Security protection method and DPMA protection model
A security protection and model technology, applied in the Web field, can solve problems such as false alarms of Web application firewalls, inability to trace the source after the event, and isolation of alarm events, etc., to achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
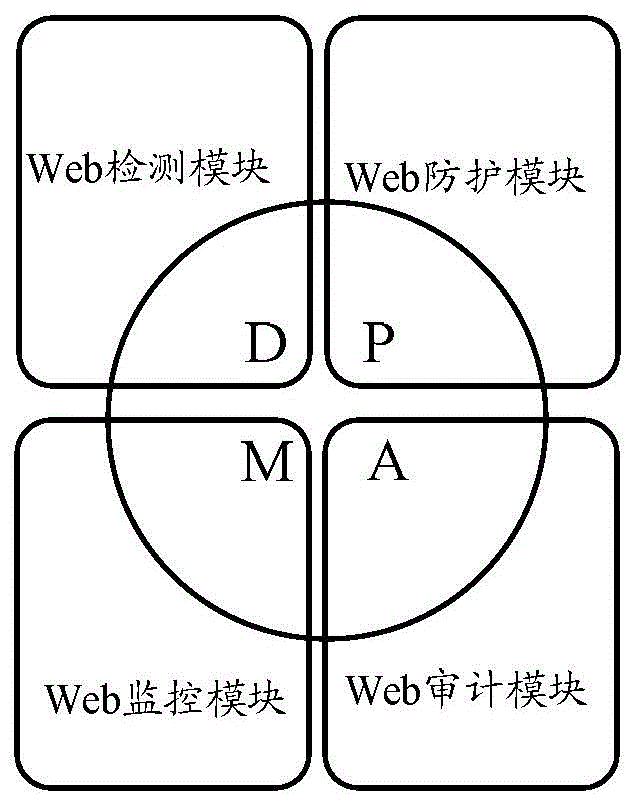
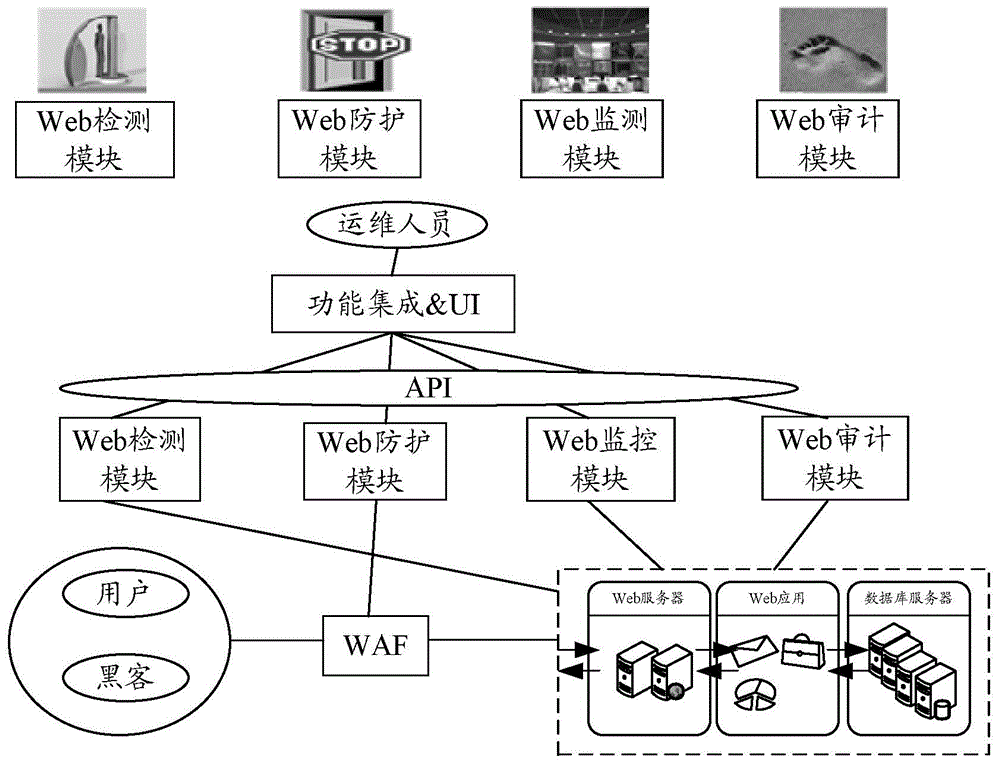
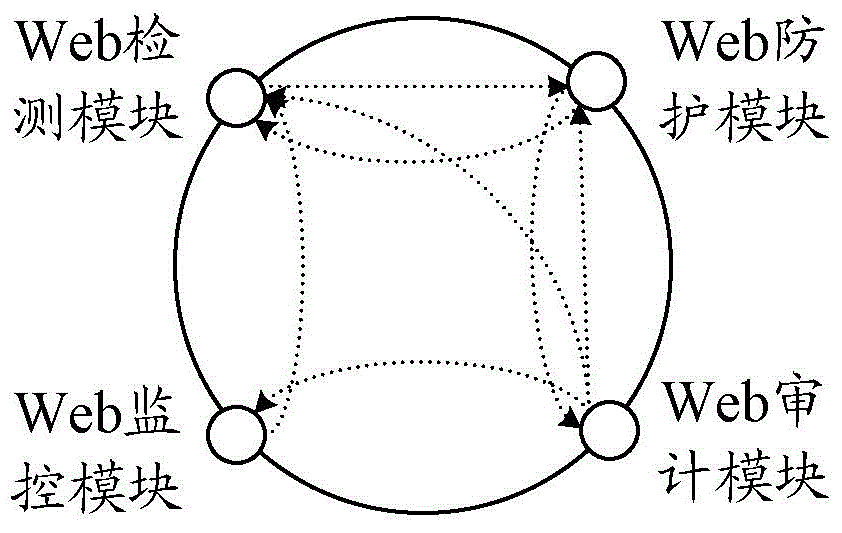
[0024] In order to make up for the deficiencies of the existing technical means, the embodiment of the present invention will provide a DPMA protection model for Web applications, such as figure 1 As shown, the DPMA (Detect, Protect, Monitor, Audit) protection model integrates the four functions of Web detection (Detect), Web protection (Protect), Web monitoring (Monitor) and Web audit (Audit). The functions correspond to a security module, for the web detection function, it corresponds to the web detection module, for the web protection function, it corresponds to the web protection module, for the web monitoring function, it corresponds to the web monitoring module, and for the web audit function, it corresponds to the web monitoring module. Corresponding to the web audit module, the security protection of the DPMA protection model runs through the entire security event life cycle, and each security module is linked with each other while exerting their respective advantages t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com