A real-time summary generating method for streaming data
A streaming data and summary technology, applied in the field of data stream identification, can solve problems such as data defects, out-of-order and overlapping, and achieve the effect of reducing memory usage, reducing memory, and reducing hash collision rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
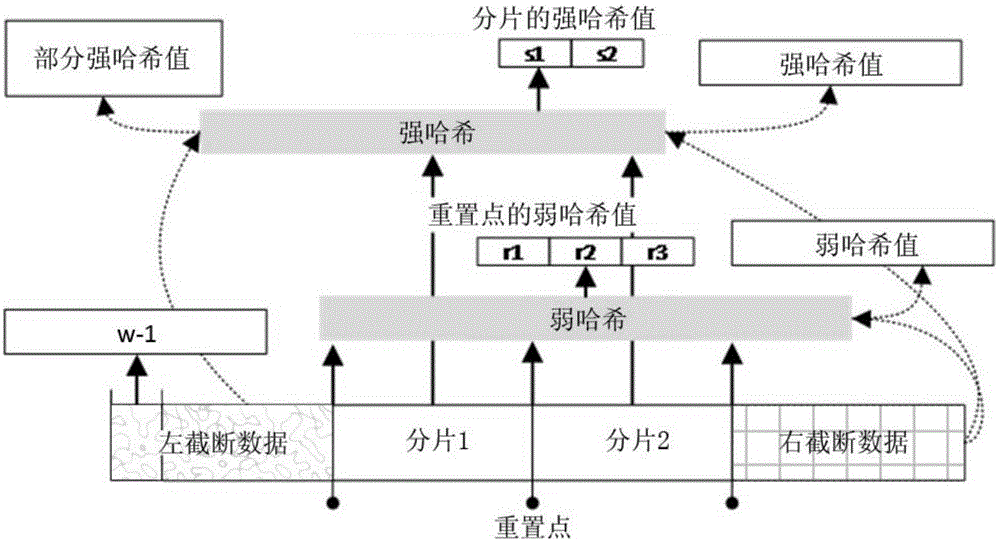
[0048] In the SFH algorithm, an input data block such as figure 1 Shown may be split into 3 parts:
[0049] 1) Fragmentation is the data between two reset points, and the fuzzy hash value of the fragmentation can be directly calculated;
[0050] 2) The left truncated data is the data from the beginning of the data block to the first reset point. The fuzzy hash value cannot be directly calculated. It is necessary to keep the first w-1 bytes of data in the buffer. You can Calculate the matrix product of the remaining bytes (leftstate);
[0051]3) The right truncated data is the data from the last reset point in the data block to the end position of the data. It is a part of the shard that has not yet fully arrived. The fuzzy hash value cannot be directly calculated, but part of the data can be calculated. matrix product (mapping hash state);
[0052] The complete processing flow mainly includes the following basic operations (multiplication and product below refer to matrix m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com