Method for carrying out Hamming error correction for error code in quantum secret key distribution postprocessing
A quantum key distribution and post-processing technology, applied in key distribution, can solve problems such as low error correction efficiency, abnormality, and reduction in the number of communication rounds, and achieve the effect of improving error correction efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] This embodiment provides a method for error correction in post-processing of quantum key distribution, including the following steps:
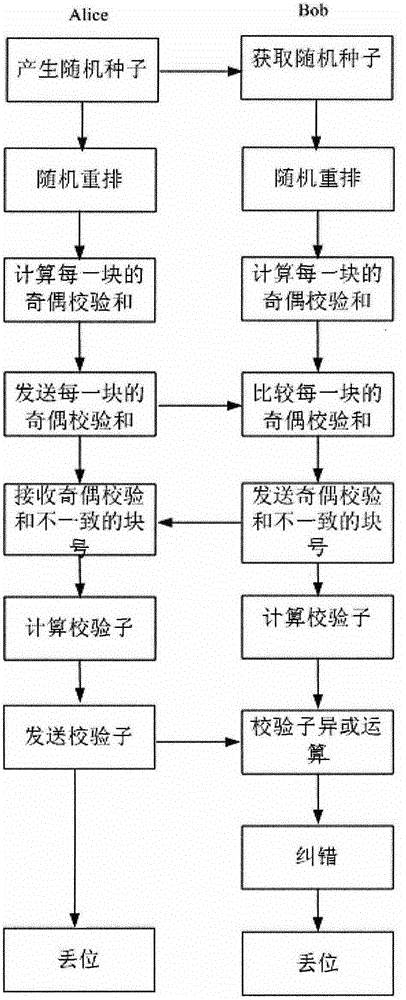
[0036] Preprocessing stage: the data structure used in the implementation of the Winnow error correction protocol is as follows: image 3 shown. Among them, Sift_Data is an external interface that calls the winnow protocol, and it calls the start_winnow data structure to start winnow error correction. The Start_Winnow data structure calls the CommuData data structure for network transmission, and at the same time calls New_Winnow for the specific error correction process. New_Winnow calls the BitBuffer data structure to store complex data in the error correction process. This data structure was created to save bandwidth and time in the subsequent error correction process. Alice at the sending end and Bob at the receiving end store the first and second original keys obtained from the physical end of quantum key distribution connected ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com