Method and device for blocking botnet control channel based on SDN (Software Defined Network) technology
A botnet and control channel technology, applied in the field of software-defined network security, can solve problems such as high operating pressure of cleaning equipment and large attack traffic
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
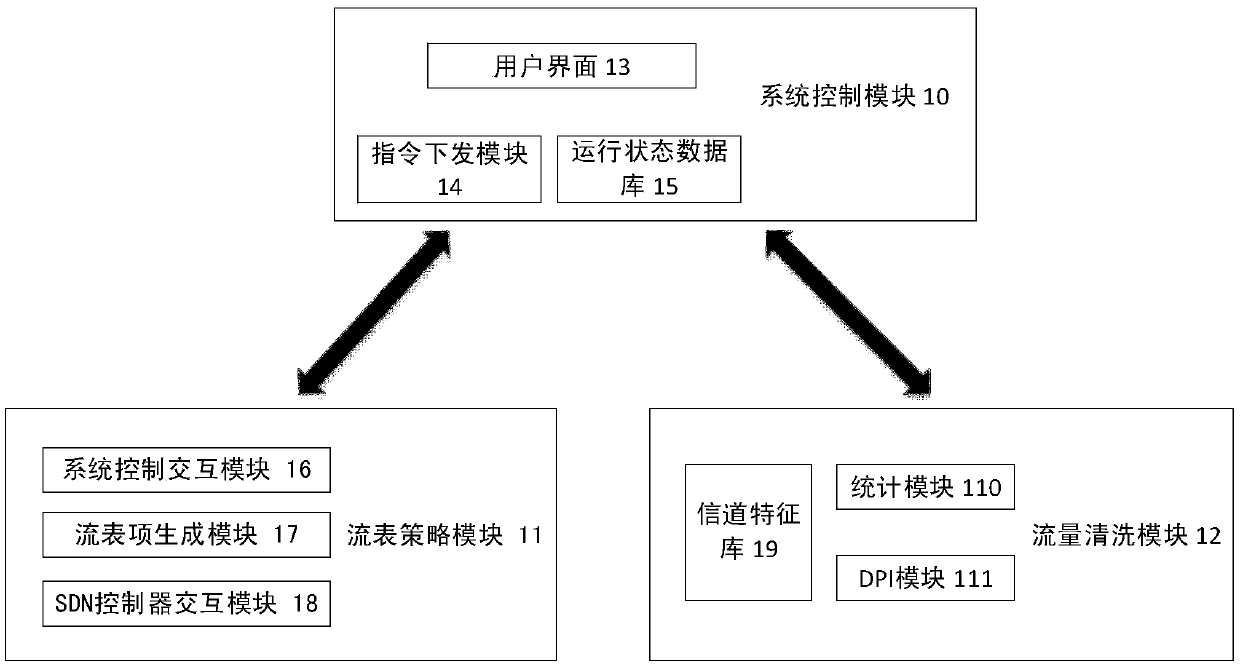
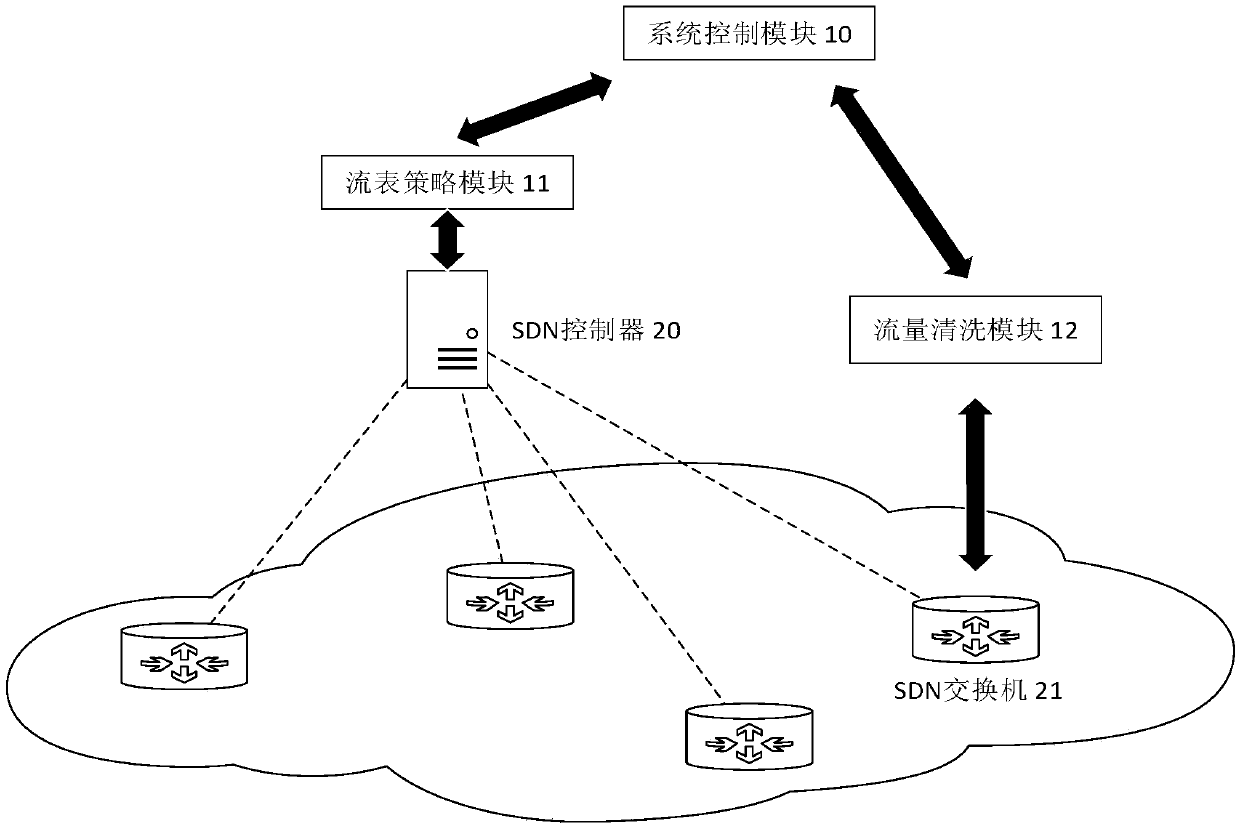
[0035] like figure 1 As shown, the device for blocking the control channel of a botnet based on SDN technology is composed of a system control module 10, a flow table policy module 11, and a traffic cleaning module 12. The specific deployment positions are as follows: figure 2 shown.
[0036] The system control module 10 can run independently on a dedicated server, or it can be deployed on the same server as the flow table policy module 11 or the traffic cleaning module 12. Users can access the WEB page provided by the system control module 10 through the HTTP protocol to realize key parameters. Configure, view the current system running status and other operations. The system control module 10 communicates with the flow table policy module 11 and the traffic cleaning module 12 through socket connections, so as to realize the delivery of system instructions and characteristic parameters and the upload of operating state parameters.
[0037] In addition to communicating with...
