ELF shared library protection method and system thereof
A technology for protecting systems and shared libraries, applied in the field of ELF shared library protection methods and systems thereof, can solve problems such as low security, and achieve the effects of improving protection, protecting interests and avoiding economic losses.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
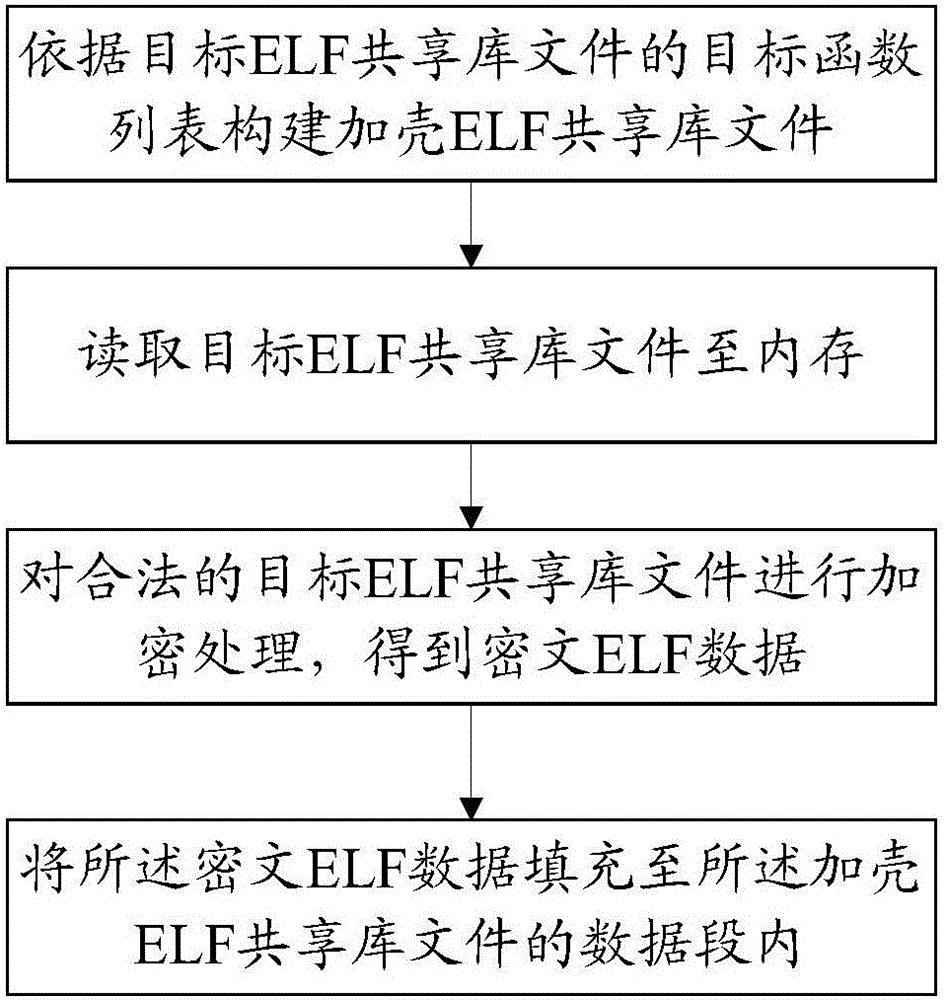
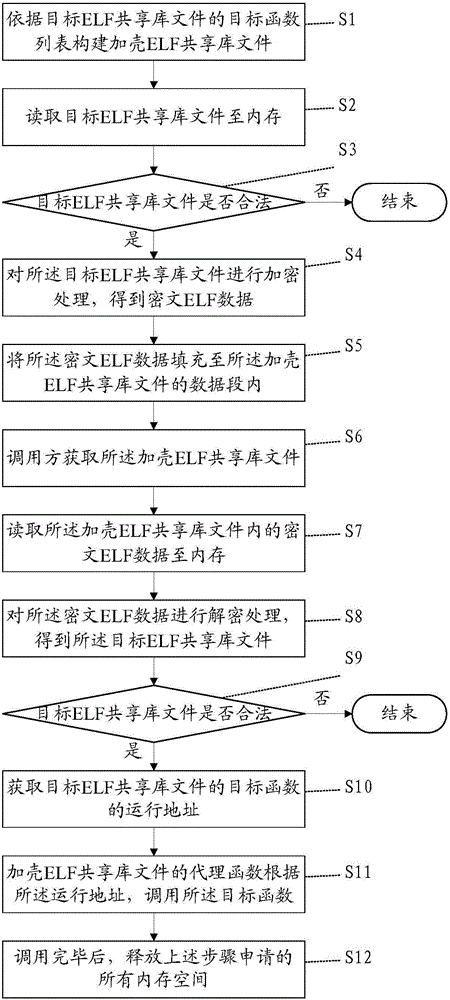
[0061] Please refer to figure 2 , The first embodiment of the present invention is an ELF shared library protection method, which includes the following steps:
[0062] S1: Build a packed ELF shared library file according to the target function list of the target ELF shared library file, the packed ELF shared library file includes a proxy function associated with the target function in the target ELF shared library file; specifically according to the target ELF shared library The callable function list thrown by the file is the target function list. The proxy function is implemented in the packed ELF shared library file. The caller, that is, the third-party caller, completes the call of the target function by calling the proxy function. For example, if there is a target function target_func1() in the target ELF shared library file, the proxy function proxy_func1() is implemented in the packed ELF shared library file, and the target function target_func1() is called inside the pro...
