Patents
Literature
43 results about "Application enablement" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
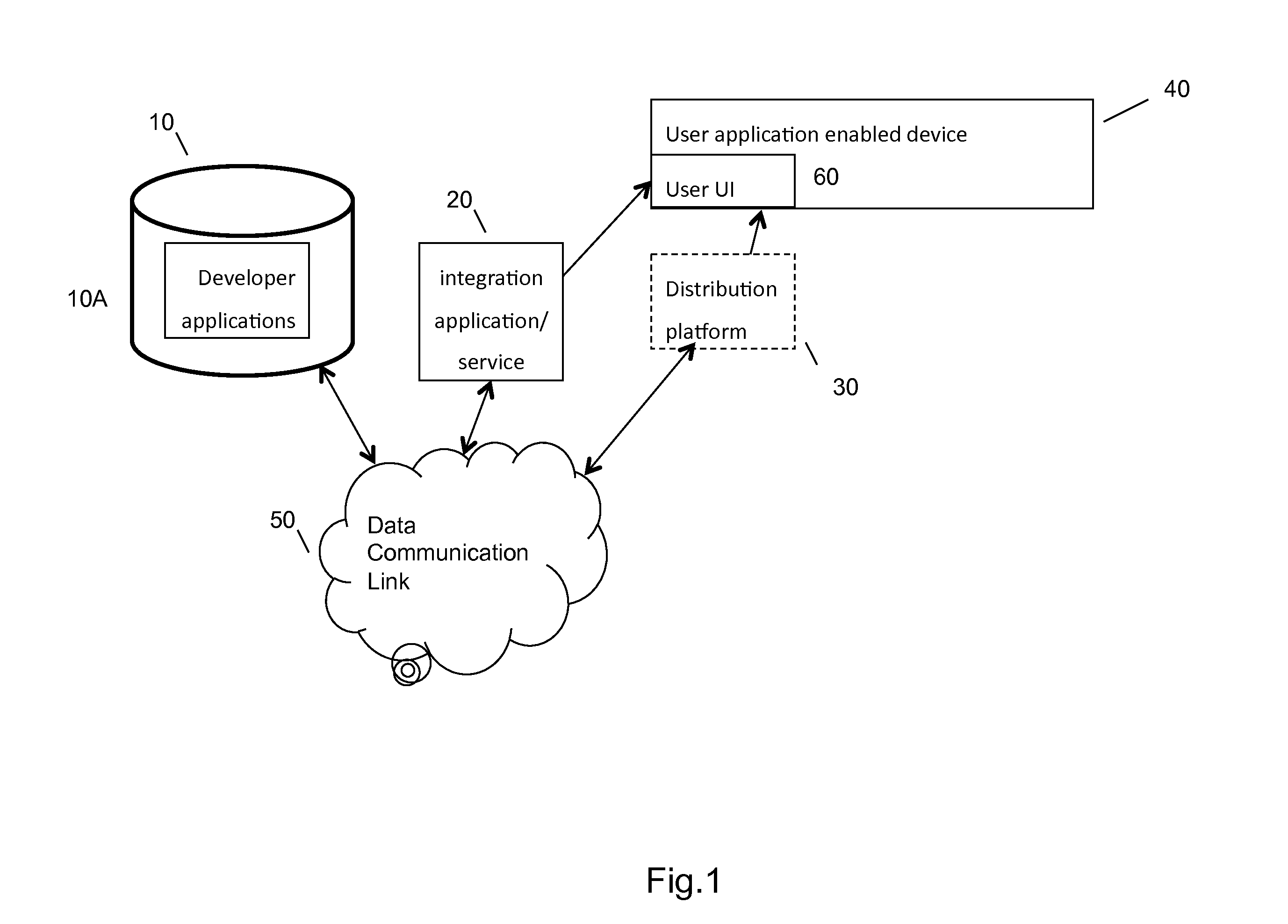
Application enablement is an approach which brings telecommunications network providers and developers together to combine their network and web abilities in creating and delivering high demand advanced services and new intelligent applications.
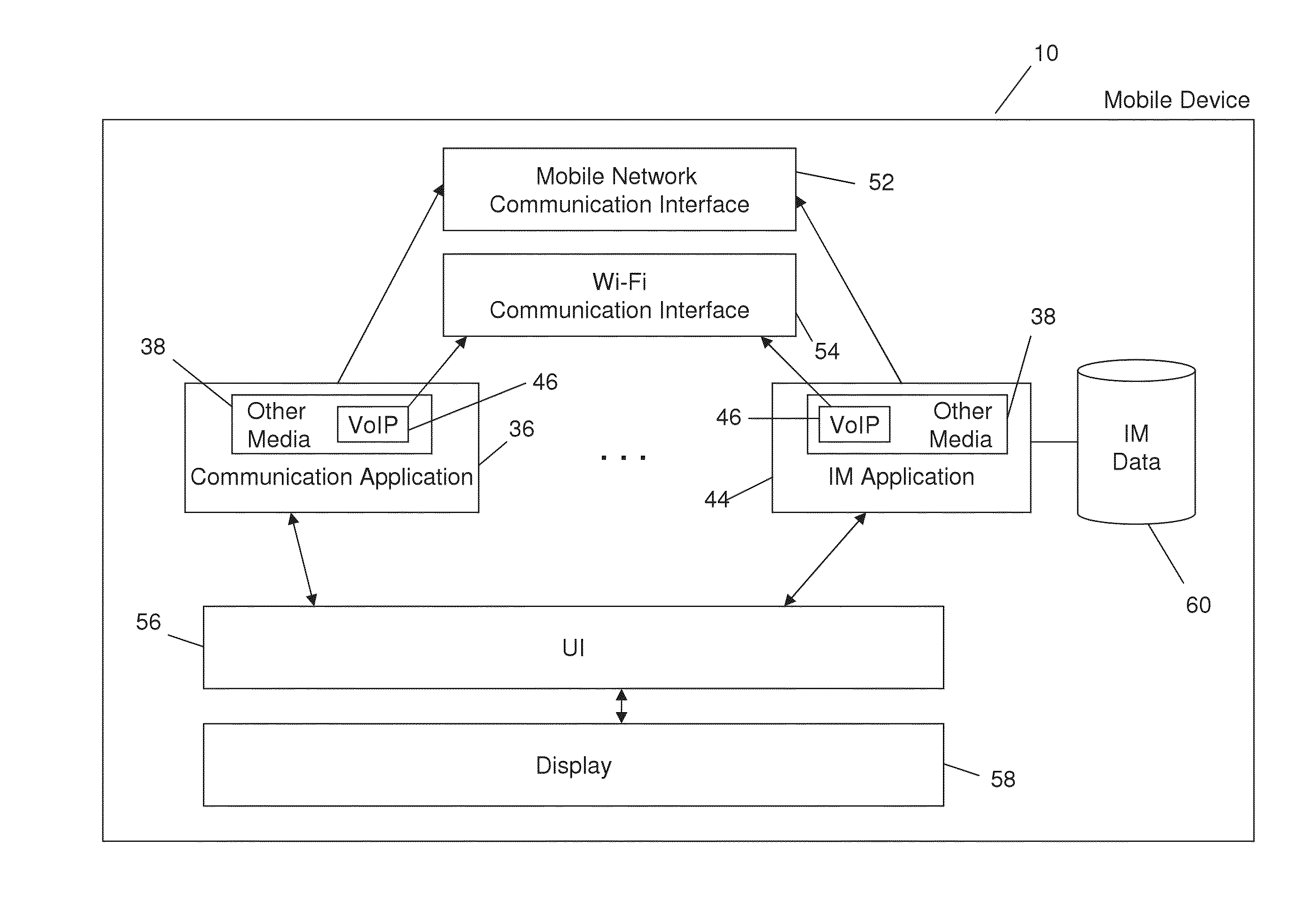
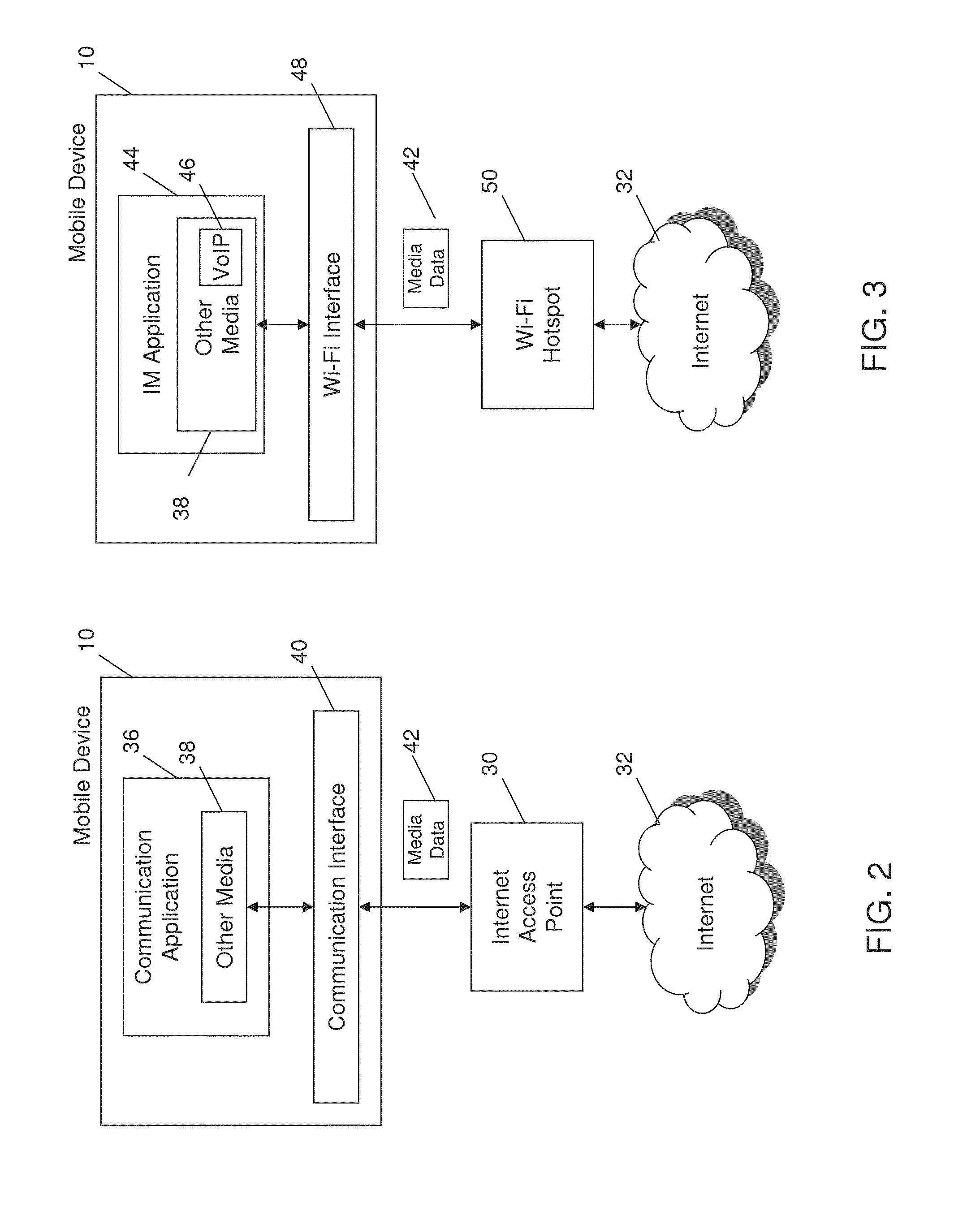
System and Method for Enabling Voice and Video Communications Using a Messaging Application
ActiveUS20130111365A1Multiple digital computer combinationsSubstation equipmentVoice communicationApplication enablement
A method and system are provided for enabling voice communications via a messaging application. The method comprises enabling an instant messaging (IM) presence status option to be selected; and blocking an incoming voice communication when the presence status option has been selected. A method and system are also provided comprising displaying a first instant message in an instant messaging conversation user interface comprising call status information; and displaying updated call status information in the instant messaging conversation user interface after determining whether an call attempt has been successful.
Owner:HUAWEI TECH CO LTD
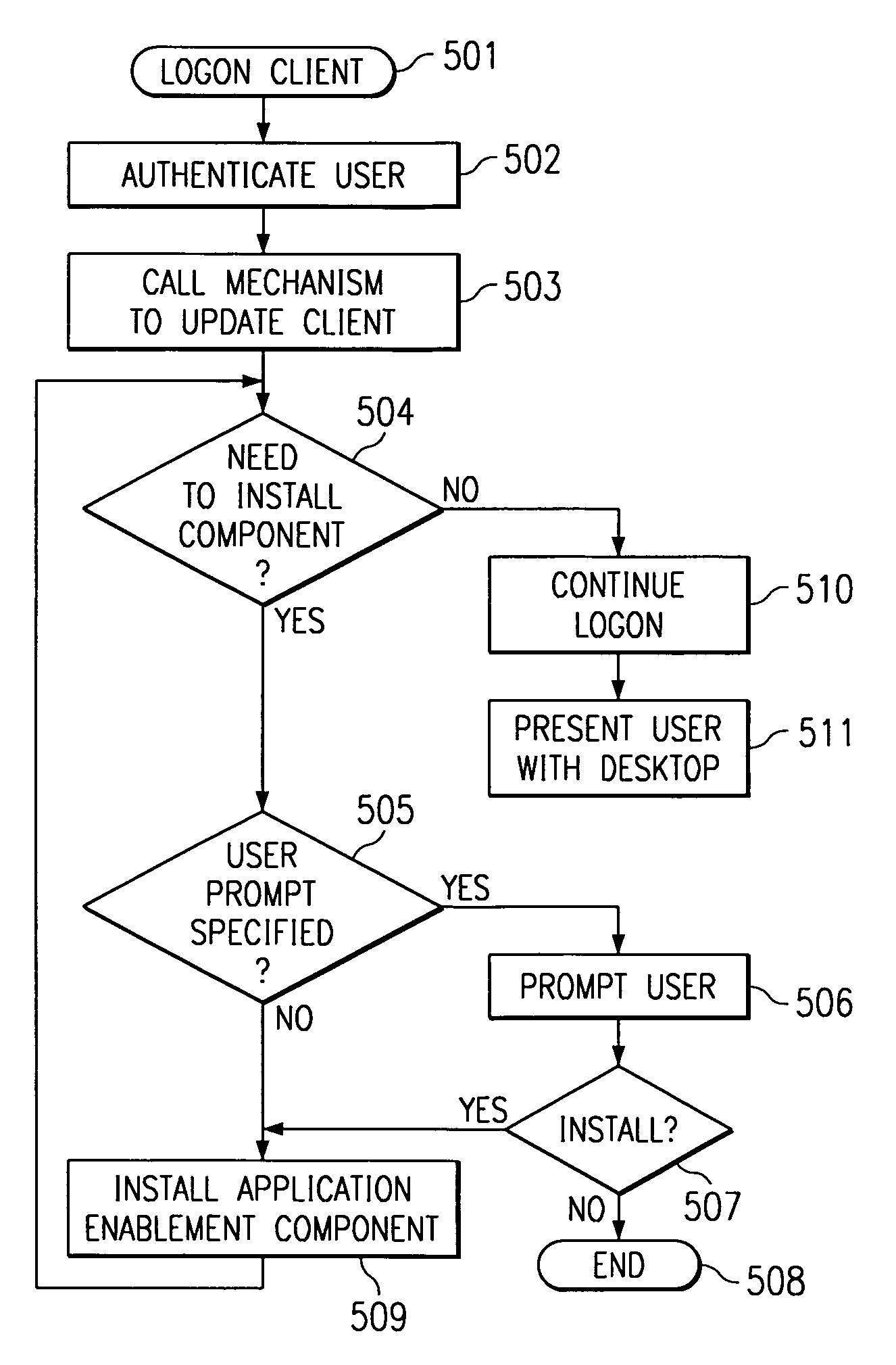
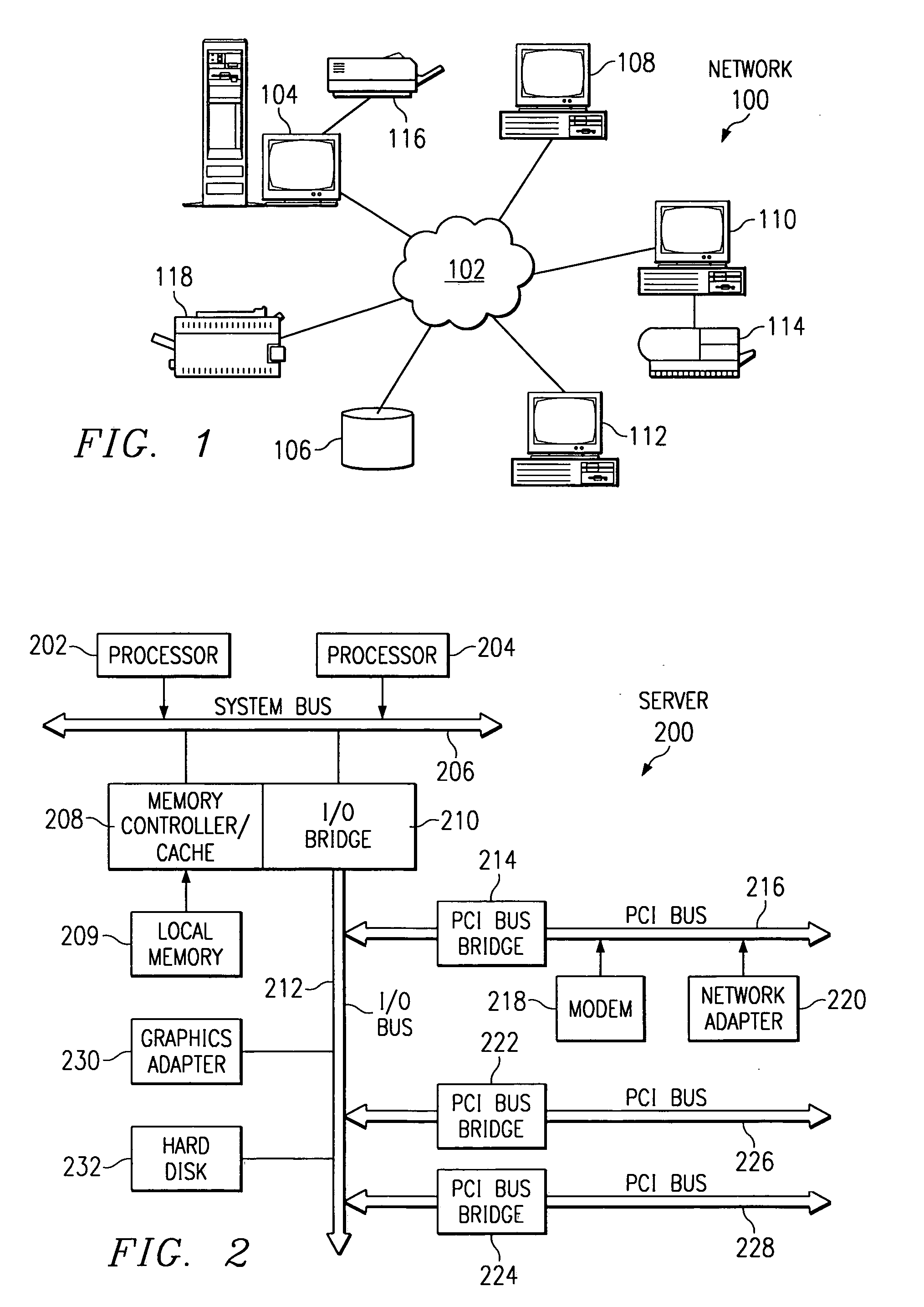
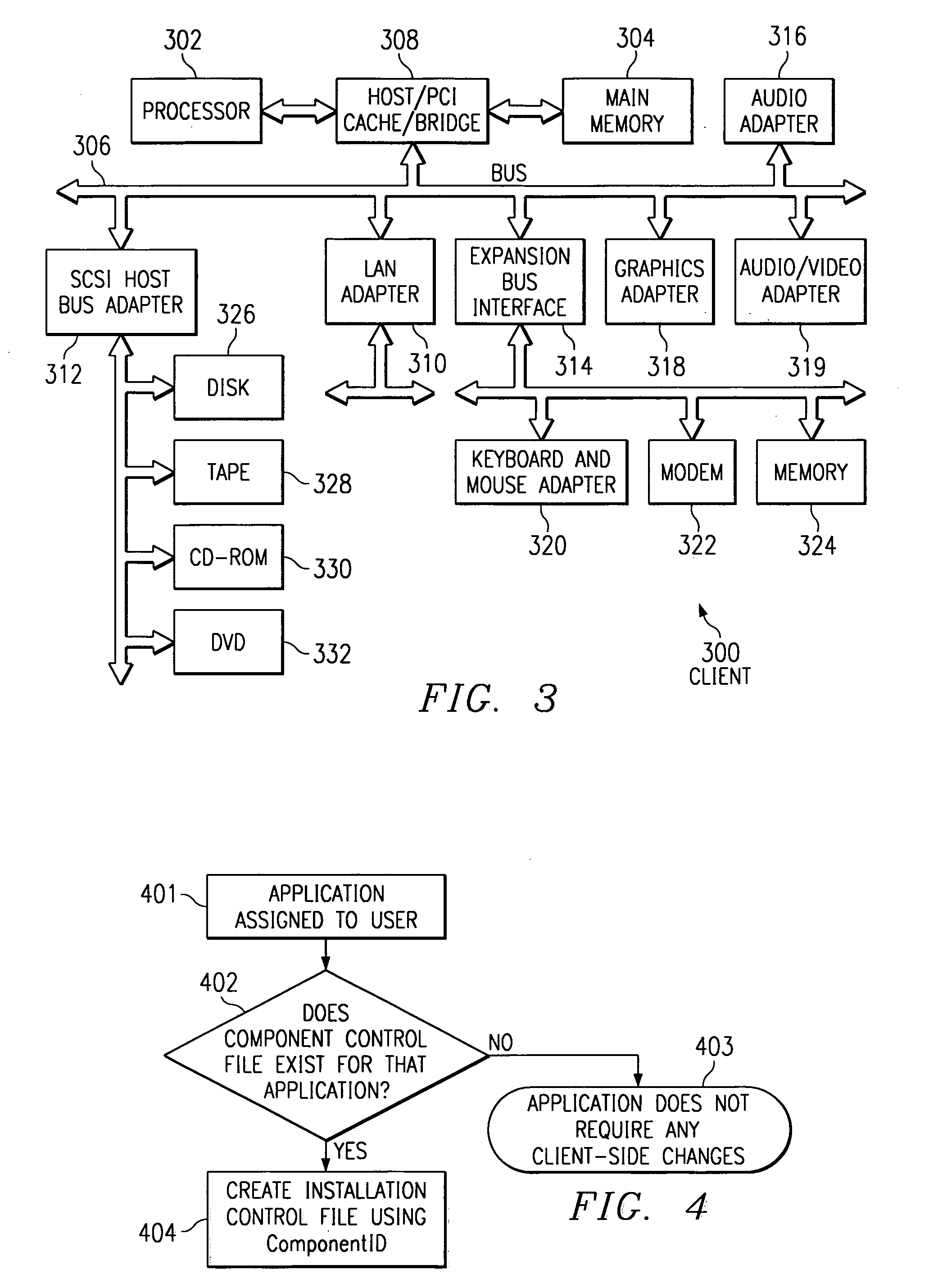
Mechanism to dynamically update a windows system with user specific application enablement support from a heterogeneous server environment
InactiveUS7024471B2Multiple digital computer combinationsProgram loading/initiatingOperational systemApplication software
A method, apparatus and program for updating client computers with user specific application enablement are provided. The invention involves creating a component control file on a network server, which defines the actions to be performed to install an enablement component needed to run an application on a client and creating an installation control file which contains a list of the enablement components needed to run the set of applications that have been assigned to a user. The enablement components are changes to the operating system's configuration. When a user logs onto a client computer, a mechanism in the client reads the user's installation control file from the server and then installs the necessary enablement components on the client operating system, if those components are not already installed. In one embodiment, the user receives a prompt before the components are installed, in case the user does not want to use the entire set of assigned applications.
Owner:IBM CORP
Application pod integration with automated mobile phone billing and distribution platform
InactiveUS20080040733A1Eliminate needSimple and automaticMetering/charging/biilling arrangementsAccounting/billing servicesApplication enablementUser interface
A platform for supporting a network-enabled application is configured to render the network enabled application for a user, via a user interface associated with the user, in accordance with various APIs included in the platform and used by a program developer to develop the network-enabled application. The rendering can included recognizing that the user interface is a mobile user interface and rendering the network-enabled application in a manner appropriate and / or optimal for the mobile user interface.
Owner:SMS AC INC
Policy controller application enablement api for wireline/wireless converged solution
InactiveUS20110202635A1Reduce the possibilityGood communication protocolDigital data processing detailsComputer security arrangementsComputer hardwareWeb browser
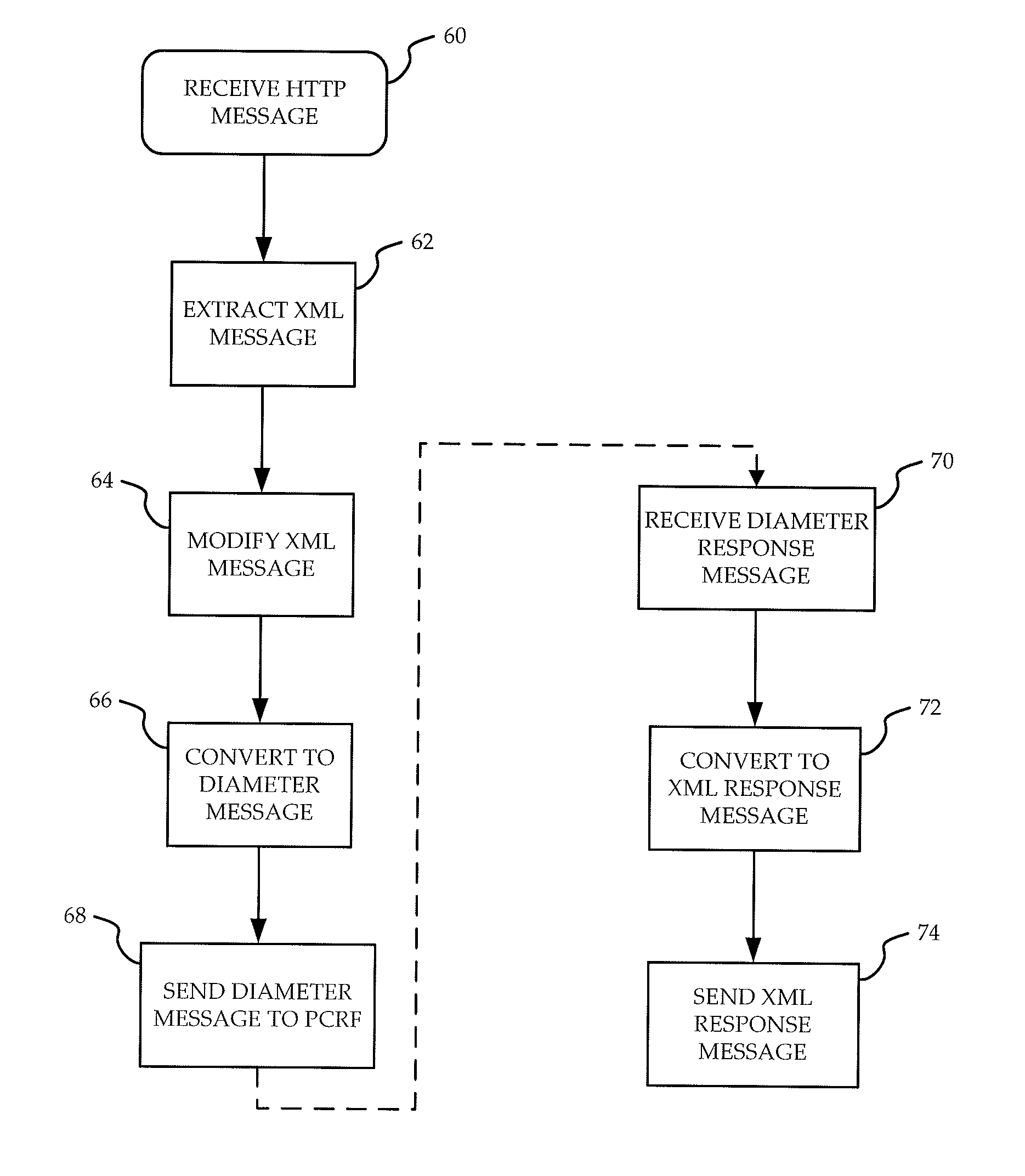
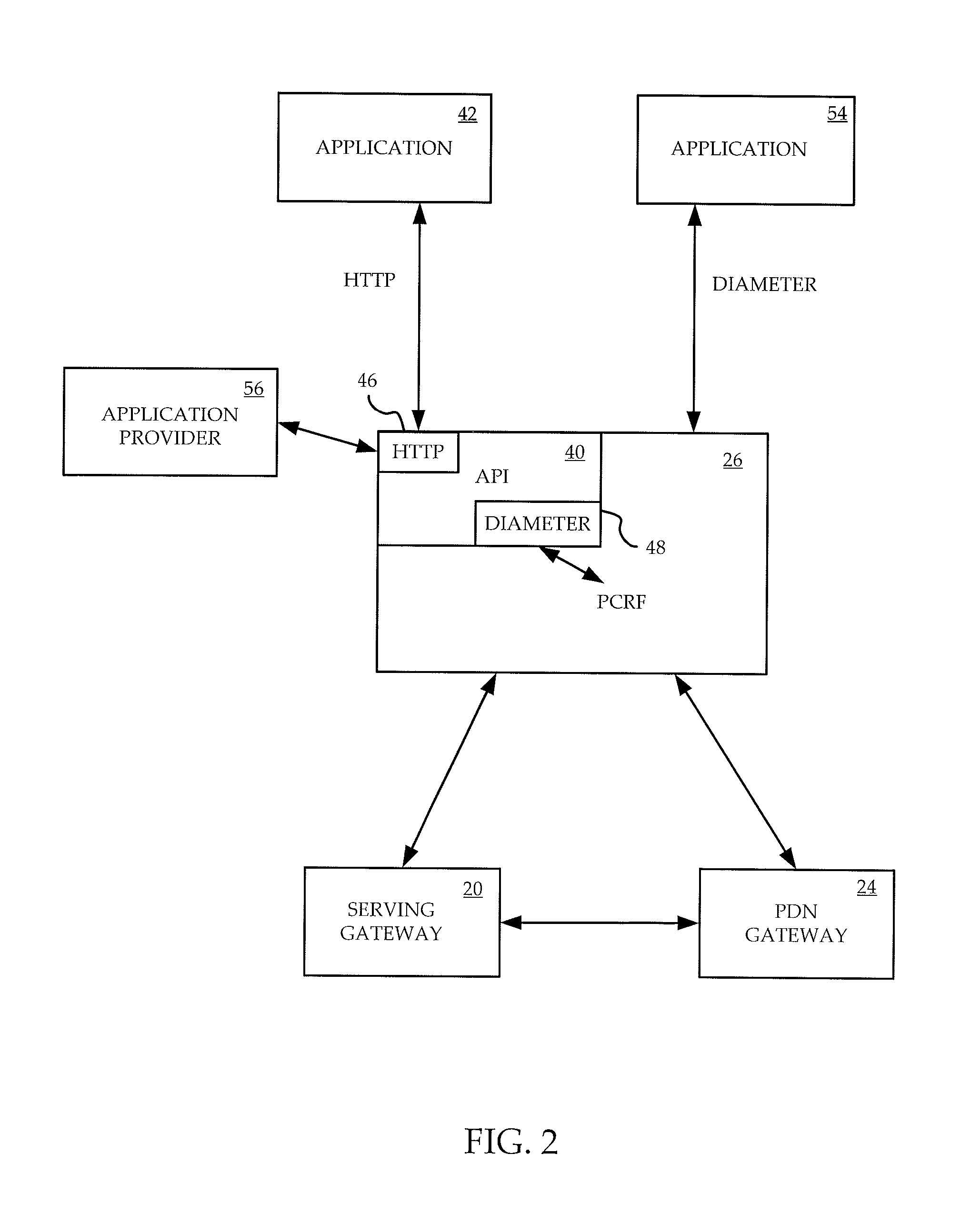
A method and apparatus are provided for allowing relatively simple interaction with a PCRF in an Evolved Packet Core. The PCRF includes an API, and instructions are sent by an application provider in an HTTP format to the API. The API translates these instructions into a diameter format so that they can be recognized by the PCRF. Response messages from the PCRF, in a diameter format, are sent to the API which translates these into a format recognized by the application provider's web browser.
