Authorization method and device
A technology for authorizing requests and authorizing information, applied in the field of communications, to solve problems such as the inability to support users to securely access protected resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
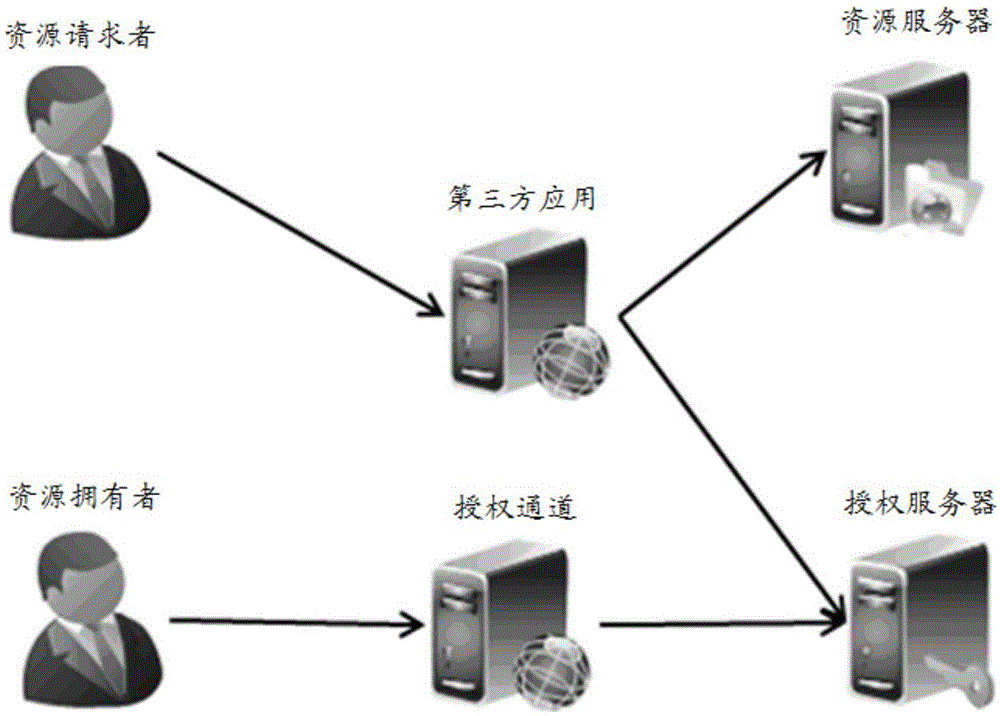
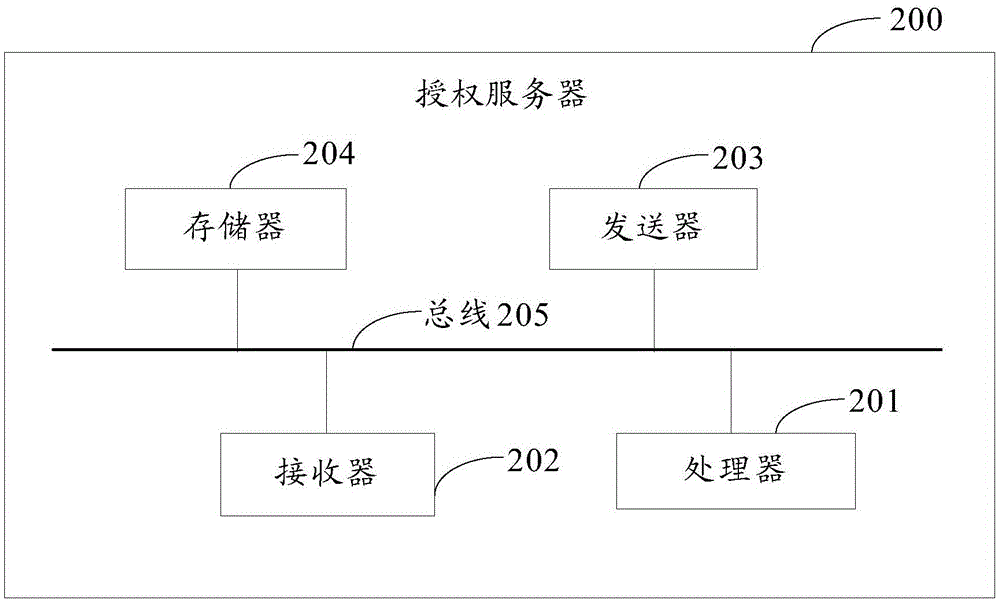
[0102] The embodiment of the present invention provides a figure 1 Authorization server 200 hosting user resources in the network architecture shown, see figure 2 , the authorization server 200 may include a processor 201, a receiver 202, a transmitter 203, a memory 204, and a bus 205, wherein the memory 204 is used to store instructions and data; the bus 205 is used to connect the processor 201, the receiver 202, the transmitter 203 and memory 204; the receiver 202 executing the instruction can be used to receive the authorization request sent by the resource requester through the first terminal, and the authorization request is used when the resource requester uses the third-party application through the first terminal to request access to the resource owner hosted in Authorize the resources of the server 200; the processor 201 executes the instruction and can be used to perform identity authentication on the resource requester, and if the identity authentication of the res...
Embodiment 2
[0149] The embodiment of the present invention provides a figure 1 The terminal 300 carrying the third-party application in the shown network architecture diagram, see image 3 , the terminal 300 may include a transmitter 301, a receiver 302, a memory 303, and a bus 304, wherein the memory 303 is used to store instructions and data; the bus 304 is used to connect the transmitter 301, the receiver 302, and the memory 303; the transmitter 301 executes This instruction can be used to send an authorization request to the authorization server when the resource requester uses a third-party application through the terminal 300 and requests access to the resource hosted by the resource owner on the authorization server. The parameters carried in the authorization request include the resource owner ID and the first The third-party application identification; the receiver 302 executes the instruction to receive the authorization instruction sent by the authorization server, so that the ...
Embodiment 3
[0153] The embodiment of the present invention provides an authorization method, which can be applied to such as figure 2 Authorization server hosting user resources for the structure shown, see Figure 4 , the main steps can include:
[0154] 401. The authorization server receives the authorization request sent by the resource requester through the first terminal, and the authorization request is used when the resource requester uses the third-party application through the first terminal to request access to the resources hosted by the resource owner on the authorization server.
[0155] The authorization server here is a server hosting user resources, and the terminal is a user device that carries third-party applications. For example, for third-party applications in the form of APP, the terminal can be smart mobile terminals such as mobile phones and iPads. In terms of application, the terminal may be a computer terminal or the like. When the resource requester requests ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com