Microcomputer bit addition verifying coded lock
A technology for verifying passwords and microcomputers. It is used in instruments, time registers, and individual input/output registers. It can solve problems such as cumbersome operations, short password security, and difficulty in remembering long passwords.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
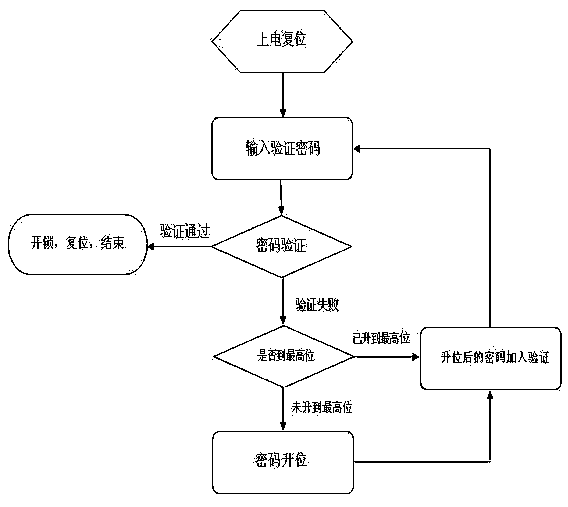
[0048] Next, a specific example will be used to describe in detail a kind of microcomputer upgrade verification combination lock of the present invention.
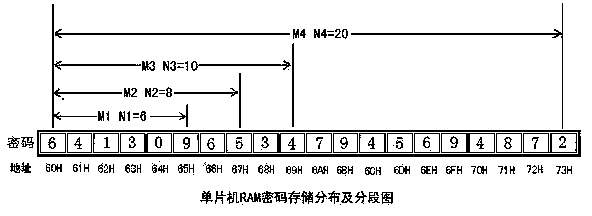
[0049] Step A. Set a password M with a length of 20 characters: 64130965347945694872 , and stored in the RAM user area of the microcontroller, such as image 3 shown.
[0050] Step B: The user needs to segment the password M according to his own needs: set the length of each password to be N 1 =6;N 2 =8;N 3 =10;N 4 =20, password segment M 1 for: 641309 ;Cipher segment M 2 for 64130965 ;Cipher segment M 3 for: 6413096534 ;Cipher segment M 4 for: 64130965347945694872 ,Such as image 3 shown.
[0051] Step C. Press the reset button once, and there will be a "beep" prompt sound, and then press the password setting button, and a continuous input prompt sound of "beep" will be issued, and then enter the password M from the keyboard: 64130965347945694872 , The digital tube displays the entered password; press th...
Embodiment 2
[0071] Below again take the Chinese phonetic alphabet of a Chinese sentence as the concrete example that password is set, describe a kind of microcomputer ascending position verification combination lock of the present invention in detail;
[0072] Chinese sentence: feel ∣ things that have been ∣ ∣ not necessarily understand it, only things that are understood can feel it more deeply;
[0073] Corresponding pinyin letters: gan jue ∣dao liao ∣de dong xi ∣bu yi ding li jie ta zhi you li jie liao de dong xi cai neng geng shen ke de gan jue ta.
[0074] Step A. Set the password M with a length of 87 bits: gan jue dao liao de dong xi bu yi ding li jie ta zhi you li jie liao de dong xi cai neng geng shen ke de gan jue ta, and store it in the RAM user of the microcontroller Area.
[0075] Step B: The user needs to segment the password M according to his own needs: set the length of each password to be N 1 =6;N 2 =13;N 3 =22; N 4 =87, password segment M 1For: gan jue; password s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com