Malicious code detection method and system based on kernel object behavior body
A malicious code detection and kernel object technology, which is applied in the computer field, can solve the problems of inability to reflect object manipulation, malicious code detection is not accurate enough, and cannot reflect operation conditions, etc. It achieves good detection and classification effects, and is easy to implement and expand , The method is simple and reliable
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0067] The present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments.
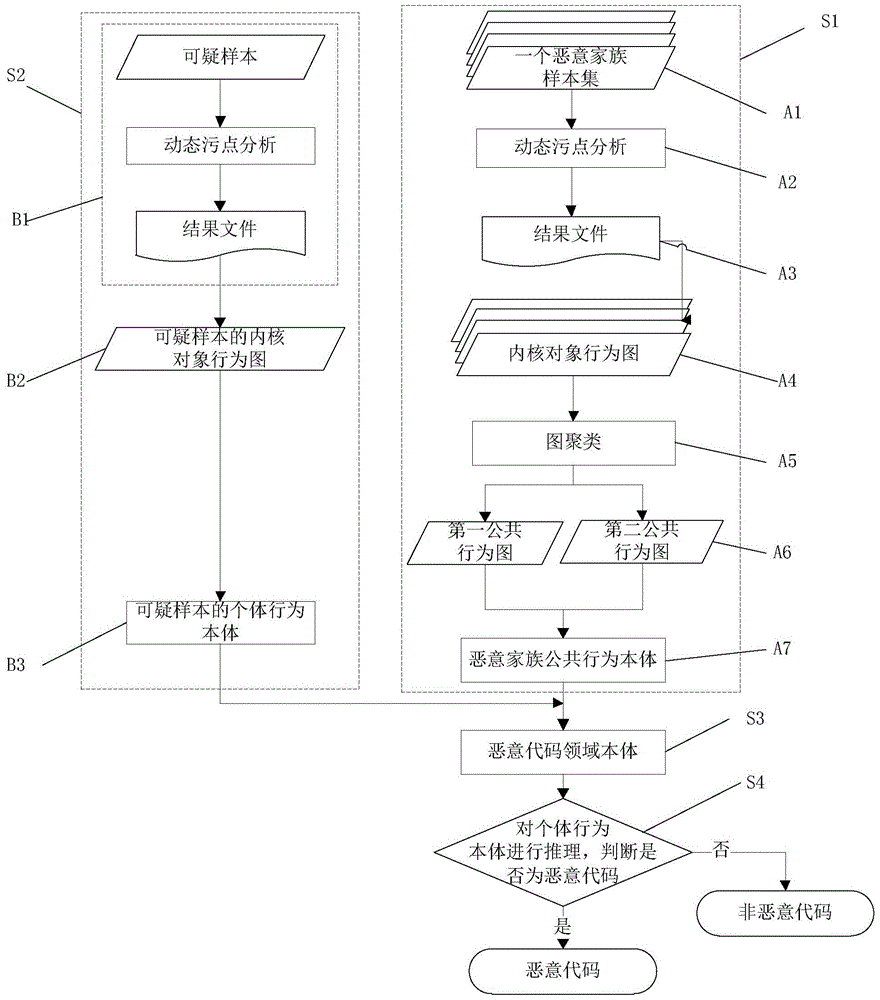
[0068] Such as figure 1 As shown, the malicious code detection method based on kernel object behavior ontology of the present invention comprises the following steps:
