User authentication method and user authentication device
A user authentication, user technology, applied in the field of survival authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
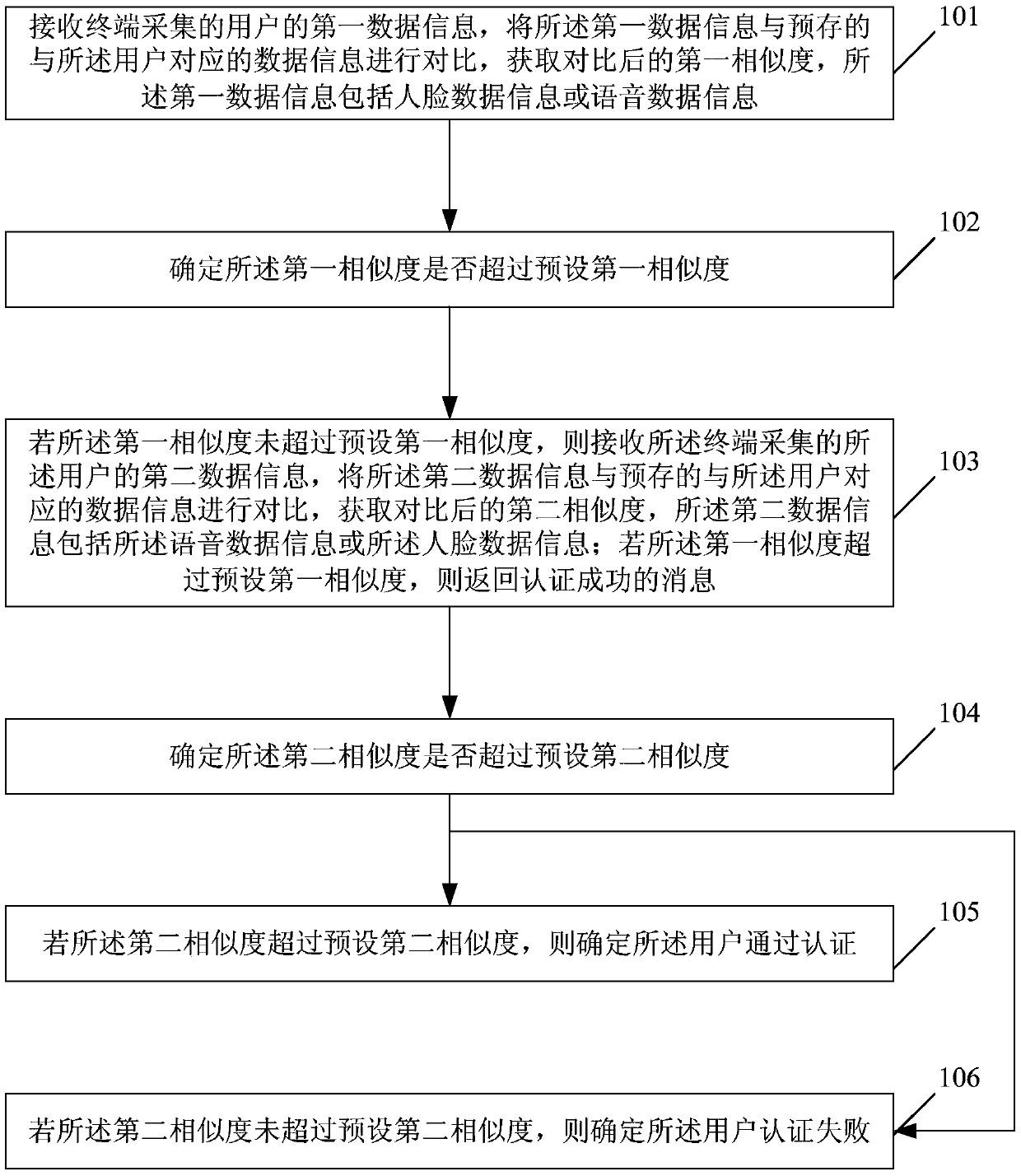
[0064] figure 1 It is a schematic flowchart of a user authentication method provided in Embodiment 1 of the present invention. The method may be performed by a user-authenticated device, wherein the device may be implemented by software and / or hardware. Such as figure 1 As shown, the method includes:
[0065] Step 101, receiving the first data information of the user collected by the terminal, comparing the first data information with the pre-stored data information corresponding to the user, and obtaining the compared first similarity, the first data information Including face data information or voice data information;
[0066] Specifically, if the first data information is face data information, the device for user authentication includes a social security personnel avatar database; a mobile device terminal with a camera for image collection; a network for data communication between the collection terminal and the background server A unit is a server used to implement a...
