Monitoring method and monitoring system for service of server
A monitoring system and server technology, applied in the field of communication, can solve problems such as inability to prevent Internet server denial of service attacks, waste of investment, complex network security implementation, etc., to achieve the effect of improving experience and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
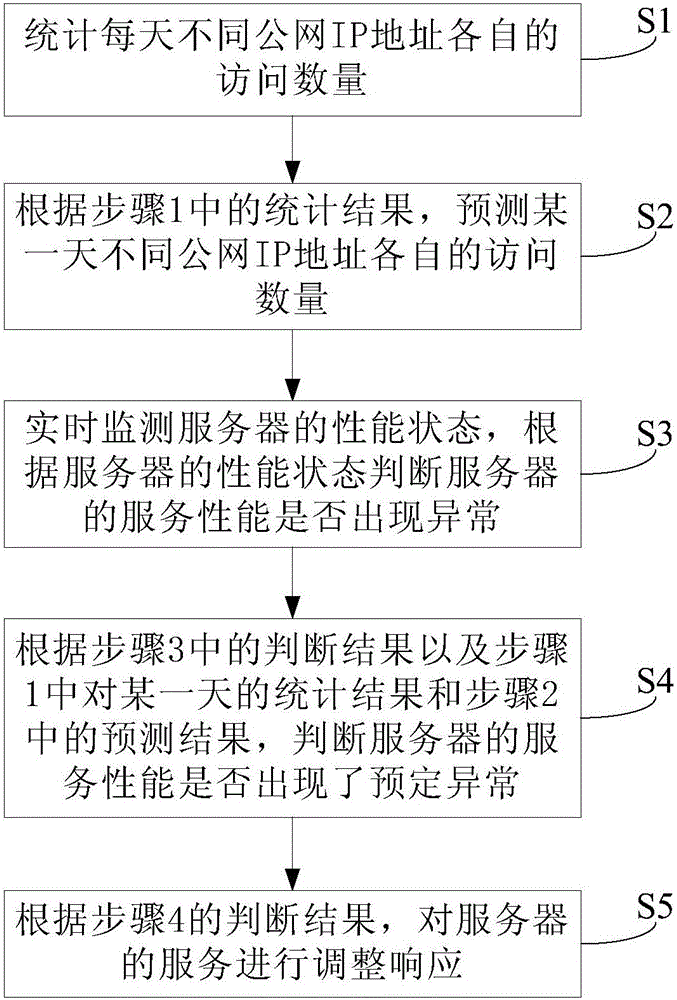
[0056] This embodiment provides a method for monitoring server services, such as figure 1 As shown, it includes: Step S1: Count the number of visits of different public network IP addresses every day.
[0057] In this step, the number of visits to the server from different public network IP addresses each day is counted.
[0058] Step S2: According to the statistical results in step S1, predict the number of visits from different public network IP addresses on a certain day.
[0059] In this step, the number of visits to the server from different public network IP addresses on a certain day is predicted. A day can be any day.
[0060] Step S3: Monitor the performance state of the server in real time, and judge whether the service performance of the server is abnormal according to the performance state of the server.
[0061] Step S4: According to the judgment result in step S3, the statistical result of a certain day in step S1 and the prediction result in step S2, judge wh...
Embodiment 2
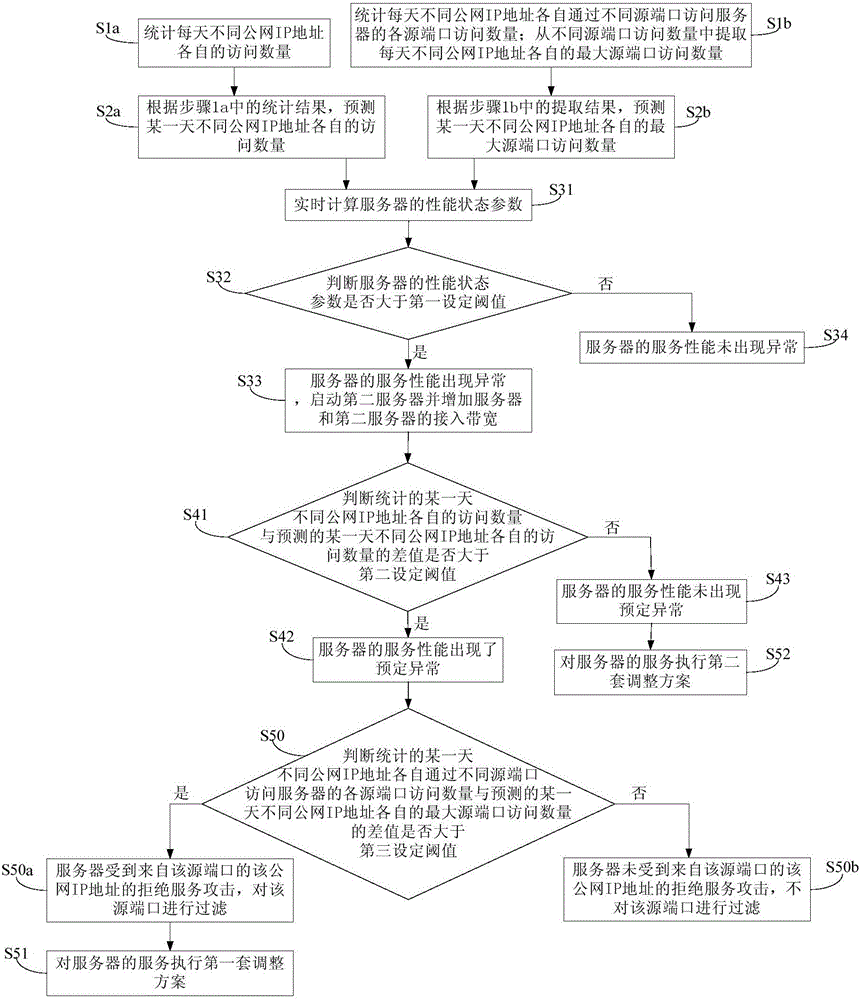
[0065] This embodiment provides a method for monitoring server services, such as figure 2 As shown, the monitoring method is used to monitor whether the firewall server is under a denial of service attack, including: Step S1 includes: Step S1a: Count the number of visits from different public network IP addresses every day.