[0069] S1: Steps for constructing malicious family public behavior ontology;
[0070] S2: Steps of constructing suspicious sample individual behavior ontology;
[0071] S3: After importing the individual behavior ontology of suspicious samples into the malicious family public behavior ontology, the malicious code domain ontology is formed;
[0072] S4: Reasoning on the individual behavior ontology to determine whether it is malicious code,
[0073] Wherein, the malicious family public behavior ontology construction step S1 includes:
[0074] A1: Construct a malicious family sample set from several malicious code samples;
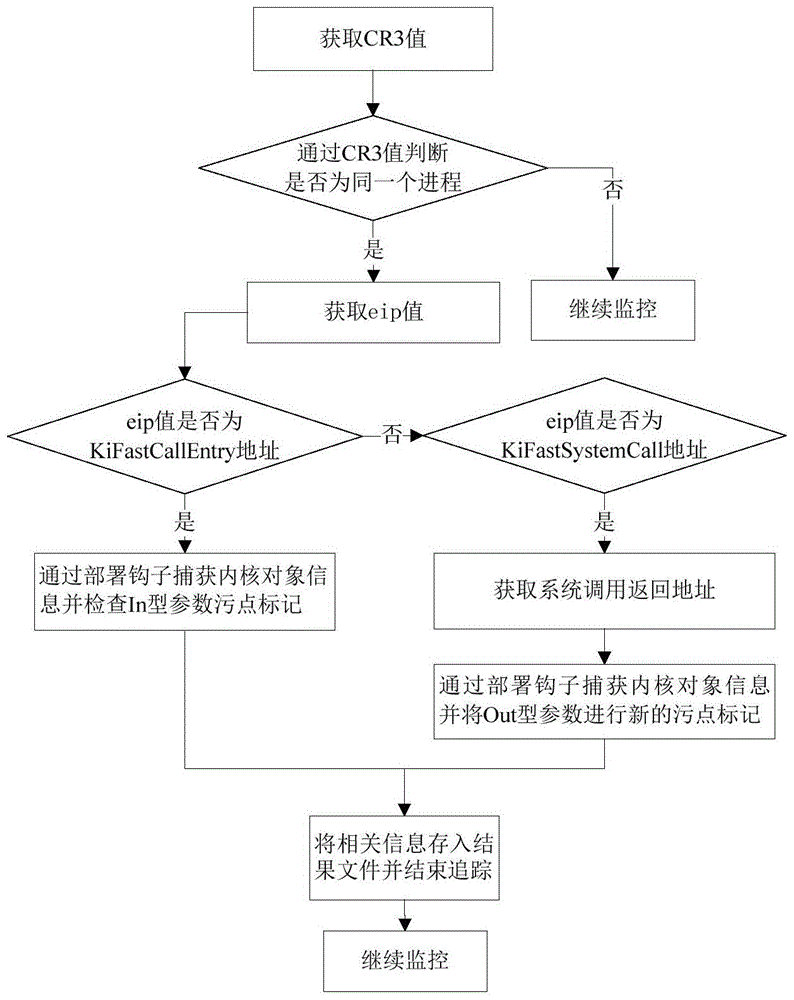
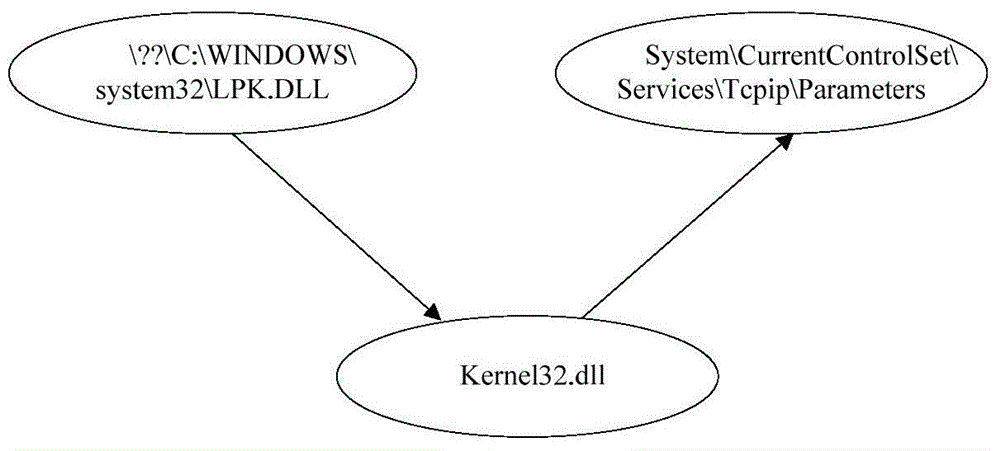
[0075] A2: Perform dynamic taint analysis on malic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com