Safe positioning method of wireless sensor network based on trust level evaluation
A wireless sensor network and secure positioning technology, applied in the field of information security, can solve the problems of less research and insufficient research on node positioning
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
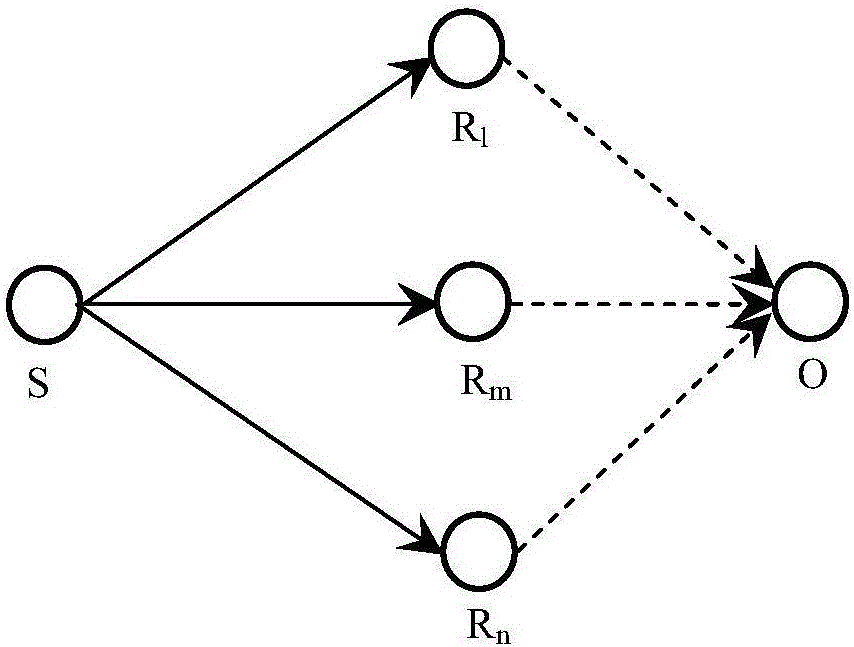
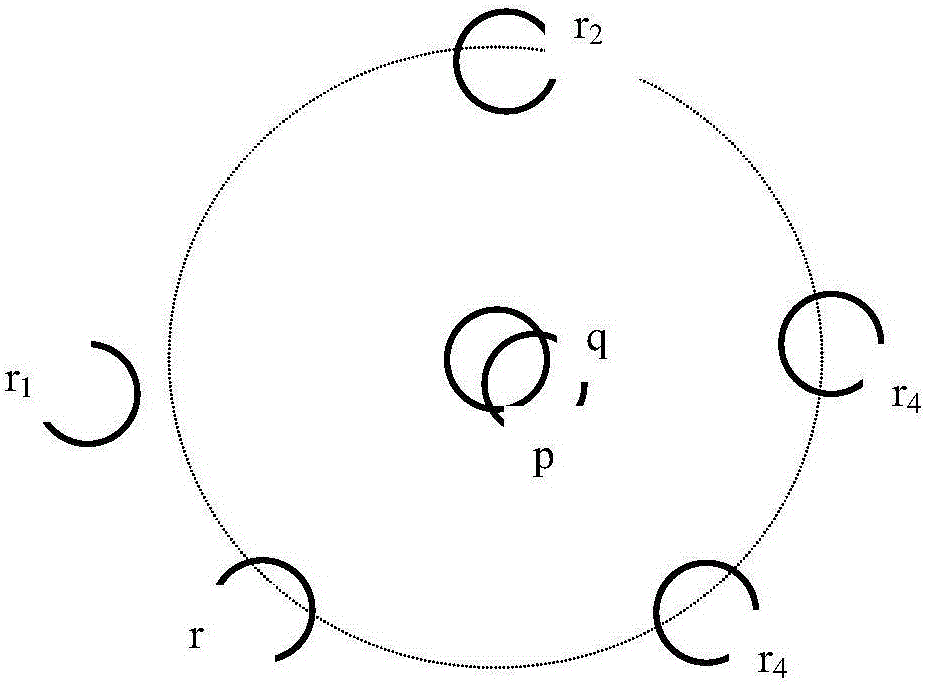
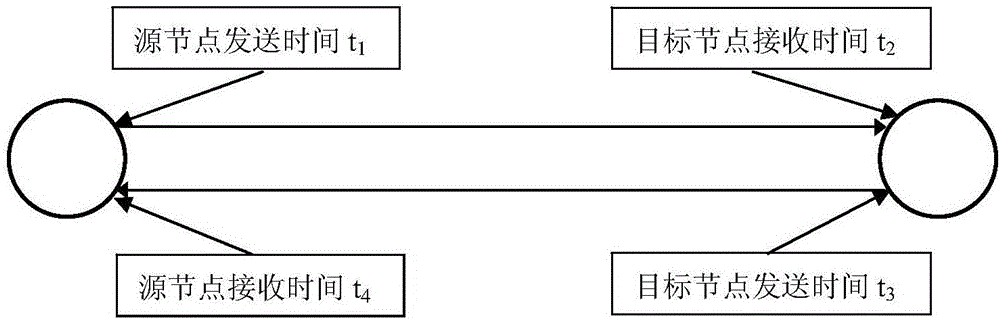
[0045] Due to the limitations of sensor nodes, the security positioning algorithm itself cannot be as complete as the attack defense methods in traditional networks. At the same time, for the diversity of attack methods, the security positioning algorithm for wireless sensor networks must have both availability and Completeness. At present, based on these characteristics, secure location algorithms are divided into three categories: (1) Secure location strategy based on robust observation calculation; (2) Secure location strategy based on isolation of malicious beacon nodes; (3) Security based on location verification Positioning strategy.
[0046] The present invention adopts the security positioning algorithm based on the tolerant attack under the first type of algorithm. Compared with other algorithms, this algorithm has the following advantages: (1) The security positioning algorithm based on the tolerant attack has a wide range of attack types and successful defense. The ch...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com