Processing methods and apparatuses for file reading and writing operations
A processing method and technology of a processing device, which are applied in the direction of digital data protection, program/content distribution protection, etc., can solve the problems of opaque encryption or decryption, inconvenient user operation, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
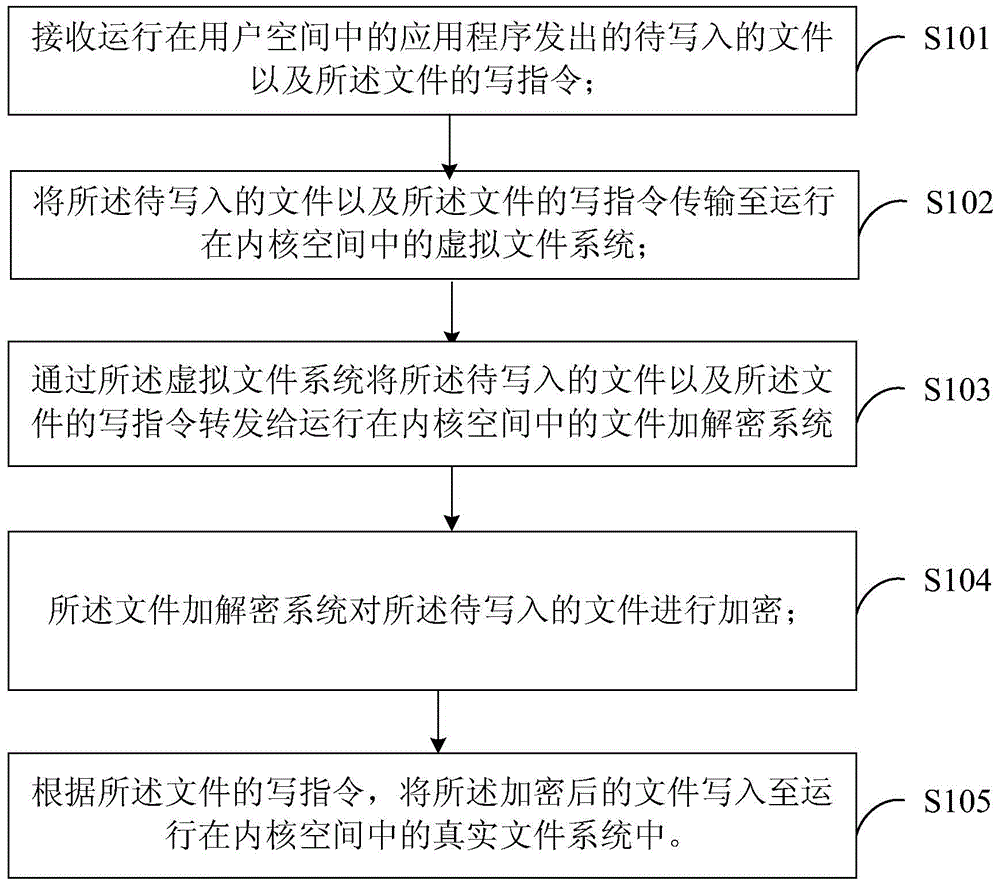
[0042] see figure 1 , the implementation flow of the processing method for file write operation provided by Embodiment 1 of the present invention, which includes the following steps:
[0043] In step S101, a file to be written and a write instruction for the file issued by an application program running in user space are received;
[0044] In step S102, the file to be written and the write instruction of the file are transmitted to the virtual file system running in the kernel space;
[0045] In step S103, the file to be written and the write instruction of the file are forwarded to the file encryption and decryption system running in the kernel space through the virtual file system;
[0046] In step S104, the file encryption and decryption system encrypts the file to be written;
[0047] In step S105, according to the write instruction of the file, the encrypted file is written into the real file system running in the kernel space.
[0048] The specific implementation proc...
Embodiment 2
[0121] see figure 2 , the specific process of finding the key of the file currently to be written for the embodiment of the present invention is as follows:
[0122] In step S201, the directory entry object pointed to by the file object of the currently opened file is searched.
[0123] In step S202, the index node object of the file is obtained according to the pointed directory entry object.
[0124] In step S203, the superblock object pointing to the file is obtained according to the inode object.
[0125] In step S204, the private data of the super block object is obtained according to the super block object of the file, wherein the private data indicates the file encryption and decryption system.
[0126] In step S205, according to the private data, the linked list storing the user ID and the key in the file encryption and decryption system is searched sequentially.
[0127] In step S206, according to the user ID of the current process, the key corresponding to the us...
Embodiment 3
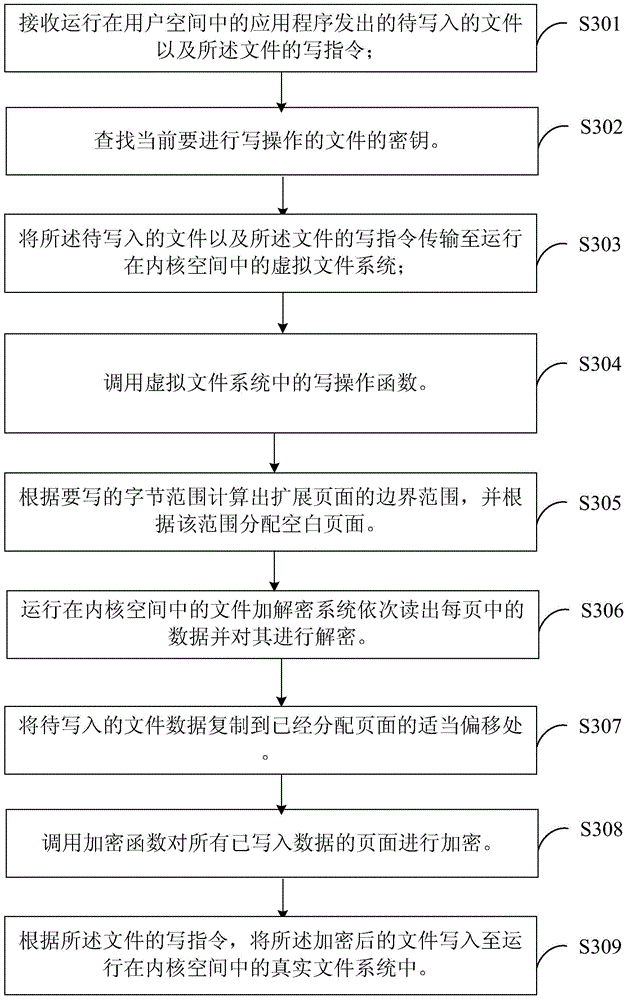
[0137] see image 3 , the specific implementation process of the processing method of the file write operation provided by the embodiment of the present invention is as follows:
[0138] In step S301, a file to be written and a write instruction for the file issued by an application program running in the user space are received;
[0139] In step S302, the key of the file currently to be written is searched.
[0140] In the embodiment of the present invention, the key of the file to be currently written is searched according to the above-mentioned implementation scheme of obtaining the key.
[0141] In step S303, the file to be written and the write instruction of the file are transmitted to the virtual file system running in the kernel space;
[0142] In step S304, the write operation function in the virtual file system is called.
[0143] In the embodiment of the present invention, the write operation function in the virtual file system is called, for example, sys_write()...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com