Perimeter security protection net and perimeter security protection method
A safety protection and security technology, applied in the direction of fences, building types, buildings, etc., can solve the problems of high cost of electrostatic induction, high maintenance cost, poor practicability, etc., to achieve the effect of not easy to find or avoid, improve reliability, and improve accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
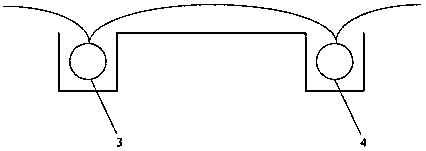
[0060] use figure 2 Any one of the shown security cables 1 to 5 forms the detection sensing field of the perimeter security protection area. The receiving / transmitting state of the detector in the one security cable is set so that the detection signal radiation field forms a dense detection sensing field around the security cable.
[0061] The detectors in a security cable include transmitting detectors and receiving detectors. The transmitting detectors and receiving detectors are spaced apart, and the ratio of the number of transmitting detectors to receiving detectors is a preset ratio, which is less than or equal to 1 . For example, the ratio of transmitting detectors to receiving detectors can be 1:1, or less than 1, that is, the number of transmitting detectors and receiving detectors set in a security cable are the same, or the number of transmitting detectors is smaller than that of receiving detectors. Quantity.
[0062] The transmitting detector and the receiving detec...
Embodiment 2
[0072] use figure 2 The two security cables in the two security cables form a detection sensing field. Specifically, one of the two security cables transmits detection signals and the other receives detection signals. The two security cables receive and send detection signals to form multiple detection signal radiation fields, multiple detection signals The radiation field is cross-covered to form a continuous and seamless detection sensing field.
[0073] Among them, the two security cables can divide the work to send and receive detection signals, and can also switch the roles of sending and receiving at any time. Assuming that the two security cables are A and B, you can set the security cable A as the transmitting cable, that is, the detectors in the security cable A are set as transmitting detectors; the security cable B is the receiving cable, that is, the detectors in the security cable B are all Set as a receiving detector; you can also switch the transceiver status of s...
Embodiment 3
[0086] Three security cables are used to form a detection sensing field. The three security cables can form a variety of combinations of sending and receiving signals to form a larger security protection area. For example, one security cable transmits detection signals and the other two security cables receive detection signals, or two security cables transmit detection signals and the other security cable receives detection signals.
[0087] (1) Three security cables form a triangular combination
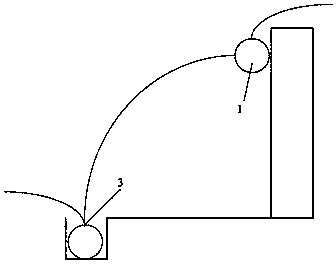
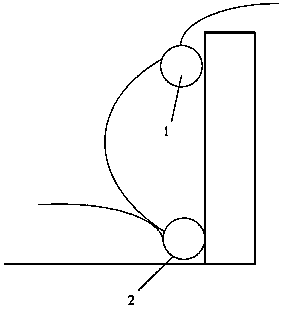
[0088] For example, using figure 2 In the security cables 1, 2 and 3, two security cables 1 and 2 are hung on the fence, and the other security cable 3 is buried below the ground. Among them, 2 can be set as a launch cable, and 1 and 3 can be set as The receiving cable can detect the process of intruding objects approaching the fence and overturning the wall.
[0089] Such as Figure 7 As shown, the area between security cables 2 and 3 is set as a warning area. Similarly, the area betwe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com