Home security system and implementation method thereof
A technology of security system and implementation method, which is applied in the direction of closed-circuit television system, television, instrument, etc., can solve the problem that the user cannot open the access control for visitors, and achieve the effect of protecting safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
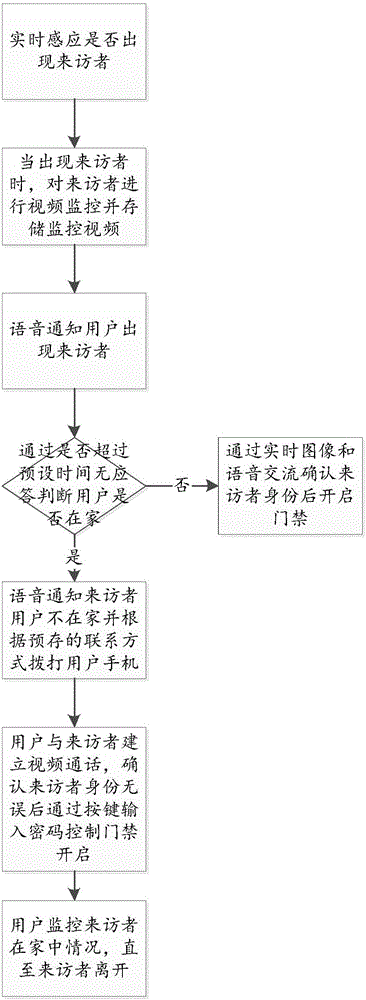
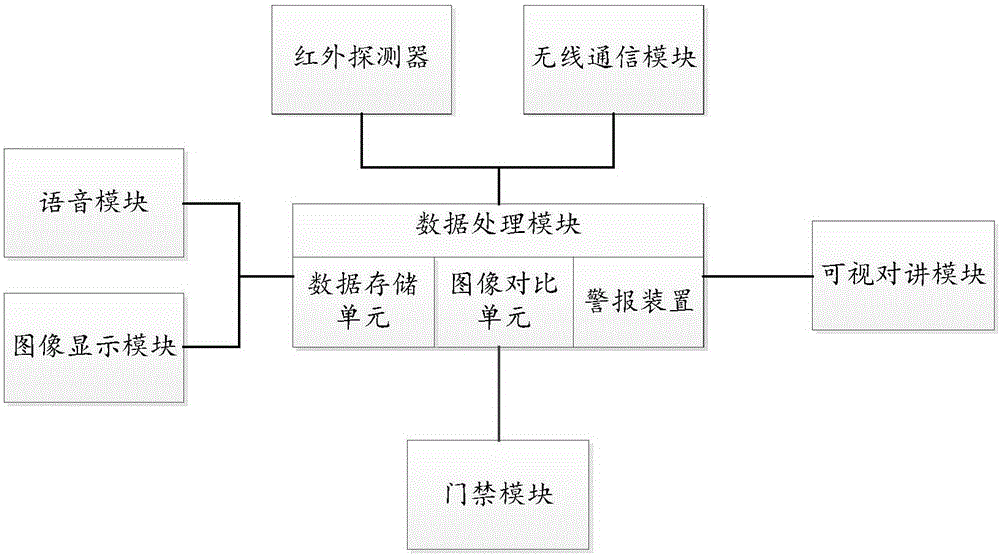
[0054]Embodiment 1: Infrared detectors are used to detect whether there are visitors at the door. When a visitor appears, the image acquisition module starts video monitoring the visitor and stores the image data of the visitor. The storage method is permanent storage until The user deletes it. When the visitor rings the doorbell, the system notifies the user of the presence of the visitor through the ringtone. When the user is at home, he can directly communicate with the visitor through the video intercom module to confirm the visitor's identity information to determine whether to give the visitor The user opens the access control. When the user is not at home, the data processing module judges whether the user response time exceeds the system preset time. When it exceeds, the data processing module judges that the user is not at home. Contact the user through the contact information, the user connects the phone and realizes the video call through the video intercom module to...
Embodiment 2
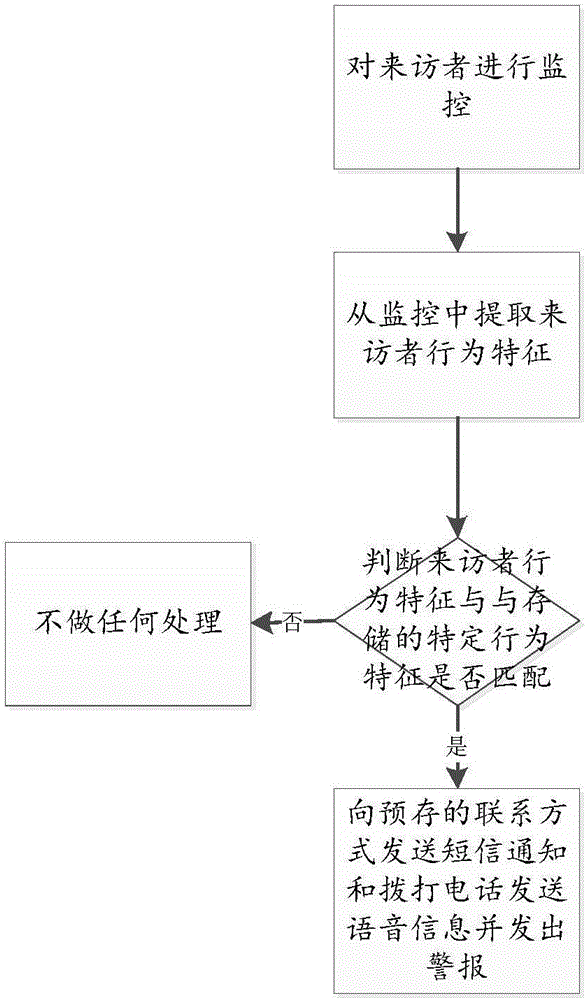
[0055] Embodiment 2: when the image acquisition module starts video surveillance of the visitor, the visitor's behavioral characteristics are compared with the specific behavioral characteristics pre-stored in the data processing module by the image comparison unit in the data processing module, when the visitor's behavior When the feature matches the pre-stored specific gratifying feature, the data processing module invokes the wireless communication module to send a short message and voice message notification according to the pre-stored contact information, and an alarm is issued through the alarm device.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com