Secure access of virtual machine memory suitable for ai assisted automotive applications
A virtual machine manager, virtual machine technology, applied in the direction of instrumentation, software simulation/interpretation/simulation, data processing input/output process, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
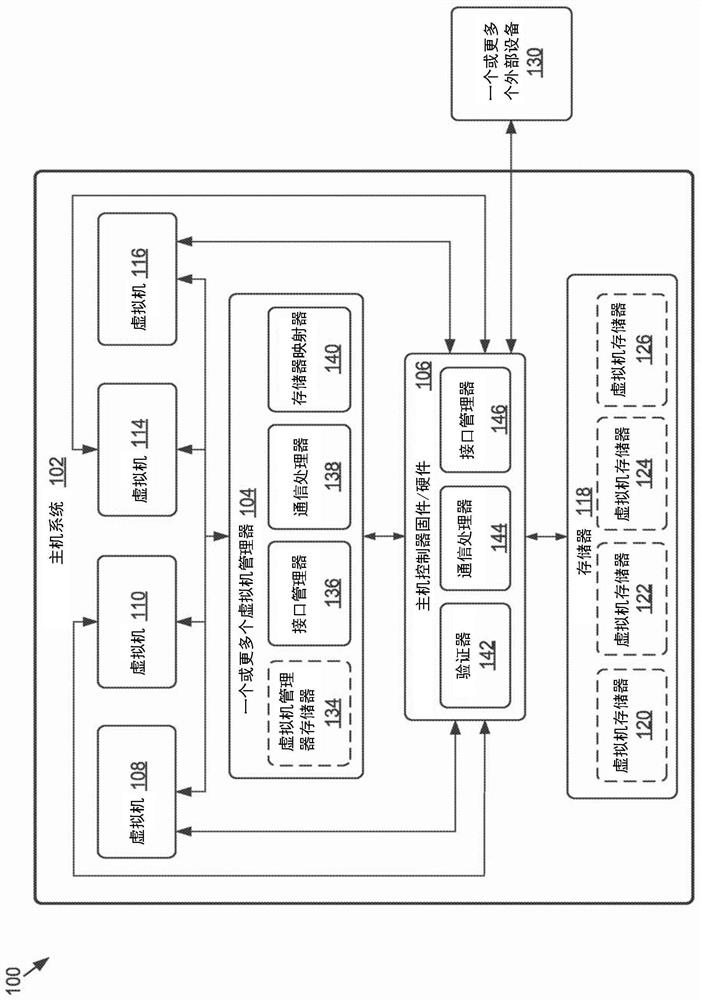
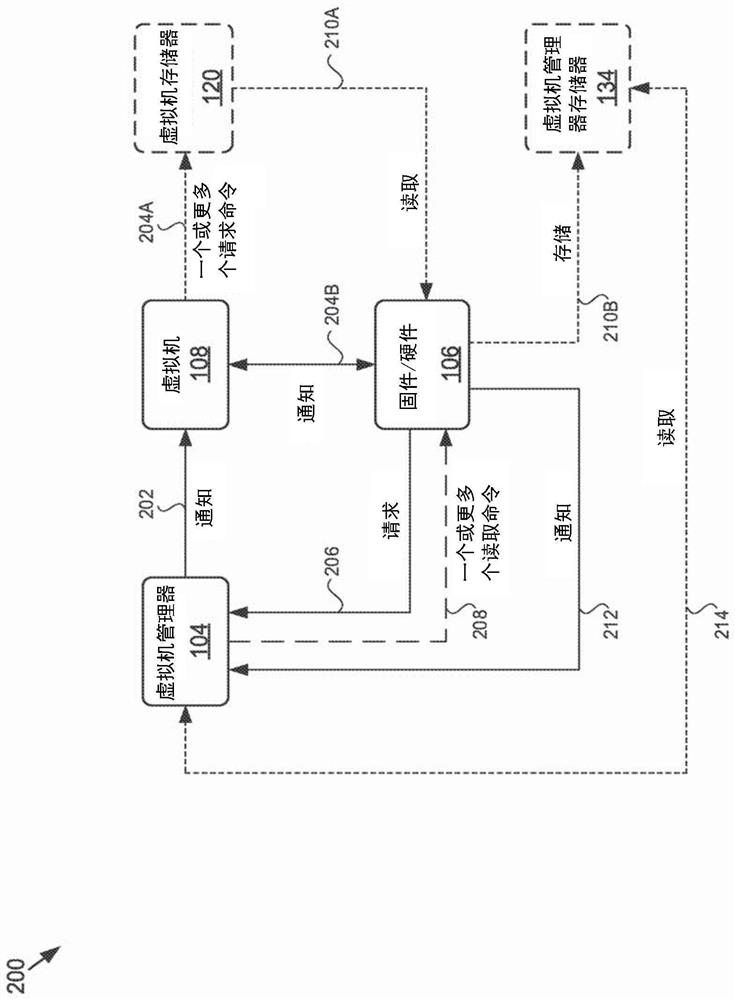
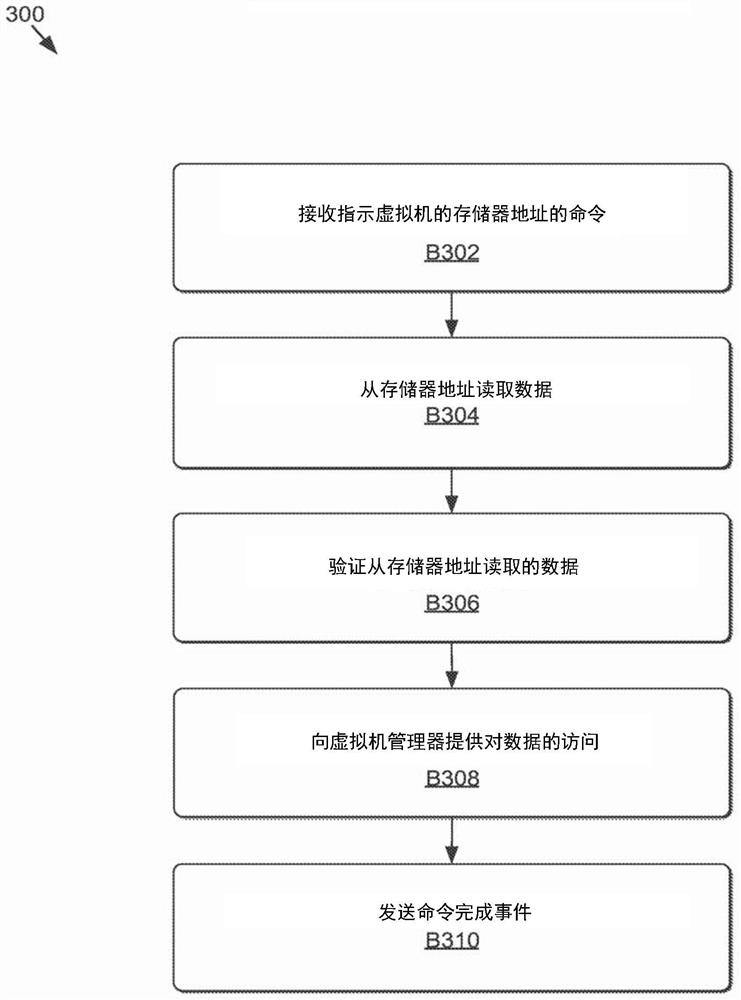
[0012] Disclosed herein is a system and method related to using a host controller's trusted firmware to authenticate one or more commands that read virtual machine memory (e.g., dedicated to or allocated to a virtual machine) system memory) and / or commands to read data from virtual machine memory to prevent inappropriate access to data in system memory. As a result, if the virtualization software is compromised, malicious actors can be prevented from accessing virtual machine memory at will.
[0013] In various embodiments, the virtualization software and one or more virtual machine managers (VMMs) of the VF may be used to facilitate the connection between the virtual machine and another entity (e.g., external virtual machine, external device), such as the host Another entity within the system (such as another virtual machine), or an entity external to the host system. A virtual machine manager may or may not include a virtual machine hypervisor of the host system. To facili...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com