Quantum key distribution, privacy amplification and data transmission methods, apparatuses, and system
一种量子密钥分发、隐私放大的技术,应用在基于量子密钥的数据传输系统,量子密钥分发领域,能够解决量子密钥分发过程存在、安全隐患等问题
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0136] In the following description, numerous specific details are set forth in order to provide a thorough understanding of the application. However, the present application can be implemented in many other ways different from those described here, and those skilled in the art can make similar promotions without violating the connotation of the present application. Therefore, the present application is not limited by the specific implementation disclosed below.
[0137] In this application, a quantum key distribution method and device, a privacy amplification method and device for the quantum key distribution process, a quantum key-based data transmission method, and a quantum key-based Keyed data transfer system. Each will be described in detail in the following examples.
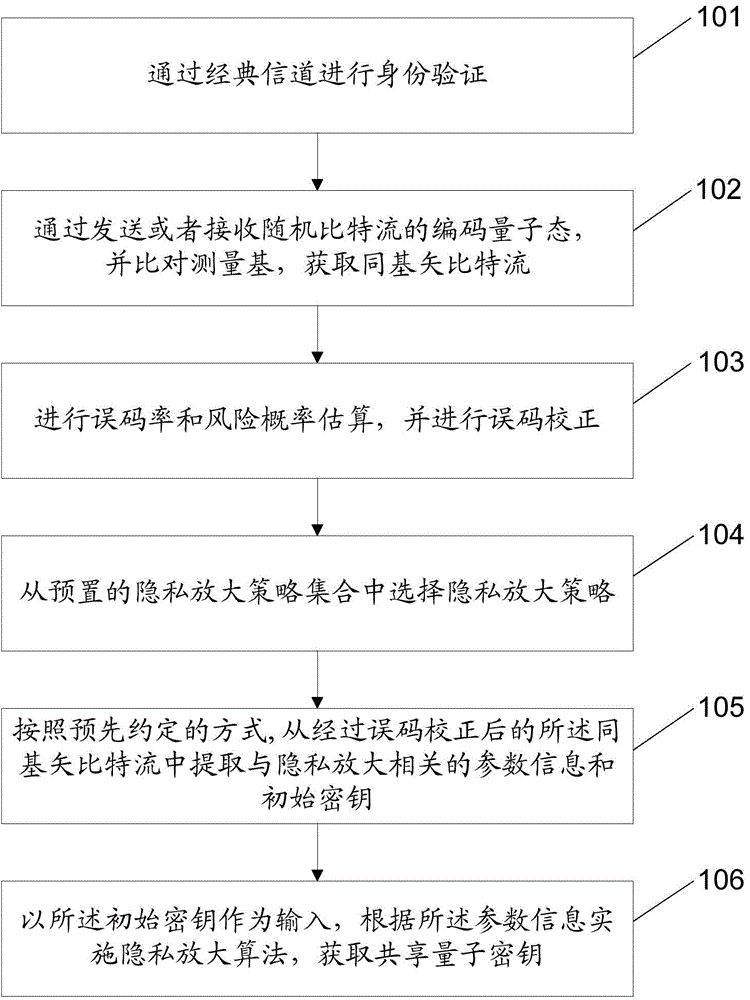
[0138] Please refer to figure 1 , which is a flowchart of an embodiment of a quantum key distribution method of the present application. The method comprises the steps of:
[0139] Step 101: Perform i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com