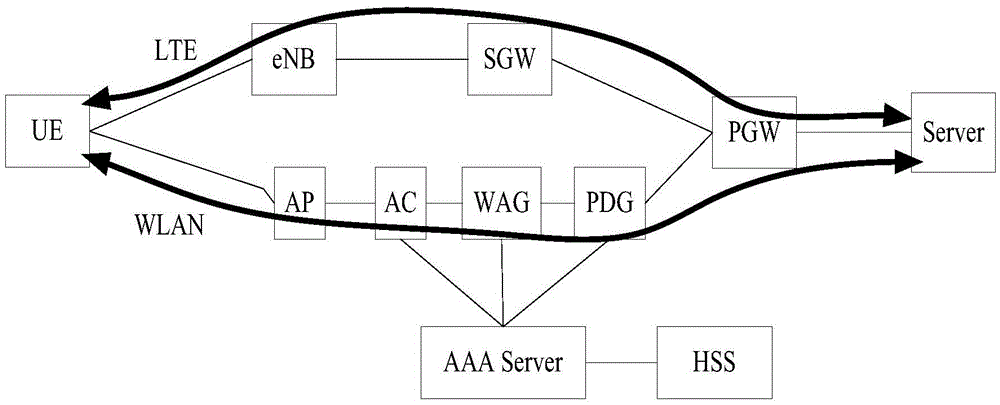
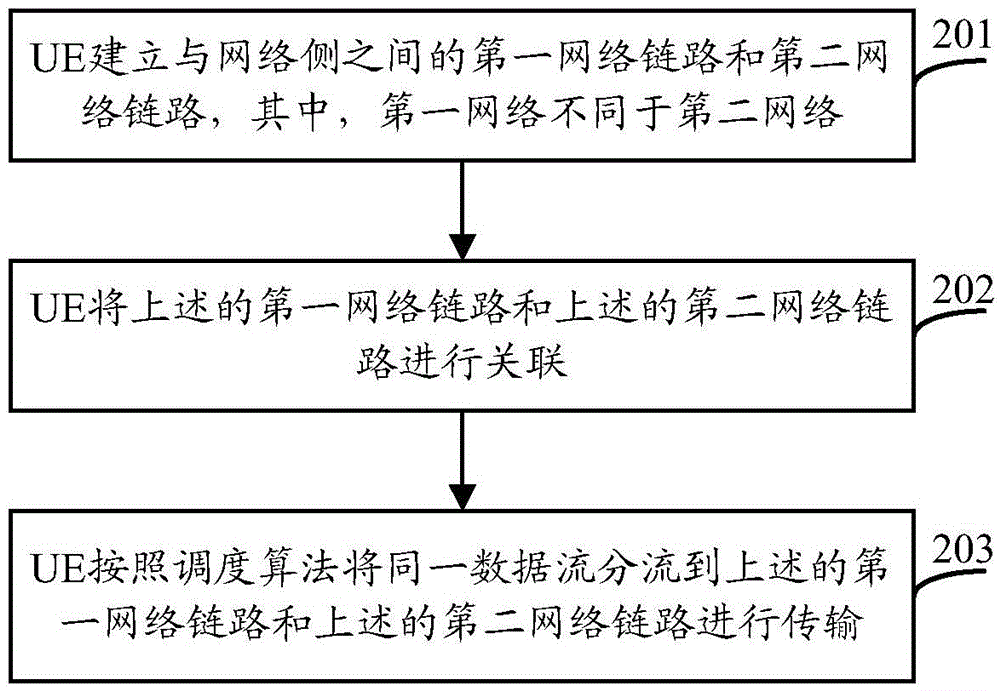
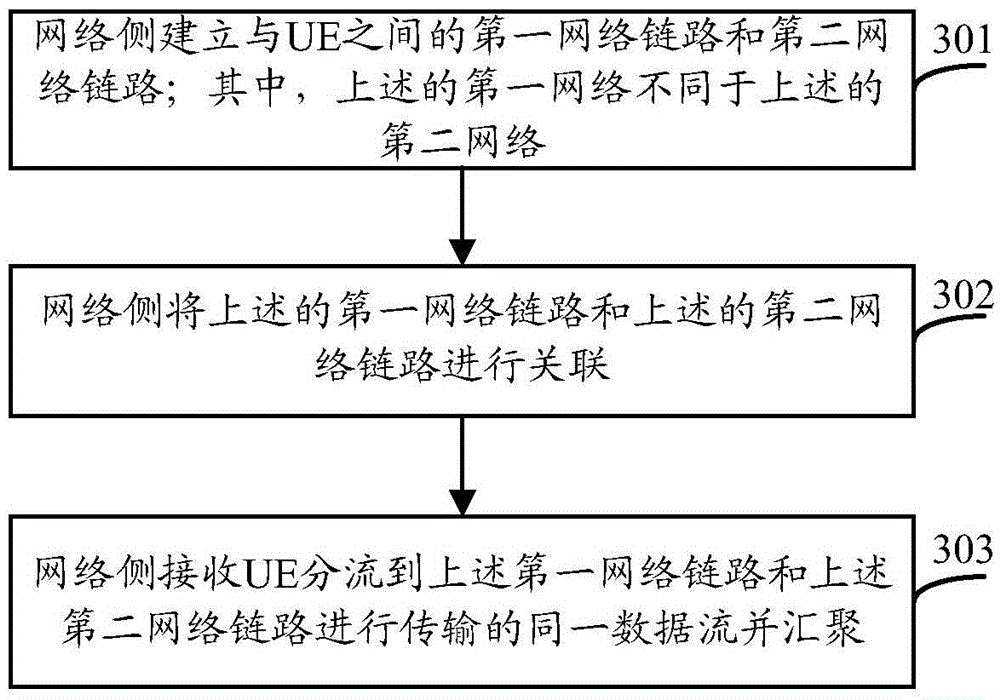
Data flow transmission method and user equipment
A technology of data stream transmission and user equipment, applied in the field of communication, can solve problems such as inability to guarantee service quality and inflexible offloading, and achieve the effect of improving service quality assurance and flexible offloading
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0080] Embodiment 1, UE authentication method 1 in WLAN:
[0081] In the embodiment of the present invention, the authentication of the UE in the WLAN mainly has the following two purposes:
[0082] 1. Identify user identity and prevent illegal user access;
[0083] 2. After the identity of the user is identified, the link of the same user in the WLAN can be associated with the link in the LTE.
[0084] Wherein, the authentication method of the UE in the WLAN given in Embodiment 1 is described as follows:
[0085] 1) If the network side (such as eNB) thinks that authentication is required, it can initiate an authentication command (AuthenticationCommand) to the UE to trigger the authentication process of the UE;
[0086] 2) The UE initiates an authentication request (AuthenticationRequest) to the network side (such as eNB) in the WLAN, wherein the authentication request carries the C-RNTI and CellID of the UE to identify its own identity;
[0087]3) After receiving the abov...
Embodiment 2
[0094] Embodiment 2, UE authentication method 2 in WLAN:
[0095] In the second embodiment, the authentication method of the UE in the WLAN may adopt the existing 802.1x authentication method in the WLAN, wherein the authentication method is based on EAP-AKA. The second embodiment will not be described in detail here.