Owner:ALCATEL LUCENT SAS
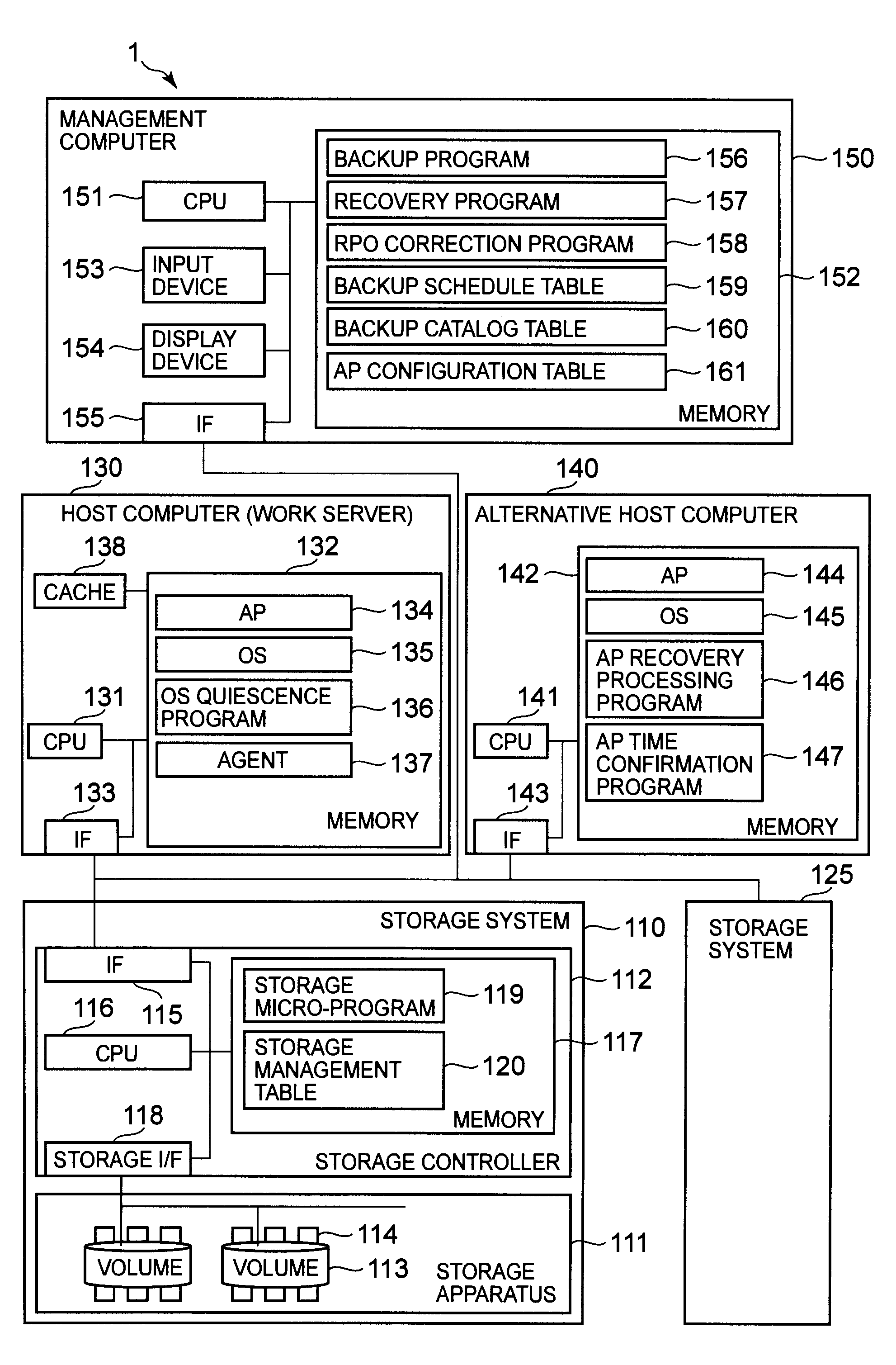
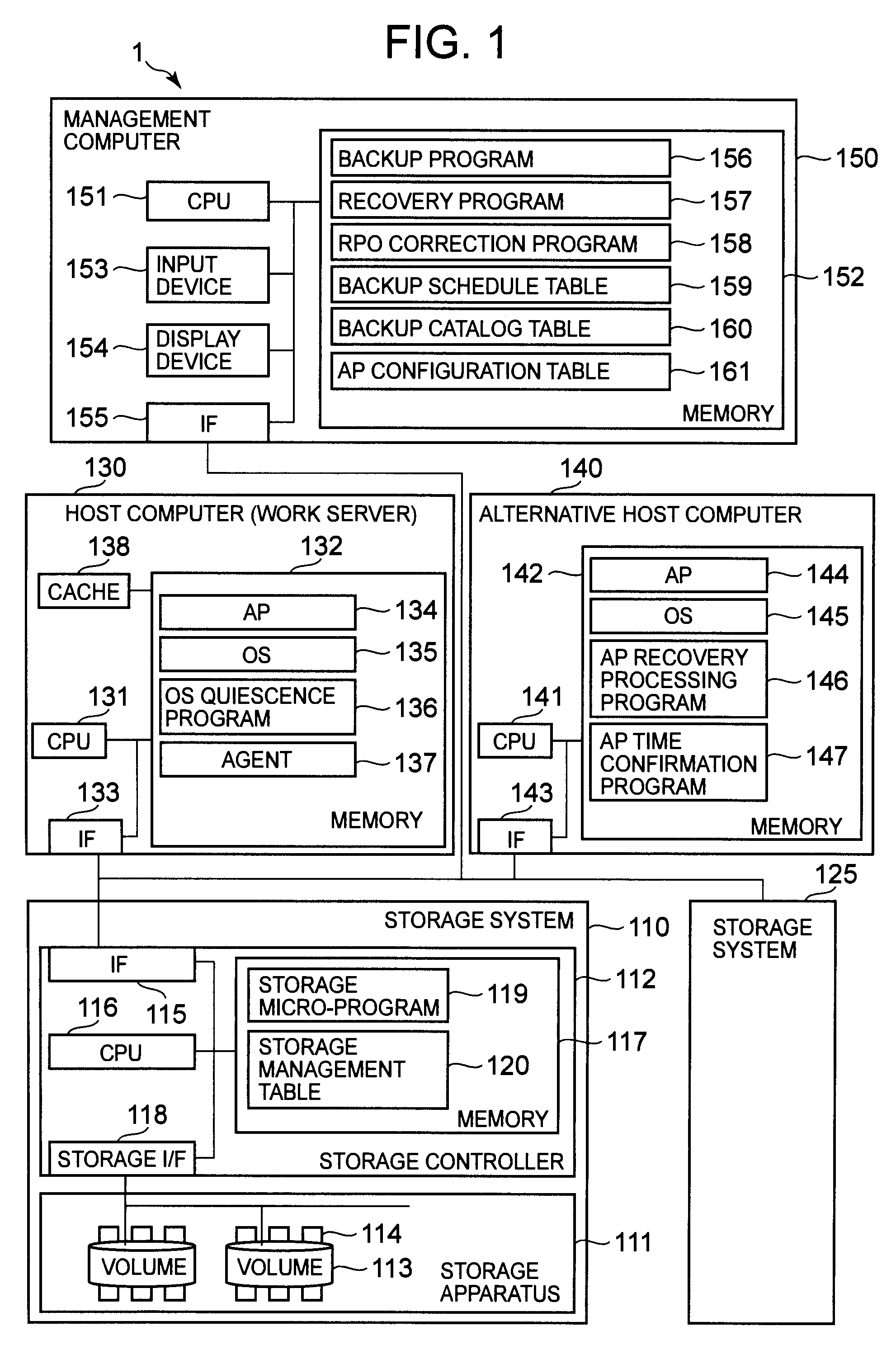
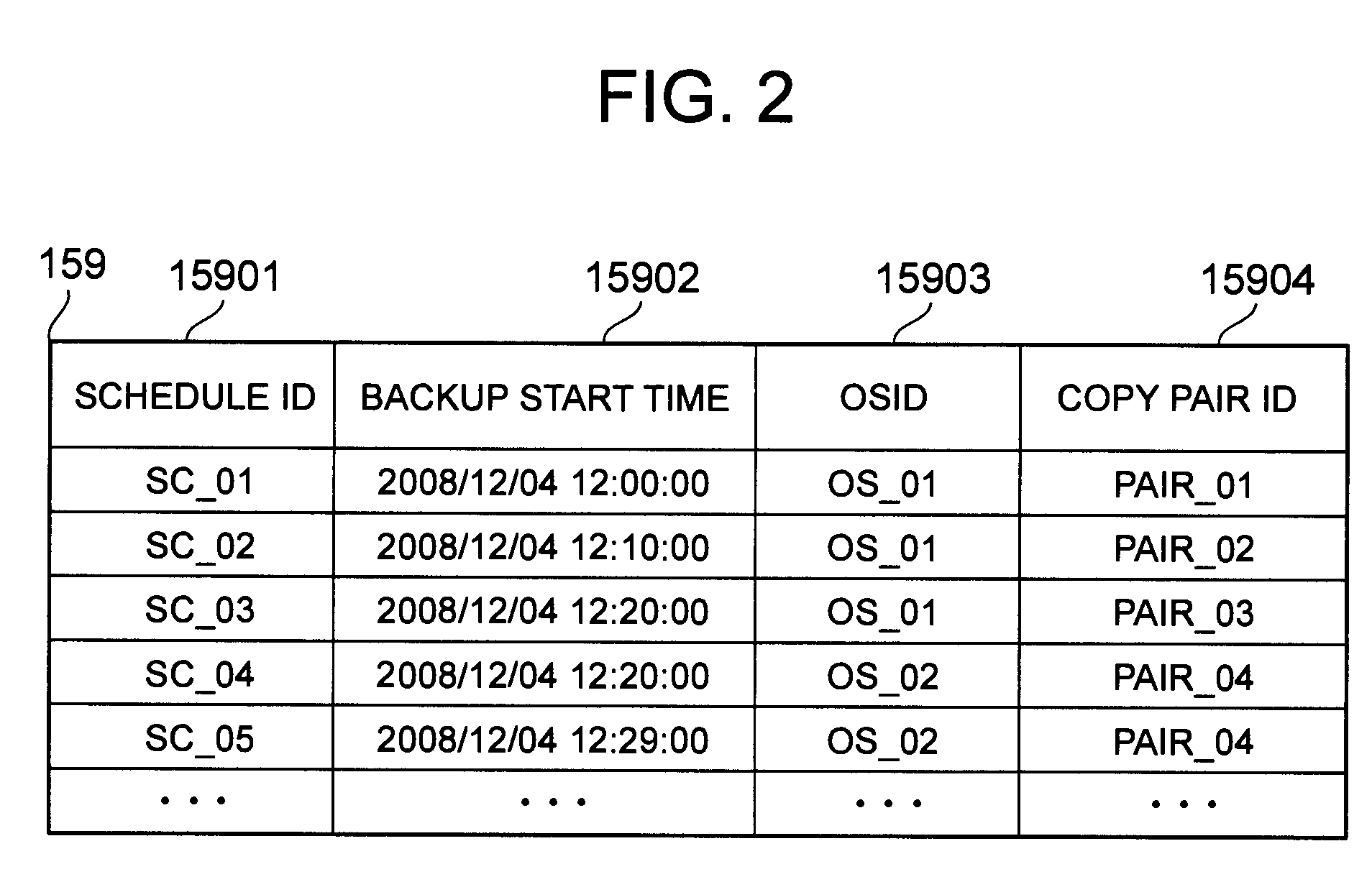
Backup method for storage system
ActiveUS20100274767A1Memory loss protectionDigital data processing detailsApplication enablementBackup
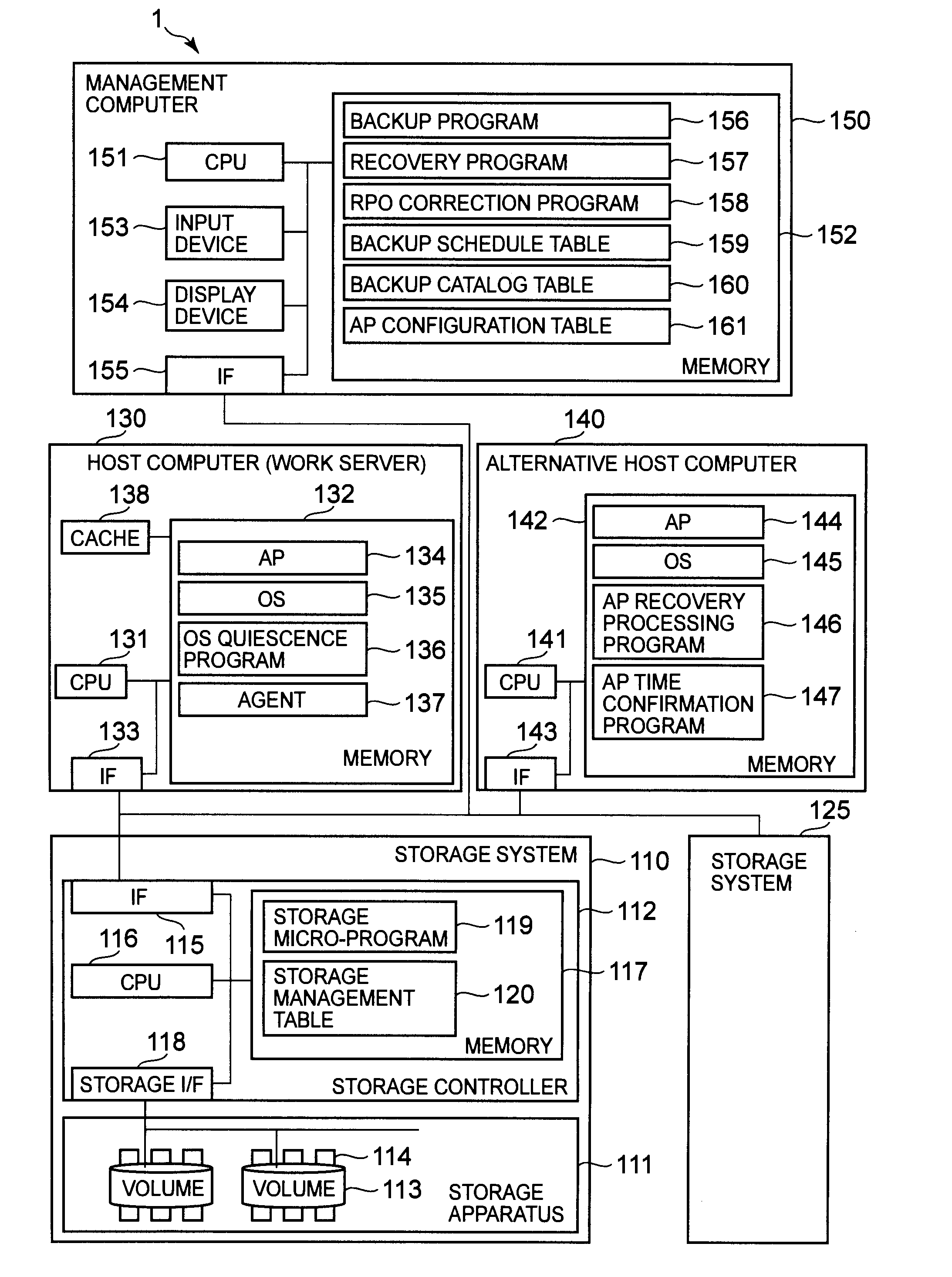
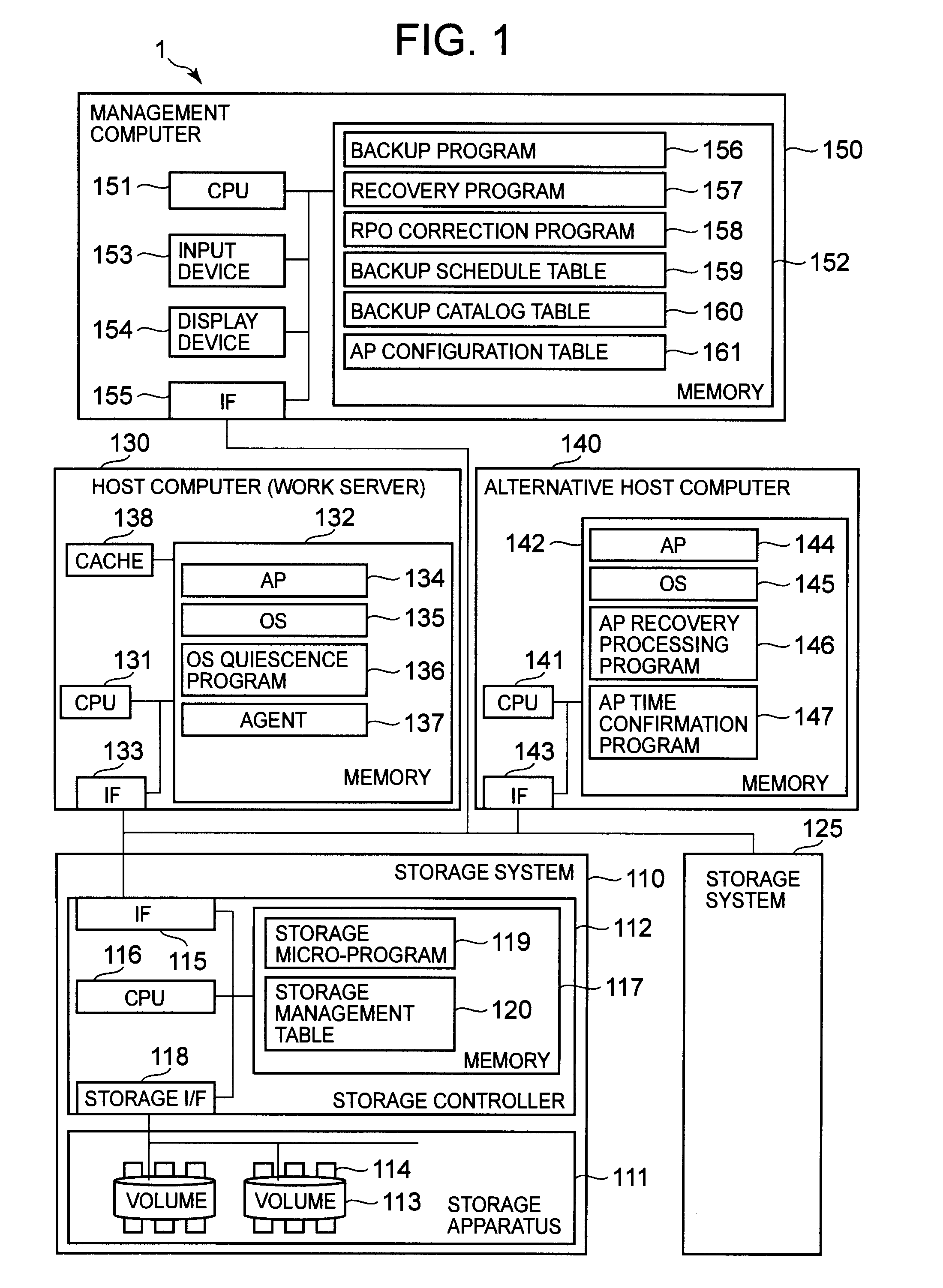
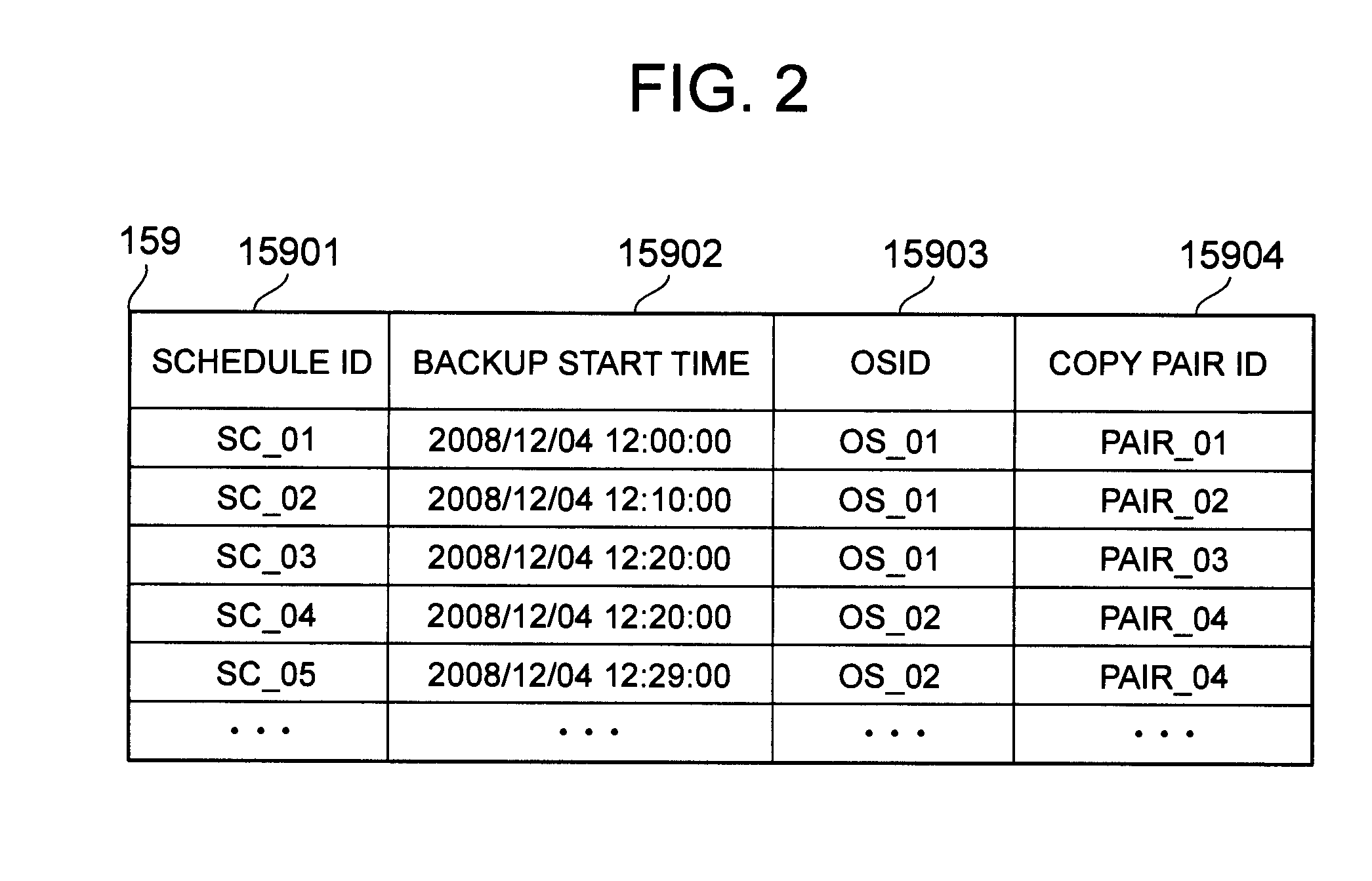
The present invention provides a backup method that makes it possible to specify the recovery-enabled time of an application even in a case where a backup has been performed without staticizing the application. In response to a first instruction from a management computer, a storage system backs up a first volume to a second volume at a first time while a first host computer continues to process an application. In response to a second instruction from the management computer, a second host computer reads out the data of the second volume and acquires a second time that is the time at which the application is recovery-enabled. The management computer stores the relationship between the backup and the second time in backup catalog information.
Owner:HITACHI LTD
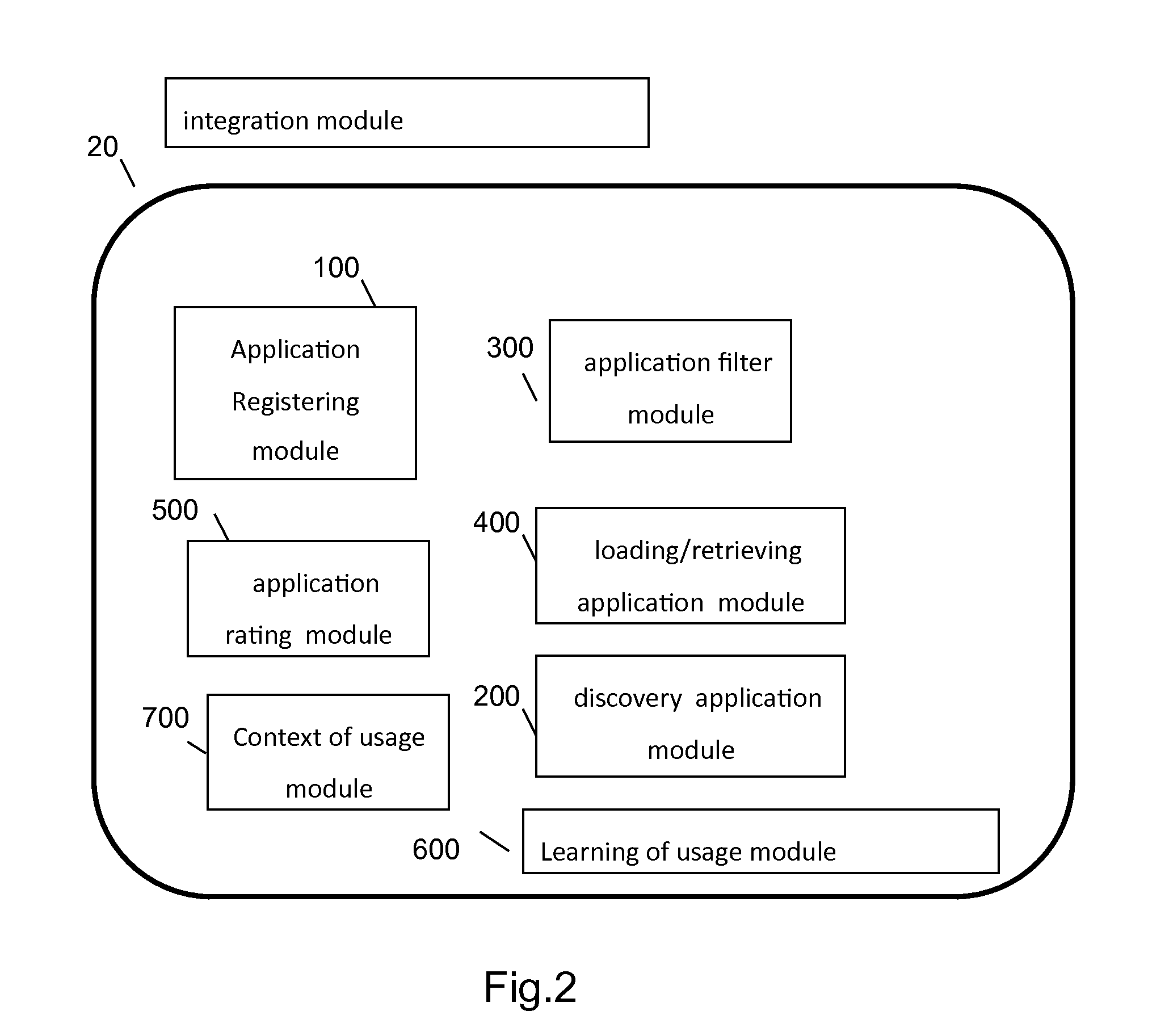
Method and system for discovering and activating an application in a computer device
InactiveUS20130283274A1Multiprogramming arrangementsMemory systemsSoftware engineeringApplication enablement
The present invention discloses a method for discovering and activating an application in a computer device. The method comprising the steps of: defining at least one application based on its functionality including at least one action which is enabled by the application, identifying a required action to be performed by the user and searching loading a relevant application for the identified action, wherein the process of defining and identifying are performed by at least one processor unit.
