Data access method, data access system and terminal
A data access and terminal technology, which is applied in the field of data access and data access systems, can solve the problems of wasting storage space, weakening the use of multi-domain and multi-space, unfavorable application data sharing, etc., and achieve the effect of realizing sharing and avoiding completion of sharing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
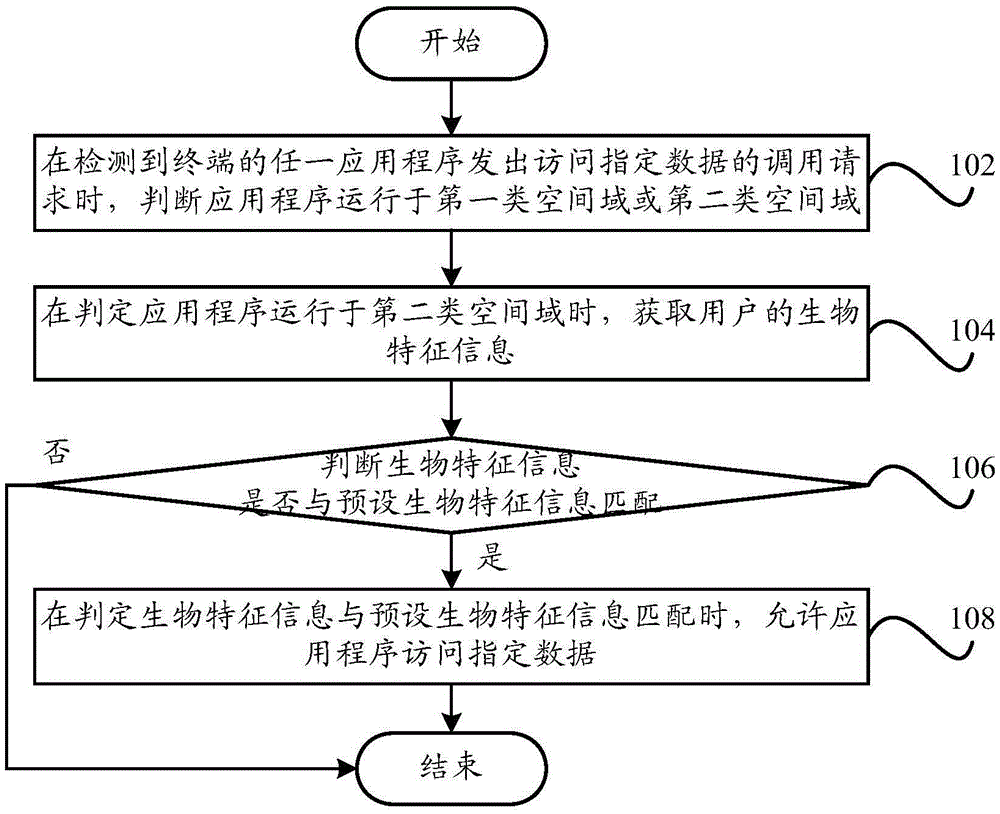
[0072] Such as Figure 6 As shown in , enter the fingerprint entry interface according to the prompt, select the finger to be entered, such as the left middle finger, and perform fingerprint entry. When the fingerprint entry is successful, access to the specified data in another spatial domain is allowed.
Embodiment 2
[0074] Such as Figure 7 As shown, enter the voice recording interface according to the prompt, and record the voice according to the prompt "Please record the voice". After the recording is completed, click OK to start the matching process with the preset voice information. access.
Embodiment 3
[0076] Such as Figure 8 As shown in Figure 1, using the built-in camera of the mobile terminal, when the user is close to the camera and one eye is completely displayed in the image, the iris information of the user is collected as biometric information. When the user keeps a certain distance from the camera and the user's face is When in the lens, take a frontal photo of the user, collect the image, match the collected iris information or face picture with the preset information, and allow access to specified data in another spatial domain after the matching is successful.
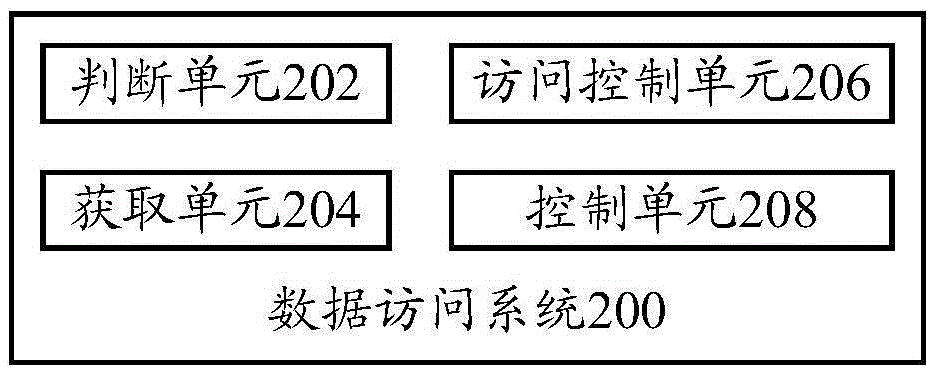
[0077] The technical solution of the present invention has been described in detail above in conjunction with the accompanying drawings, considering the technical problem of how to design a new multi-user domain data access solution to improve the fluency and security of the operating system proposed in the related art. The present invention proposes a new data access scheme, wherein the first type of sp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com