[0066] In this step, the number of visits to the server from different public network IP addresses each day is counted. For example, count the number of access servers from the dth public IP address on the cth day as Ncd.
[0067] Step S1 also includes: Step S1b: counting the number of each source port visit of different public network IP addresses accessing the server through different source ports each day; extracting the respective maximum source port visit numbers of different public network IP addresses every day from the number of different source port visits .
[0068] For example, the number of visits from each source port of the d-th public IP...
Embodiment 3
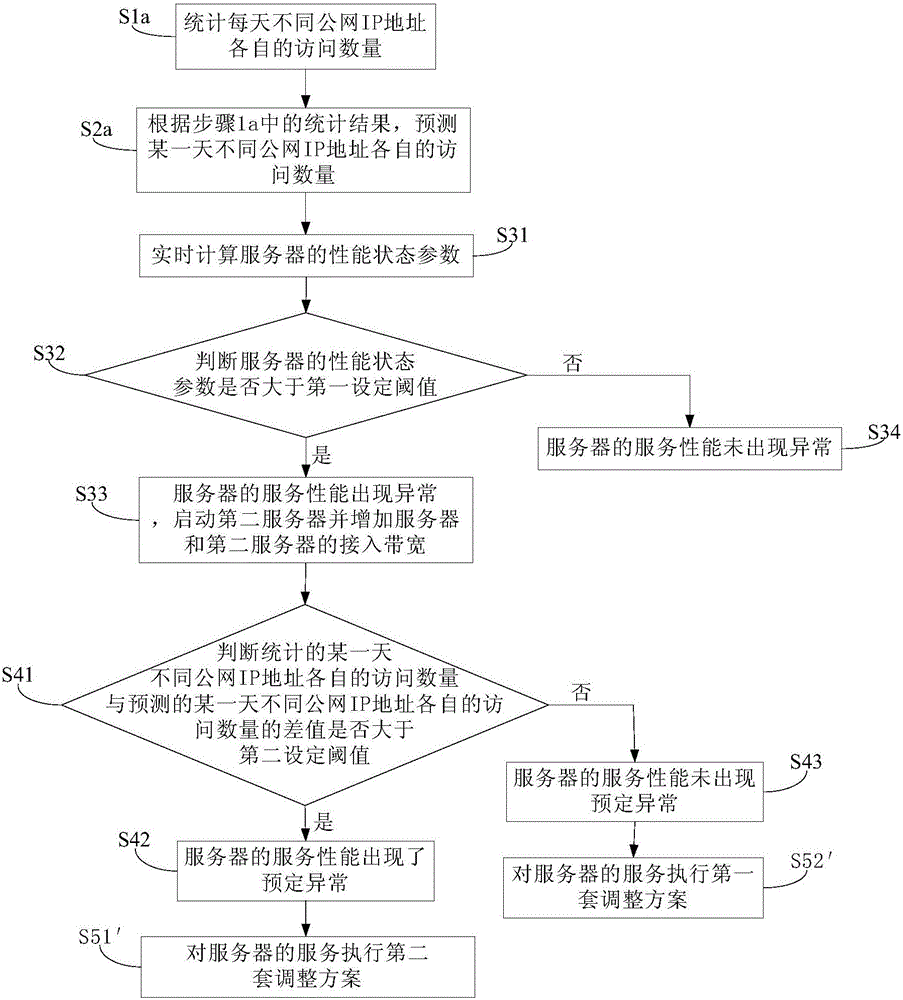
[0101]This embodiment provides a monitoring method for server services, which is different from the monitoring method in Embodiment 2, such as image 3 As shown, the monitoring method is used to monitor whether the user group or user access frequency of the video server increases. Wherein, step S5 specifically includes: when the user group or user access frequency of the server increases, perform step S51': execute the second set of adjustment schemes for the server's services. When the user group or user access frequency of the server does not increase, perform step S52': execute the first set of adjustment schemes for the server's services.
[0102] Correspondingly, the monitoring method does not include step S1b, step S2b, step S50, step S50a and step S50b.
[0103] Other steps of the monitoring method in this embodiment are the same as those in Embodiment 2, and will not be repeated here.
[0104] The server service monitoring method provided in Embodiment 3 can monitor ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com