Owner:MIMRAN DAVID
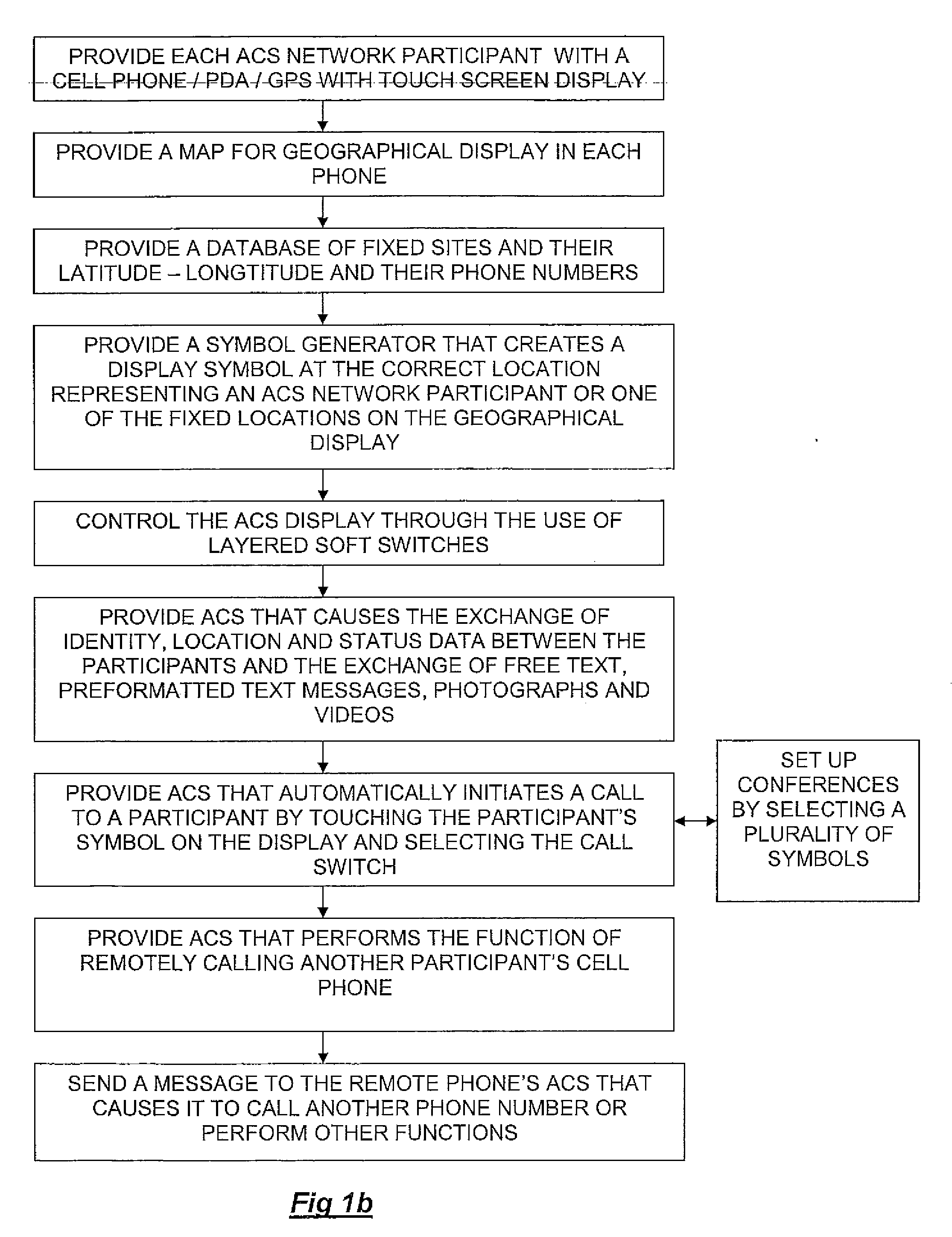
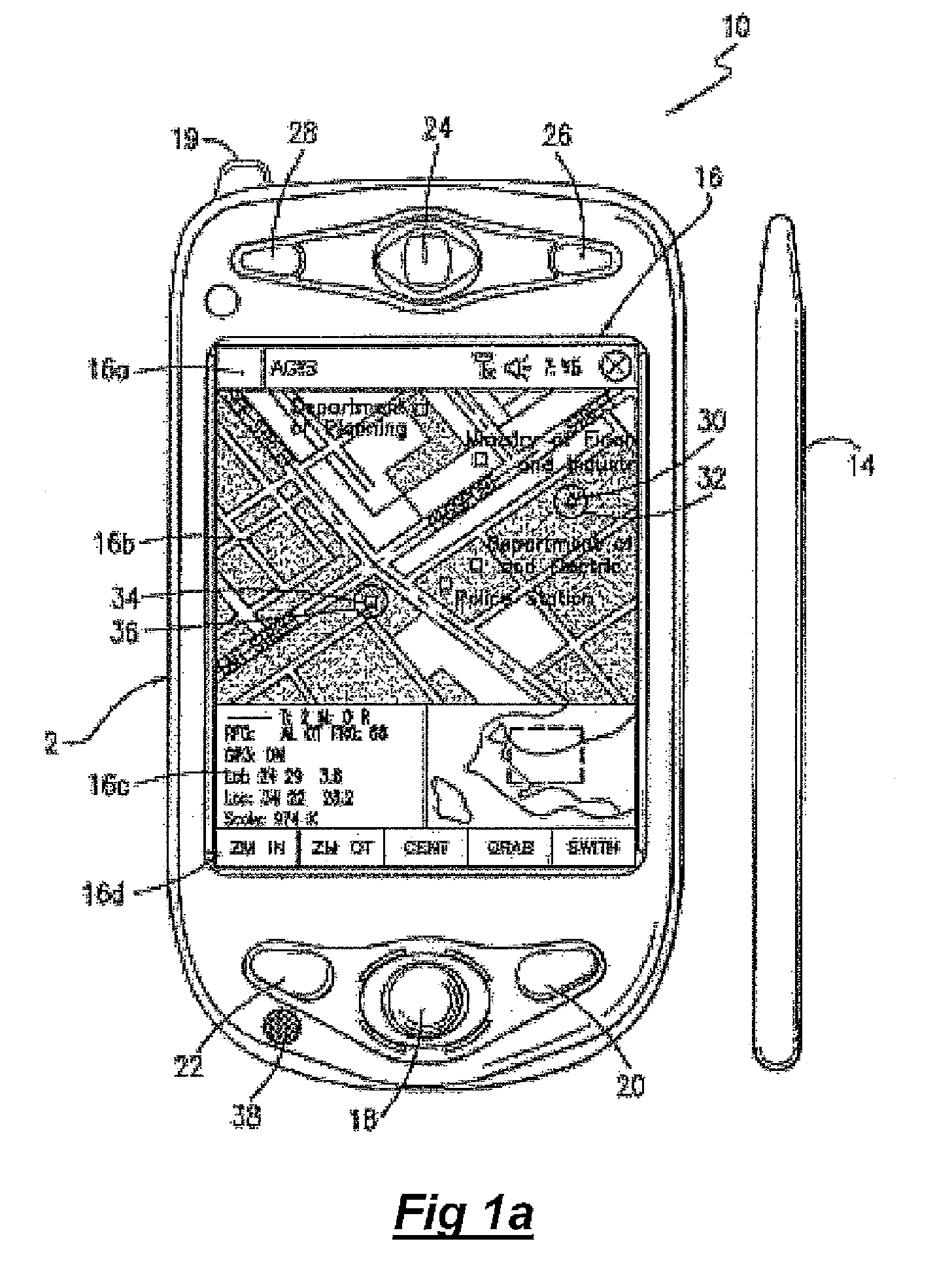
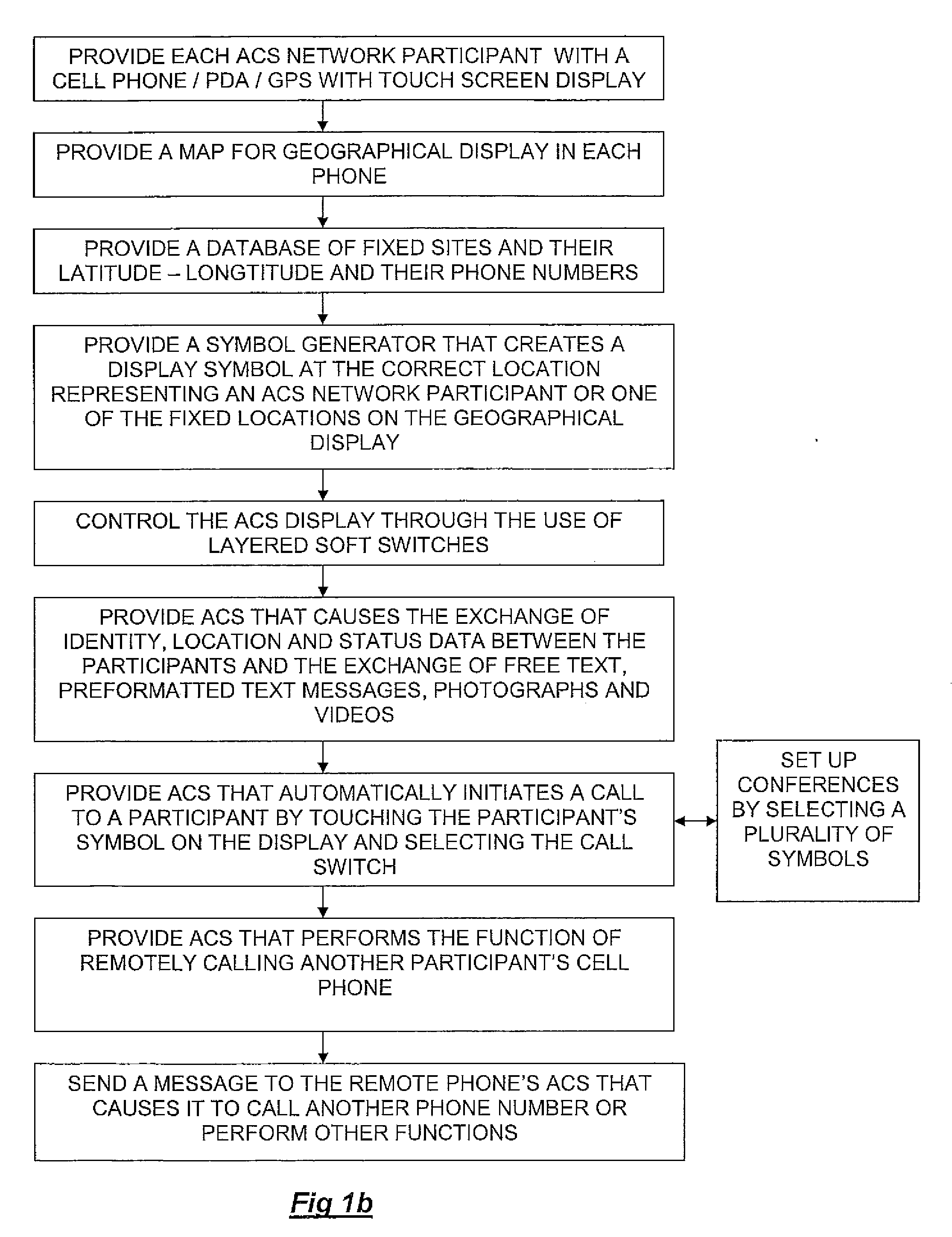
Method of utilizing forced alerts for interactive remote communications
ActiveUS20090075685A1Position fixationDevices with wireless LAN interfaceDisplay devicePersonal computer
The system and method having a specialized software application on a personal computer or a PDA / cell phone that that enables a participant to force an automatic acknowledgement and a manual response to a text or voice message from other participants within the same network. Each participant's PC or PDA / cell phone includes a force message alert software application program for both creating and processing these forced message alerts. The system and method enabled by the force message alert software application program provides the ability to (a) allow an operator to create and transmit a forced message alert from a sender PC or PDA / cell phone to one or more recipient PCs and PDA / cell phones within the communication network; (b) automatically transmit an acknowledgement of receipt to the sender PC or PDA cell phone upon the receipt of the forced message alert; (c) periodically resend the message to the recipient PCs and PDA / cell phones that have not sent an acknowledgement; (d) provide an indication of which recipient PCs and PDA / cell phones have acknowledged the forced message alert; (e) provide a manual response list on the display of the recipient PC and PDA / cell phone's display that can only be cleared by manually transmitting a response; and (f) provide an indication on the sender PC or PDA / cell phone of the status and content the manual responses
Owner:AGIS SOFTWARE DEVEMENT LLC
Backup method for storage system
ActiveUS8185502B2Digital data processing detailsError detection/correctionApplication enablementBackup
Owner:HITACHI LTD
Fitting system for sporting equipment
ActiveUS9261526B2Cooperate wellMaximize fitGymnastic exercisingDigital computer detailsRange of motionSports equipment
Enables a fitting system for sporting equipment using an application that executes on a mobile phone for example to prompt and accept motion inputs from a given motion capture sensor to measure a user's size, range of motion, speed and then utilizes that same sensor to capture motion data from a piece of equipment, for example to further optimize the fit of, or suggest purchase of a particular piece of sporting equipment. Utilizes correlation or other data mining of motion data for size, range of motion, speed of other users to maximize the fit of a piece of equipment for the user based on other user's performance with particular equipment. For example, this enables a user of a similar size, range of motion and speed to data mine for the best performance equipment, e.g., longest drive, lowest putt scores, highest winning percentage, etc., associated with other users having similar characteristics.
Owner:NEWLIGHT CAPITAL LLC
Method of utilizing forced alerts for interactive remote communications
The system and method having a specialized software application on a personal computer or a PDA / cell phone that that enables a participant to force an automatic acknowledgement and a manual response to a text or voice message from other participants within the same network. Each participant's PDA / cell phone includes a force message alert software application program for both creating and processing these forced message alerts. The system and method enabled by the force message alert software application program provides the ability to (a) allow an operator to create and transmit a forced message alert from a sender PDA / cell phone to one or more recipient PCs and PDA / cell phones within the communication network; (b) automatically transmit an acknowledgement of receipt to the sender PDA cell phone upon the receipt of the forced message alert; (c) periodically resend the message to the recipient PCs and PDA / cell phones that have not sent an acknowledgement; (d) provide an indication of which recipient PCs and PDA / cell phones have acknowledged the forced message alert; (e) provide a manual response list on the display of the recipient PC and PDA / cell phone's display that can only be cleared by manually transmitting a response; and (f) provide an indication on the sender PDA / cell phone of the status and content the manual responses.
Owner:AGIS SOFTWARE DEVEMENT LLC
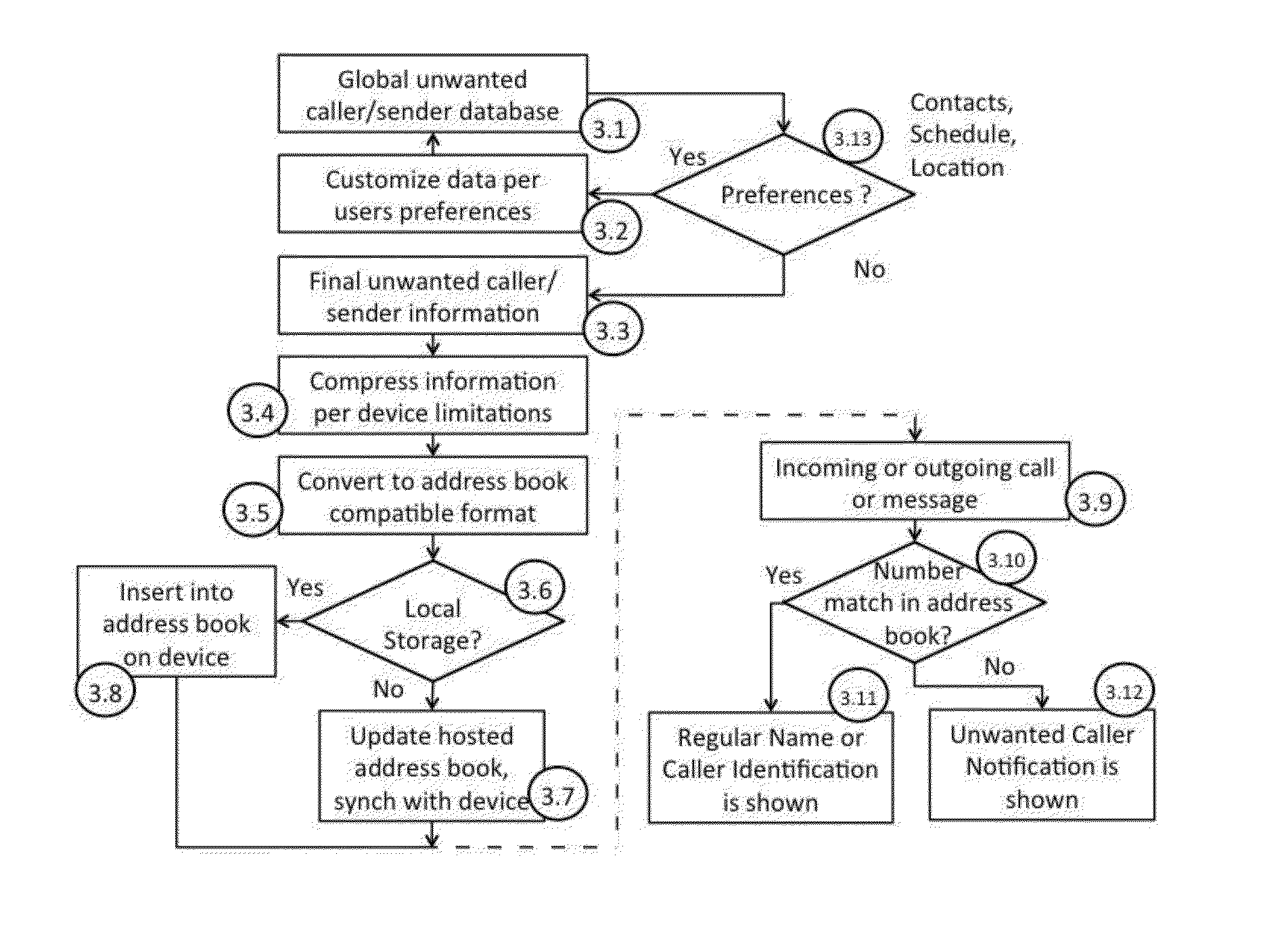
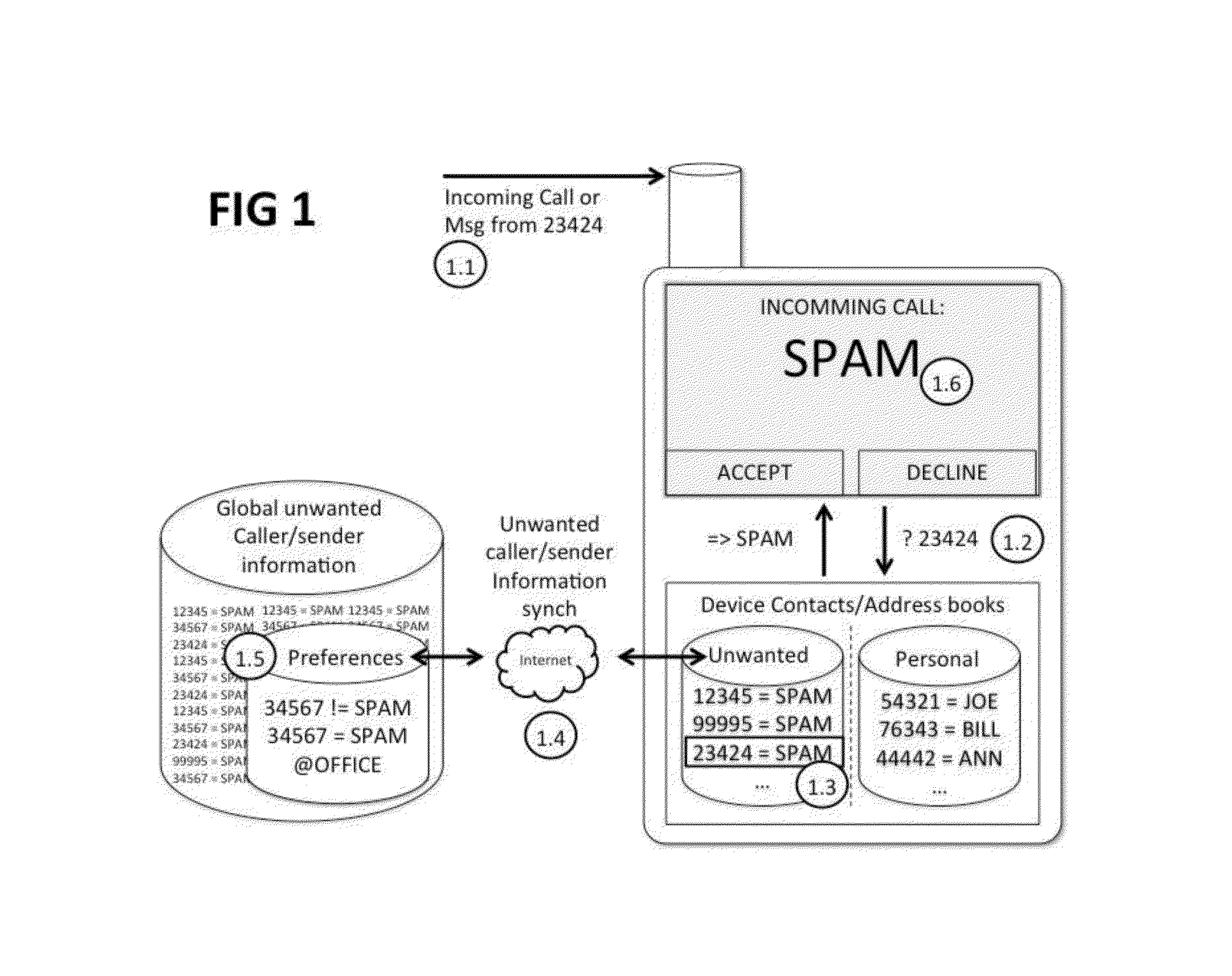
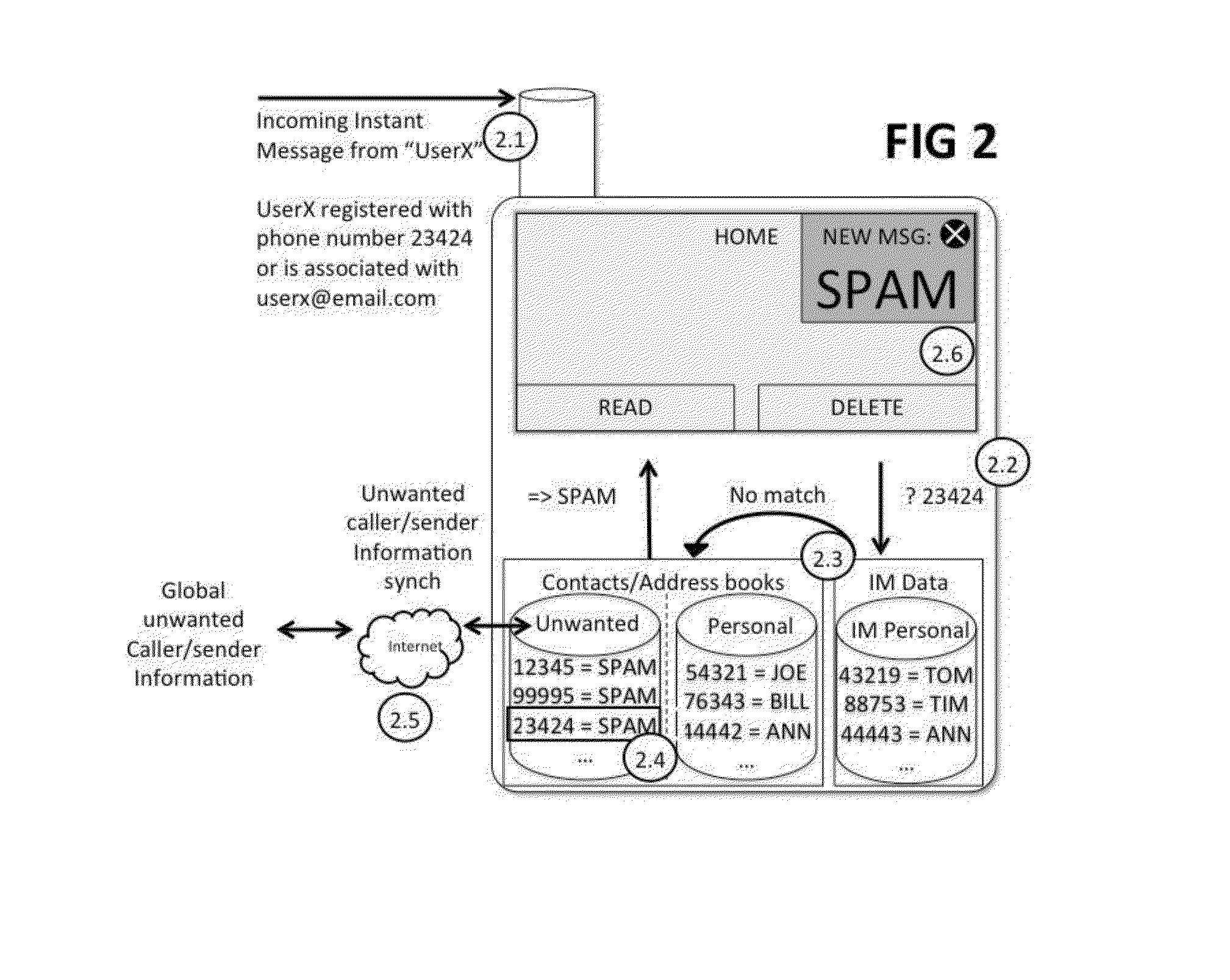
Unwanted caller and message sender identification for restricted communication devices
ActiveUS20150334230A1Special service for subscribersCommmunication supplementary servicesAddress bookApplication enablement
Method for enabling unwanted caller notifications or unwanted message sender notifications for all communication devices and applications including those with restricted programmatic call and message log access. The method delivers and stores a database of unwanted caller / message sender identification information in the device default contacts list, which is made available to the device's default caller / message sender identification service and to applications installed on the device. In one embodiment the unwanted caller / message sender identification information database is delivered as a separate synchronized address book, which can include additional unwanted caller notification information, for example the number or type of complaints about a given phone number.
