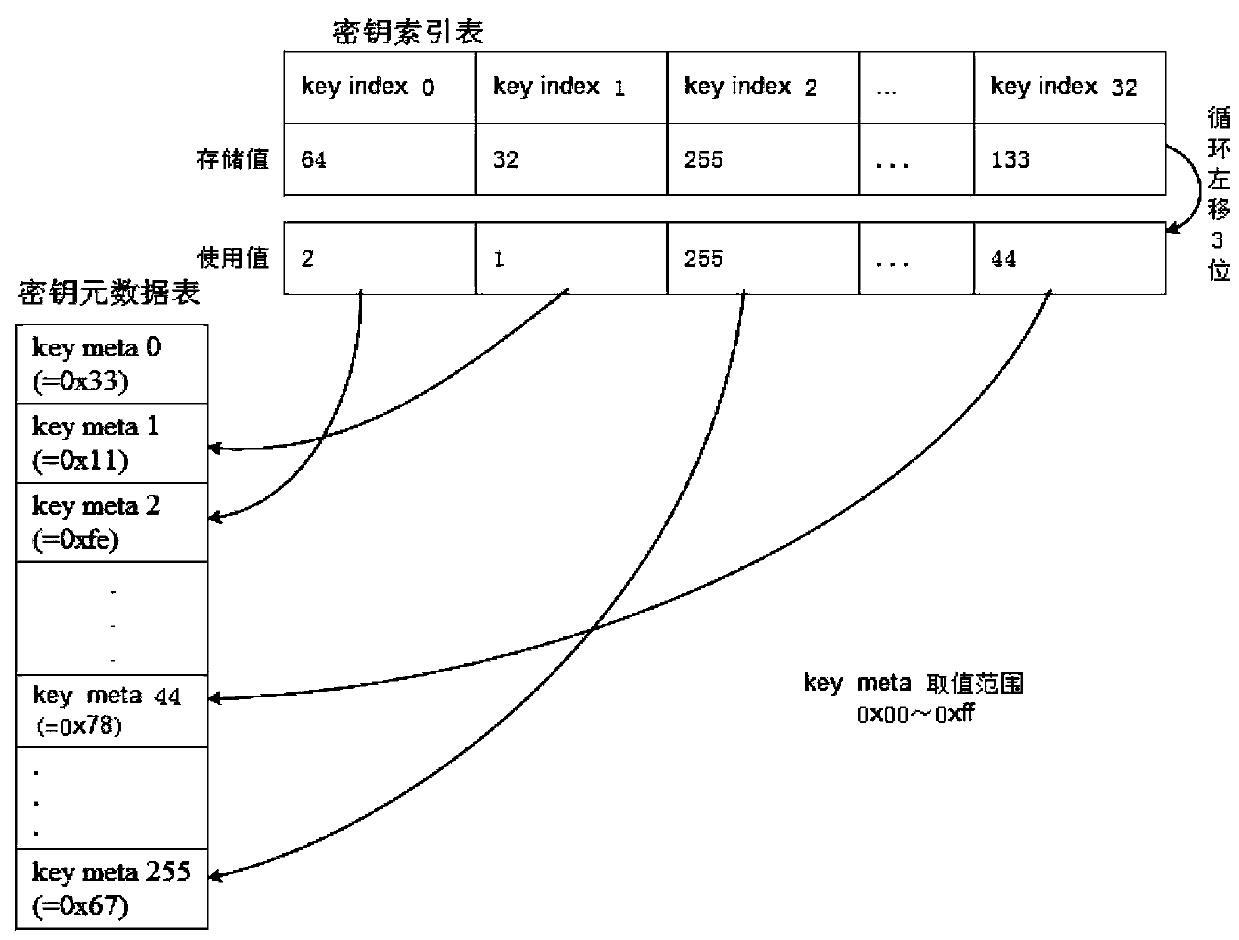
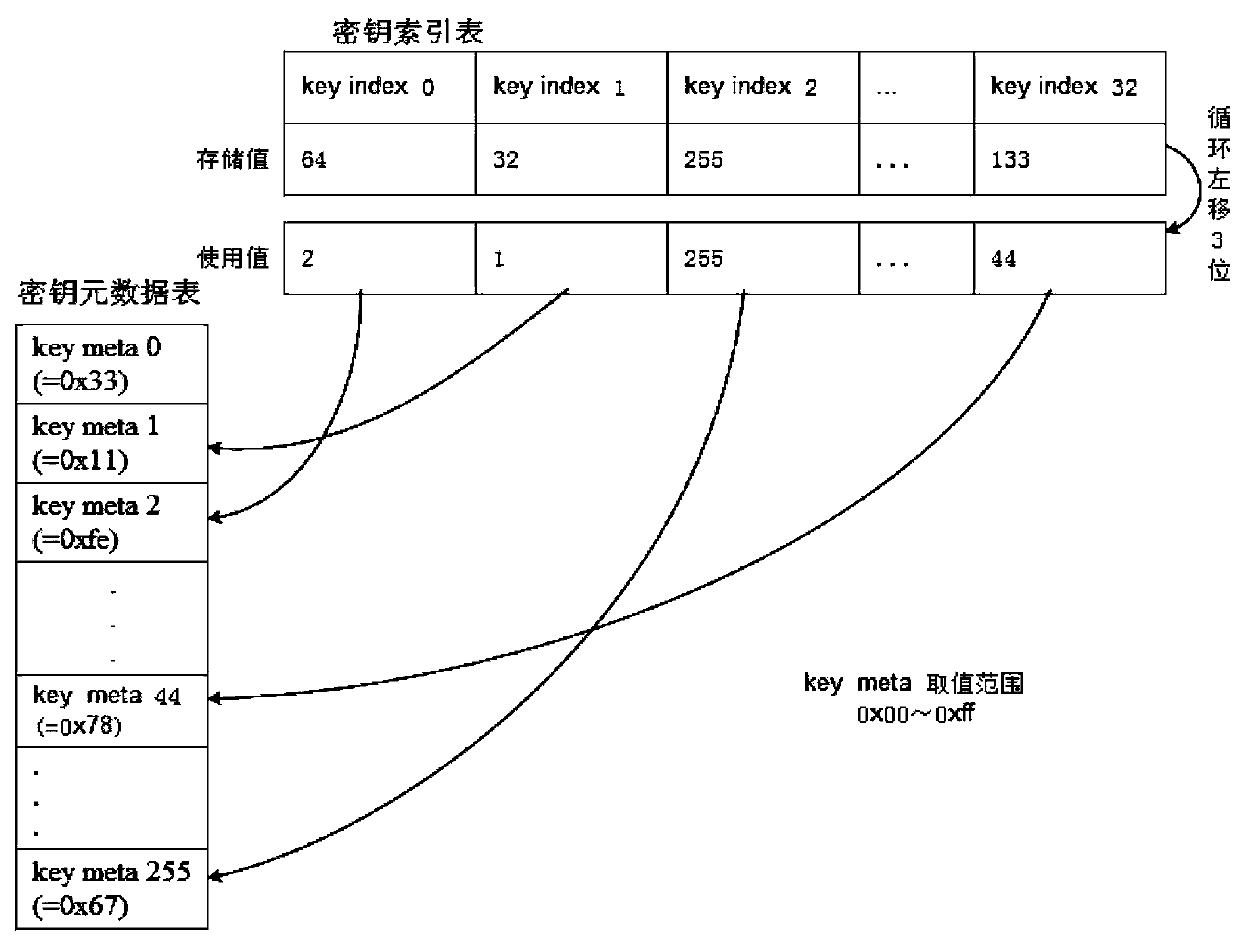
[0018] Such as figure 1 Shown, a kind of method of root key required for encryption authentication in FLASH security storage of the present invention comprises the following steps:
[0019] Step 1. First create a key metadata table. The total length of the key metadata table is 256 bytes. The key metadata table is composed of 256 key metadata key meta, that is, each key metadata key meta The length is one byte, and the value of the key metadata key meta is a hexadecimal number, the value ranges from 0x00 to 0xff, and the value of the key metadata key meta in the key metadata table is unique , that is to say, any two key metadata keymeta values in the key metadata table will not be the same;
[0020] Step 2. In order to further ensure security, the key metadata table is not stored in one piece in the FLASH continuously. The key metadata table is divided into 16 groups, and each group consists of 16 consecutive key metadata key meta For example, key meta0~key meta15 is the f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com