Block chain based CA authentication and management method, device and system
A CA authentication and management method technology, applied in the direction of user identity/authority verification, etc., can solve the problems of affecting the verification process results, occupying the user's local storage space, increasing the amount of user operations, etc., to simplify user operations, save user space, improve safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
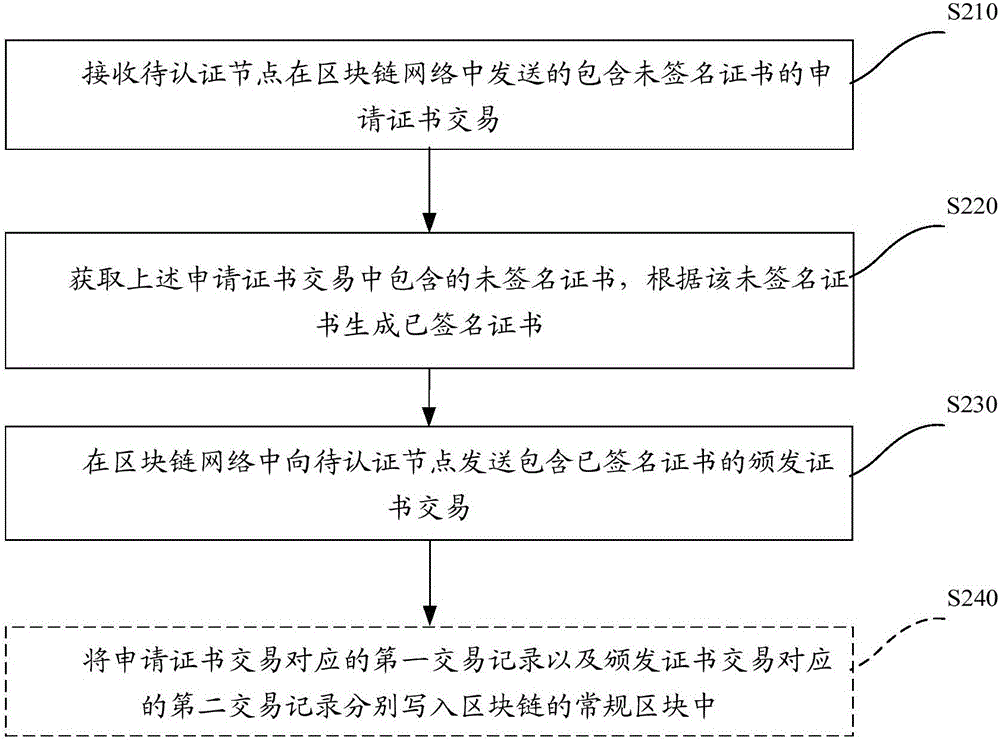
[0059] This embodiment is mainly used to implement certificate issuing management operations. Specifically, issuing certificates involves the process of generating root CA certificates, the process of applying for certificates from lower-level CAs to higher-level CAs, and the process of customers applying for certificates from CA institutions, which are described below:
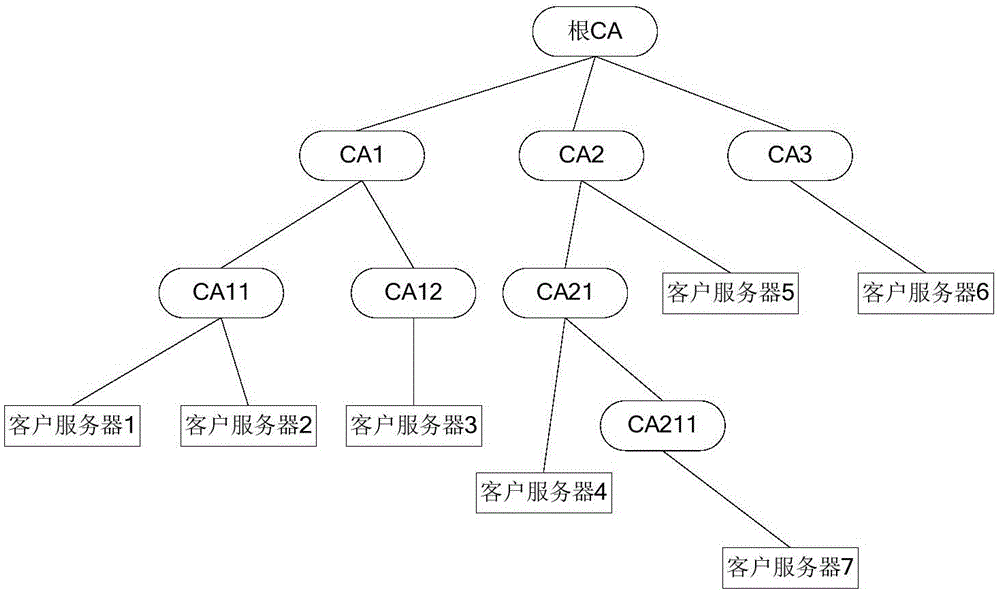
[0060] (1) The certificate generation process of the root CA authority:
[0061] Since the root CA is the most trusted certificate authority, and the certificate of the root CA is a self-signed certificate without the certification of the superior CA, the certificate of the root CA can be trusted for a long time and hardly needs to be changed. Therefore, in the embodiment of the present invention, the root CA certificate is hard-coded into the genesis block. Since the rest of the blocks are built after the genesis block, the operation of each node on the blockchain cannot affect the genesis block. The block ...
Embodiment 2
[0085] This embodiment is mainly used to implement certificate revocation management operations. Specifically, revoking a certificate involves the operation of the upper-level CA organization to revoke the certificate issued by the lower-level CA organization, and the operation of the CA organization to revoke the certificate issued by the CA organization for the client. Since the procedures of the two types of revocation operations are similar, the following mainly introduces the first Class undo operation:
[0086] The upper-level CA agency searches the blockchain for the transaction records of transactions initiated by the CA agency to its lower-level CA agencies, finds the latest transaction, and takes out the signed certificate contained in it. Among them, if the certificate can be taken out from the latest transaction, it means that there is a revocable certificate, otherwise, it returns directly. If there is a revocable certificate, the upper-level CA institution initi...
Embodiment 3
[0091] This embodiment is mainly used to implement query (verification) certificate management operations. Among them, the verification of the certificate is usually verified by the user who has information interaction with the certificate owner (such as the website server). The verification process not only needs to verify whether the certificate owned by the certificate owner is valid, but also verifies the certificate authority layer by layer. certificate. Specifically, the main steps of the verification process are as follows:
[0092] Step 1. The user terminal accesses the website server, and the website server sends the certificate owned by the website server to the user terminal.
[0093] Step 2: The user terminal sends a certificate query request to any network node in the blockchain network, and the network node receives and processes the certificate query request.
[0094] Among them, the network node that receives and processes the certificate query request can be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com