Owner:HIYA INC
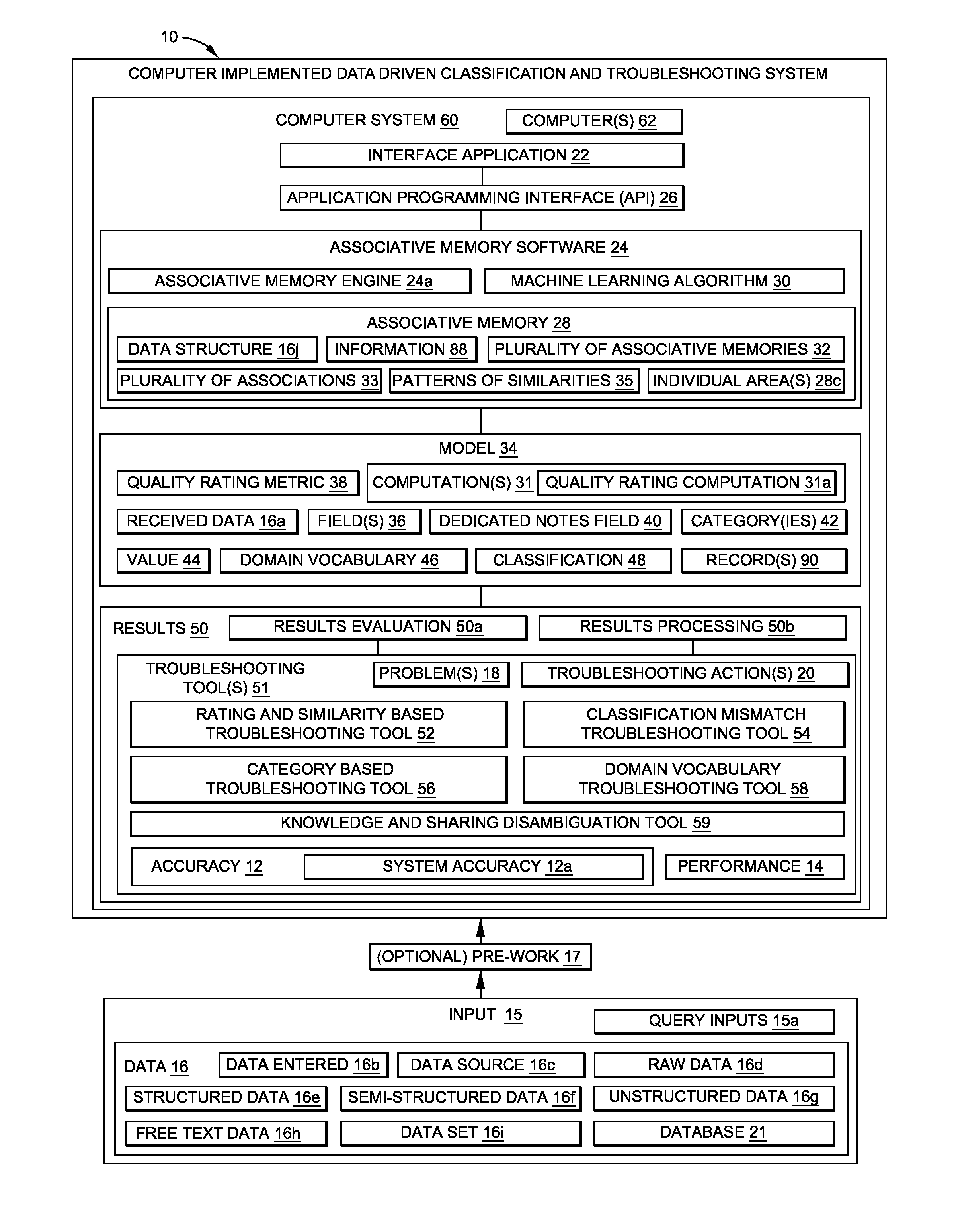
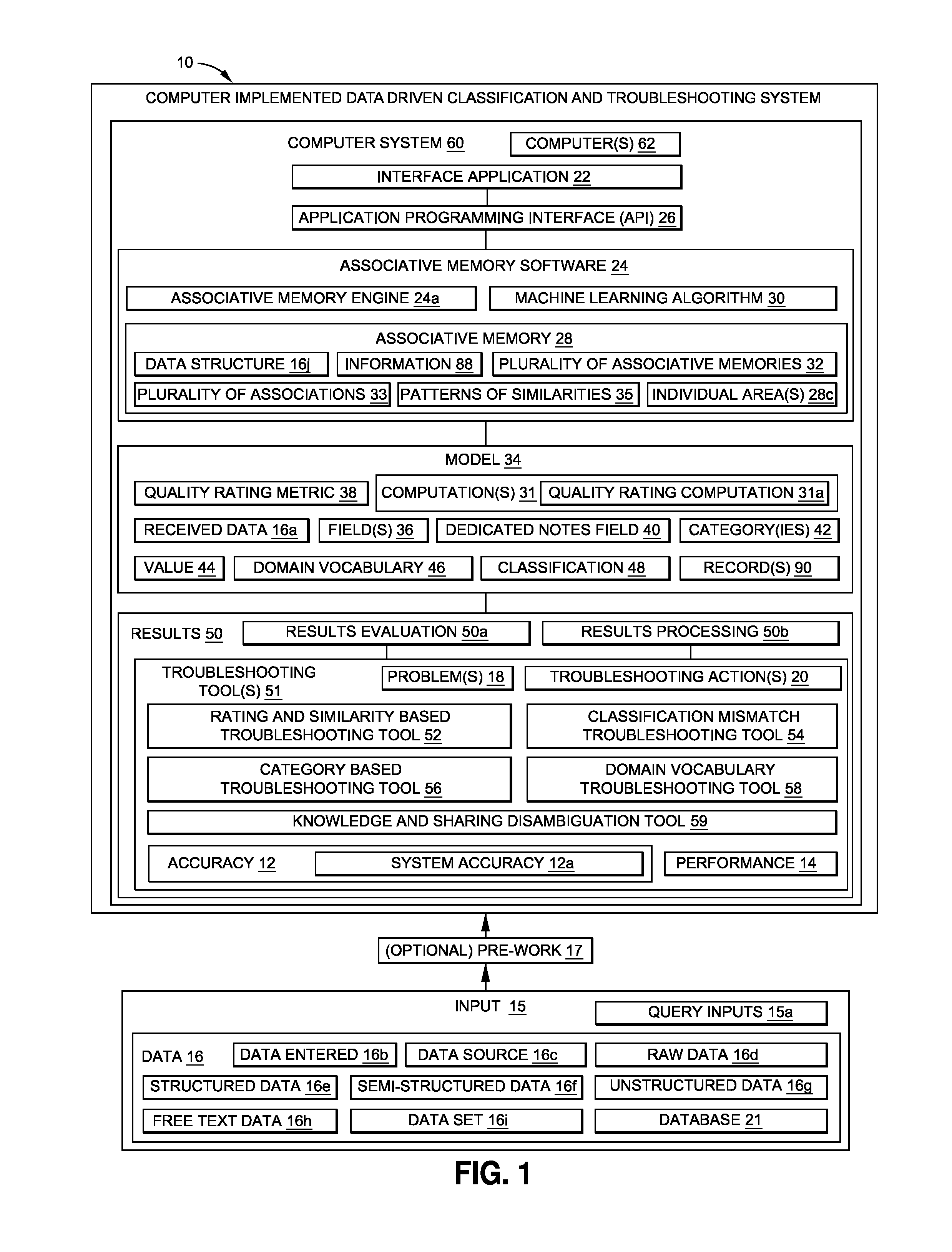
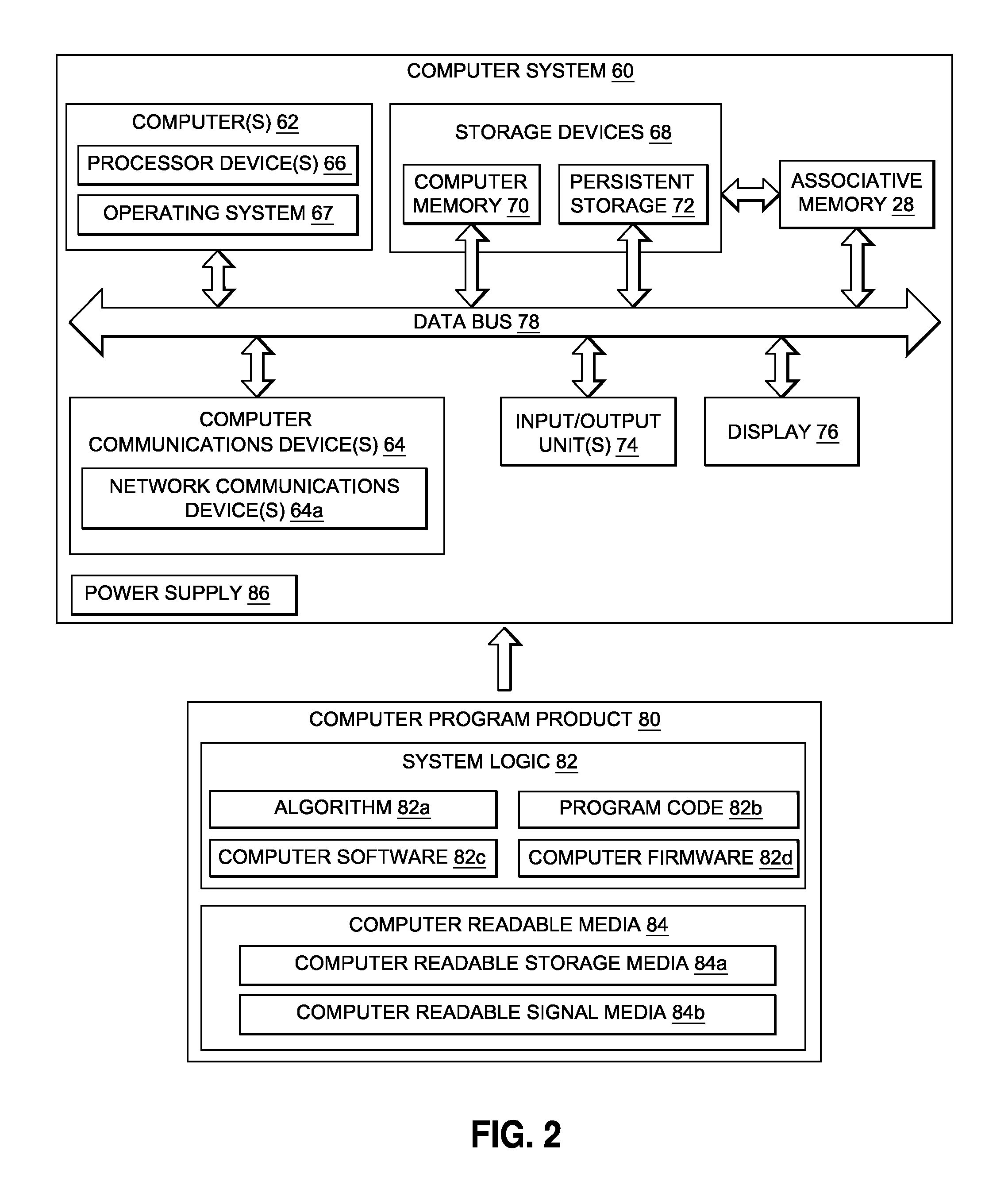
Data driven classification and troubleshooting system and method
ActiveUS20170024662A1Improve accuracyImprove performanceRelational databasesBiological modelsQuality ratingApplication enablement
There is provided a computer implemented data driven classification and troubleshooting system and method. The system has an interface application enabled to receive data. The system has an associative memory software in communication with the interface application via an API. The associative memory software has an associative memory and a machine learning algorithm. The system has one or more individual areas, within the associative memory, requiring one or more troubleshooting actions to improve accuracy of the individual areas. The system has at least one troubleshooting tool enabled by the interface application. The at least one troubleshooting tool enables or performs the troubleshooting actions. The system has a quality rating metric (QRM) that measures a strength and an assurance that one or more predictions of the associative memory are correct. The one or more troubleshooting actions results in improving the accuracy and the performance of the associative memory.
Owner:THE BOEING CO
Method and system for recording telephone operators of large-scale call center via network
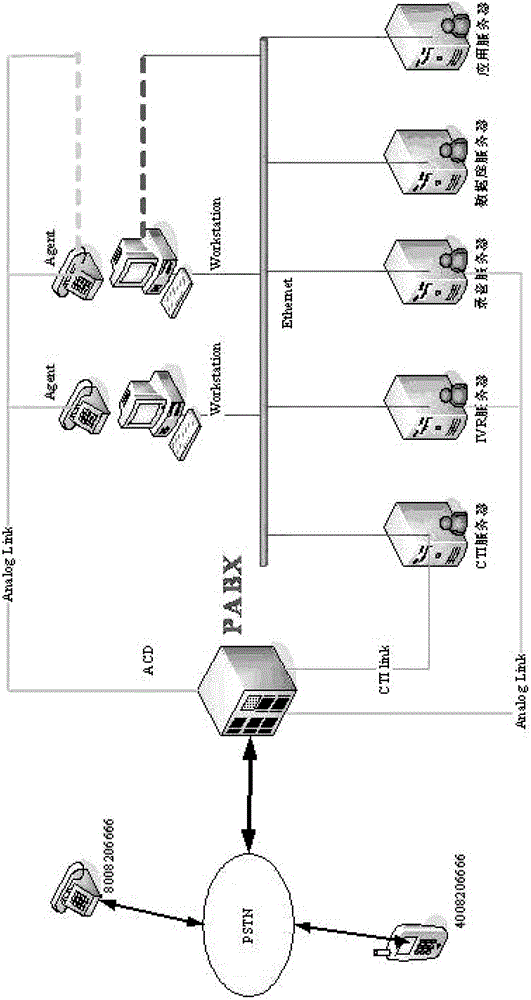
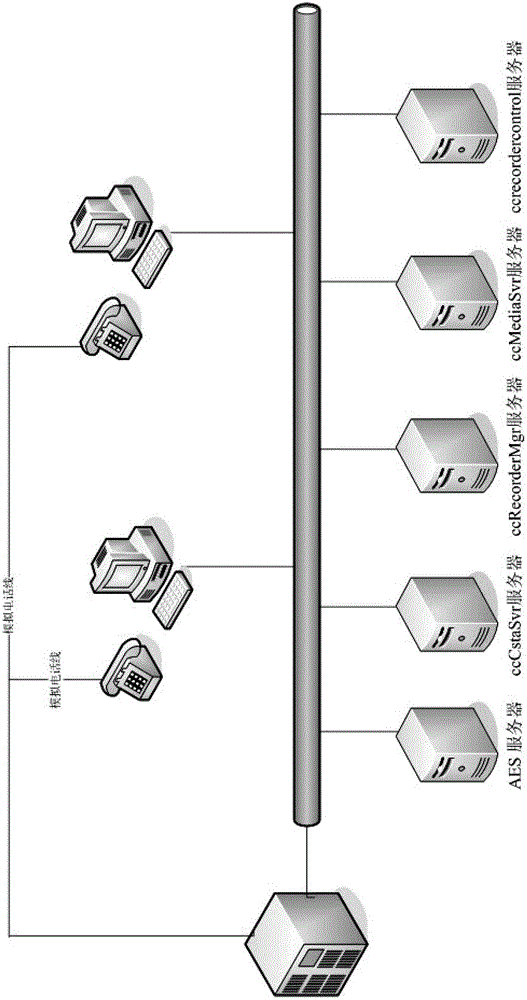
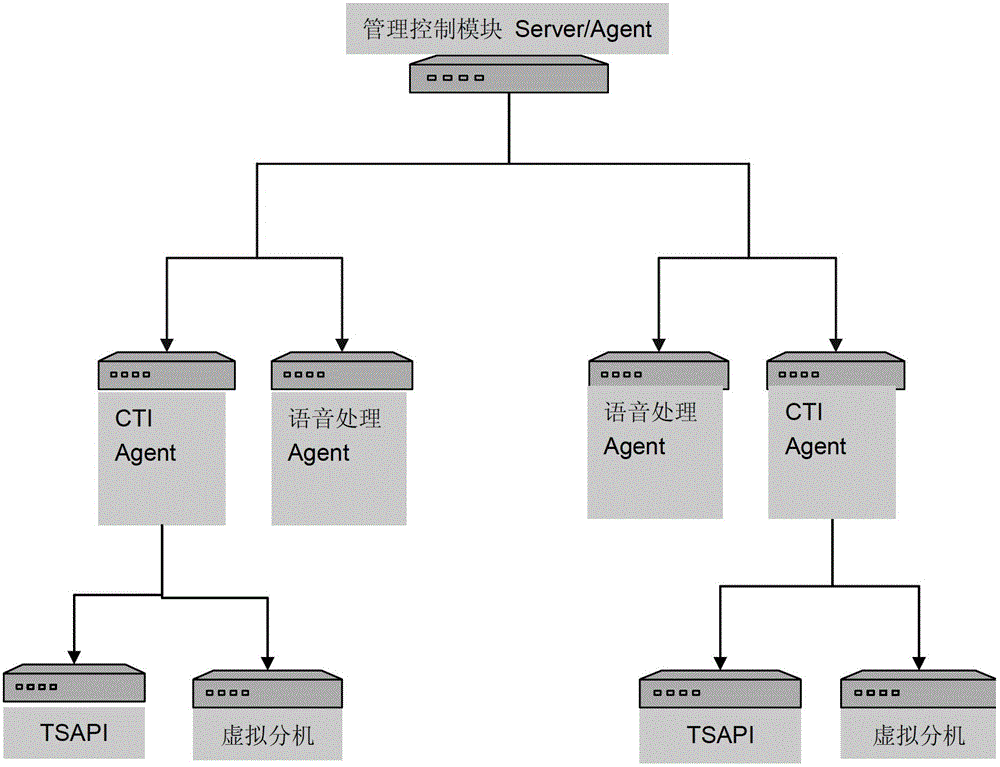
ActiveCN102752464AReduce the amount requiredImprove performanceSpecial service for subscribersAutomatic call-answering/message-recording/conversation-recordingTelephone networkApplication enablement
The invention discloses a method for recording telephone operators of a large-scale call center via the network. The method includes monitoring information of a recorded extension; starting recording by responsible modules uniformly when recording is required; transferring various requests of service sides at low levels to an AES (application enablement service) server and receiving processing results fed back by the AES server; registering and monitoring IP (internet protocol) monitoring extensions; starting monitoring and recording according to set strategy after information for requiring recording is received; receiving voice flow recorded, and converting the voice flow into voice files in any format, and compressing and dumping the voice files generated.
Owner:SHANGHAI CTRIP COMMERCE CO LTD
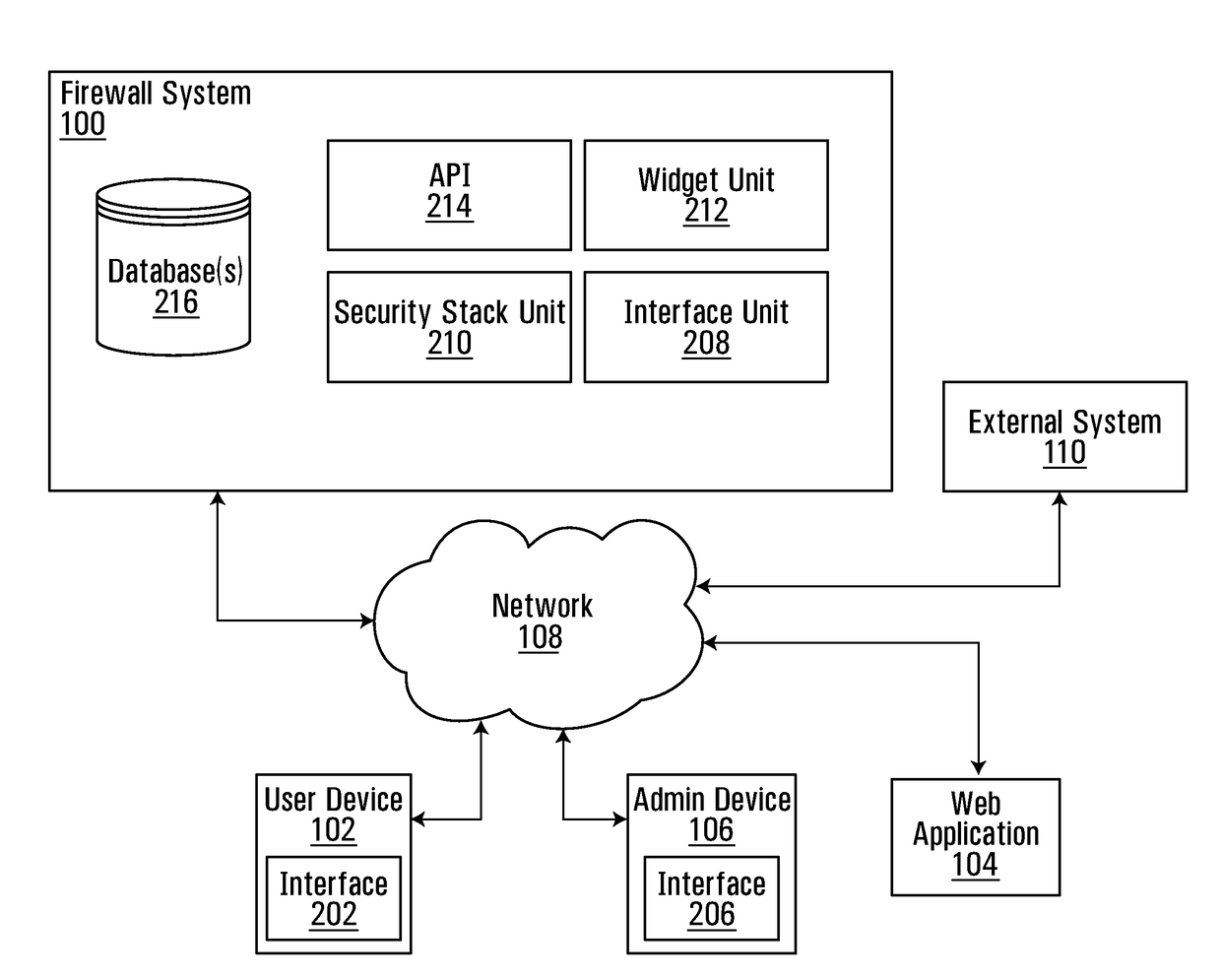
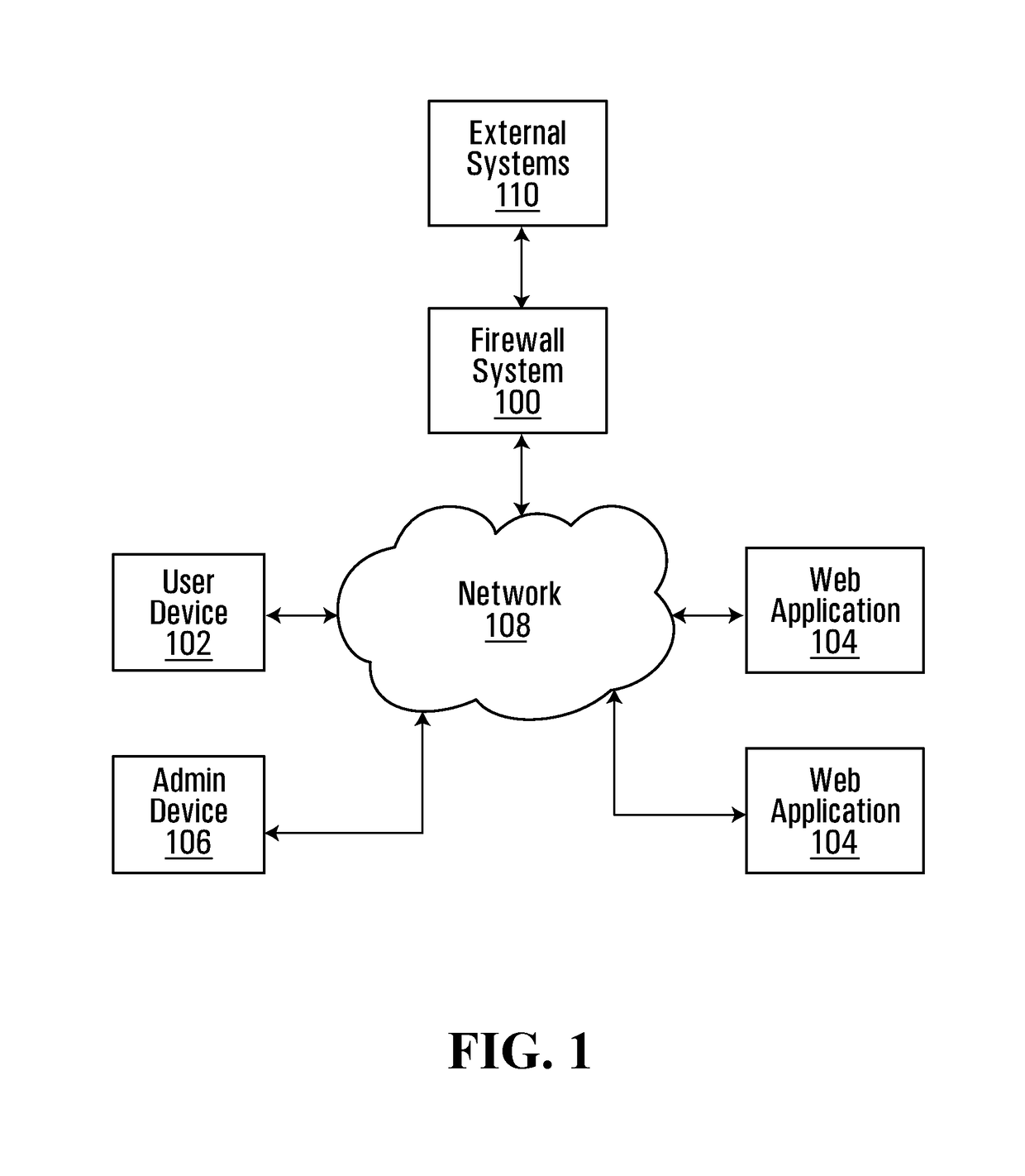
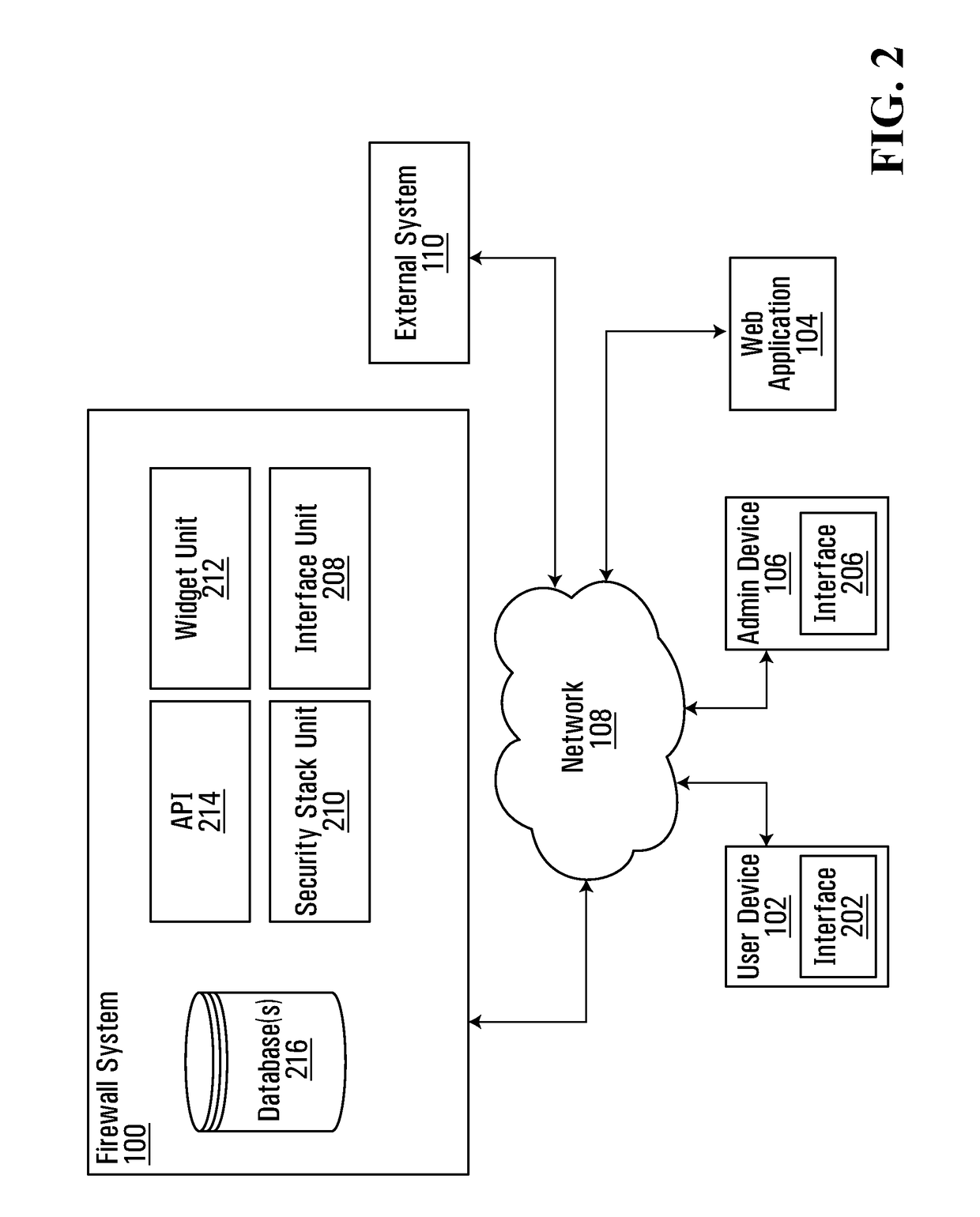
Web application firewall
ActiveUS20180241721A1Easy to updateAvoid triggering excessive false positivesTransmissionWeb applicationApplication programming interface
Embodiments described herein provide an application programming interface and framework for a web application firewall single policy model. The framework can layer on top of a firewall platform that provides web application specific widgets that may be toggled and configured to enable or disable certain firewall actions on a per application basis. The framework includes a security stack that defines the order for the widgets. The security stack can provide the ability for a single policy model to be used for the firewall and allows for per application customizations.