Embodiment 2
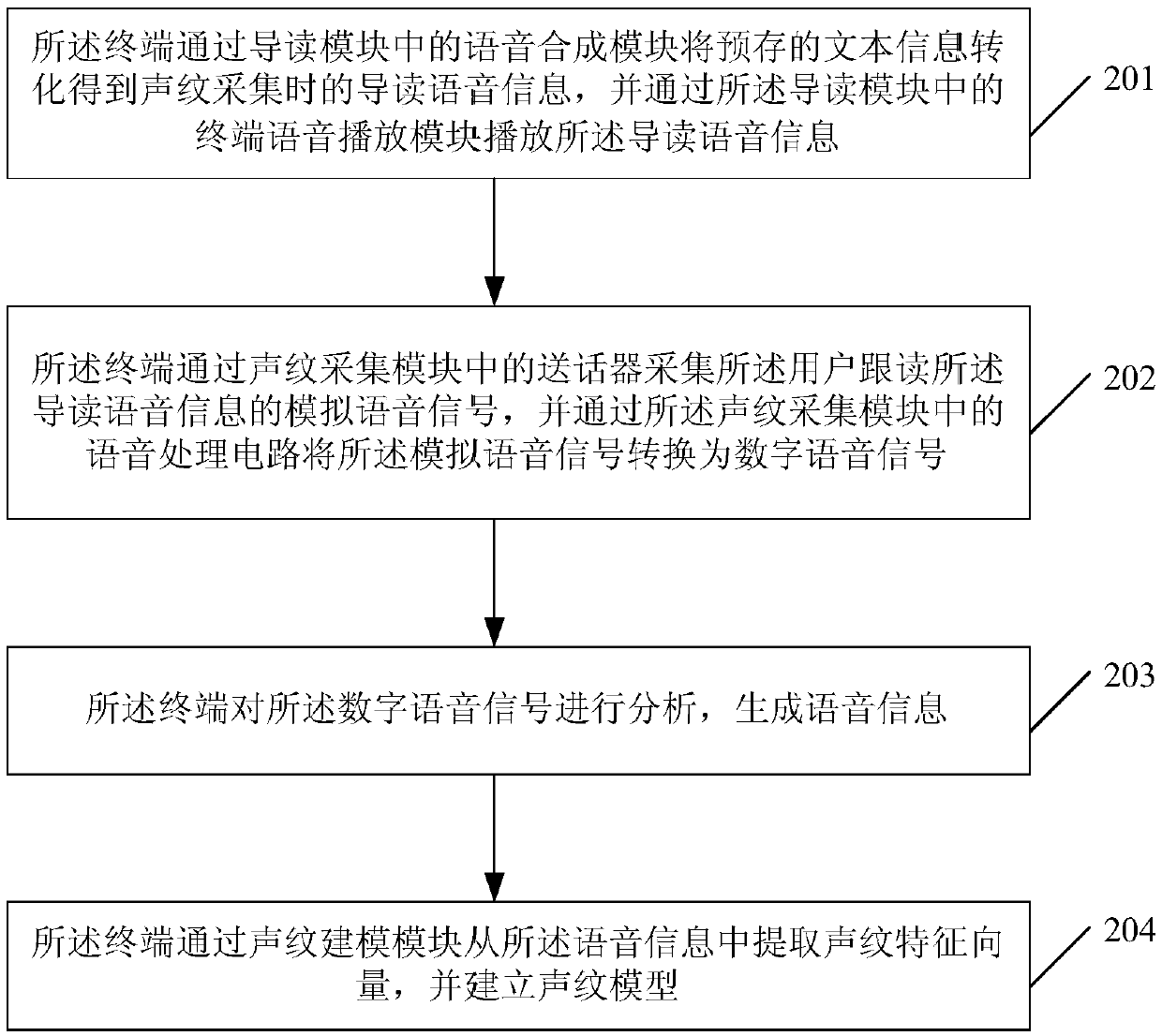
[0094] refer to figure 2 , figure 2 It is a schematic flowchart of a method for collecting voice data information by a terminal provided in Embodiment 2 of the present invention. The methods include:
[0095] Step 201, the terminal converts the pre-stored text information through the speech synthesis module in the reading guide module to obtain the reading guide voice information when the voiceprint is collected, and plays the reading guide voice information through the terminal voice playback module in the reading guide module;
[0096] Step 202, the terminal collects the analog voice signal of the user reading the guide voice information through the microphone in the voiceprint collection module, and converts the analog voice signal through the voice processing circuit in the voiceprint collection module The signal is converted into a digital voice signal;
[0097] Step 203, the terminal analyzes the digital voice signal to generate voice information;
[0098] Step 204...
Embodiment 3
