A trusted working system for power grid information security based on big data
An information security and big data technology, applied in the field of big data, can solve problems such as potential safety hazards and impacts on the normal operation of the power grid, and achieve the effects of safety assurance, reduction of manual intervention, and improvement of computing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
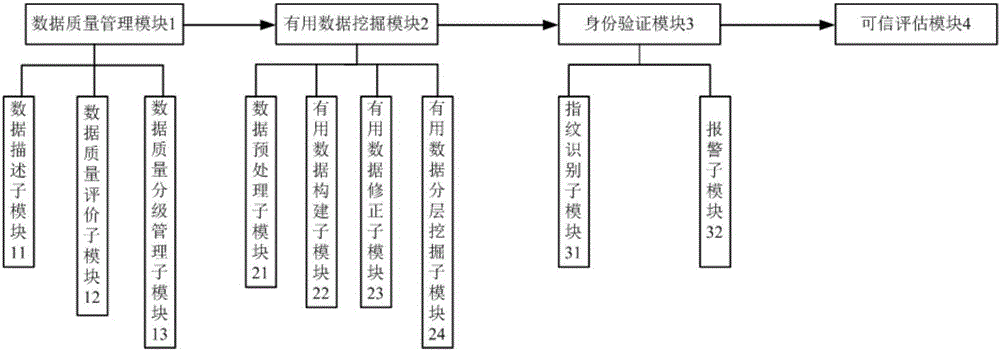
[0052] Such as figure 1 The big data-based power grid information security trusted working system shown includes a data quality management module 1, a useful data mining module 2, an identity verification module 3 and a trusted evaluation module 4, wherein the quality management module 1 includes a data descriptor Module 11, data quality evaluation sub-module 12 and data quality classification management sub-module 13, useful data mining module 2 includes data preprocessing sub-module 21, useful data construction sub-module 22, useful data correction sub-module 23 and useful data hierarchical mining The sub-module 24 and the identity verification module 3 include a fingerprint identification sub-module 31 and an alarm sub-module 32 .
[0053] (1) Data description sub-module 11:
[0054] The data is described by introducing the attributes of the data itself and the attributes of the data influencer. The attributes of the data itself are represented by the size of the data, the...
Embodiment 2
[0092] Such as figure 1 The big data-based power grid information security trusted working system shown includes a data quality management module 1, a useful data mining module 2, an identity verification module 3 and a trusted evaluation module 4, wherein the quality management module 1 includes a data descriptor Module 11, data quality evaluation sub-module 12 and data quality classification management sub-module 13, useful data mining module 2 includes data preprocessing sub-module 21, useful data construction sub-module 22, useful data correction sub-module 23 and useful data hierarchical mining The sub-module 24 and the identity verification module 3 include a fingerprint identification sub-module 31 and an alarm sub-module 32 .
[0093] (1) Data description sub-module 11:
[0094] The data is described by introducing the attributes of the data itself and the attributes of the data influencer. The attributes of the data itself are represented by the size of the data, the...
Embodiment 3
[0132] Such as figure 1 The big data-based power grid information security trusted working system shown includes a data quality management module 1, a useful data mining module 2, an identity verification module 3 and a trusted evaluation module 4, wherein the quality management module 1 includes a data descriptor Module 11, data quality evaluation sub-module 12 and data quality classification management sub-module 13, useful data mining module 2 includes data preprocessing sub-module 21, useful data construction sub-module 22, useful data correction sub-module 23 and useful data hierarchical mining The sub-module 24 and the identity verification module 3 include a fingerprint identification sub-module 31 and an alarm sub-module 32 .
[0133] (1) Data description sub-module 11:
[0134] The data is described by introducing the attributes of the data itself and the attributes of the data influencer. The attributes of the data itself are represented by the size of the data, the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com