Owner:ROYAL BANK OF CANADA
Context management system for a network including a heterogenous set of terminals
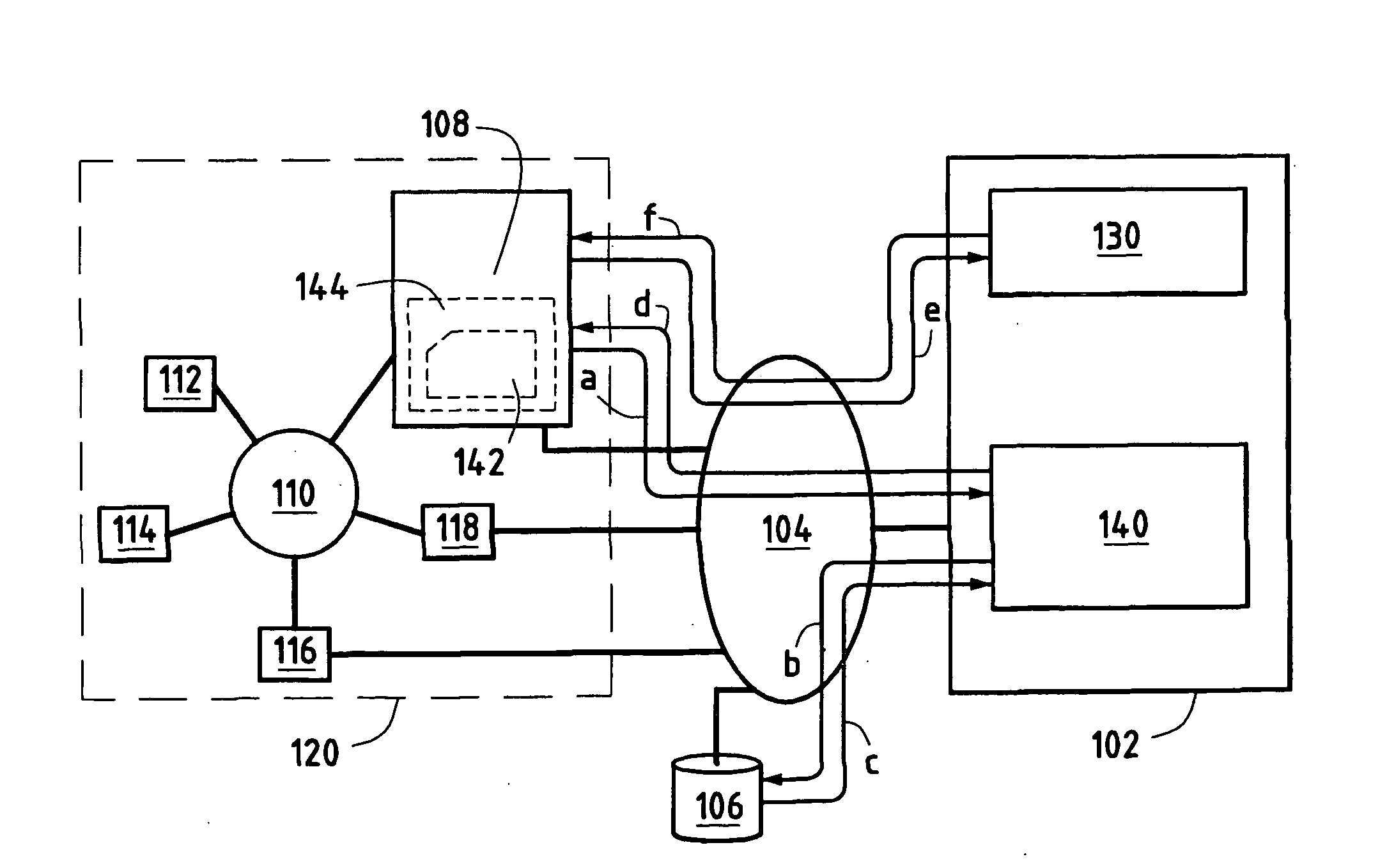
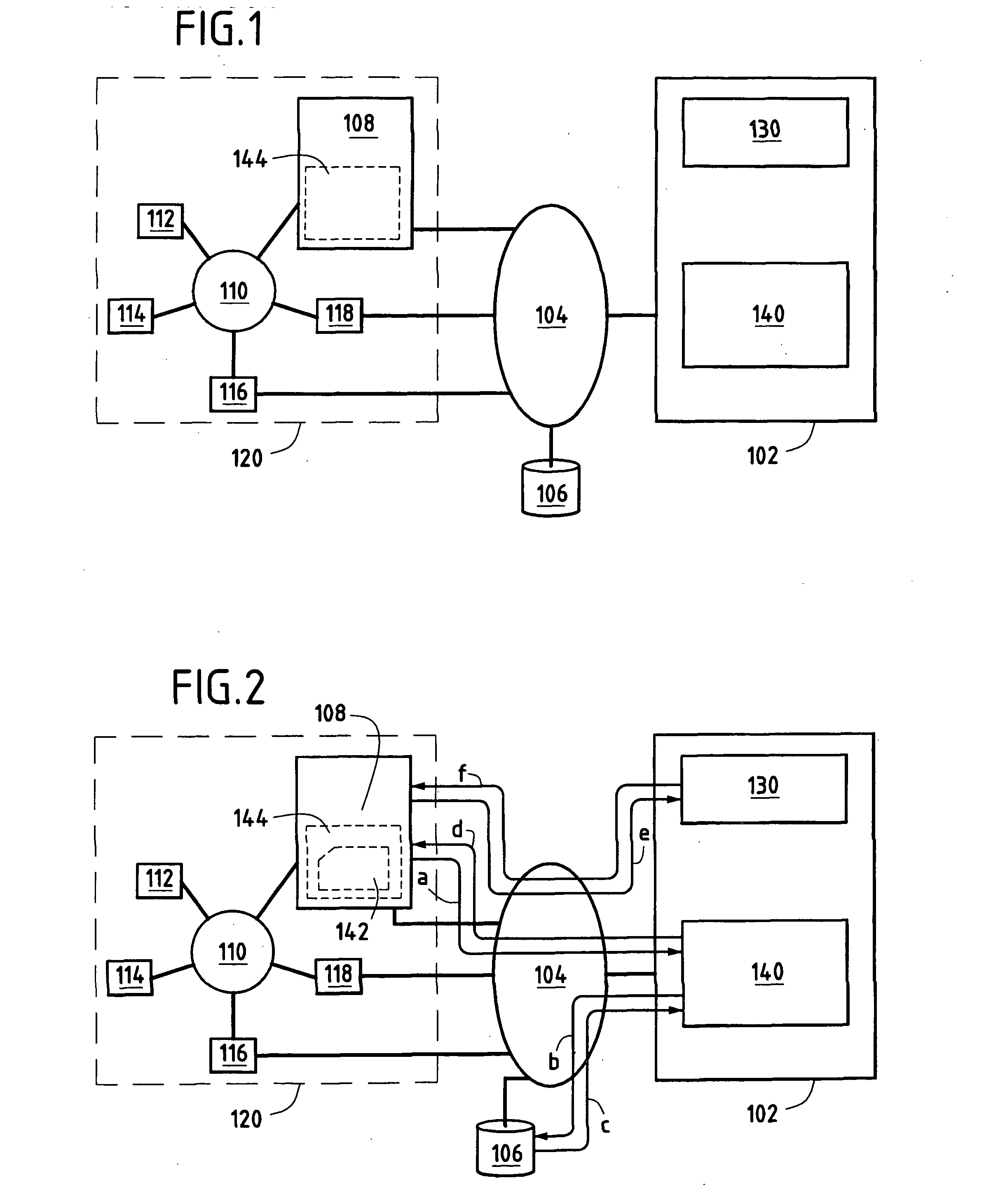
InactiveUS20070067423A1Simplify and automate context managementInstruments for road network navigationRoad vehicles traffic controlInformation processingContext management
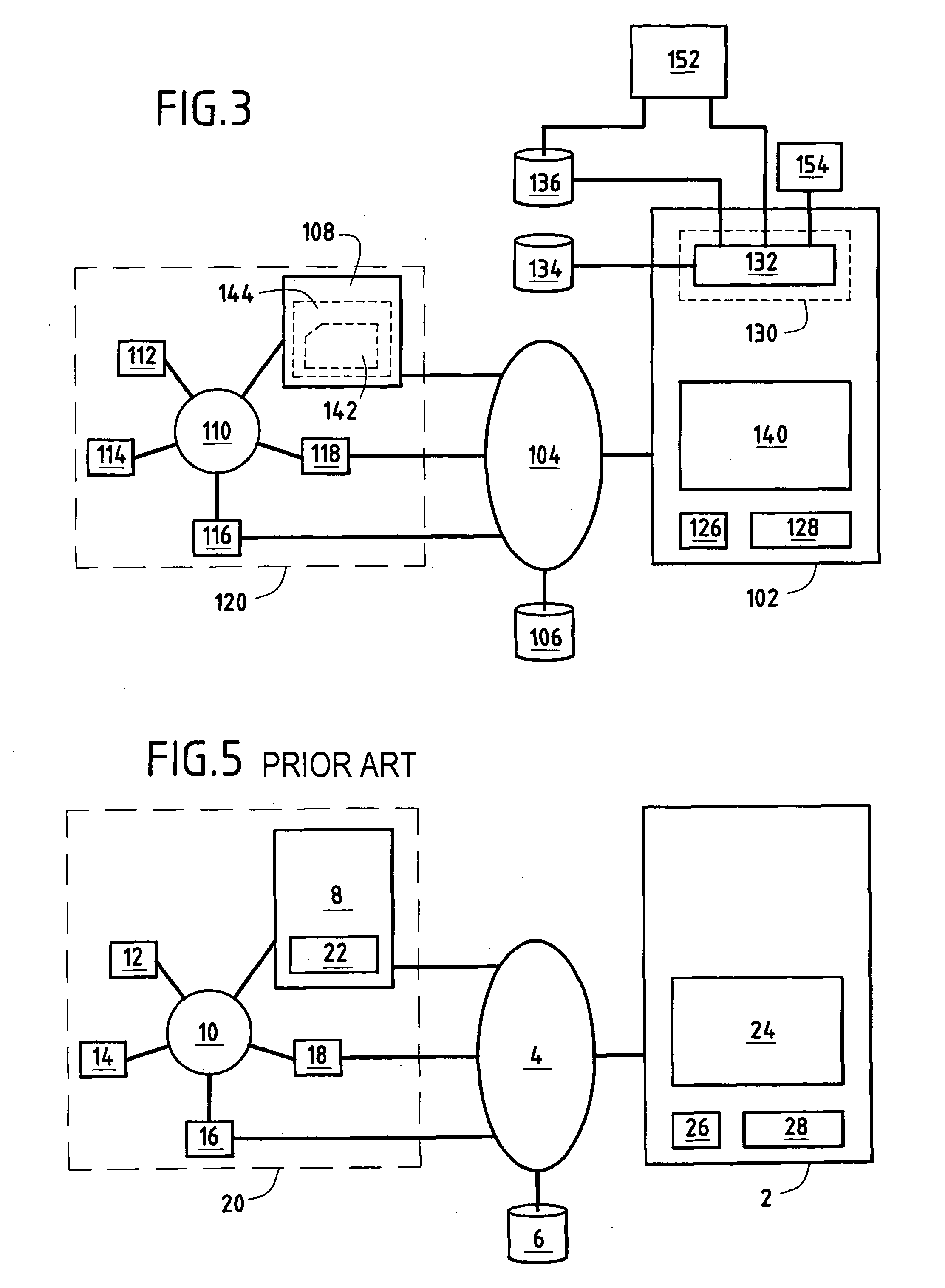
A context management system offering a user (160) the most appropriate context for processing information comprises a heterogeneous set (120) of terminals interconnected by a local information transmission network (110) and including a master terminal (108), a server computer (102) comprising processing means (130) for determining the most appropriate context for information processing by said heterogeneous set (120) of terminals, and an external information transmission network (104) connecting the server (102) at least to the master terminal (108). The server (102) further comprises a converter module (140) for sending the master terminal (108) an application (142) enabling the user (160) to download said most appropriate context to the master terminal (108).
Owner:FRANCE TELECOM SA
Network determining method and device
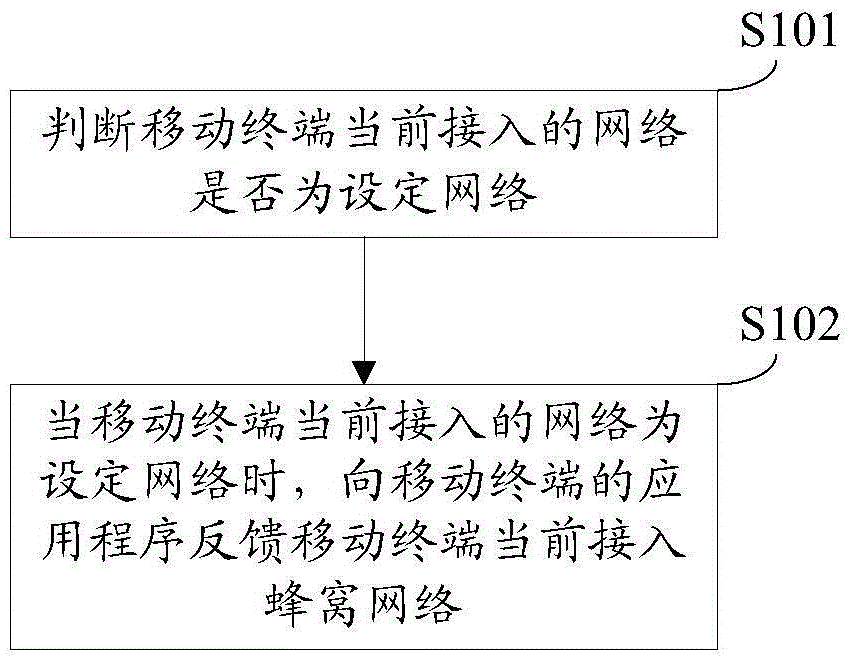
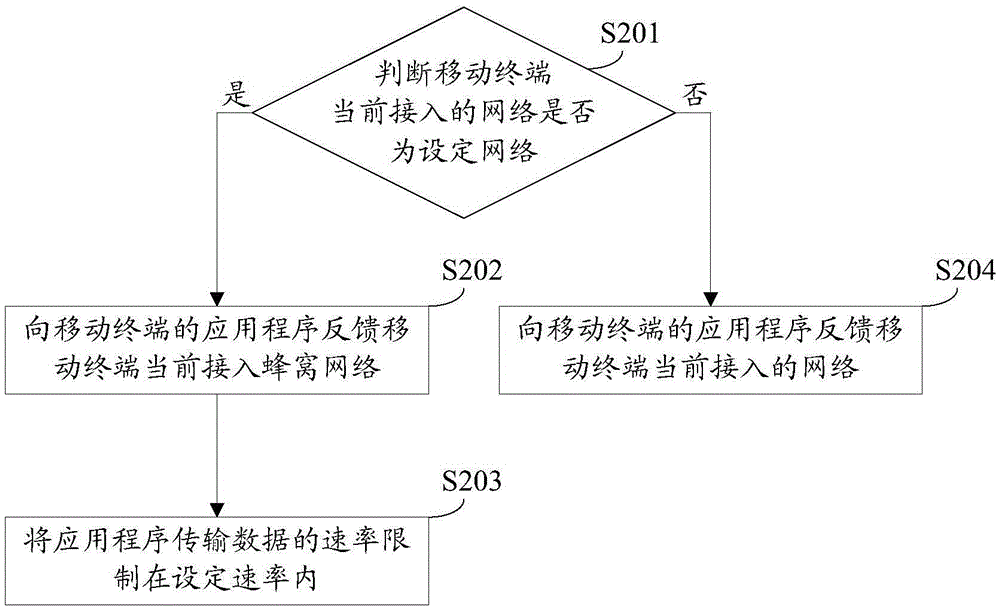
The disclosure relates to a network determining method and device, and belongs to the technical field of a mobile terminal. The method includes the steps of: judging whether a mobile terminal current access network is a set network; and when the mobile terminal current access network is the set network, feeding back a cellular network currently accessed by the mobile terminal to an application of the mobile terminal, the set network being a Wireless Fidelity (WiFi) hotspot network established based on the cellular network. When the mobile terminal current access network is the set network, that the mobile terminal current access network is a cellular network is fed back to the application of the mobile network, and the set network is the WiFi hotspot network established based on the cellular network. When the mobile terminal current access network is the cellular network in essence, that the current access network is the cellular network is fed back to the application, and the application starts using a strategy that the network is used conservatively. Some unessential uploading and downloading operations are avoided, the network usage is reduced, and furthermore the user payment is reduced.
Owner:XIAOMI INC
Domain-based application program function
The invention provides a domain-based application program function, and particularly relates to a system and a method of a specific function for starting or prohibiting an application program of Web browser or a browser-based application program. For example, a method for controlling an application program function can comprise the following steps of connecting contents requested by a server and receiving a response from the server; the information of the response contains the requested contents and a text character string token embedded in the contents; the token is decoded, and the information contained in the token is analyzed, to determine that which functions of the application program can be used for displaying the requested contents, and can invoke the application program function which enables the requested contents to be displayed on the same level; the token can be a digital certificate based on a domain name of the server or a cryptographic hash of the domain name of the server.
Owner:RES INST OF SUN YAT SEN UNIV & SHENZHEN
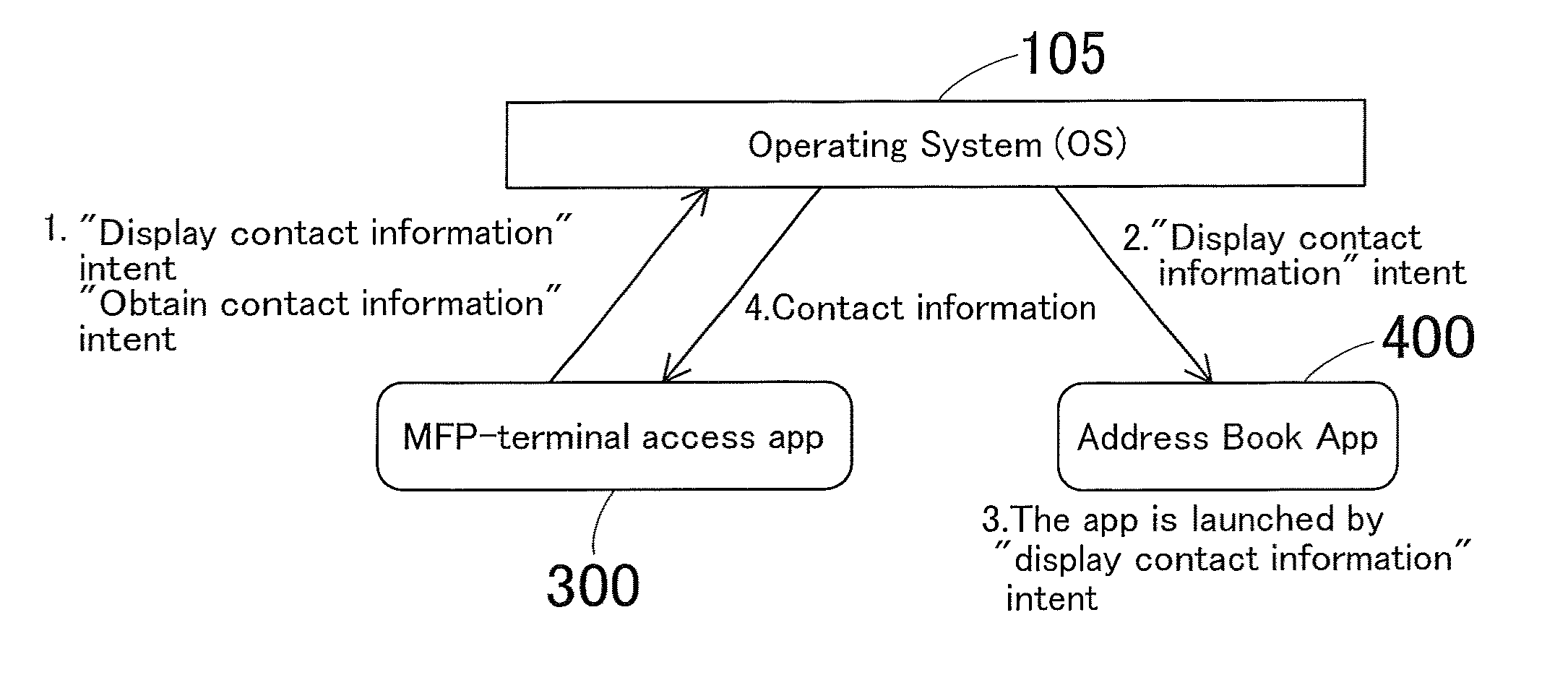
Contact information transfer system, contact information transfer method, portable terminal apparatus, and recording medium
A contact information transfer system includes an image processing apparatus and a portable terminal apparatus; the portable terminal apparatus includes a cooperation portion that launches a second application for organizing contact information upon access to the image processing apparatus being enabled by a first application for accessing the image processing apparatus, the contact information including contact identification information and points of contact connected to the respective contact identification information, a contact information obtaining portion that obtains the contact information, and a transfer portion that transfers the contact information to the image processing apparatus; the image processing apparatus includes a receiving portion that receives the contact information, a display, and a display controller that displays the contact information on the display by converting it into a data format supported on the display.
Owner:KONICA MINOLTA INC
System and method for providing application-specific on-line charging in a communications environment
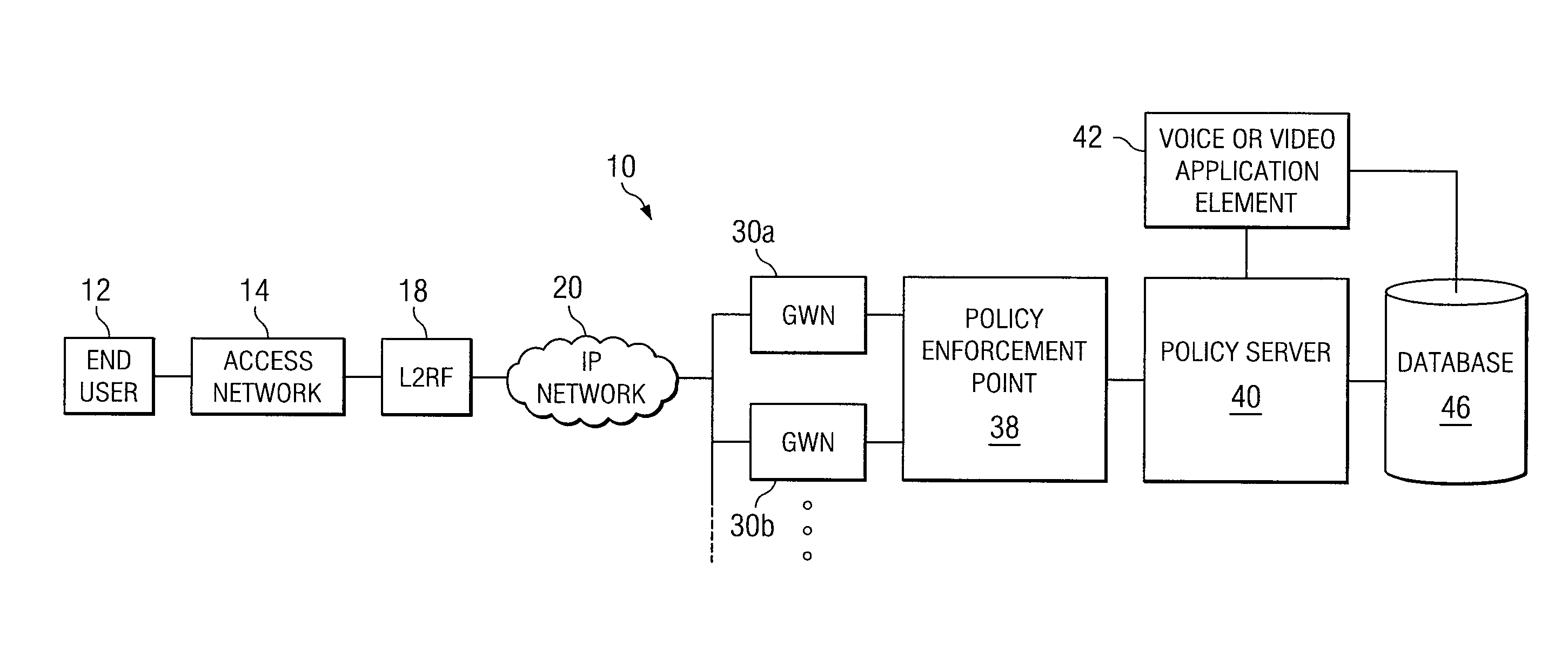
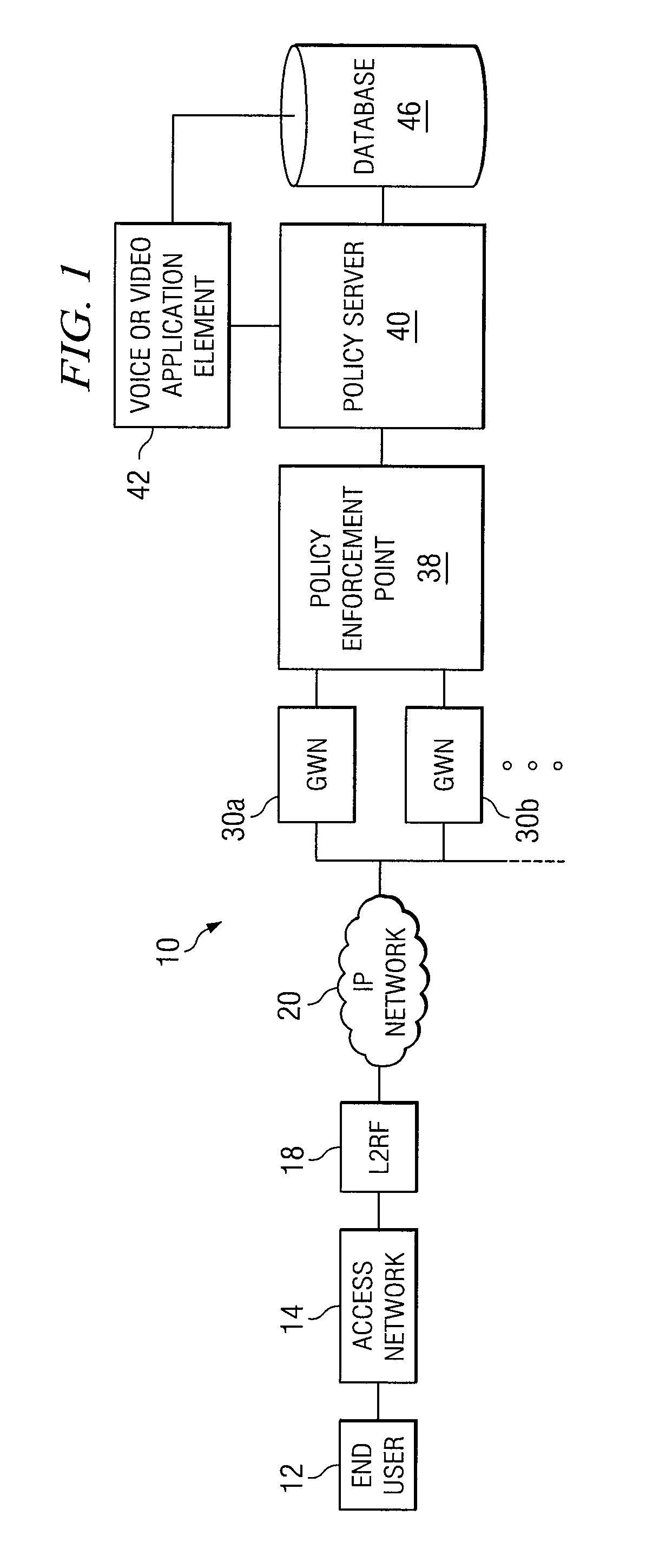
ActiveUS7971228B2Accurate chargesReduce disadvantagesDigital data processing detailsUser identity/authority verificationComputer networkApplication specific
An architecture for A method for providing on-line charging in a network environment is provided that includes interacting with an application that is selected by an end user, and with a policy enforcement point to install corresponding policies that are inclusive of charging rules. The method also includes performing, via a policy server, on-line charging interactions on behalf of the selected application itself such that application-specific on-line charging for the application is enabled. In more particular embodiments, the policy server understands which application is interacting with it by use of application tokens, source, or service identifiers. Also, the application element can query the policy server indirectly to grant network resources and the policy server examines an end user's policy profile or a network-wide profile (or both) and recognizes that on-line charging applies to the selected application.
