Java reflection mechanism-based automatic Android application shelling method
A reflection mechanism and automatic technology, applied in computer security devices, instruments, calculations, etc., can solve problems such as unrecoverable code and unrecoverable
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] An embodiment of the present invention will be further described below in conjunction with the accompanying drawings.
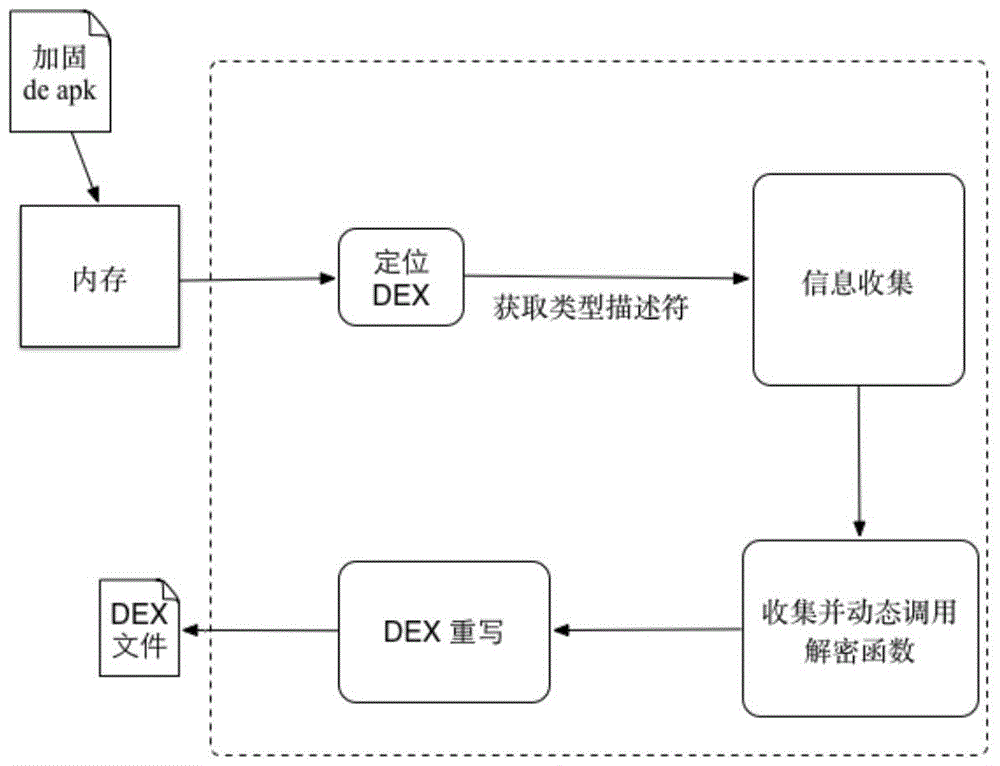
[0018] In the embodiment of the present invention, such as figure 1 and figure 2 As shown, the Android application automatic shelling method based on the Java reflection mechanism includes the following steps:
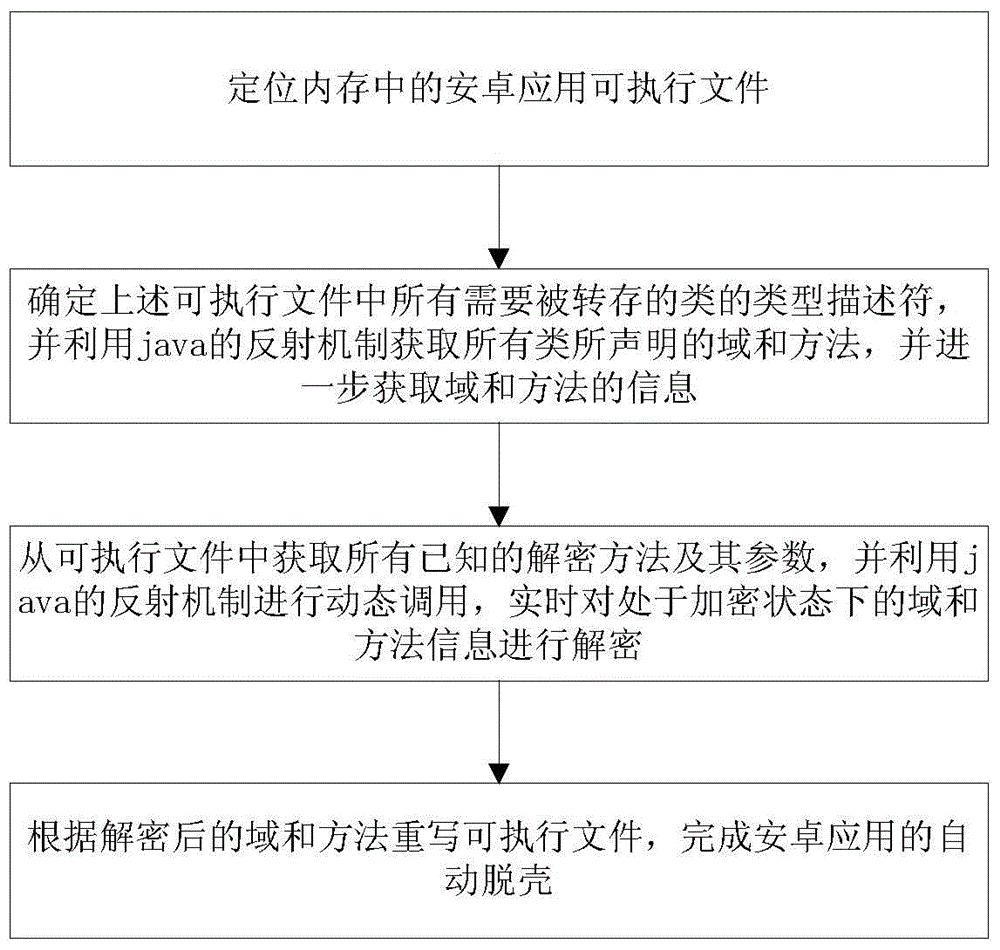
[0019] Step 1. Locate the Android application executable file in the memory;
[0020] Android reinforcement technology usually adopts multiple schemes to carry out DEX hiding (e.g. erasing the DEX header logo), but when the Dalvik virtual machine is running, the system will save all DEX files loaded into memory in a global variable gDvm; the present invention The embodiment dynamically loads libdvm.so through dlopen and dlsym functions, and obtains the address of the global variable gDvm, finally obtains pDexFile through this structure, that is, the loaded DEX memory address;
[0021] Step 2, determine the type descriptors of all the classe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com