Embodiment 2
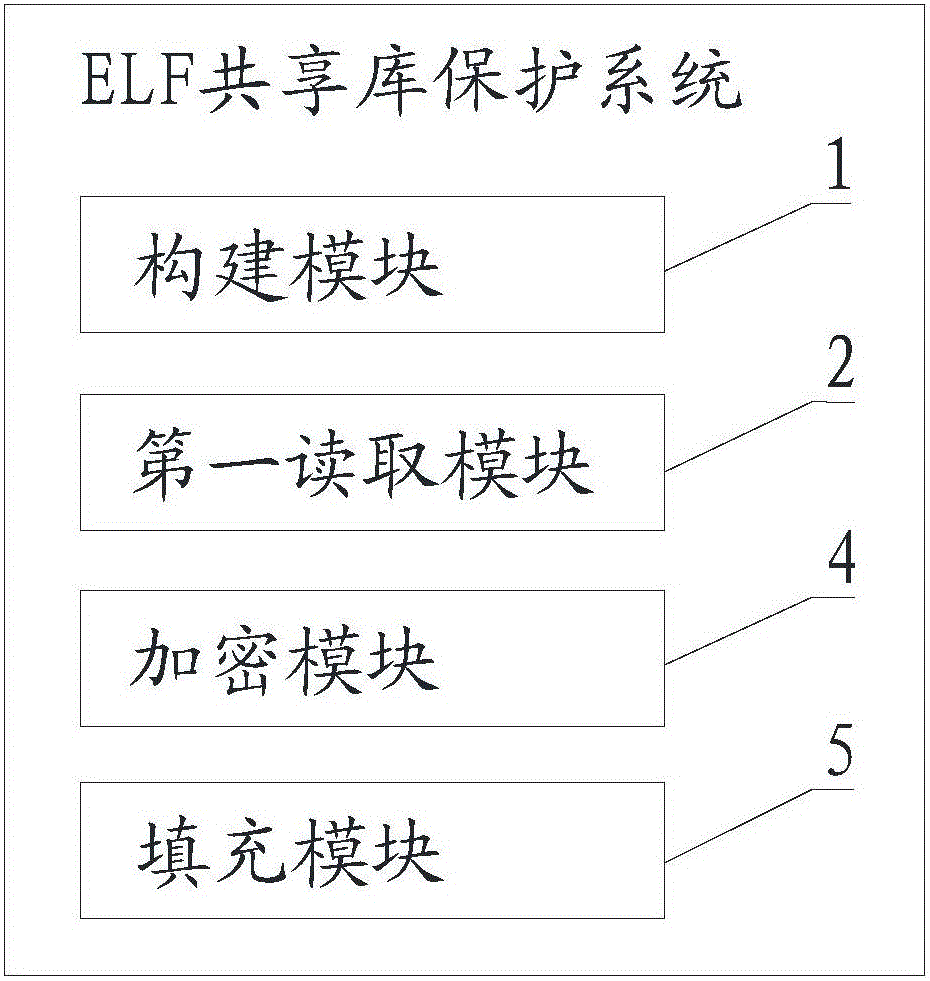
[0076] Please refer to Figure 4 , This embodiment is an ELF shared library protection system corresponding to the above method, including:
[0077] Building module 1, used to build a packed ELF shared library file according to the target function list of the target ELF shared library file;
[0078] The first reading module 2 is used to read the target ELF shared library file to the memory;
[0079] The first judgment module 3 is used to judge whether the target ELF shared library file is legal, and obtain the first judgment result;
[0080] The encryption module 4 is configured to perform encryption processing on the target ELF shared library file if the first judgment result is yes, to obtain ciphertext ELF data;
[0081] The filling module 5 is used to fill the ciphertext ELF data into the data segment of the packed ELF shared library file;
[0082] The second reading module 6 is used to read the ciphertext ELF data in the packed ELF shared library file to the memory;
[0083] The dec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com