Owner:CISCO TECH INC
Method and system for replicating stored information
ActiveUS8595457B1Reduce copyImprove performanceRedundant operation error correctionMemory systemsOperational systemApplication enablement
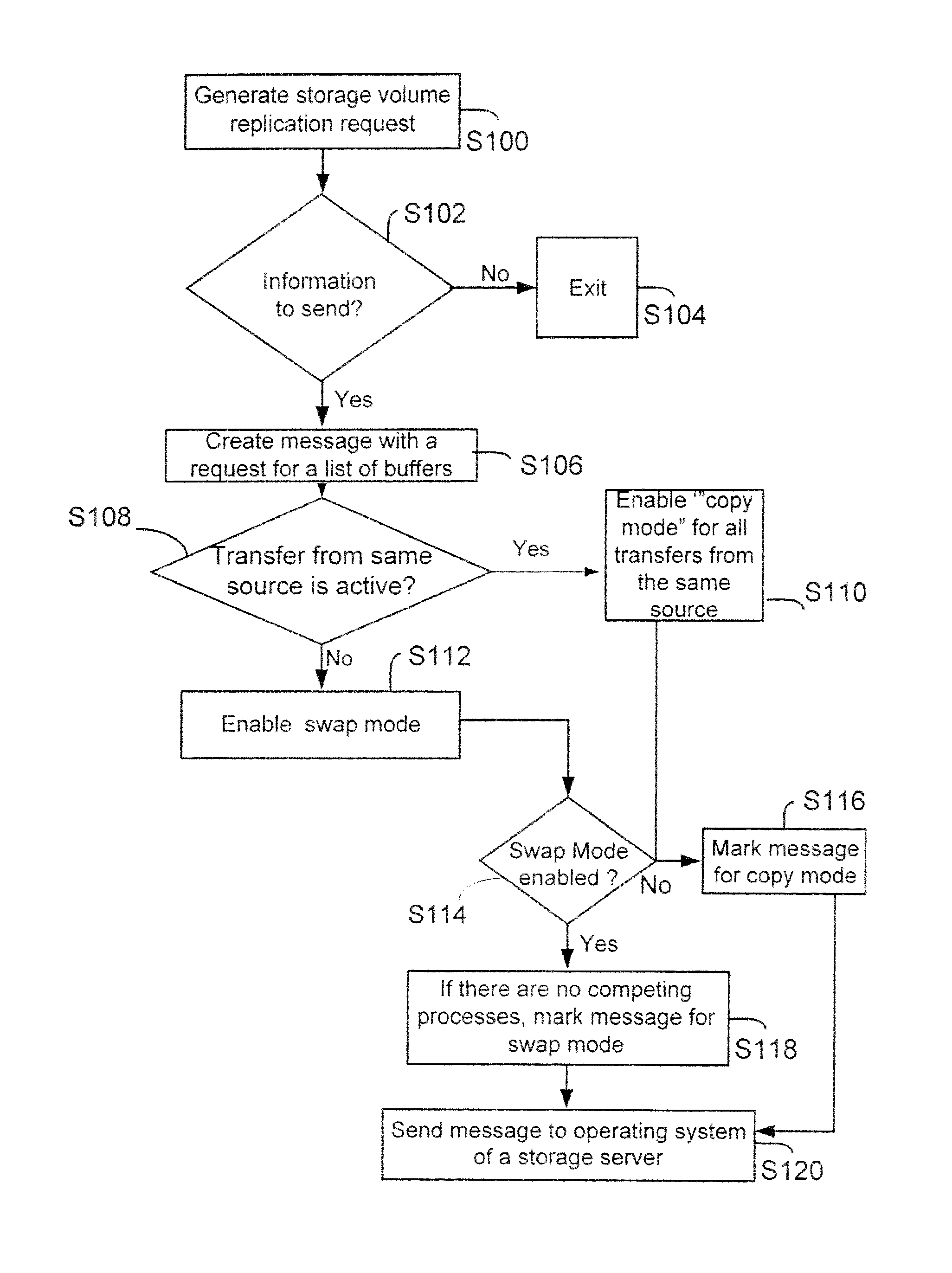
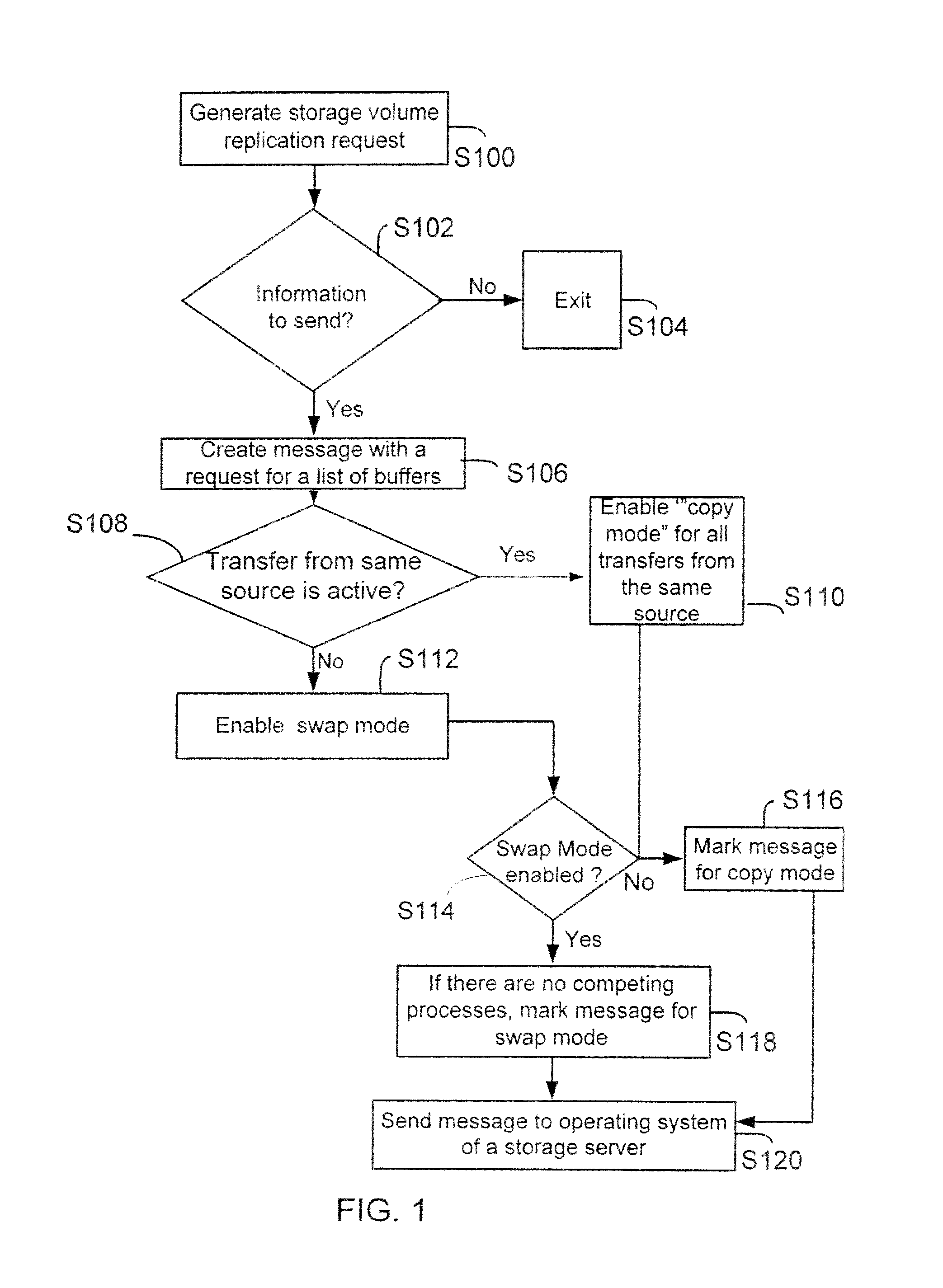
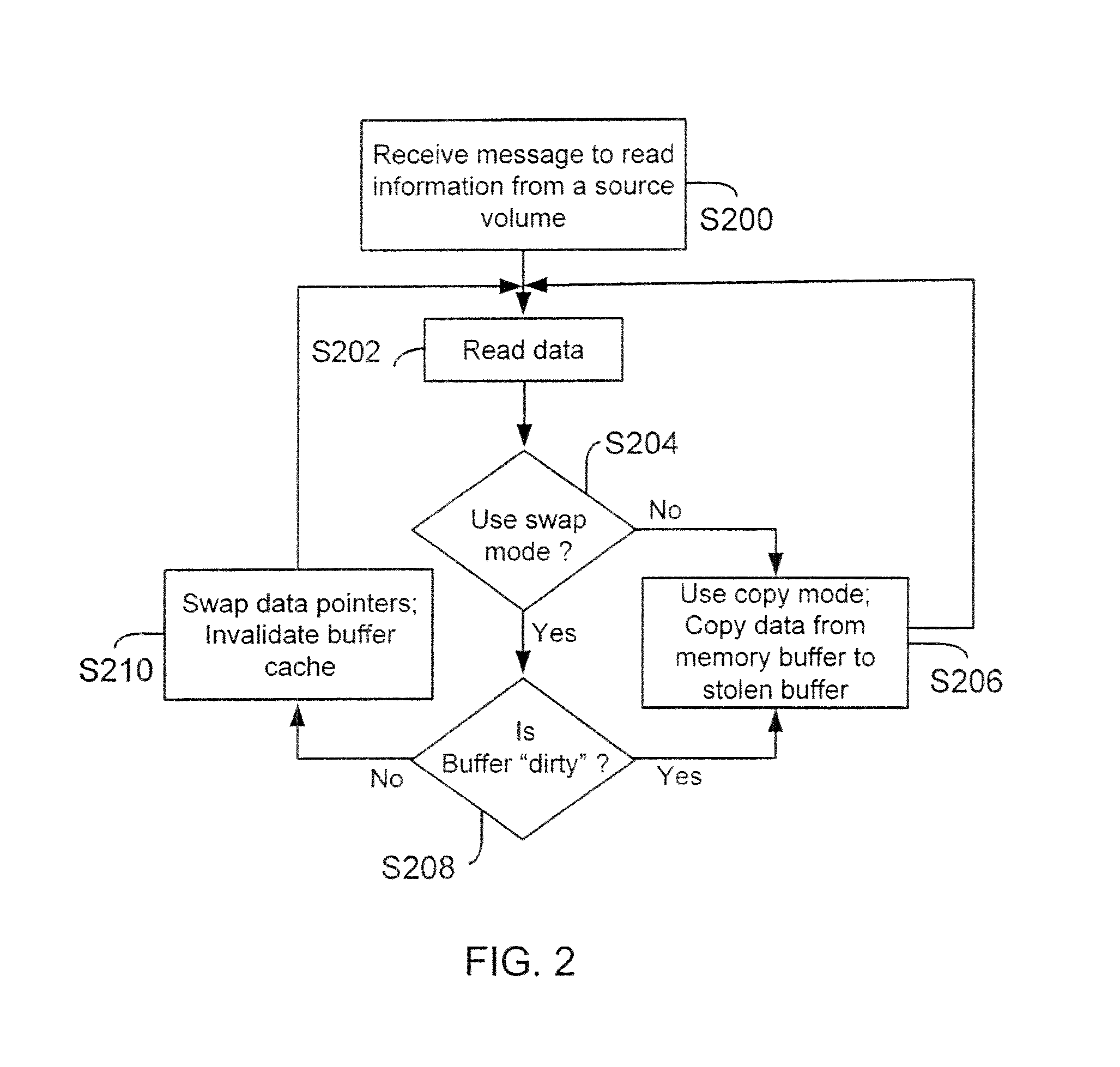
Method and system for replicating a storage volume is provided. Information is adaptively replicated in a swap mode or a copy mode. When information is copied from a storage volume to a memory buffer, an application determines if another information transfer from the same source volume is pending. If a transfer from the same source is pending, then information is copied from the memory buffer to a stolen buffer in a copy mode. If a transfer from the same source is not pending, then instead of copying the information, the application enables a swap mode. During the swap mode, an operating system for a storage system swaps a pointer from the stolen buffer to information stored in the memory buffer. The memory buffer itself is invalidated so that no other module can access the memory buffer. Because the pointers are swapped, the application accesses information directly from the memory buffer.
Owner:NETWORK APPLIANCE INC
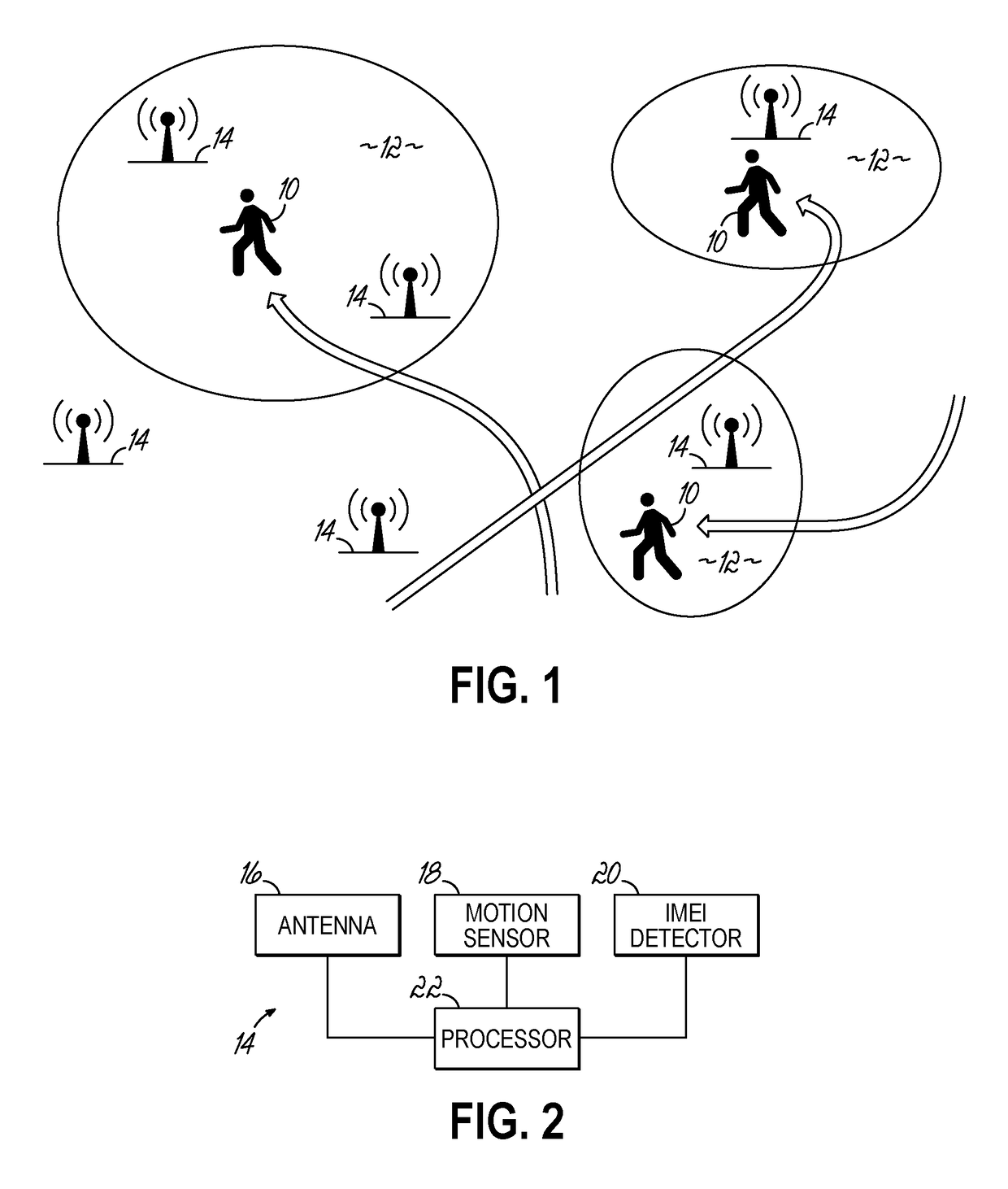
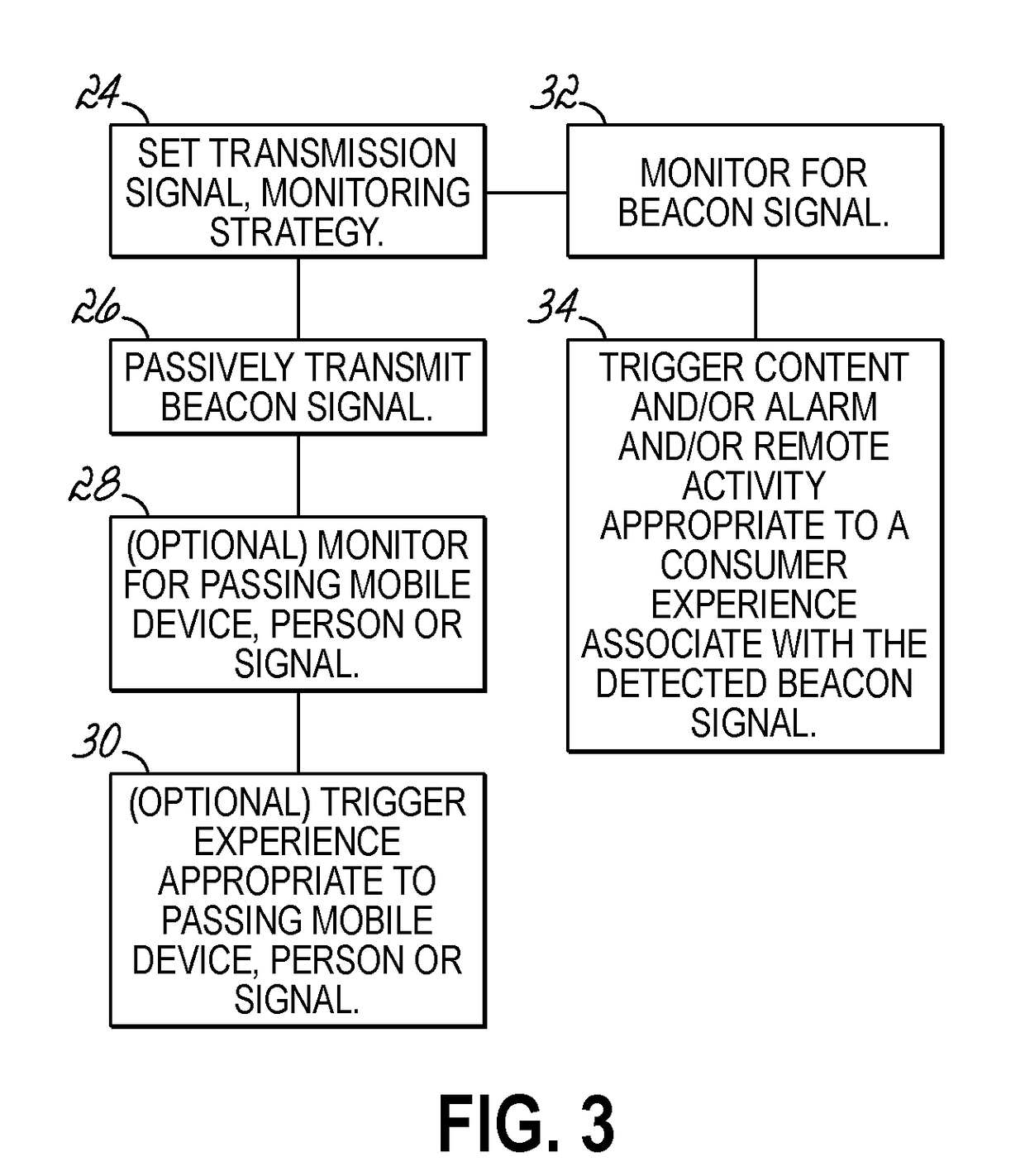
In-house fixture or signage with location based intelligence
InactiveUS20180288583A1Eliminate needServices signallingConnection managementLocation trackingDisplay device
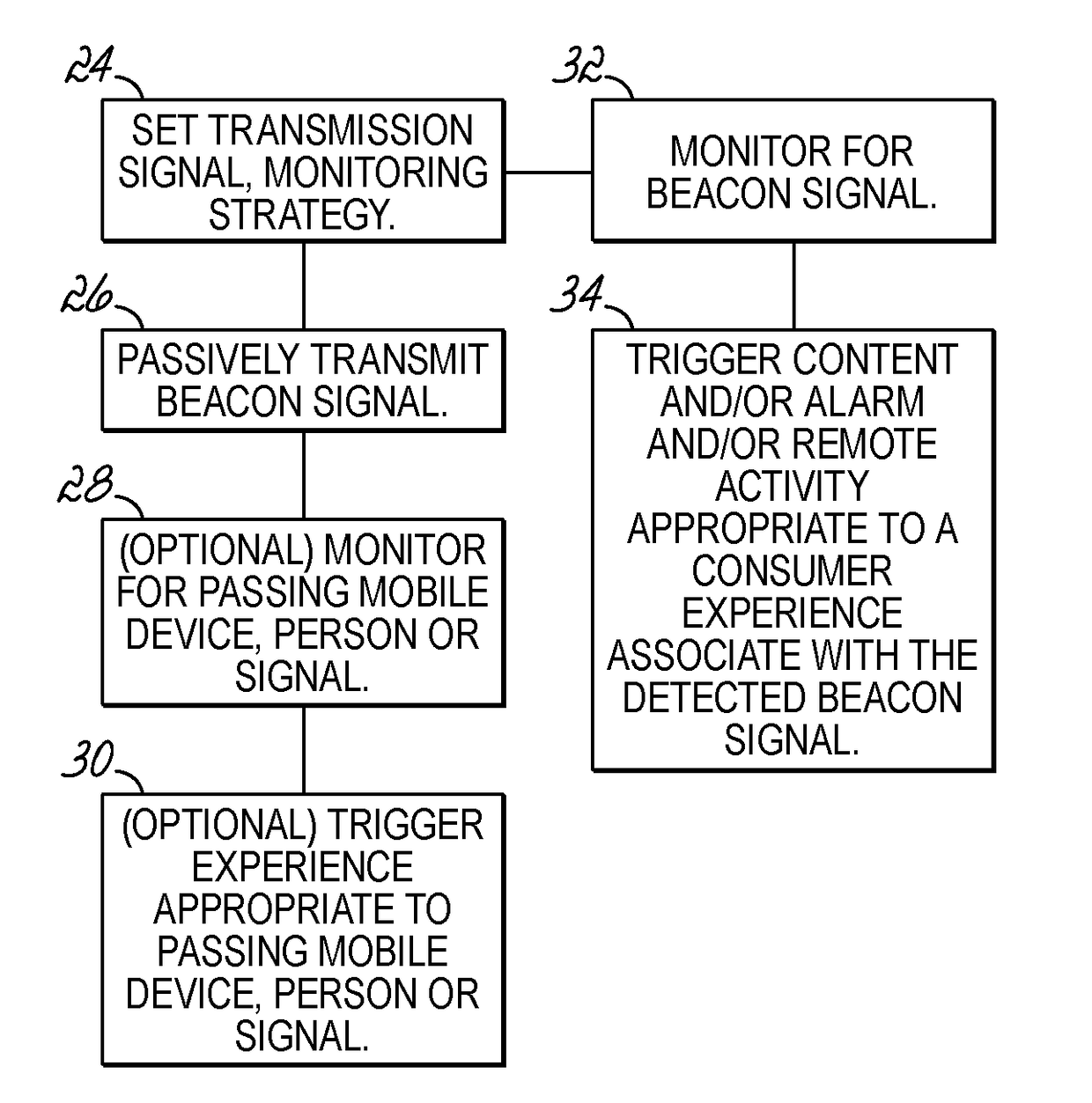
A display fixture that is enabled with location tracking systems to locate customers in a retail or trade environment and provide a more holistic experience for the customer that works through, rather than in competition, with the customer's mobile device. An App on a customer's mobile device enables location tracking systems on the mobile device such as GPS, WiFI tracking, Bluetooth Low Energy (BLE), in order to locate the customer within a retail or trade environment while the App is operational. Display fixtures are equipped with beacon devices to aid in the identification of the location of the customer mobile device relative to the display fixture. Proximity of the customer device may cause the App to deliver an experience to the customer via the mobile device and / or trigger a response in the display fixture itself.
Owner:MCRAE IMAGING
Information processing method and electronic devices
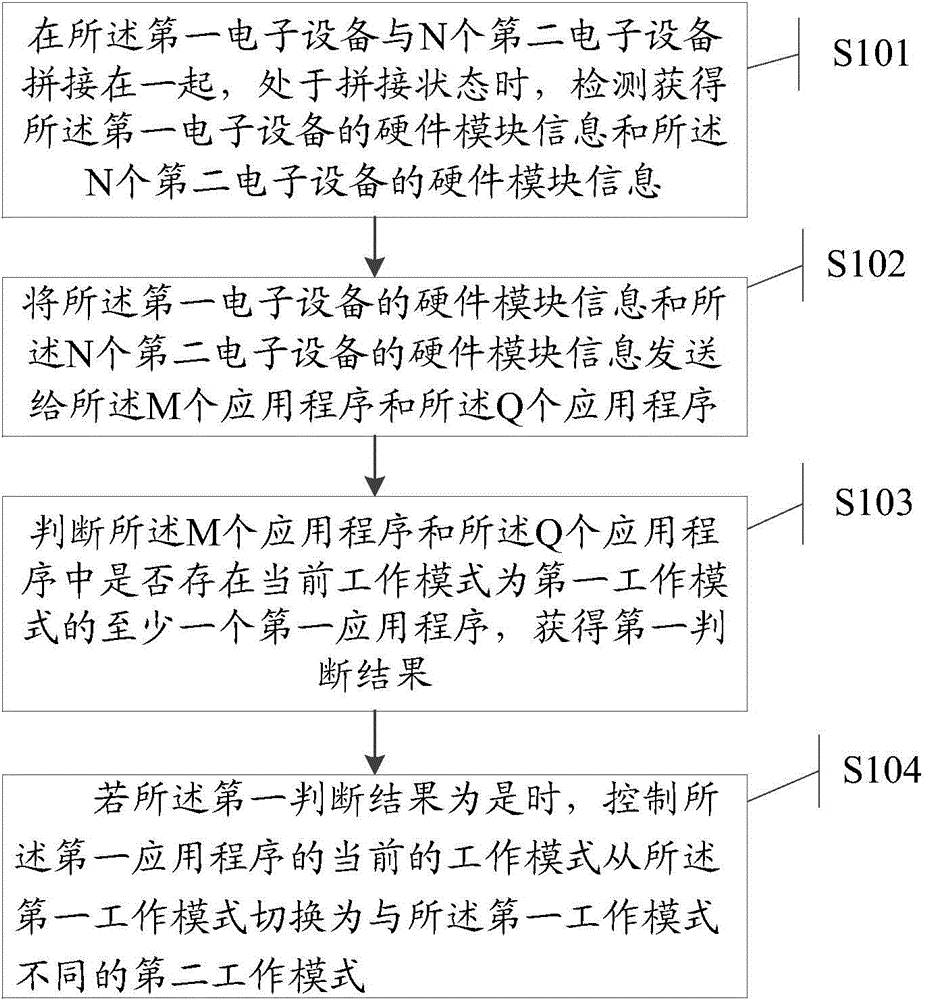
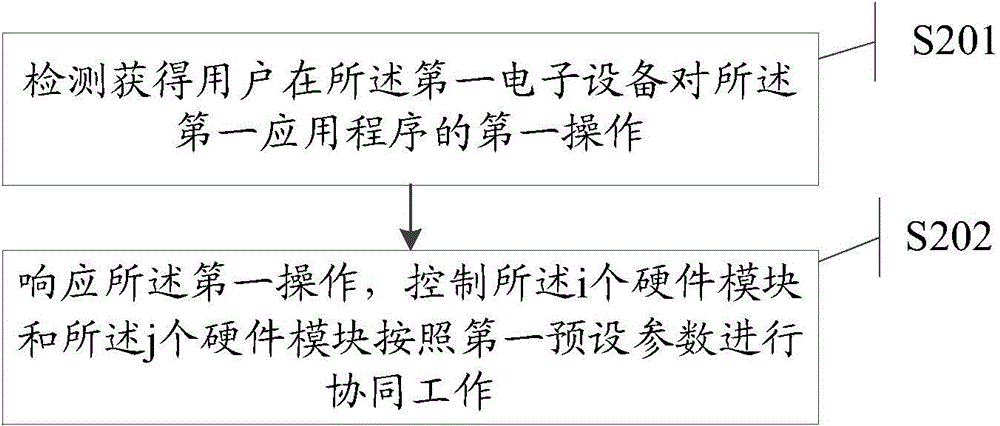
ActiveCN104536821ASolve the problem of poor experienceIncrease profitProgram initiation/switchingInformation processingComputer module
The invention discloses an information processing method and electronic devices. The information processing method is applied to the first electronic device. When the first electronic device is in a splicing state, hardware module information of the first electronic device and hardware module information of the N second electronic devices are obtained through detection, whether a first application program in a first working mode is installed in the first electronic device and the N second electronic devices is judged, and the current working mode of the first application program is controlled to be switched from the first working mode to a second working mode different from the first working mode. The method is used for solving the technical problems that after electronic devices are spliced in the prior art, configuration situations in the spliced electronic devices cannot be obtained actively and control over switching of working modes of application programs cannot be conducted actively, thereby achieving the technical advantages that after the electronic devices are spliced, configuration in the spliced electronic devices is obtained actively and the application program is noticed starting the corresponding working mode.