Embodiment 3
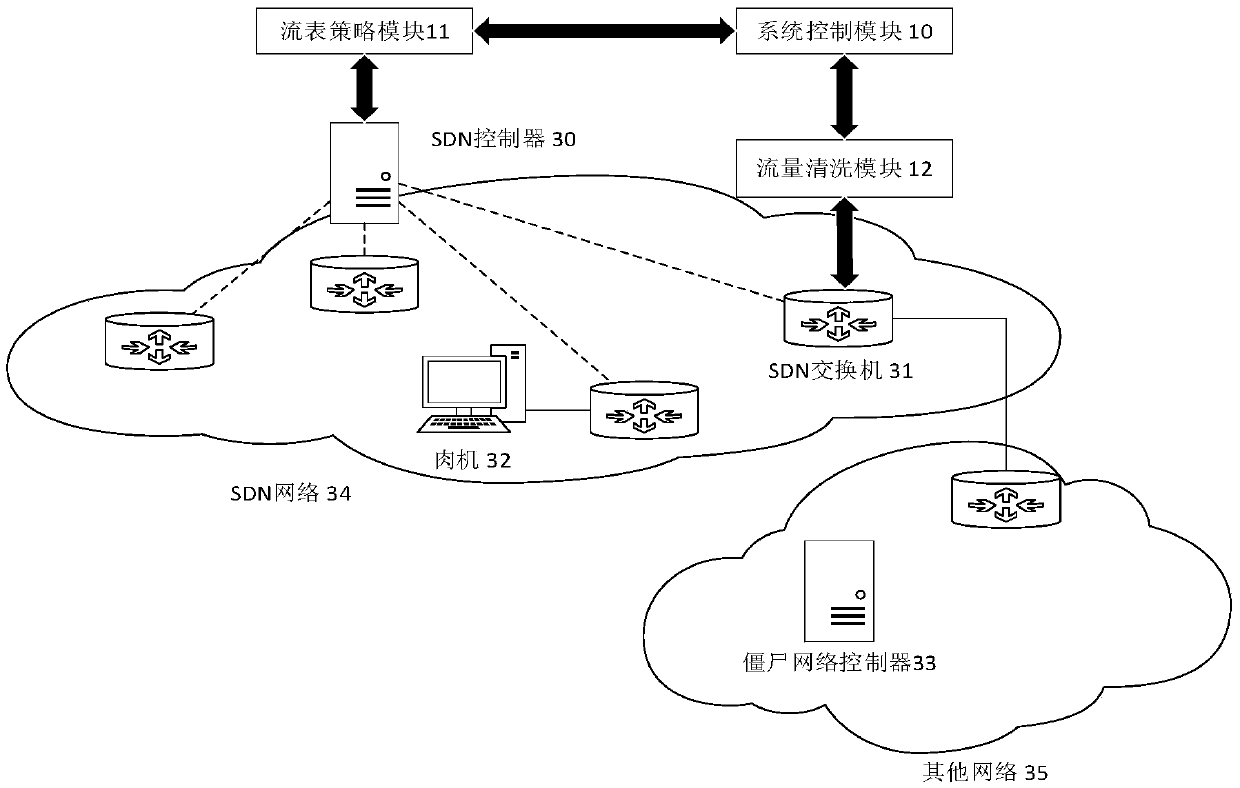
[0040] like image 3 As shown, for a botnet where the bot 32 is within the range of the SDN network 34 and the botnet controller 33 is in other networks 35, under normal circumstances the infected bot 32 can join the control channel of the botnet controller 33, upload user information and Receive instructions from the botnet controller.
[0041] When the system control module 10 , the flow table policy module 11 , and the traffic cleaning module 12 are connected and started, the user completes the configuration through the system control module 10 . The flow table policy module 11 sends the flow table for redirection to the SDN switch in the SDN network 34 through the SDN controller 30 . When the bot 32 sends a message to the botnet controller 33, because the network layer and transport layer characteristics of the message are consistent with those in the redirection flow table, the message will be redirected to the traffic cleaning module 12, and the traffic cleaning module ...
Embodiment 4
[0043] like Figure 4 As shown, for both the bot 42 and the botnet controller 43 are within the range of the SDN network 44, under normal circumstances the infected bot 42 can join the control channel of the botnet controller 43, upload user information and receive information from the botnet controller instructions.
[0044] When the system control module 10 , the flow table policy module 11 , and the traffic cleaning module 12 are connected and started, the user completes the configuration through the system control module 10 . The flow table policy module 11 sends the flow table for redirection to the SDN switch in the SDN network 46 through the SDN controller 40 . When the bot 45 sends a message to the botnet controller 44, since the network layer and transport layer characteristics of the message are consistent with those in the redirection flow table, the message will be redirected to the traffic cleaning module 12, and the traffic cleaning module 12 uses the depth The...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com