[0096] Since the authentication method of the UE in the LTE network is similar to the authentication method of the UE in the WLAN in Embodiment 2 and is independent of each other, after the WLAN link and the LTE link are established between the UE and the network side, You can associate WLAN links with LTE links in the following ways:
[0097] 1) Determine a unified user ID, which can be used to identify a user in both WLAN and LTE, such as the user's IMSI.
[0098] 2), the authentication process of UE in WLAN is a process independent of LTE authentication, but after the authentication is passed and the WLAN link is established, the user ID needs to be stored...
Embodiment 3
[0104] Embodiment 3, UE authentication method 3 in WLAN:
[0105] In the third embodiment, under the condition that the WLAN module and the LTE module of the UE are inseparable, the authentication process of the LTE is used to realize the authentication of the UE in the WLAN. The specific method is as follows:
[0106] 1), UE reports whether it supports WLAN in LTE, and WLANMACAddress; wherein, these WLAN information can be sent to the network side (such as eNB) through RadioCapabilitiesprocedure, or sent to the network side (such as eNB) through any other feasible LTEProcedure;
[0107] 2) When the UE establishes an LTE link, the network side (such as eNB) can obtain the WLAN capability and WLANMACAddress supported by the UE through LTE, and then scan the existing WLAN link according to the WLANMACAddress. If found, the WLAN link and LTE Links are associated so that the scheduling policy negotiation and data flow distribution process can be started later;
[0108] 3) When t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com