Owner:LENOVO (BEIJING) CO LTD
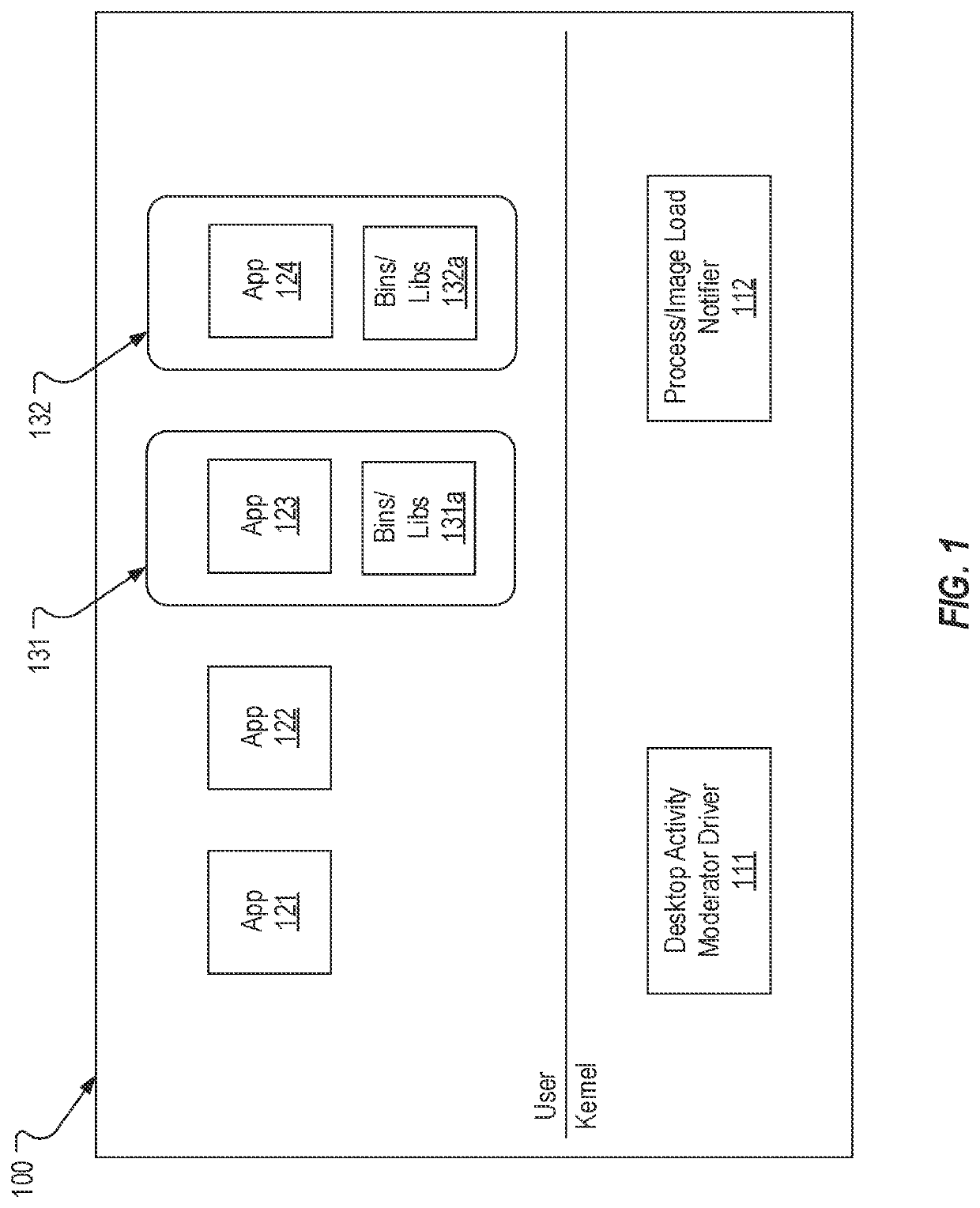
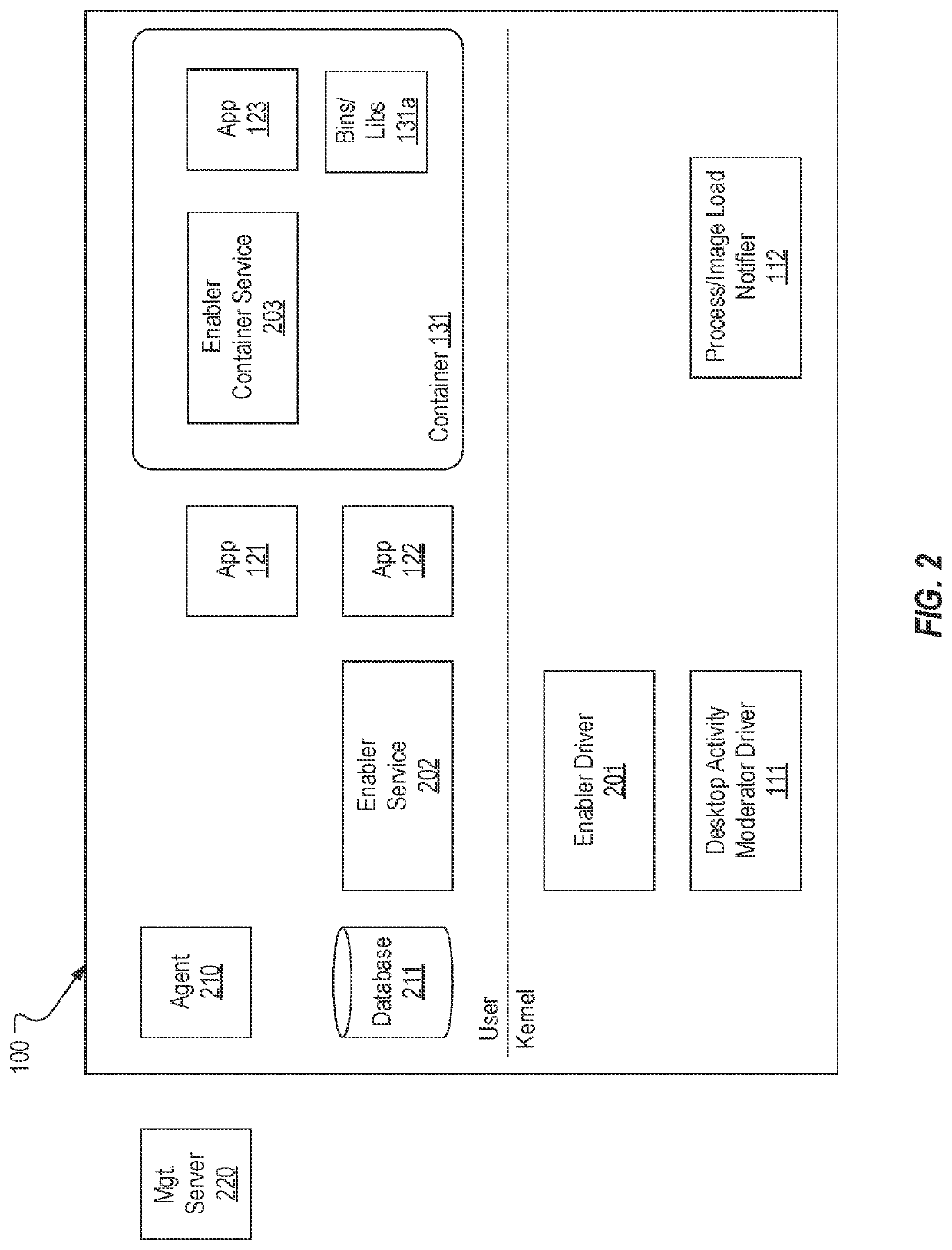
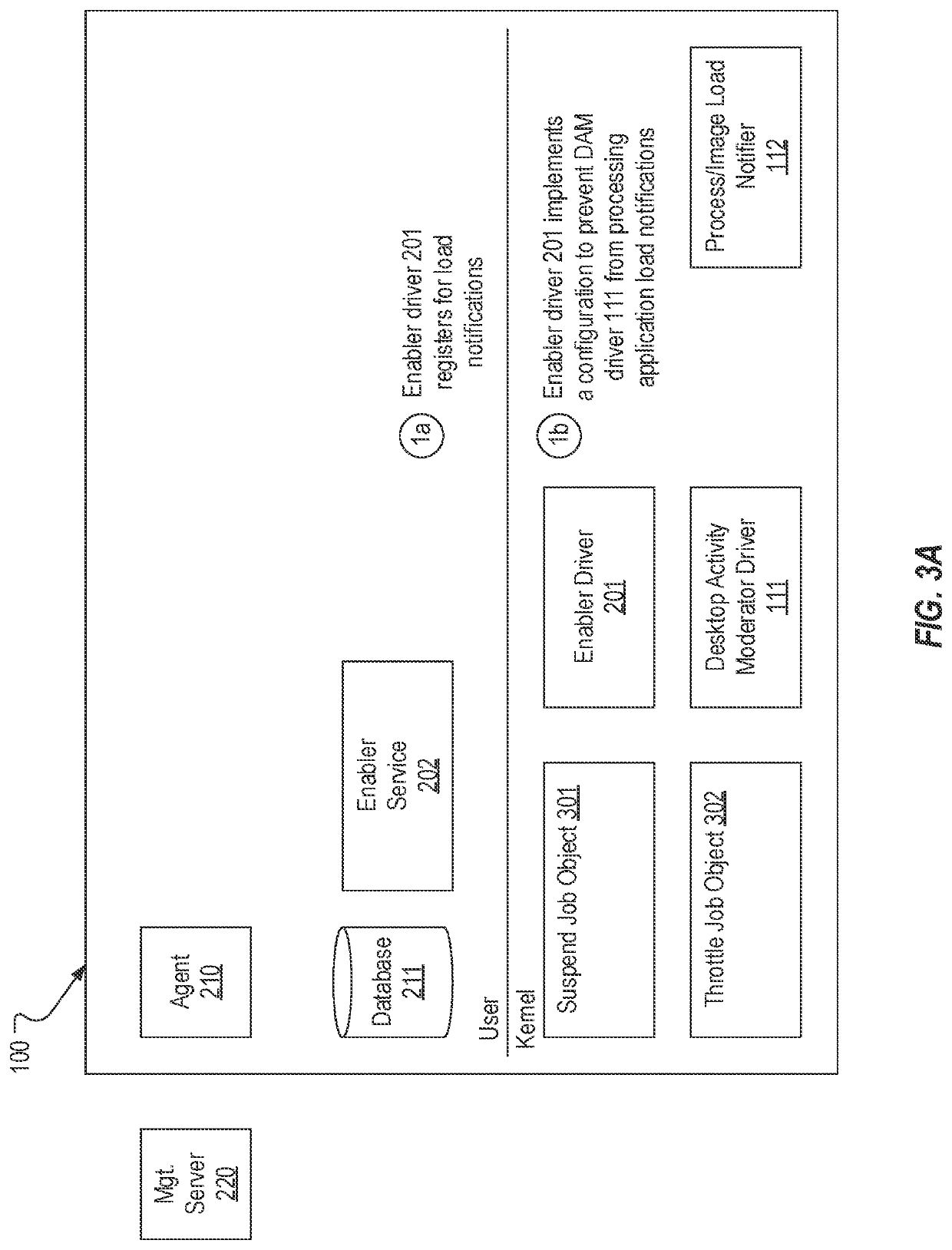
Enabling modern standby for unsupported applications
PendingUS20220283848A1Well formedProgram initiation/switchingResource allocationApplication enablementOperating system
Modern Standby is enabled for unsupported applications. An enabler driver can be included on a system that supports Modern Standby and can be configured to detect when applications are loaded on the system. When an unsupported application is loaded, the enabler driver can interface with an enabler service to determine whether the unsupported application is Modern Standby capable. If so, the enabler driver can add the unsupported application to a throttle job object that the operating system uses to determine which applications should remain active during Modern Standby. In instances where an application is deployed in a container, an enabler container service can be leveraged to determine whether the containerized application is Modern Standby capable. If so, the enabler driver can add the container to the throttle job object.
Owner:DELL PROD LP
Network Information Delivery towards Application at Device Side
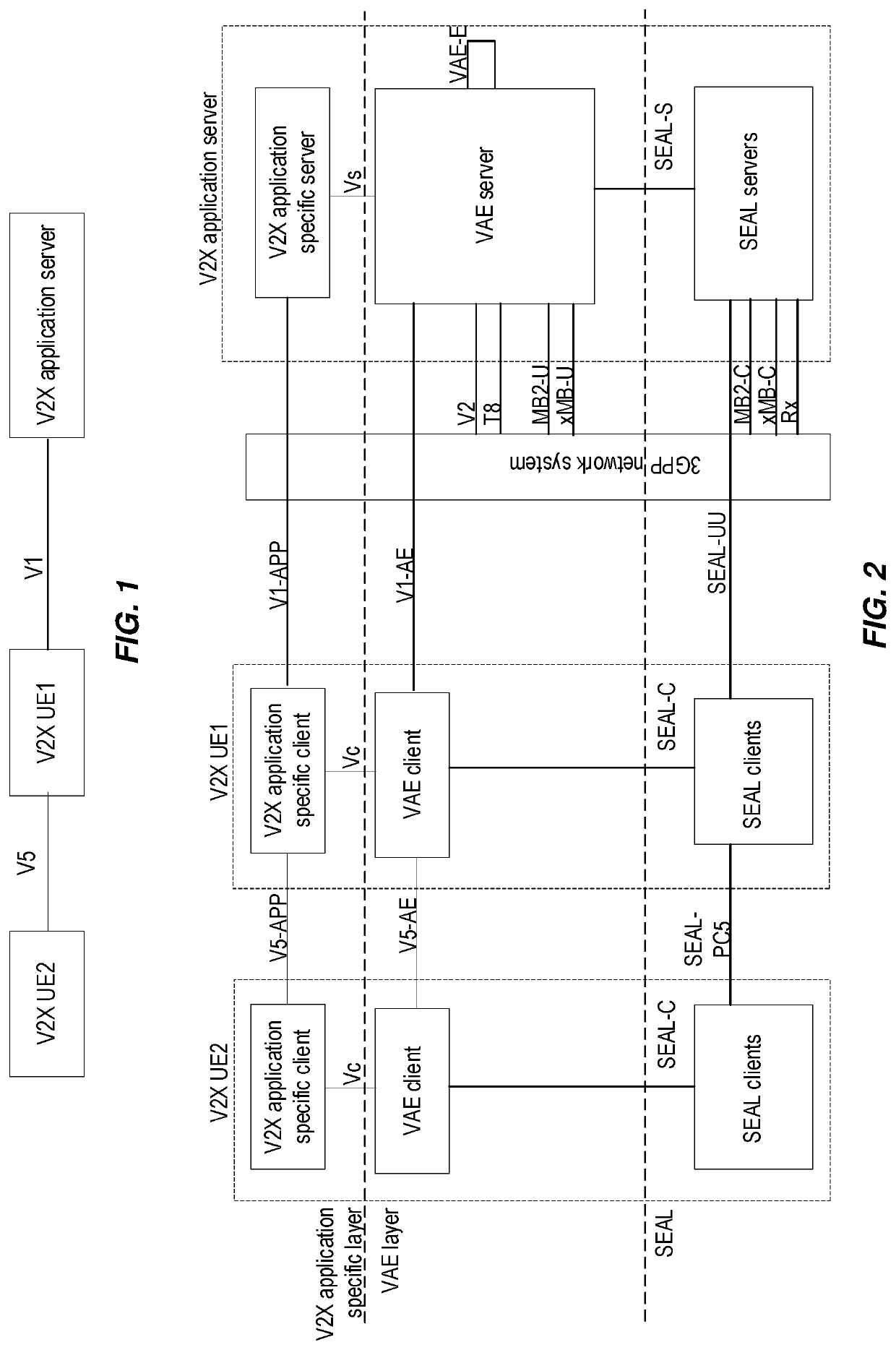
PendingUS20220329994A1Particular environment based servicesTransmissionApplication serverEngineering
A V2X UE (e.g., wireless device) that includes a vehicle-to-everything (V2X) application enabler (VAE) client and a V2X application-specific client associated with a V2X application, where the V2X UE is connected with a V2X application server is enabled to receive notifications of conditions occurring in a wireless network that connects them. The V2X application-specific client in the UE performing a registration with the V2X application server for receiving notifications. The registration comprises one or more conditions monitored by a network function (NF) in the wireless network. For example, the condition can be related to QoS provided by the network in a particular geographic area and / or in a particular time window, where the NF can be a network data and analytics function (NWDAF). The VAE client receives from the VAE server the notifications. The VAE client can receive a notification of a particular occurrence of the condition after the NF monitoring detects the occurrence.
Owner:TELEFON AB LM ERICSSON (PUBL)
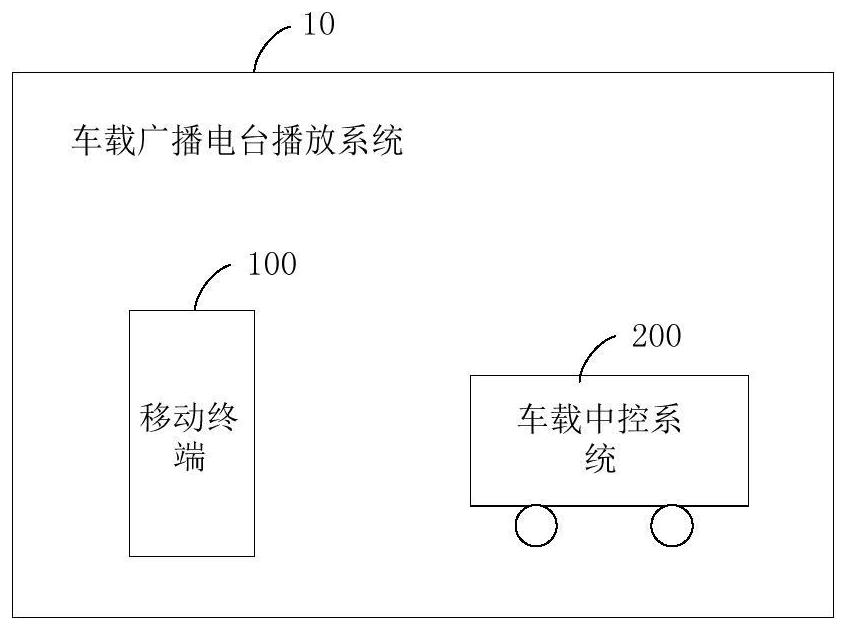
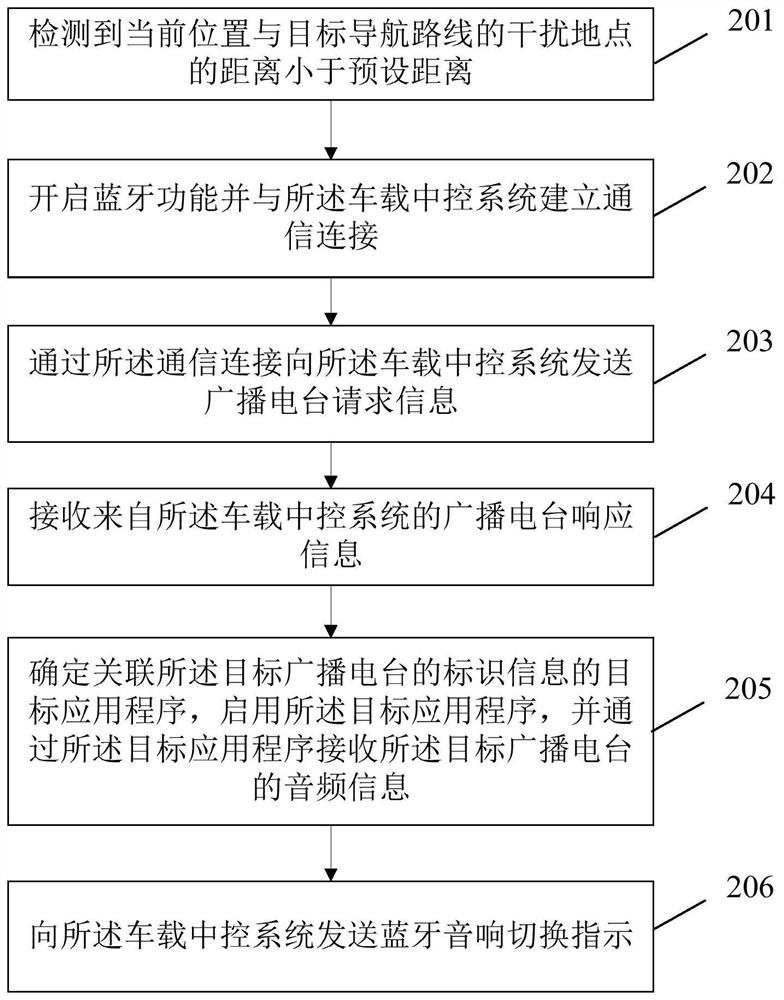
Control method of vehicle-mounted broadcasting station in interference scene and related device
ActiveCN113014343ABroadcast specific applicationsShort range communication serviceInterference (communication)In vehicle
The invention provides a control method of a vehicle-mounted broadcasting station in an interference scene and a related device. The method comprises the following steps: detecting that the distance between a current position and an interference site of a target navigation route is smaller than a preset distance; starting a Bluetooth function and establishing communication connection with a vehicle-mounted central control system; broadcasting station request information is sent to the vehicle-mounted central control system through the communication connection; receiving the broadcast station response information from the vehicle-mounted central control system; determining a target application program associated with the identification information of the target broadcasting station, starting the target application program, and receiving audio information of the target broadcasting station through the target application program; and sending a Bluetooth sound equipment switching instruction to the vehicle-mounted central control system. According to the invention, the use continuity and intelligence of the vehicle-mounted broadcasting station can be improved, and the user experience is improved.
Owner:深圳市广峰科技有限公司
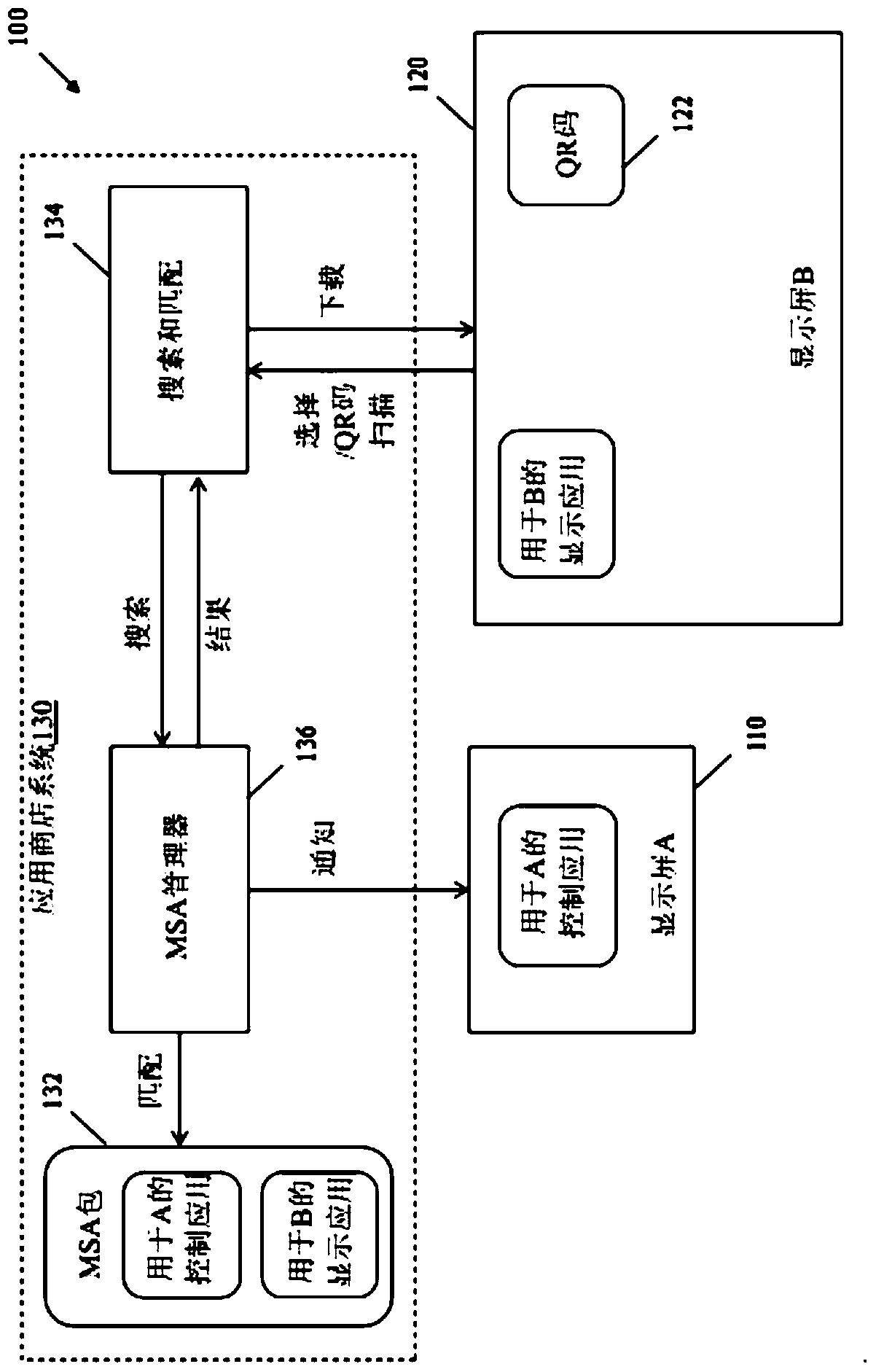
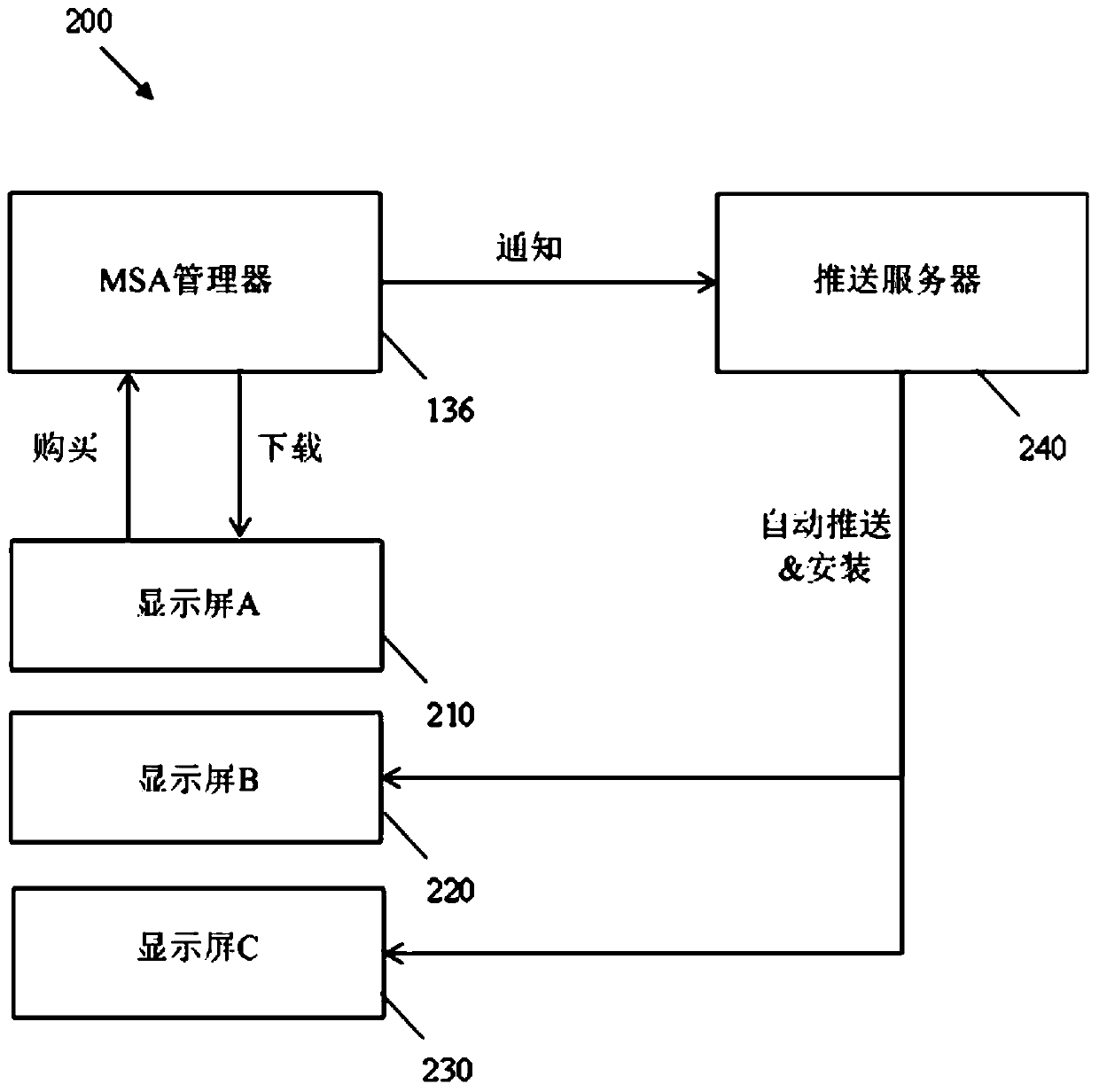
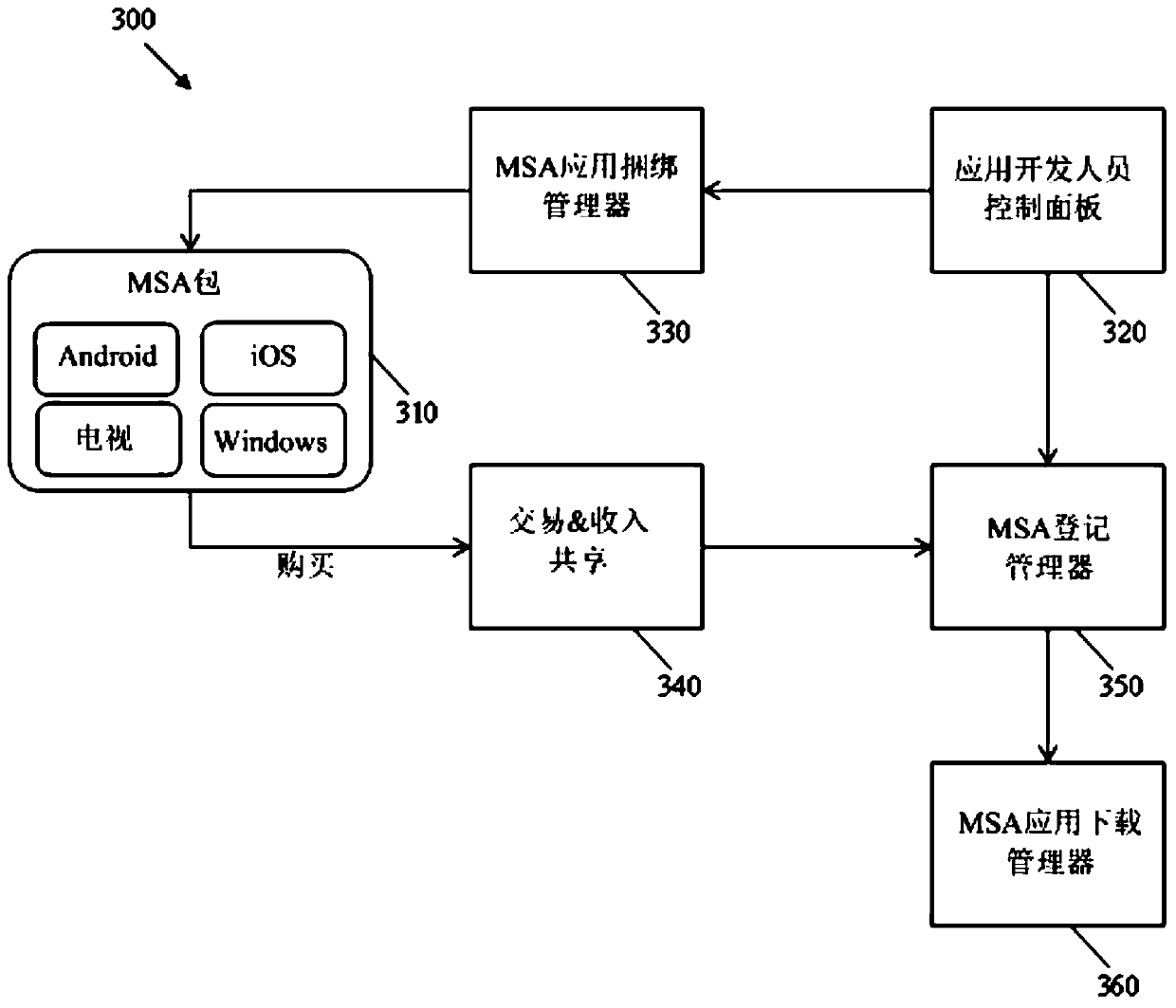
Multi-screen application enablement and distribution service
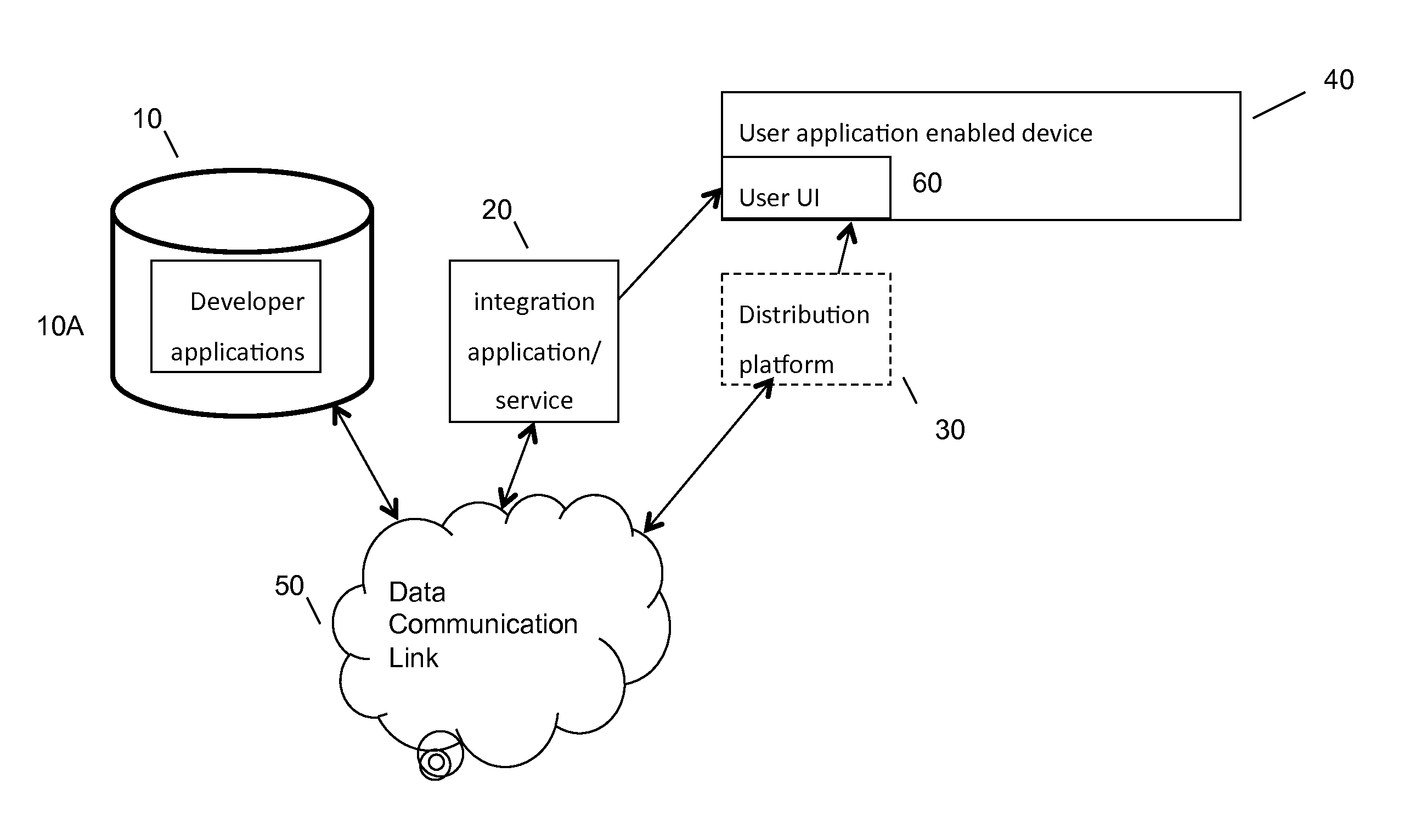
A method implemented by an application (app) store system for providing applications over a network to one or more users, the method comprising the application store system managing a multi-screen application (MSA) package containing a set of related applications, wherein one or more relationships between the set of related applications are predefined; the application store system receives a request from a first user device over the network to download at least a portion of the MSA package; and the application The store system causes the set of related applications to be downloaded to a plurality of user devices including the first user device in response to the request based on the one or more relationships between the set of related applications.