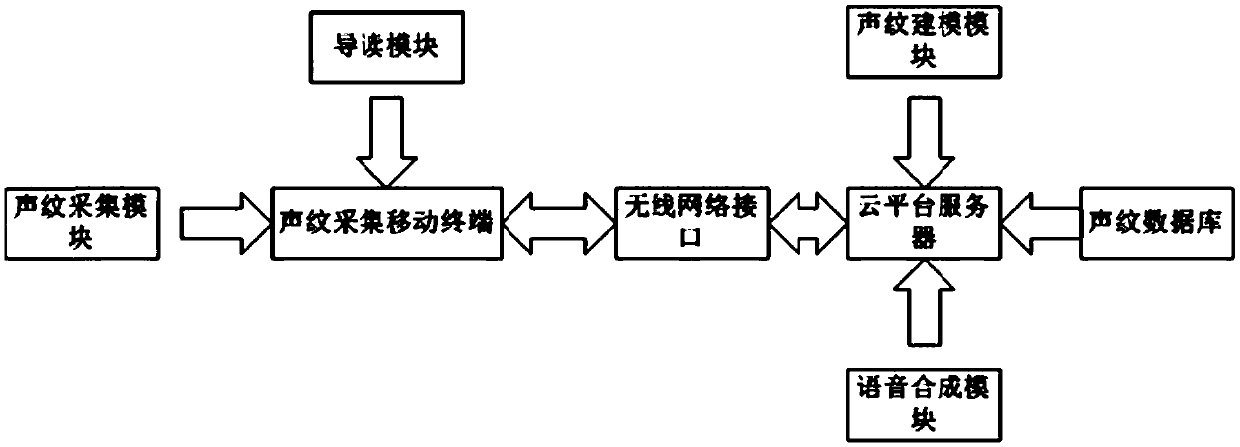
[0105] refer to Figure 5 , Figure 5 It is a schematic flowchart of a method for collecting voice data information by a terminal provided in Embodiment 3 of the present invention. The methods include:
[0106] Step 501, the terminal obtains the basic information of the user, the basic information includes the user's name, ID number and / or mobile phone number;
[0107] Step 502, the terminal queries the background server for the corresponding pre-stored user unique identifier according to the basic information of the user;
[0108] Step 503, the terminal binds the unique user identifier and the first data information, and sends the bound first data information to the background server.
[0109] Specifically, in the process of voice authentication, the basic information entered by the insured person or the basic user information obtained from the social security database generates a unique ID number in the database as the unique identification of the insured person. The voic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com