Owner:HUAWEI TECH CO LTD
Method for establishing and maintaining a digital family and friends tree and adding newborn or unborn to same
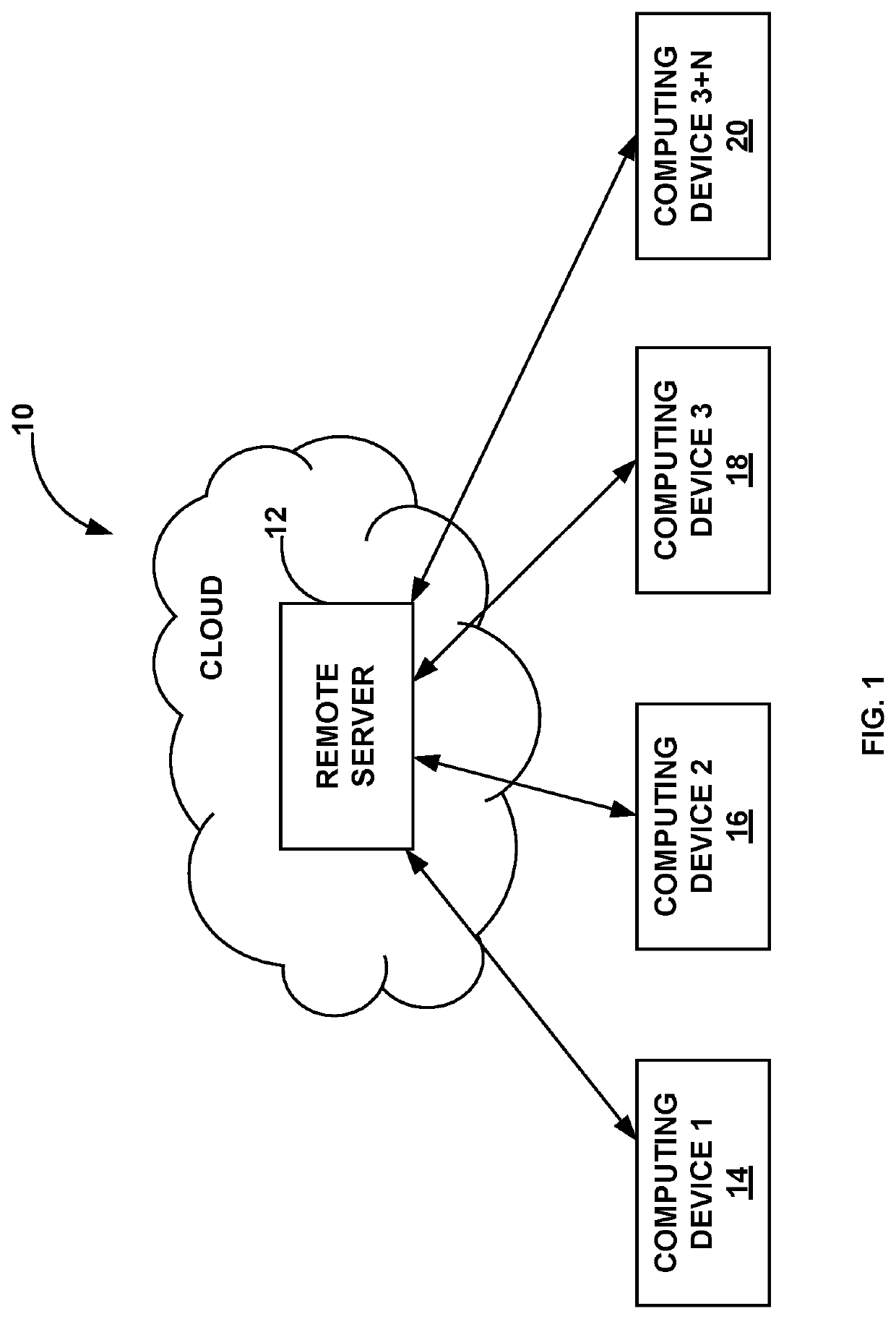
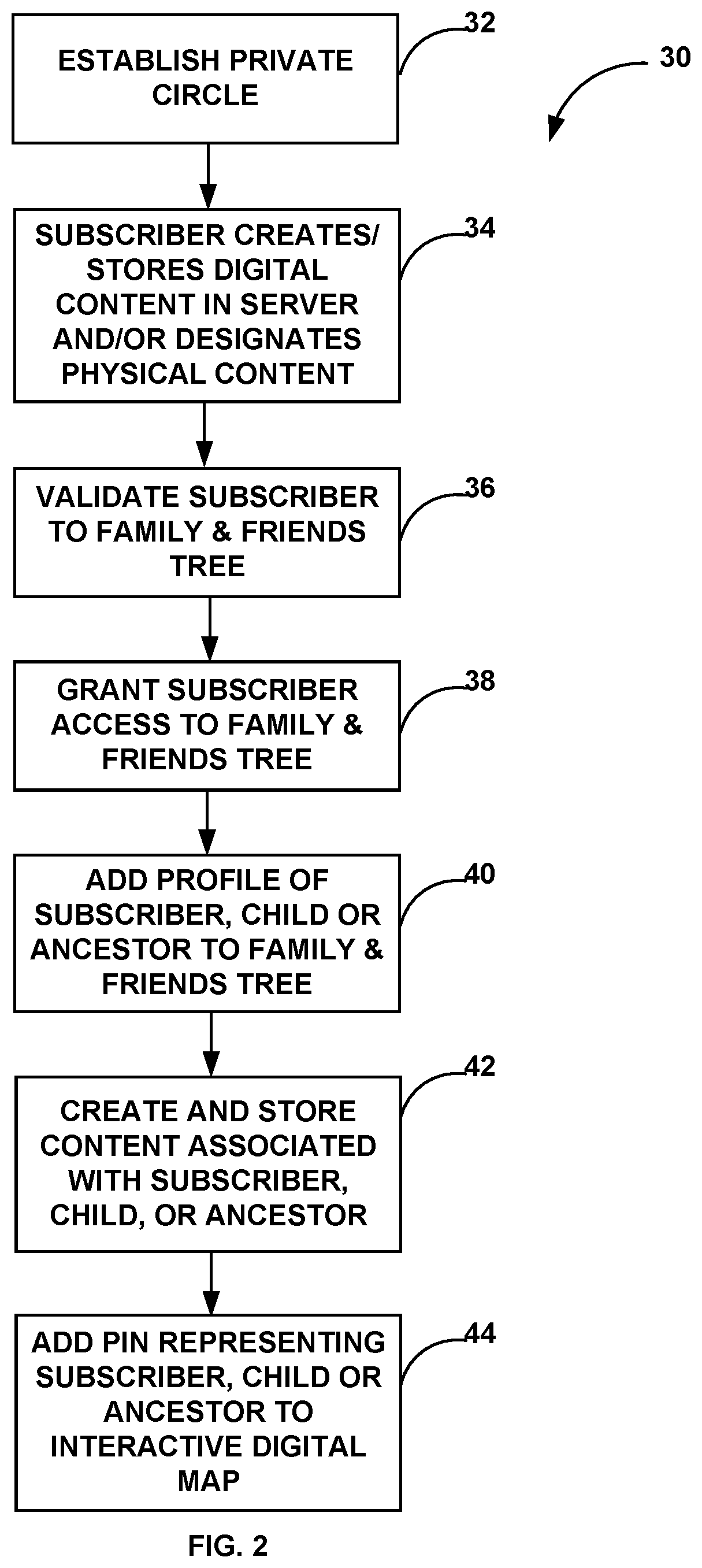
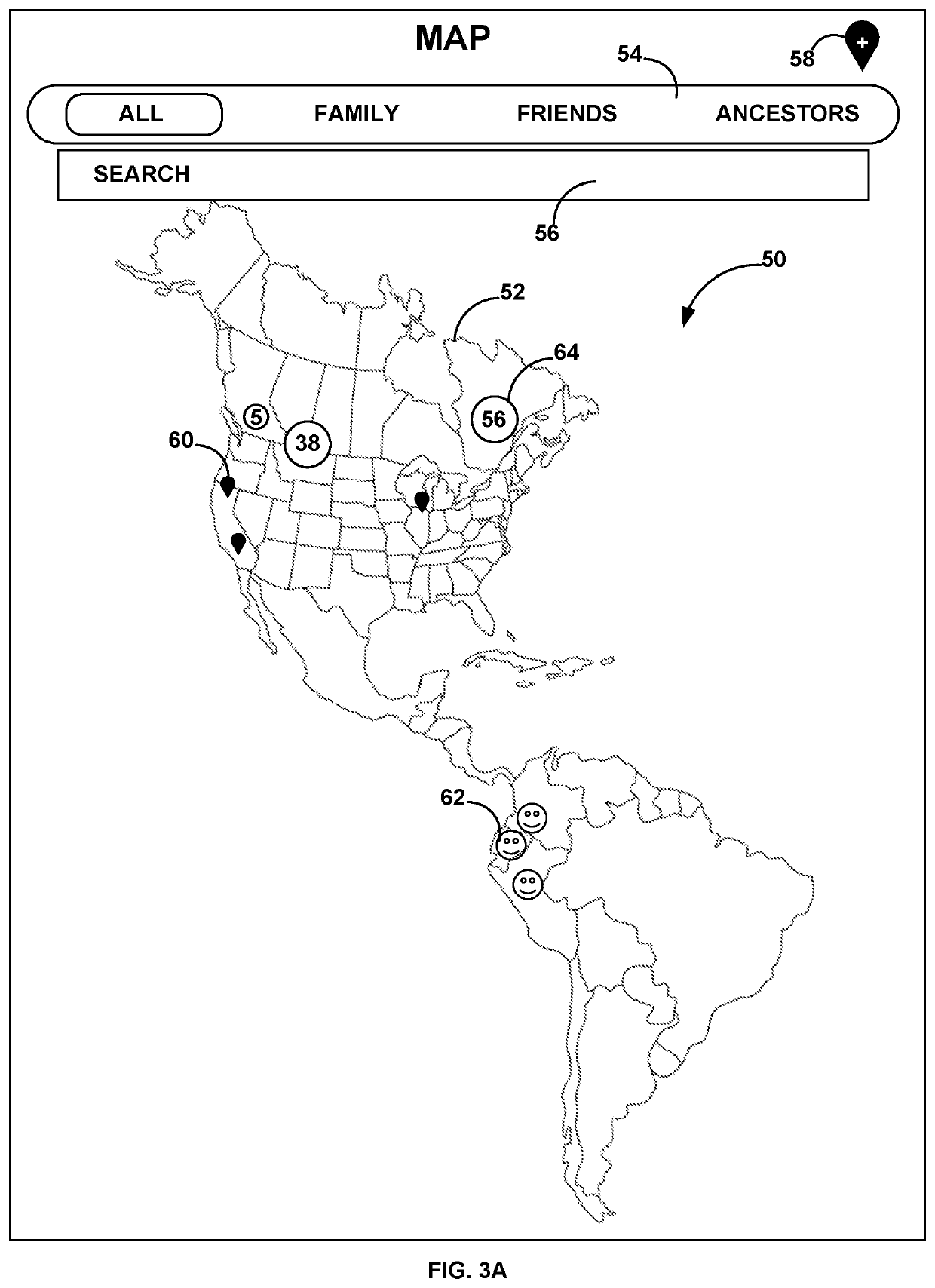
PendingUS20220122194A1Data processing applicationsData switching networksEngineeringApplication enablement
The present web-based system and methods enabled by an application executable on a computing device of the system allow subscribers to develop a private circle and interactive family & friends tree within a private social network, adding a newborn or unborn person to same, and scheduling delivery of selected content to a designated recipient, either on a future date or upon occurrence of a future event having a date unknown to the subscriber. The system may determine a delivery date for the selected content, even if no date is specified by the subscriber, based on data obtained from other subscribers to the private circle and / or machine learning analysis, and may validate the delivery date before delivering the content.
Owner:CIRCLEIT LLC
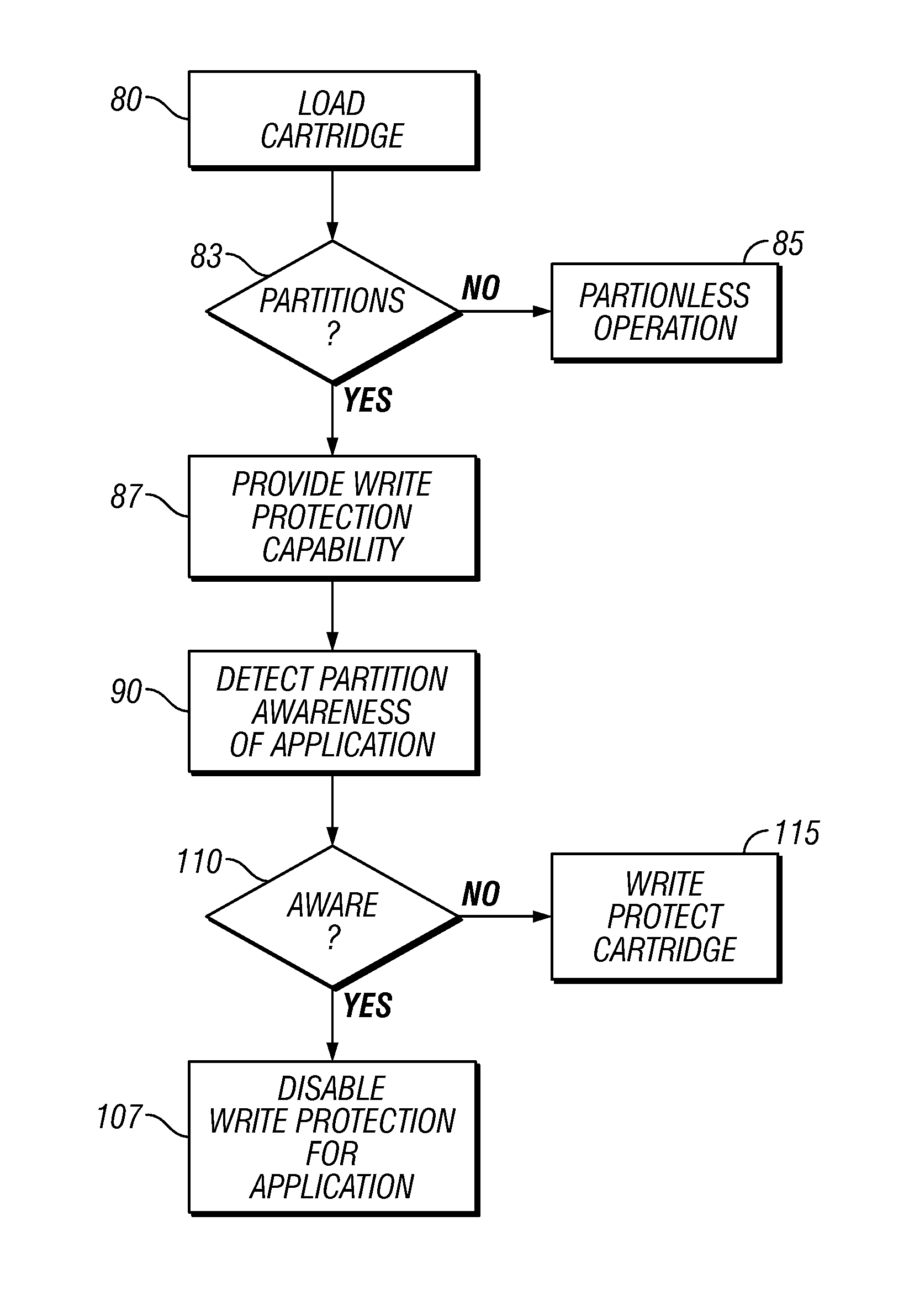
Control of logical write protection of rewritable data storage cartridge
InactiveUS8612709B2Input/output to record carriersElectronic editing digitised analogue information signalsWrite protectionApplication enablement
Write protection for data of a rewritable data storage cartridge having partitions is provided in certain circumstances by providing logical write protection; and in response to detection of an application issuing at least one partition-based command with respect to the rewritable data storage cartridge, the logical write protection is disabled with respect to the detected application. Thus, where the cartridge has a non-default index addressing location, in response to detection of an application issuing at least one command initially addressing a location other than the non-default index location, logical write protection is enabled with respect to the detected application; and if the non-default index location is addressed, the logical write protection is disabled.
Owner:IBM CORP
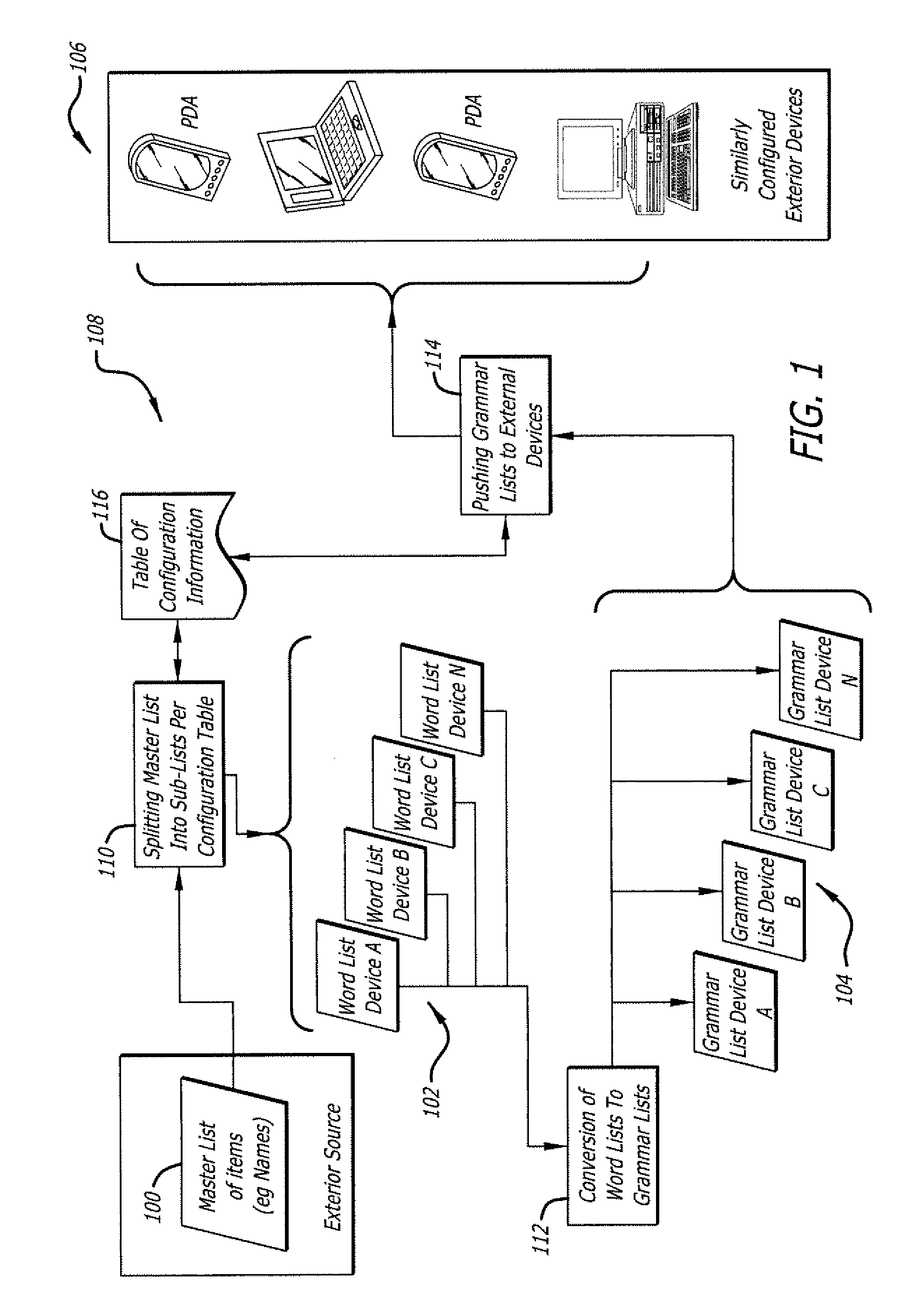
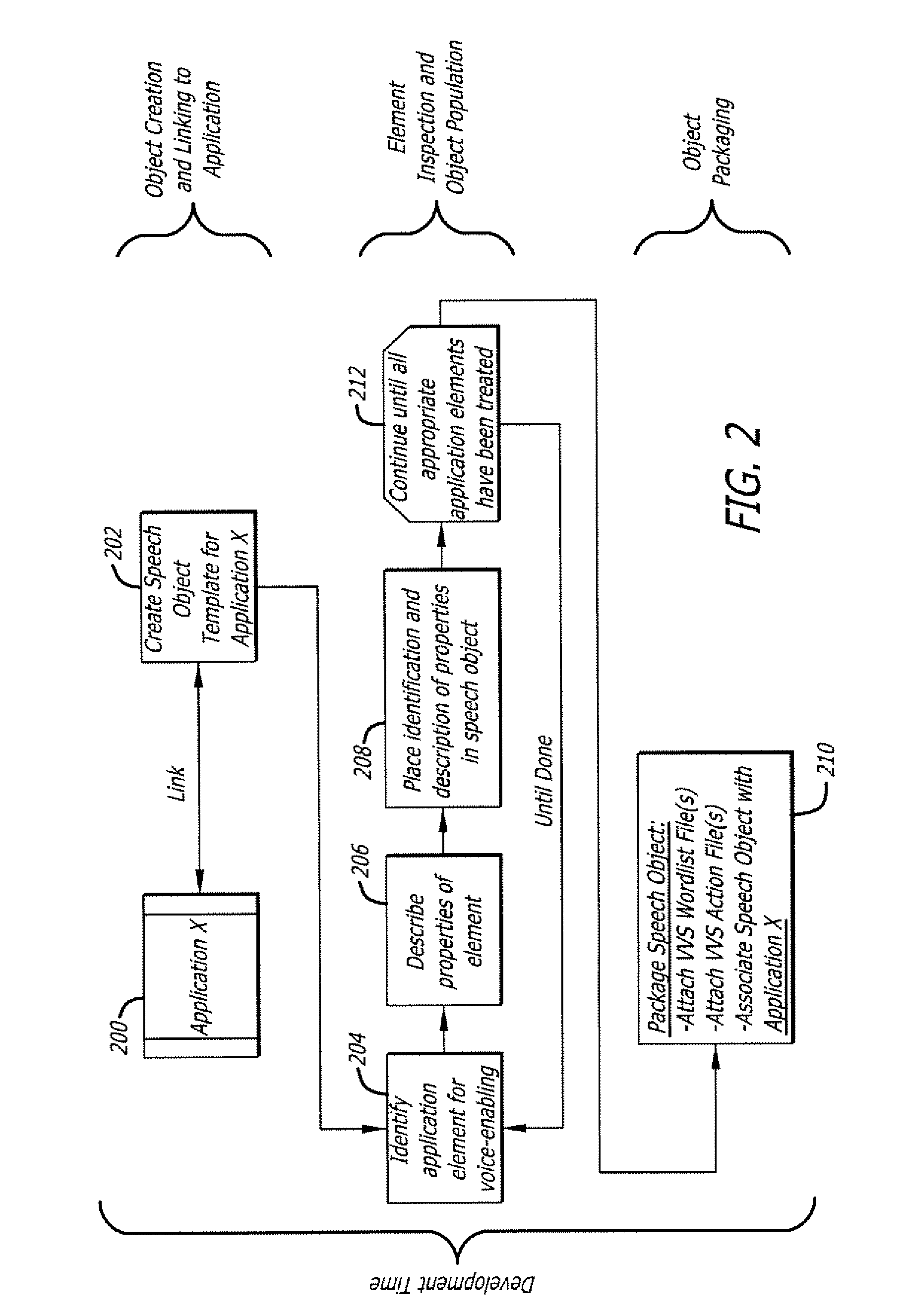
Methodology for voice enabling applications
Owner:VANGARD VOICE SYST
Method, apparatus and computer program product for enabling dual mode communication
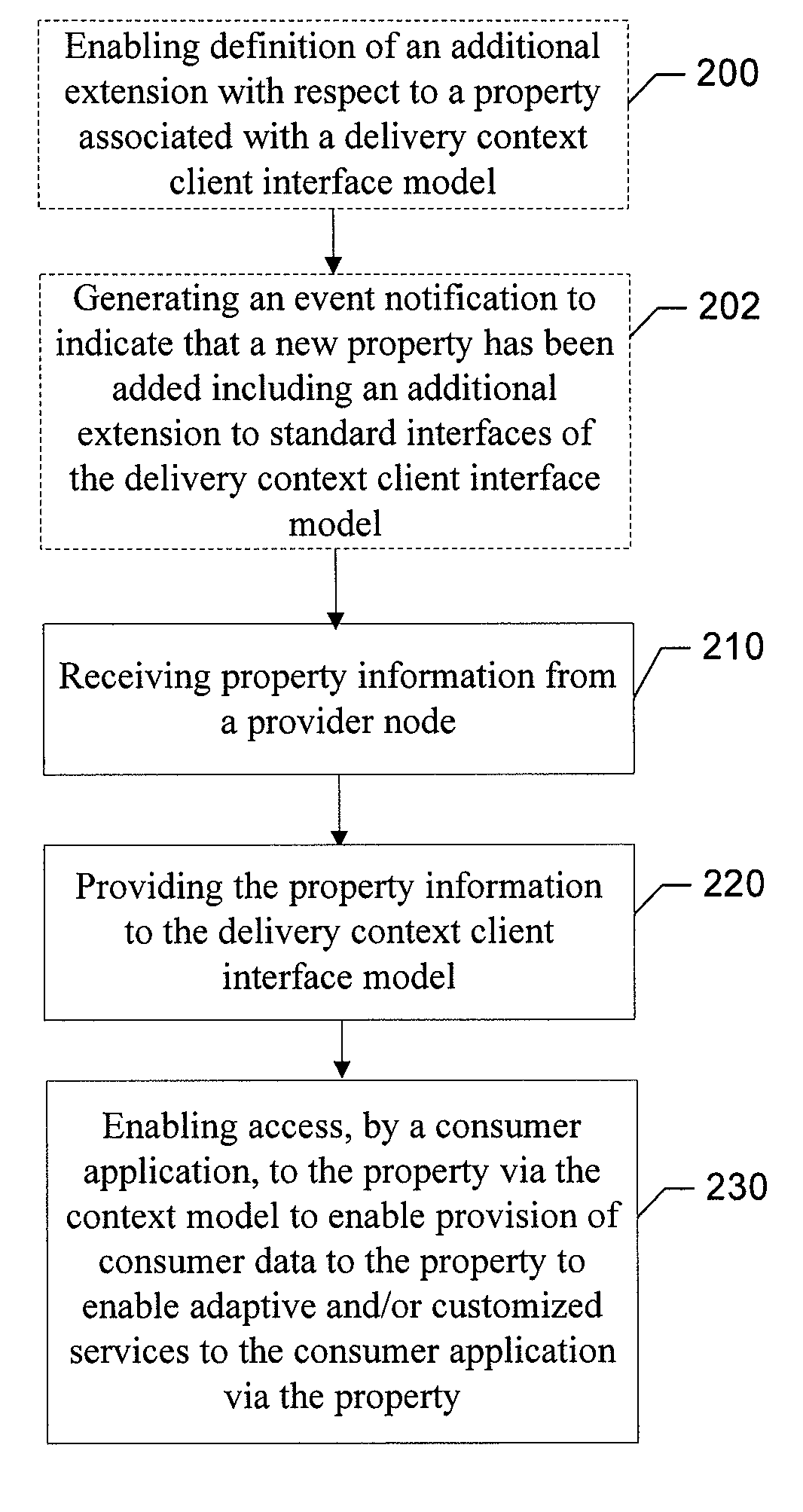
InactiveUS8010669B2Improve abilitiesMultiple digital computer combinationsSubstation equipmentDual modeContext model
An apparatus for enabling dual mode communication may include a processor. The processor may be configured to receive property information from a provider node, provide the property information to a delivery context client interface based context model, and enable access, by a consumer application, to the property via the delivery context client interface based context model to enable provision of consumer data to the property to enable adaptive or customized services to the consumer application via the property. A corresponding method and computer program product are also provided.
Owner:WSOU INVESTMENTS LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com